Views: 81
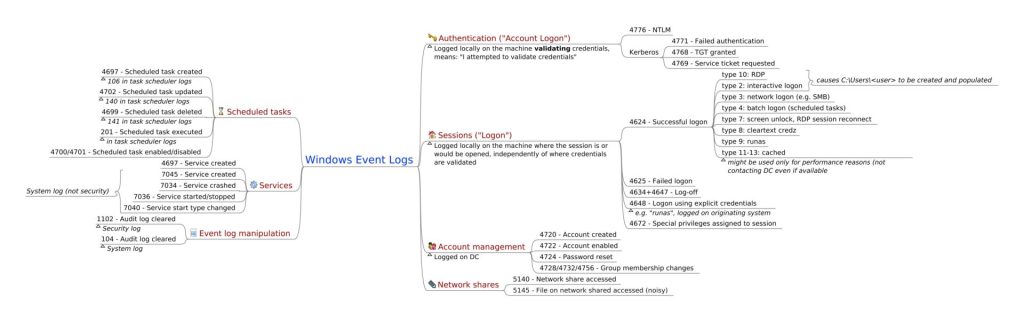
SOC (Security Operations Center) teams typically monitor various Windows event IDs to detect and respond to security incidents. While the specific event IDs may vary depending on the organization’s security policies and requirements, here are some commonly monitored Windows event IDs:
- Event ID 4624: This event indicates a successful user logon. Monitoring this event can help detect unauthorized access attempts.
- Event ID 4625: This event indicates a failed logon attempt. SOC teams can monitor this event to identify potential brute force attacks or unauthorized access attempts.
- Event ID 4776: This event indicates an account authentication failure. It can be helpful in detecting potential password spraying or account takeover attempts.
- Event ID 4688: This event indicates the creation of a new process. Monitoring this event can help identify suspicious or malicious processes running on a system.
- Event ID 7045: This event indicates the installation or modification of a service. SOC teams can monitor this event to detect unauthorized service installations or modifications.
- Event ID 5140: This event indicates the creation of a new file. Monitoring this event can help detect suspicious file activity or unauthorized file creation.
- Event ID 5156: This event indicates the filtering platform has allowed a connection. Monitoring this event can help identify network traffic and connections that might be malicious.
- Event ID Event ID 4689: This event indicates the closing of a process. Monitoring this event can help identify abnormal process terminations or potential indicators of compromise.
- Event ID 4740: This event indicates an account lockout. Monitoring this event can help detect brute force or password guessing attacks.
- Event ID Event ID 4769: This event indicates a Kerberos service ticket request. Monitoring this event can help identify potential Kerberos authentication issues or attacks.
It’s important to note that the specific event IDs to monitor may vary depending on the organization’s security policies, compliance requirements, and specific threat landscape. SOC teams often customize their event monitoring based on their unique environment and risk factors.