Views: 22
Locate tcpdump
which tcpdumpInstall TCPdump
sudo apt install tcpdumpTcpdump Version Validation
sudo tcpdump --versionTCPDump will resolve IPs to hostnames by default.
Traffic Captures with Tcpdump
Basic Capture Options
| Switch Command | Result |
|---|---|
| D | Will display any interfaces available to capture from. |
| i | Selects an interface to capture from. ex. -i eth0 |
| n | Do not resolve hostnames. |
| nn | Do not resolve hostnames or well-known ports. |
| e | Will grab the ethernet header along with upper-layer data. |
| X | Show Contents of packets in hex and ASCII. |
| XX | Same as X, but will also specify ethernet headers. (like using Xe) |
| v, vv, vvv | Increase the verbosity of output shown and saved. |
| c | Grab a specific number of packets, then quit the program. |
| s | Defines how much of a packet to grab. |
| S | change relative sequence numbers in the capture display to absolute sequence numbers. (13248765839 instead of 101) |
| q | Print less protocol information. |
| r file.pcap | Read from a file. |
| w file.pcap | Write into a file |
Listing Available Interfaces
sudo tcpdump -DChoosing an Interface to Capture From
sudo tcpdump -i eth0Disable Name Resolution
sudo tcpdump -i eth0 -nnDisplay the Ethernet Header
sudo tcpdump -i eth0 -eInclude ASCII and Hex Output
sudo tcpdump -i eth0 -XTcpdump Switch Combinations
sudo tcpdump -i eth0 -nnvXXTcpdump Output
Tcpdump Shell Breakdown
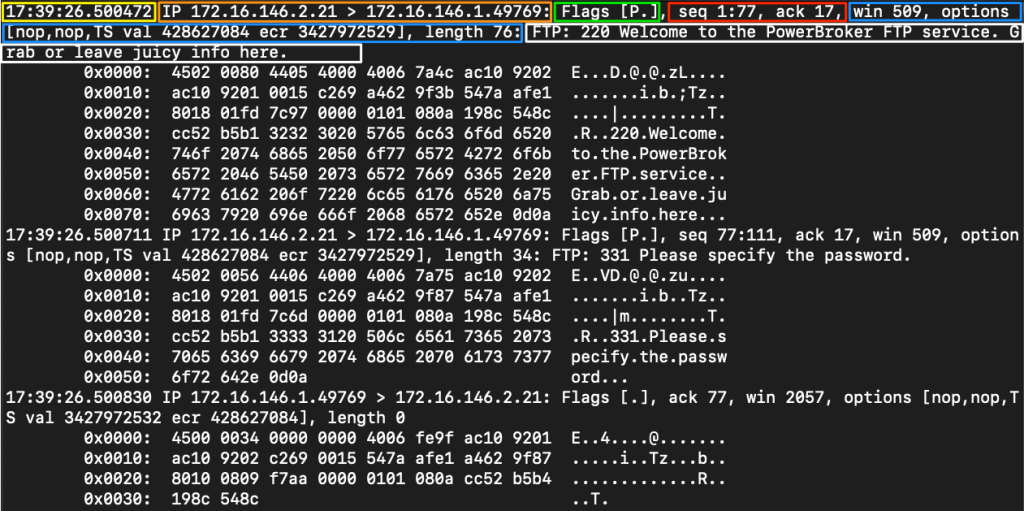
| Filter | Result |
|---|---|
| Timestamp | Yellow The timestamp field comes first and is configurable to show the time and date in a format we can ingest easily. |
| Protocol | Orange This section will tell us what the upper-layer header is. In our example, it shows IP. |
| Source & Destination IP.Port | Orange This will show us the source and destination of the packet along with the port number used to connect. Format == IP.port == 172.16.146.2.21 |
| Flags | Green This portion shows any flags utilized. |
| Sequence and Acknowledgement Numbers | Red This section shows the sequence and acknowledgment numbers used to track the TCP segment. Our example is utilizing low numbers to assume that relative sequence and ack numbers are being displayed. |
| Protocol Options | Blue Here, we will see any negotiated TCP values established between the client and server, such as window size, selective acknowledgments, window scale factors, and more. |
| Notes / Next Header | White Misc notes the dissector found will be present here. As the traffic we are looking at is encapsulated, we may see more header information for different protocols. In our example, we can see the TCPDump dissector recognizes FTP traffic within the encapsulation to display it for us. |
File Input/Output with Tcpdump
Save PCAP Output to a File
sudo tcpdump -i eth0 -w ~/output.pcapReading Output From a File
sudo tcpdump -r ~/output.pcapTcpdump Packet Filtering
Filtering and Advanced Syntax Options
Helpful TCPDump Filters
| Filter | Result |
|---|---|
| host | host will filter visible traffic to show anything involving the designated host. Bi-directional |
| src / dest | src and dest are modifiers. We can use them to designate a source or destination host or port. |
| net | net will show us any traffic sourcing from or destined to the network designated. It uses / notation. |
| proto | will filter for a specific protocol type. (ether, TCP, UDP, and ICMP as examples) |
| port | port is bi-directional. It will show any traffic with the specified port as the source or destination. |
| portrange | portrange allows us to specify a range of ports. (0-1024) |
| less / greater “< >” | less and greater can be used to look for a packet or protocol option of a specific size. |
| and / && | and && can be used to concatenate two different filters together. for example, src host AND port. |
| or | or allows for a match on either of two conditions. It does not have to meet both. It can be tricky. |
| not | not is a modifier saying anything but x. For example, not UDP. |
Host Filter
### Syntax: host [IP]
sudo tcpdump -i eth0 host 172.16.146.2Source/Destination Filter
### Syntax: src/dst [host|net|port] [IP|Network Range|Port]
sudo tcpdump -i eth0 src host 172.16.146.2Utilizing Source With Port as a Filter
sudo tcpdump -i eth0 tcp src port 80Using Destination in Combination with the Net Filter
sudo tcpdump -i eth0 dest net 172.16.146.0/24Protocol Filter
### Syntax: [tcp/udp/icmp]
sudo tcpdump -i eth0 udpProtocol Number Filter
With protocols that use both TCP and UDP for different functions, such as DNS, we can filter looking at one or the other TCP/UDP port 53 or filter for port 53. By doing this, we will see any traffic-utilizing that port, regardless of the transport protocol.
### Syntax: proto [protocol number]
sudo tcpdump -i eth0 proto 17Port Filter
### Syntax: port [port number]
sudo tcpdump -i eth0 tcp port 443Port Range Filter
### Syntax: portrange [portrange 0-65535]
sudo tcpdump -i eth0 portrange 0-1024Less/Greater Filter
### Syntax: less/greater [size in bytes]
sudo tcpdump -i eth0 less 64Those packets consisted of SYN, FIN, or KeepAlive packets are mostly smaller . Less than and greater than can be a helpful modifier set.
Utilizing Greater
sudo tcpdump -i eth0 greater 500AND Filter
### Syntax: and [requirement]
sudo tcpdump -i eth0 host 192.168.0.1 and port 23OR Filter
### Syntax: or/|| [requirement]
sudo tcpdump -r sus.pcap icmp or host 172.16.146.1NOT Filter
### Syntax: not/! [requirement]
sudo tcpdump -r sus.pcap not icmpInterpreting Tips and Tricks
Using the -S switch will display absolute sequence numbers, which can be extremely long. Typically, tcpdump displays relative sequence numbers, which are easier to track and read. However, if we look for these values in another tool or log, we will only find the packet based on absolute sequence numbers. For example, 13245768092588 to 100.
The -v, -X, and -e switches can help you increase the amount of data captured, while the -c, -n, -s, -S, and -q switches can help reduce and modify the amount of data written and seen.
Many handy options that can be used but are not always directly valuable for everyone are the -A and -l switches. A will show only the ASCII text after the packet line, instead of both ASCII and Hex. L will tell tcpdump to output packets in a different mode. L will line buffer instead of pooling and pushing in chunks. It allows us to send the output directly to another tool such as grep using a pipe |.
sudo tcpdump -Ar telnet.pcapASCII values shown below each output line because of our use of -A. This can be helpful when quickly looking for something human-readable in the output.
Piping a Capture to Grep
sudo tcpdump -Ar http.cap -l | grep 'mailto:*'Looking for TCP Protocol Flags
tcpdump -i eth0 'tcp[13] &2 != 0'Hunting For a SYN Flag
sudo tcpdump -i eth0 'tcp[13] &2 != 0'| Link | Description |
|---|---|
| IP Protocol | RFC 791 describes IP and its functionality. |
| ICMP Protocol | RFC 792 describes ICMP and its functionality. |
| TCP Protocol | RFC 793 describes the TCP protocol and how it functions. |
| UDP Protocol | RFC 768 describes UDP and how it operates. |
| RFC Quick Links | This Wikipedia article contains a large list of protocols tied to the RFC that explains their implementation. |

