Views: 84
Intrusion Detection System (IDS)
IDS is a passive monitoring solution for detecting possible malicious activities/patterns, abnormal incidents, and policy violations. It is responsible for generating alerts for each suspicious event.
There are two main types of IDS systems;
- Network Intrusion Detection System (NIDS) – NIDS monitors the traffic flow from various areas of the network. The aim is to investigate the traffic on the entire subnet. If a signature is identified, an alert is created.
- Host-based Intrusion Detection System (HIDS) – HIDS monitors the traffic flow from a single endpoint device. The aim is to investigate the traffic on a particular device. If a signature is identified, an alert is created.
Intrusion Prevention System (IPS)
IPS is an active protecting solution for preventing possible malicious activities/patterns, abnormal incidents, and policy violations. It is responsible for stopping/preventing/terminating the suspicious event as soon as the detection is performed.
There are four main types of IPS systems;
- Network Intrusion Prevention System (NIPS) – NIPS monitors the traffic flow from various areas of the network. The aim is to protect the traffic on the entire subnet. If a signature is identified, the connection is terminated.
- Behaviour-based Intrusion Prevention System (Network Behaviour Analysis – NBA) – Behaviour-based systems monitor the traffic flow from various areas of the network. The aim is to protect the traffic on the entire subnet. If a signature is identified, the connection is terminated.
Network Behaviour Analysis System works similar to NIPS. The difference between NIPS and Behaviour-based is; behaviour based systems require a training period (also known as “baselining”) to learn the normal traffic and differentiate the malicious traffic and threats. This model provides more efficient results against new threats. The system is trained to know the “normal” to detect “abnormal”. The training period is crucial to avoid any false positives.
- Wireless Intrusion Prevention System (WIPS) – WIPS monitors the traffic flow from of wireless network. The aim is to protect the wireless traffic and stop possible attacks launched from there. If a signature is identified, the connection is terminated.
- Host-based Intrusion Prevention System (HIPS) – HIPS actively protects the traffic flow from a single endpoint device. The aim is to investigate the traffic on a particular device. If a signature is identified, the connection is terminated.
Detection/Prevention Techniques
| Technique | Approach |
| Signature-Based | This technique relies on rules that identify the specific patterns of the known malicious behaviour. This model helps detect known threats. |
| Behaviour-Based | This technique identifies new threats with new patterns that pass through signatures. The model compares the known/normal with unknown/abnormal behaviours. This model helps detect previously unknown or new threats. |
| Policy-Based | This technique compares detected activities with system configuration and security policies. This model helps detect policy violations. |
SNORT
SNORT is an open-source, rule-based Network Intrusion Detection and Prevention System (NIDS/NIPS). It was developed and still maintained by Martin Roesch, open-source contributors, and the Cisco Talos team.
Capabilities of Snort;
- Live traffic analysis
- Attack and probe detection
- Packet logging
- Protocol analysis
- Real-time alerting
- Modules & plugins
- Pre-processors
- Cross-platform support! (Linux & Windows)
Snort has three main use models;
- Sniffer Mode – Read IP packets and prompt them in the console application.
- Packet Logger Mode – Log all IP packets (inbound and outbound) that visit the network.
- NIDS (Network Intrusion Detection System) and NIPS (Network Intrusion Prevention System) Modes – Log/drop the packets that are deemed as malicious according to the user-defined rules.
user@ubuntu$ snort -V
,,_ -*> Snort! <*-
o" )~ Version 2.9.7.0 GRE (Build XXXXXX)
'''' By Martin Roesch & The Snort Team: http://www.snort.org/contact#team
Copyright (C) 2014 Cisco and/or its affiliates. All rights reserved.
Copyright (C) 1998-2013 Sourcefire, Inc., et al.
Using libpcap version 1.9.1 (with TPACKET_V3)
Using PCRE version: 8.39 2016-06-14
Using ZLIB version: 1.2.11Configuration check
“-T” is used for testing configuration, and “-c” is identifying the configuration file (snort.conf).
user@ubuntu$ sudo snort -c /etc/snort/snort.conf -T
--== Initializing Snort ==--
Initializing Output Plugins!
Initializing Preprocessors!
Initializing Plug-ins!
... [Output truncated]
--== Initialization Complete ==--
,,_ -*> Snort! <*-
o" )~ Version 2.9.7.0 GRE (Build XXXX)
'''' By Martin Roesch & The Snort Team: http://www.snort.org/contact#team
Copyright (C) 2014 Cisco and/or its affiliates. All rights reserved.
Copyright (C) 1998-2013 Sourcefire, Inc., et al.
Using libpcap version 1.9.1 (with TPACKET_V3)
Using PCRE version: 8.39 2016-06-14
Using ZLIB version: 1.2.11
Rules Engine: SF_SNORT_DETECTION_ENGINE Version 2.4
Preprocessor Object: SF_GTP Version 1.1
Preprocessor Object: SF_SIP Version 1.1
Preprocessor Object: SF_SSH Version 1.1
Preprocessor Object: SF_SMTP Version 1.1
Preprocessor Object: SF_POP Version 1.0
Preprocessor Object: SF_DCERPC2 Version 1.0
Preprocessor Object: SF_IMAP Version 1.0
Preprocessor Object: SF_DNP3 Version 1.1
Preprocessor Object: SF_SSLPP Version 1.1
Preprocessor Object: SF_MODBUS Version 1.1
Preprocessor Object: SF_SDF Version 1.1
Preprocessor Object: SF_REPUTATION Version 1.1
Preprocessor Object: SF_DNS Version 1.1
Preprocessor Object: SF_FTPTELNET Version 1.2
... [Output truncated]
Snort successfully validated the configuration!
Snort exitingSnort Parameters
| Parameter | Description |
| -V / –version | This parameter provides information about your instance version. |
| -c | Identifying the configuration file |
| -T | Snort’s self-test parameter, you can test your setup with this parameter. |
| –q | Quiet mode prevents snort from displaying the default banner and initial information about your setup. |
Snort Operation Modes
Sniffer Mode
Like tcpdump, Snort has various flags capable of viewing various data about the packet it is ingesting.
Sniffer mode parameters are explained in the table below;
| Parameter | Description |
| -v | Verbose. Display the TCP/IP output in the console. |
| -d | Display the packet data (payload). |
| -e | Display the link-layer (TCP/IP/UDP/ICMP) headers. |
| –X | Display the full packet details in HEX. |
| –i | This parameter helps to define a specific network interface to listen/sniff. Once you have multiple interfaces, you can choose a specific interface to sniff. |
Sniffing with parameter “-i”
Start the Snort instance in verbose mode (-v) and use the interface (-i) “eth0”
sudo snort -v -i eth0In case you have only one interface, Snort uses it by default. The above example demonstrates to sniff on the interface named “eth0”.
Sniffing with parameter “-v”
Start the Snort instance in verbose mode (-v)
sudo snort -vSniffing with parameter “-d”
Start the Snort instance in dumping packet data mode (-d)
sudo snort -d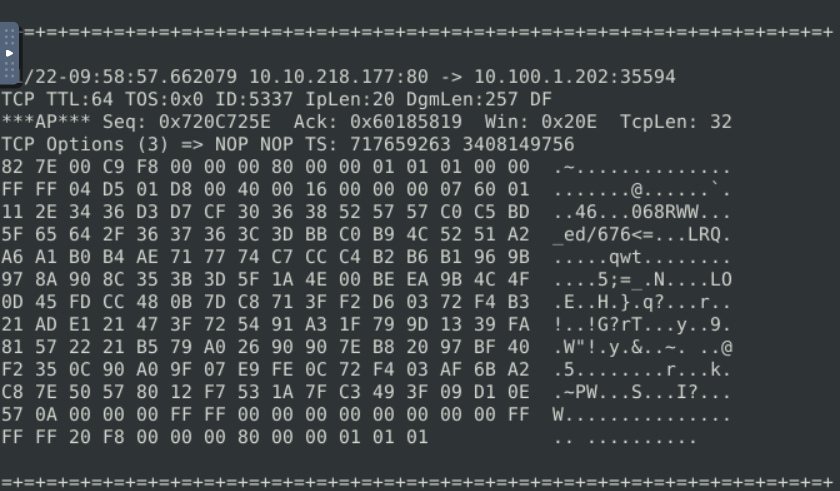
Sniffing with parameter “-de”
Start the Snort instance in dump (-d) and link-layer header grabbing (-e) mode
snort -d -e11/22-10:19:29.232699 02:C2:E4:E3:36:97 -> 02:C8:85:B5:5A:AA type:0x800 len:0x277
10.10.218.177:80 -> 10.100.1.202:35594 TCP TTL:64 TOS:0x0 ID:16868 IpLen:20 DgmLen:617 DF
***AP*** Seq: 0x75F00D1C Ack: 0x6019DFB9 Win: 0x238 TcpLen: 32
TCP Options (3) => NOP NOP TS: 718890834 3409381328
82 7E 02 31 F8 00 00 00 80 00 00 01 01 01 00 00 .~.1............
FF FF 00 00 00 3F 00 43 00 19 00 00 00 07 60 01 .....?.C......`.
4A CE CE CE 60 60 60 8B 8B 8B 69 69 69 3C 3C 3C J...```...iii<<<
73 73 73 A9 A9 A9 64 64 64 95 95 95 BE BE BE C3 sss...ddd.......
C3 C3 9A 9A 9A 62 62 62 71 71 71 B5 B5 B5 97 97 .....bbbqqq.....
97 C6 C6 C6 42 42 42 C1 C1 C1 AF AF AF CC CC CC ....BBB.........
BB BB BB 4A 4A 4A CD CD CD 86 86 86 5D 5D 5D CA ...JJJ......]]].
CA CA 8E 8E 8E BC BC BC A3 A3 A3 70 70 70 3E 3E ...........ppp>>
3E B4 B4 B4 BD BD BD 5E 5E 5E 40 40 40 44 44 44 >......^^^@@@DDD
4F 4F 4F B6 B6 B6 B7 B7 B7 9F 9F 9F 9B 9B 9B 98 OOO.............
98 98 91 91 91 9C 9C 9C 46 46 46 65 65 65 76 76 ........FFFeeevv
76 4B 4B 4B 7F 7F 7F A0 A0 A0 6E 6E 6E 6F 6F 6F vKKK......nnnooo
41 41 41 56 56 56 B3 B3 B3 4E 4E 4E 8C 8C 8C 5F AAAVVV...NNN..._
5F 5F A5 A5 A5 A4 A4 A4 54 54 54 94 94 94 AB AB __......TTT.....
AB A1 A1 A1 AC AC AC 63 63 63 AD AD AD C0 C0 C0 .......ccc......
6D 6D 6D 67 67 67 52 52 52 7C 7C 7C 47 47 47 82 mmmgggRRR|||GGG.
82 82 9B 02 EC 9C C9 72 82 40 10 86 9B 62 54 60 .......r.@...bT`
D4 10 24 B8 6B DC CD EA BE 2F 31 7B F4 FD 1F C8 ..$.k..../1{....
06 66 AA 9C 72 6A CA F2 62 0E FE 55 DC 9A 6F BA .f..rj..b..U..o.
1B 38 7E 5C F3 EF 37 E0 D8 00 FE 75 62 2A 87 82 .8~\..7....ub*..
49 26 86 29 A1 E1 E2 5B 2E 2A 40 50 18 6B 87 25 I&.)...[.*@P.k.%
B7 D1 83 52 3D 6B 18 C6 03 14 D1 01 51 23 82 42 ...R=k......Q#.B
83 A9 22 22 22 D4 58 52 05 86 B0 1E 9F 44 2B 82 ..""".XR.....D+.
1F A7 33 DF 05 92 F9 E7 9C 0C C1 07 49 BD BC 76 ..3.........I..v
BA 3D D9 40 1C D1 AF 0D 86 DA 48 18 C4 D3 34 8D [email protected].
F2 5D A4 C7 B8 0F B3 7E 2F 61 E8 5E 1C 33 71 A7 .].....~/a.^.3q.
33 80 3C 11 10 73 4A 69 92 23 0A 84 2E 96 C5 D5 3.<..sJi.#......
5A 86 A8 DE 60 9C 16 41 E9 C4 16 11 E1 88 6C 90 Z...`..A......l.
37 52 4A 60 36 32 44 58 F8 5E F6 5D A2 B2 D0 85 7RJ`62DX.^.]....
80 B8 23 B2 19 82 7B D9 2E 4C 82 C6 52 45 D1 05 ..#...{..L..RE..
7C C4 B1 CF CF 2F 59 17 DF 26 C6 86 6A C2 75 23 |..../Y..&..j.u#
2A 84 F5 53 6B D4 7F 65 6A 94 1E FC DD E5 0F 9A *..Sk..ej.......
8D AD B7 13 1E EA D1 79 56 D3 51 BF E5 E9 D6 19 .......yV.Q.....
16 CF 89 1F CE B5 EC B2 1B D8 03 00 00 FF FF 00 ................
00 00 00 00 00 00 00 FF FF FF 20 F8 00 00 00 80 .......... .....
00 00 01 01 01 .....
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
WARNING: No preprocessors configured for policy 0.
WARNING: No preprocessors configured for policy 0.
WARNING: No preprocessors configured for policy 0.
11/22-10:19:29.238473 02:C8:85:B5:5A:AA -> 02:C2:E4:E3:36:97 type:0x800 len:0x42
10.100.1.202:35596 -> 10.10.218.177:80 TCP TTL:64 TOS:0x0 ID:2931 IpLen:20 DgmLen:52 DF
***A**** Seq: 0xDCEB166F Ack: 0x83091287 Win: 0x1957 TcpLen: 32
TCP Options (3) => NOP NOP TS: 3409381340 718890830
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
WARNING: No preprocessors configured for policy 0.
11/22-10:19:29.238559 02:C8:85:B5:5A:AA -> 02:C2:E4:E3:36:97 type:0x800 len:0x42
10.100.1.202:35594 -> 10.10.218.177:80 TCP TTL:64 TOS:0x0 ID:17714 IpLen:20 DgmLen:52 DF
***A**** Seq: 0x6019DFB9 Ack: 0x75F018CF Win: 0x334D TcpLen: 32
TCP Options (3) => NOP NOP TS: 3409381340 718890834
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
WARNING: No preprocessors configured for policy 0.
11/22-10:19:29.253639 02:C8:85:B5:5A:AA -> 02:C2:E4:E3:36:97 type:0x800 len:0x62
10.100.1.202:35594 -> 10.10.218.177:80 TCP TTL:64 TOS:0x0 ID:17715 IpLen:20 DgmLen:84 DF
***AP*** Seq: 0x6019DFB9 Ack: 0x75F018CF Win: 0x334D TcpLen: 32
TCP Options (3) => NOP NOP TS: 3409381355 718890834
82 8A FA D4 27 A5 02 D4 27 A5 FA D4 27 A4 FB D5 ....'...'...'...
82 8A 04 5B 70 57 FC 5B 70 57 04 5B 70 56 05 5A ...[pW.[pW.[pV.Z
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
WARNING: No preprocessors configured for policy 0.
11/22-10:19:29.253640 02:C8:85:B5:5A:AA -> 02:C2:E4:E3:36:97 type:0x800 len:0x62
10.100.1.202:35596 -> 10.10.218.177:80 TCP TTL:64 TOS:0x0 ID:2932 IpLen:20 DgmLen:84 DF
***AP*** Seq: 0xDCEB166F Ack: 0x83091287 Win: 0x1957 TcpLen: 32
TCP Options (3) => NOP NOP TS: 3409381355 718890830
82 8A B6 BD 3D 7B 4E BD 3D 7B B6 BD 3D 7A B7 BC ....={N.={..=z..
82 8A 84 90 42 F0 7C 90 42 F0 84 90 42 F1 85 91 ....B.|.B...B...
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
11/22-10:19:29.253751 02:C2:E4:E3:36:97 -> 02:C8:85:B5:5A:AA type:0x800 len:0x42
10.10.218.177:80 -> 10.100.1.202:35596 TCP TTL:64 TOS:0x0 ID:8563 IpLen:20 DgmLen:52 DF
***A**** Seq: 0x83091287 Ack: 0xDCEB168F Win: 0x1ED TcpLen: 32
TCP Options (3) => NOP NOP TS: 718890855 3409381355
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
WARNING: No preprocessors configured for policy 0.
WARNING: No preprocessors configured for policy 0.
WARNING: No preprocessors configured for policy 0.
11/22-10:19:29.257122 02:C8:85:B5:5A:AA -> 02:C2:E4:E3:36:97 type:0x800 len:0x42
10.100.1.202:35596 -> 10.10.218.177:80 TCP TTL:64 TOS:0x0 ID:2933 IpLen:20 DgmLen:52 DF
***A**** Seq: 0xDCEB168F Ack: 0x83095871 Win: 0x1907 TcpLen: 32
TCP Options (3) => NOP NOP TS: 3409381358 718890858
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
WARNING: No preprocessors configured for policy 0.
11/22-10:19:29.257122 02:C8:85:B5:5A:AA -> 02:C2:E4:E3:36:97 type:0x800 len:0x42
10.100.1.202:35596 -> 10.10.218.177:80 TCP TTL:64 TOS:0x0 ID:2934 IpLen:20 DgmLen:52 DF
***A**** Seq: 0xDCEB168F Ack: 0x8309AEC2 Win: 0x1887 TcpLen: 32
TCP Options (3) => NOP NOP TS: 3409381358 718890858
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
WARNING: No preprocessors configured for policy 0.
WARNING: No preprocessors configured for policy 0.
WARNING: No preprocessors configured for policy 0.
11/22-10:19:29.258958 02:C8:85:B5:5A:AA -> 02:C2:E4:E3:36:97 type:0x800 len:0x42
10.100.1.202:35594 -> 10.10.218.177:80 TCP TTL:64 TOS:0x0 ID:17716 IpLen:20 DgmLen:52 DF
***A**** Seq: 0x6019DFD9 Ack: 0x75F0B50C Win: 0x327D TcpLen: 32
TCP Options (3) => NOP NOP TS: 3409381360 718890860
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
WARNING: No preprocessors configured for policy 0.
11/22-10:19:29.259166 02:C8:85:B5:5A:AA -> 02:C2:E4:E3:36:97 type:0x800 len:0x62
10.100.1.202:35594 -> 10.10.218.177:80 TCP TTL:64 TOS:0x0 ID:17717 IpLen:20 DgmLen:84 DF
***AP*** Seq: 0x6019DFD9 Ack: 0x75F0B50C Win: 0x334D TcpLen: 32
TCP Options (3) => NOP NOP TS: 3409381360 718890860
82 8A 72 59 3A E8 8A 59 3A E8 72 59 3A E9 73 58 ..rY:..Y:.rY:.sX
82 8A E7 64 F5 77 1F 64 F5 77 E7 64 F5 76 E6 65 ...d.w.d.w.d.v.e
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
WARNING: No preprocessors configured for policy 0.
11/22-10:19:29.261745 02:C8:85:B5:5A:AA -> 02:C2:E4:E3:36:97 type:0x800 len:0x62
10.100.1.202:35596 -> 10.10.218.177:80 TCP TTL:64 TOS:0x0 ID:2935 IpLen:20 DgmLen:84 DF
***AP*** Seq: 0xDCEB168F Ack: 0x8309AEC2 Win: 0x1957 TcpLen: 32
TCP Options (3) => NOP NOP TS: 3409381363 718890858
82 8A 07 9E AC 36 FF 9E AC 36 07 9E AC 37 06 9F .....6...6...7..
82 8A DF 6E B7 0D 27 6E B7 0D DF 6E B7 0C DE 6F ...n..'n...n...o
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
Sniffing with parameter “-X”
Start the Snort instance in full packet dump mode (-X)
sudo snort -X+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
WARNING: No preprocessors configured for policy 0.
11/22-10:23:33.379755 10.100.1.202:35594 -> 10.10.218.177:80
TCP TTL:64 TOS:0x0 ID:23732 IpLen:20 DgmLen:68 DF
***AP*** Seq: 0x601B0EFD Ack: 0x7A29DA5B Win: 0x334D TcpLen: 32
TCP Options (3) => NOP NOP TS: 3409625477 719134959
0x0000: 02 C2 E4 E3 36 97 02 C8 85 B5 5A AA 08 00 45 00 ....6.....Z...E.
0x0010: 00 44 5C B4 40 00 40 06 ED 16 0A 64 01 CA 0A 0A .D\.@.@....d....
0x0020: DA B1 8B 0A 00 50 60 1B 0E FD 7A 29 DA 5B 80 18 .....P`...z).[..
0x0030: 33 4D CB B6 00 00 01 01 08 0A CB 3A C1 85 2A DD 3M.........:..*.
0x0040: 20 EF 82 8A 39 73 7A 9E C1 73 7A 9E 39 73 7A 9F ...9sz..sz.9sz.
0x0050: 38 72 8r
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
11/22-10:23:33.379828 10.10.218.177:80 -> 10.100.1.202:35594
TCP TTL:64 TOS:0x0 ID:28124 IpLen:20 DgmLen:52 DF
***A**** Seq: 0x7A29DA5B Ack: 0x601B0F0D Win: 0x240 TcpLen: 32
TCP Options (3) => NOP NOP TS: 719134981 3409625457
0x0000: 02 C8 85 B5 5A AA 02 C2 E4 E3 36 97 08 00 45 00 ....Z.....6...E.
0x0010: 00 34 6D DC 40 00 40 06 DB FE 0A 0A DA B1 0A 64 .4m.@[email protected]
0x0020: 01 CA 00 50 8B 0A 7A 29 DA 5B 60 1B 0F 0D 80 10 ...P..z).[`.....
0x0030: 02 40 F1 0F 00 00 01 01 08 0A 2A DD 21 05 CB 3A .@........*.!..:
0x0040: C1 71 .q
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
WARNING: No preprocessors configured for policy 0.
11/22-10:23:33.380164 10.100.1.202:35596 -> 10.10.218.177:80
TCP TTL:64 TOS:0x0 ID:9228 IpLen:20 DgmLen:68 DF
***AP*** Seq: 0xDCEC2903 Ack: 0x8753ECE4 Win: 0x1957 TcpLen: 32
TCP Options (3) => NOP NOP TS: 3409625478 719134975
0x0000: 02 C2 E4 E3 36 97 02 C8 85 B5 5A AA 08 00 45 00 ....6.....Z...E.
0x0010: 00 44 24 0C 40 00 40 06 25 BF 0A 64 01 CA 0A 0A .D$.@.@.%..d....
0x0020: DA B1 8B 0C 00 50 DC EC 29 03 87 53 EC E4 80 18 .....P..)..S....
0x0030: 19 57 2A 70 00 00 01 01 08 0A CB 3A C1 86 2A DD .W*p.......:..*.
0x0040: 20 FF 82 8A 6A 7D AF 70 92 7D AF 70 6A 7D AF 71 ...j}.p.}.pj}.q
0x0050: 6B 7C k|
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
WARNING: No preprocessors configured for policy 0.
WARNING: No preprocessors configured for policy 0.
WARNING: No preprocessors configured for policy 0.
11/22-10:23:33.385386 10.100.1.202:35594 -> 10.10.218.177:80
TCP TTL:64 TOS:0x0 ID:23733 IpLen:20 DgmLen:100 DF
***AP*** Seq: 0x601B0F0D Ack: 0x7A2A6A6D Win: 0x328D TcpLen: 32
TCP Options (3) => NOP NOP TS: 3409625483 719134983
0x0000: 02 C2 E4 E3 36 97 02 C8 85 B5 5A AA 08 00 45 00 ....6.....Z...E.
0x0010: 00 64 5C B5 40 00 40 06 EC F5 0A 64 01 CA 0A 0A .d\.@.@....d....
0x0020: DA B1 8B 0A 00 50 60 1B 0F 0D 7A 2A 6A 6D 80 18 .....P`...z*jm..
0x0030: 32 8D C4 6D 00 00 01 01 08 0A CB 3A C1 8B 2A DD 2..m.......:..*.
0x0040: 21 07 82 8A A2 88 0A EC 5A 88 0A EC A2 88 0A ED !.......Z.......
0x0050: A3 89 82 8A 72 58 66 36 8A 58 66 36 72 58 66 37 ....rXf6.Xf6rXf7
0x0060: 73 59 82 8A 11 F8 92 78 E9 F8 92 78 11 F8 92 79 sY.....x...x...y
0x0070: 10 F9 ..
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
WARNING: No preprocessors configured for policy 0.
11/22-10:23:33.385773 10.100.1.202:35596 -> 10.10.218.177:80
TCP TTL:64 TOS:0x0 ID:9229 IpLen:20 DgmLen:52 DF
***A**** Seq: 0xDCEC2913 Ack: 0x875437F5 Win: 0x18F7 TcpLen: 32
TCP Options (3) => NOP NOP TS: 3409625483 719134984
0x0000: 02 C2 E4 E3 36 97 02 C8 85 B5 5A AA 08 00 45 00 ....6.....Z...E.
0x0010: 00 34 24 0D 40 00 40 06 25 CE 0A 64 01 CA 0A 0A .4$.@.@.%..d....
0x0020: DA B1 8B 0C 00 50 DC EC 29 13 87 54 37 F5 80 10 .....P..)..T7...
0x0030: 18 F7 43 8B 00 00 01 01 08 0A CB 3A C1 8B 2A DD ..C........:..*.
0x0040: 21 08 !.
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
WARNING: No preprocessors configured for policy 0.
11/22-10:23:33.385889 10.100.1.202:35596 -> 10.10.218.177:80
TCP TTL:64 TOS:0x0 ID:9230 IpLen:20 DgmLen:84 DF
***AP*** Seq: 0xDCEC2913 Ack: 0x875437F5 Win: 0x1957 TcpLen: 32
TCP Options (3) => NOP NOP TS: 3409625484 719134984
0x0000: 02 C2 E4 E3 36 97 02 C8 85 B5 5A AA 08 00 45 00 ....6.....Z...E.
0x0010: 00 54 24 0E 40 00 40 06 25 AD 0A 64 01 CA 0A 0A .T$.@.@.%..d....
0x0020: DA B1 8B 0C 00 50 DC EC 29 13 87 54 37 F5 80 18 .....P..)..T7...
0x0030: 19 57 0B C8 00 00 01 01 08 0A CB 3A C1 8C 2A DD .W.........:..*.
0x0040: 21 08 82 8A E1 0F 73 83 19 0F 73 83 E1 0F 73 82 !.....s...s...s.
0x0050: E0 0E 82 8A 45 D8 84 A9 BD D8 84 A9 45 D8 84 A8 ....E.......E...
0x0060: 44 D9 D.
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
We can use the parameters both in combined and separated form as follows;
- snort -v
- snort -vd
- snort -de
- snort -v -d -e
- snort -X
Logger Mode
| Parameter | Description |
|---|---|
| -l | Logger mode, target log and alert output directory. Default output folder is /var/log/snortThe default action is to dump as tcpdump format in /var/log/snort |
| -K ASCII | Log packets in ASCII format. |
| -r | Reading option, read the dumped logs in Snort. |
| -n | Specify the number of packets that will process/read. Snort will stop after reading the specified number of packets. |
Logging with parameter “-l”
sudo snort -dev -l .The -l . part of the command creates the logs in the current directory.
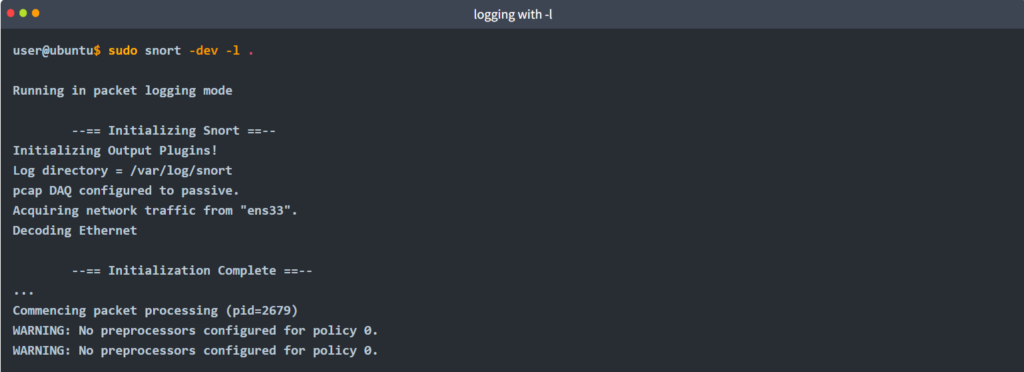
Once the traffic is generated, Snort will start showing the packets and log them in the target directory. You can configure the default output directory in snort.config file. However, you can use the “-l” parameter to set a target directory. Identifying the default log directory is useful for continuous monitoring operations, and the “-l” parameter is much more useful for testing purposes.
Logging with parameter “-K ASCII”
sudo snort -dev -K ASCIIOnce the traffic is generated, Snort will start showing the packets in verbosity mode as follows;
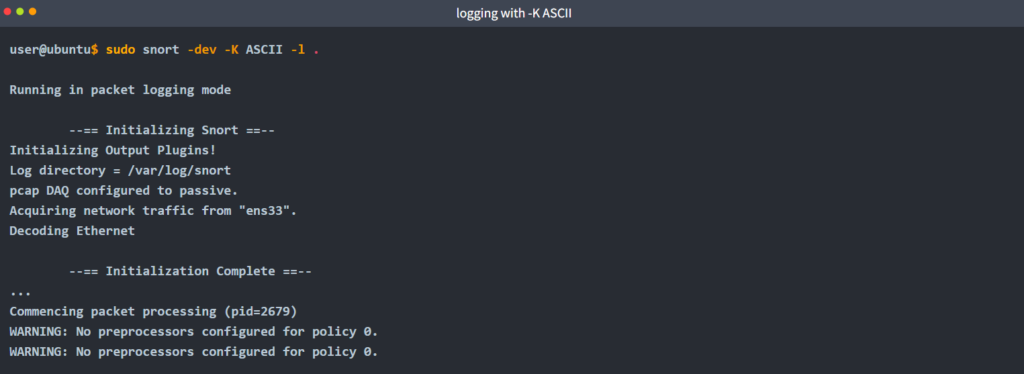
The logs created with “-K ASCII” parameter is entirely different. There are seperate folders with IP address names. Let’s look into them.
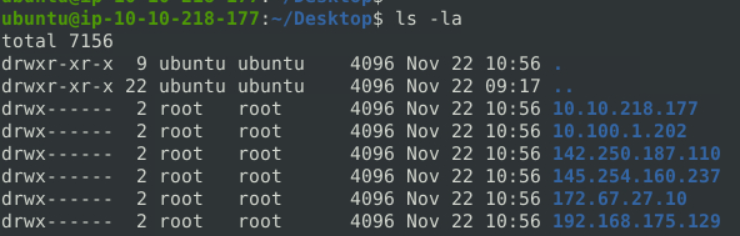
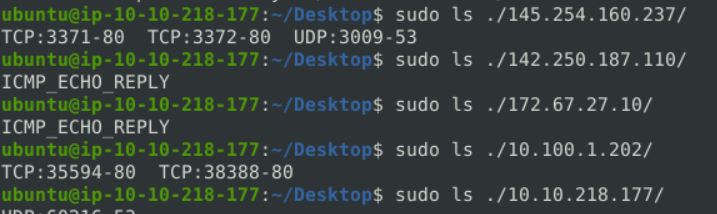
In a nutshell, ASCII mode provides multiple files in human-readable format, so it is possible to read the logs easily by using a text editor. By contrast with ASCII format, binary format is not human-readable and requires analysis using Snort or an application like tcpdump.
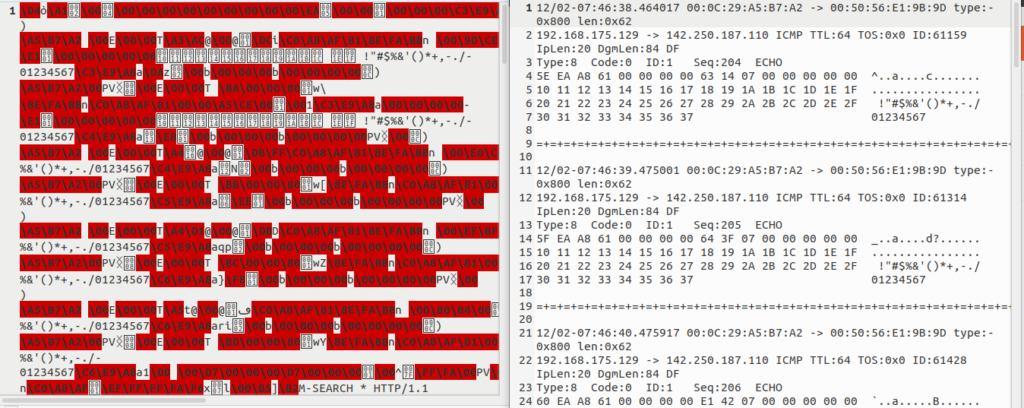
Let’s compare the ASCII format with the binary format by opening both of them in a text editor. The difference between the binary log file and the ASCII log file is shown below. (Left side: binary format. Right side: ASCII format).
Reading generated logs with parameter “-r”
Start the Snort instance in packet reader mode
sudo snort -r snort.log.1638459842
WARNING: No preprocessors configured for policy 0.
11/22-10:49:17.567621 10.100.1.202:35596 -> 10.10.218.177:80
TCP TTL:64 TOS:0x0 ID:15704 IpLen:20 DgmLen:68 DF
***AP*** Seq: 0xDCED34BA Ack: 0x8C352801 Win: 0x20A8 TcpLen: 32
TCP Options (3) => NOP NOP TS: 3411169643 720679167
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
11/22-10:49:17.567654 10.10.218.177:80 -> 10.100.1.202:35596
TCP TTL:64 TOS:0x0 ID:31830 IpLen:20 DgmLen:52 DF
***A**** Seq: 0x8C352801 Ack: 0xDCED34CA Win: 0x1F5 TcpLen: 32
TCP Options (3) => NOP NOP TS: 720679169 3411169643
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
WARNING: No preprocessors configured for policy 0.
WARNING: No preprocessors configured for policy 0.
WARNING: No preprocessors configured for policy 0.
11/22-10:49:17.568607 10.100.1.202:35596 -> 10.10.218.177:80
TCP TTL:64 TOS:0x0 ID:15705 IpLen:20 DgmLen:52 DF
***A**** Seq: 0xDCED34CA Ack: 0x8C361CB4 Win: 0x1F74 TcpLen: 32
TCP Options (3) => NOP NOP TS: 3411169644 720679169
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+
WARNING: No preprocessors configured for policy 0.
11/22-10:49:17.569767 10.100.1.202:35596 -> 10.10.218.177:80
TCP TTL:64 TOS:0x0 ID:15706 IpLen:20 DgmLen:68 DF
***AP*** Seq: 0xDCED34CA Ack: 0x8C3627D0 Win: 0x20A8 TcpLen: 32
TCP Options (3) => NOP NOP TS: 3411169645 720679169
=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+Note that Snort can read and handle the binary like output (tcpdump and Wireshark also can handle this log format). However, if you create logs with “-K ASCII” parameter, Snort will not read them.
Opening log file with tcpdump.
sudo tcpdump -r snort.log.1638459842 -ntc 10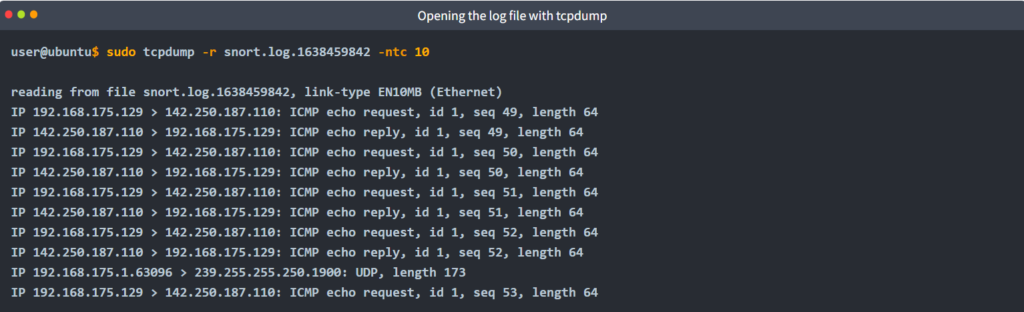
Opening log file with Wireshark.
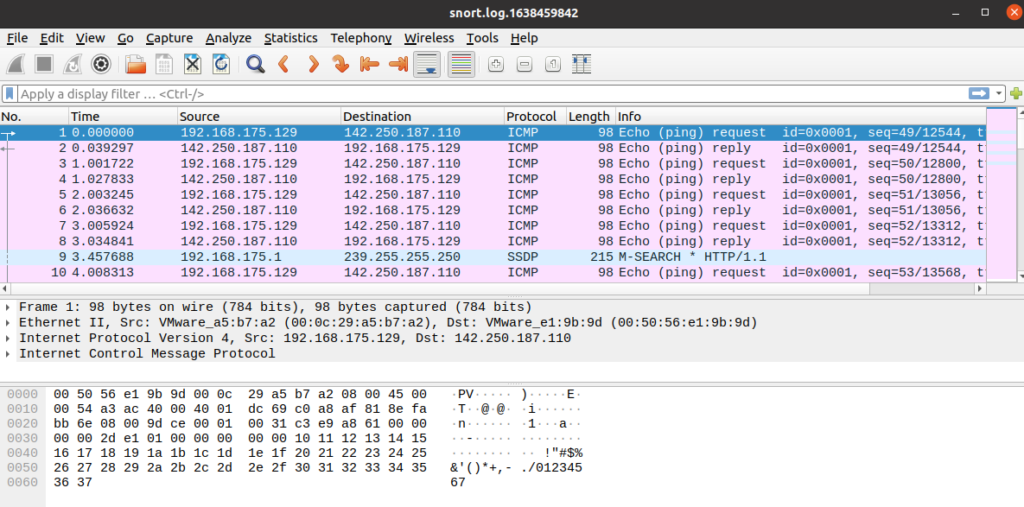
“-r” parameter also allows users to filter the binary log files. You can filter the processed log to see specific packets with the “-r” parameter and Berkeley Packet Filters (BPF).
sudo snort -r logname.log -Xsudo snort -r logname.log icmpsudo snort -r logname.log tcpsudo snort -r logname.log 'udp and port 53'
The output will be the same as the above, but only packets with the chosen protocol will be shown. Additionally, you can specify the number of processes with the parameter “-n”. The following command will process only the first 10 packets:
snort -dvr logname.log -n 10Please use the following resources to understand how the BPF works and its use.
- https://en.wikipedia.org/wiki/Berkeley_Packet_Filter
- https://biot.com/capstats/bpf.html
- https://www.tcpdump.org/manpages/tcpdump.1.html
IDS/IPS mode
Capabilities of Snort are not limited to sniffing and logging the traffic. IDS/IPS mode helps you manage the traffic according to user-defined rules.
IDS/IPS mode depends on the rules and configuration.
NIDS mode parameters are explained in the table below;
| Parameter | Description |
|---|---|
| -c | Defining the configuration file. |
| -T | Testing the configuration file. |
| -N | Disable logging. |
| -D | Background mode. |
| -A | Alert modes; full: Full alert mode, providing all possible information about the alert. This one also is the default mode; once you use -A and don’t specify any mode, snort uses this mode.fast: Fast mode shows the alert message, timestamp, source and destination IP, along with port numbers.console: Provides fast style alerts on the console screen.cmg: CMG style,basic header details with payload in hex and text format.none: Disabling alerting. |
Once you start running IDS/IPS mode, you need to use rules. As we mentioned earlier, we will use a pre-defined ICMP rule as an example. The defined rule will only generate alerts in any direction of ICMP packet activity.
This rule is located in “/etc/snort/rules/local.rules”.
alert icmp any any <> any any (msg: "ICMP Packet Found"; sid: 100001; rev:1;)Snort will create an “alert” file if the traffic flow triggers an alert.
IDS/IPS mode with parameter “-c and -T”
Start the Snort instance and test the configuration file.
sudo snort -c /etc/snort/snort.conf -TThis command will check your configuration file and prompt it if there is any misconfiguratioın in your current setting.
ubuntu@ip-10-10-218-177:~/Desktop$ sudo snort -c /etc/snort/snort.conf -T
Running in Test mode
--== Initializing Snort ==--
Initializing Output Plugins!
Initializing Preprocessors!
Initializing Plug-ins!
Parsing Rules file "/etc/snort/snort.conf"
PortVar 'HTTP_PORTS' defined : [ 80:81 311 383 591 593 901 1220 1414 1741 1830 2301 2381 2809 3037 3128 3702 4343 4848 5250 6988 7000:7001 7144:7145 7510 7777 7779 8000 8008 8014 8028 8080 8085 8088 8090 8118 8123 8180:8181 8243 8280 8300 8800 8888 8899 9000 9060 9080 9090:9091 9443 9999 11371 34443:34444 41080 50002 55555 ]
PortVar 'SHELLCODE_PORTS' defined : [ 0:79 81:65535 ]
PortVar 'ORACLE_PORTS' defined : [ 1024:65535 ]
PortVar 'SSH_PORTS' defined : [ 22 ]
PortVar 'FTP_PORTS' defined : [ 21 2100 3535 ]
PortVar 'SIP_PORTS' defined : [ 5060:5061 5600 ]
PortVar 'FILE_DATA_PORTS' defined : [ 80:81 110 143 311 383 591 593 901 1220 1414 1741 1830 2301 2381 2809 3037 3128 3702 4343 4848 5250 6988 7000:7001 7144:7145 7510 7777 7779 8000 8008 8014 8028 8080 8085 8088 8090 8118 8123 8180:8181 8243 8280 8300 8800 8888 8899 9000 9060 9080 9090:9091 9443 9999 11371 34443:34444 41080 50002 55555 ]
PortVar 'GTP_PORTS' defined : [ 2123 2152 3386 ]
Detection:
Search-Method = AC-Full-Q
Split Any/Any group = enabled
Search-Method-Optimizations = enabled
Maximum pattern length = 20
Tagged Packet Limit: 256
Loading dynamic engine /usr/lib/snort_dynamicengine/libsf_engine.so... done
Loading all dynamic detection libs from /usr/lib/snort_dynamicrules...
WARNING: No dynamic libraries found in directory /usr/lib/snort_dynamicrules.
Finished Loading all dynamic detection libs from /usr/lib/snort_dynamicrules
Loading all dynamic preprocessor libs from /usr/lib/snort_dynamicpreprocessor/...
Loading dynamic preprocessor library /usr/lib/snort_dynamicpreprocessor//libsf_ssl_preproc.so... done
Loading dynamic preprocessor library /usr/lib/snort_dynamicpreprocessor//libsf_sip_preproc.so... done
Loading dynamic preprocessor library /usr/lib/snort_dynamicpreprocessor//libsf_imap_preproc.so... done
Loading dynamic preprocessor library /usr/lib/snort_dynamicpreprocessor//libsf_smtp_preproc.so... done
Loading dynamic preprocessor library /usr/lib/snort_dynamicpreprocessor//libsf_reputation_preproc.so... done
Loading dynamic preprocessor library /usr/lib/snort_dynamicpreprocessor//libsf_ftptelnet_preproc.so... done
Loading dynamic preprocessor library /usr/lib/snort_dynamicpreprocessor//libsf_dce2_preproc.so... done
Loading dynamic preprocessor library /usr/lib/snort_dynamicpreprocessor//libsf_sdf_preproc.so... done
Loading dynamic preprocessor library /usr/lib/snort_dynamicpreprocessor//libsf_modbus_preproc.so... done
Loading dynamic preprocessor library /usr/lib/snort_dynamicpreprocessor//libsf_gtp_preproc.so... done
Loading dynamic preprocessor library /usr/lib/snort_dynamicpreprocessor//libsf_dns_preproc.so... done
Loading dynamic preprocessor library /usr/lib/snort_dynamicpreprocessor//libsf_dnp3_preproc.so... done
Loading dynamic preprocessor library /usr/lib/snort_dynamicpreprocessor//libsf_ssh_preproc.so... done
Loading dynamic preprocessor library /usr/lib/snort_dynamicpreprocessor//libsf_pop_preproc.so... done
Finished Loading all dynamic preprocessor libs from /usr/lib/snort_dynamicpreprocessor/
Log directory = /var/log/snort
WARNING: ip4 normalizations disabled because not inline.
WARNING: tcp normalizations disabled because not inline.
WARNING: icmp4 normalizations disabled because not inline.
WARNING: ip6 normalizations disabled because not inline.
WARNING: icmp6 normalizations disabled because not inline.
Frag3 global config:
Max frags: 65536
Fragment memory cap: 4194304 bytes
Frag3 engine config:
Bound Address: default
Target-based policy: WINDOWS
Fragment timeout: 180 seconds
Fragment min_ttl: 1
Fragment Anomalies: Alert
Overlap Limit: 10
Min fragment Length: 100
Max Expected Streams: 768
Stream global config:
Track TCP sessions: ACTIVE
Max TCP sessions: 262144
TCP cache pruning timeout: 30 seconds
TCP cache nominal timeout: 3600 seconds
Memcap (for reassembly packet storage): 8388608
Track UDP sessions: ACTIVE
Max UDP sessions: 131072
UDP cache pruning timeout: 30 seconds
UDP cache nominal timeout: 180 seconds
Track ICMP sessions: INACTIVE
Track IP sessions: INACTIVE
Log info if session memory consumption exceeds 1048576
Send up to 2 active responses
Wait at least 5 seconds between responses
Protocol Aware Flushing: ACTIVE
Maximum Flush Point: 16000
Stream TCP Policy config:
Bound Address: default
Reassembly Policy: WINDOWS
Timeout: 180 seconds
Limit on TCP Overlaps: 10
Maximum number of bytes to queue per session: 1048576
Maximum number of segs to queue per session: 2621
Options:
Require 3-Way Handshake: YES
3-Way Handshake Timeout: 180
Detect Anomalies: YES
Reassembly Ports:
21 client (Footprint)
22 client (Footprint)
23 client (Footprint)
25 client (Footprint)
42 client (Footprint)
53 client (Footprint)
79 client (Footprint)
80 client (Footprint) server (Footprint)
81 client (Footprint) server (Footprint)
109 client (Footprint)
110 client (Footprint)
111 client (Footprint)
113 client (Footprint)
119 client (Footprint)
135 client (Footprint)
136 client (Footprint)
137 client (Footprint)
139 client (Footprint)
143 client (Footprint)
161 client (Footprint)
additional ports configured but not printed.
Stream UDP Policy config:
Timeout: 180 seconds
HttpInspect Config:
GLOBAL CONFIG
Detect Proxy Usage: NO
IIS Unicode Map Filename: /etc/snort/unicode.map
IIS Unicode Map Codepage: 1252
Memcap used for logging URI and Hostname: 150994944
Max Gzip Memory: 104857600
Max Gzip Sessions: 201649
Gzip Compress Depth: 65535
Gzip Decompress Depth: 65535
DEFAULT SERVER CONFIG:
Server profile: All
Ports (PAF): 80 81 311 383 591 593 901 1220 1414 1741 1830 2301 2381 2809 3037 3128 3702 4343 4848 5250 6988 7000 7001 7144 7145 7510 7777 7779 8000 8008 8014 8028 8080 8085 8088 8090 8118 8123 8180 8181 8243 8280 8300 8800 8888 8899 9000 9060 9080 9090 9091 9443 9999 11371 34443 34444 41080 50002 55555
Server Flow Depth: 0
Client Flow Depth: 0
Max Chunk Length: 500000
Small Chunk Length Evasion: chunk size <= 10, threshold >= 5 times
Max Header Field Length: 750
Max Number Header Fields: 100
Max Number of WhiteSpaces allowed with header folding: 200
Inspect Pipeline Requests: YES
URI Discovery Strict Mode: NO
Allow Proxy Usage: NO
Disable Alerting: NO
Oversize Dir Length: 500
Only inspect URI: NO
Normalize HTTP Headers: NO
Inspect HTTP Cookies: YES
Inspect HTTP Responses: YES
Extract Gzip from responses: YES
Decompress response files:
Unlimited decompression of gzip data from responses: YES
Normalize Javascripts in HTTP Responses: YES
Max Number of WhiteSpaces allowed with Javascript Obfuscation in HTTP responses: 200
Normalize HTTP Cookies: NO
Enable XFF and True Client IP: NO
Log HTTP URI data: NO
Log HTTP Hostname data: NO
Extended ASCII code support in URI: NO
Ascii: YES alert: NO
Double Decoding: YES alert: NO
%U Encoding: YES alert: YES
Bare Byte: YES alert: NO
UTF 8: YES alert: NO
IIS Unicode: YES alert: NO
Multiple Slash: YES alert: NO
IIS Backslash: YES alert: NO
Directory Traversal: YES alert: NO
Web Root Traversal: YES alert: NO
Apache WhiteSpace: YES alert: NO
IIS Delimiter: YES alert: NO
IIS Unicode Map: GLOBAL IIS UNICODE MAP CONFIG
Non-RFC Compliant Characters: 0x00 0x01 0x02 0x03 0x04 0x05 0x06 0x07
Whitespace Characters: 0x09 0x0b 0x0c 0x0d
rpc_decode arguments:
Ports to decode RPC on: 111 32770 32771 32772 32773 32774 32775 32776 32777 32778 32779
alert_fragments: INACTIVE
alert_large_fragments: INACTIVE
alert_incomplete: INACTIVE
alert_multiple_requests: INACTIVE
FTPTelnet Config:
GLOBAL CONFIG
Inspection Type: stateful
Check for Encrypted Traffic: YES alert: NO
Continue to check encrypted data: YES
TELNET CONFIG:
Ports: 23
Are You There Threshold: 20
Normalize: YES
Detect Anomalies: YES
FTP CONFIG:
FTP Server: default
Ports (PAF): 21 2100 3535
Check for Telnet Cmds: YES alert: YES
Ignore Telnet Cmd Operations: YES alert: YES
Ignore open data channels: NO
FTP Client: default
Check for Bounce Attacks: YES alert: YES
Check for Telnet Cmds: YES alert: YES
Ignore Telnet Cmd Operations: YES alert: YES
Max Response Length: 256
SMTP Config:
Ports: 25 465 587 691
Inspection Type: Stateful
Normalize: ATRN AUTH BDAT DATA DEBUG EHLO EMAL ESAM ESND ESOM ETRN EVFY EXPN HELO HELP IDENT MAIL NOOP ONEX QUEU QUIT RCPT RSET SAML SEND STARTTLS SOML TICK TIME TURN TURNME VERB VRFY X-EXPS XADR XAUTH XCIR XEXCH50 XGEN XLICENSE X-LINK2STATE XQUE XSTA XTRN XUSR CHUNKING X-ADAT X-DRCP X-ERCP X-EXCH50
Ignore Data: No
Ignore TLS Data: No
Ignore SMTP Alerts: No
Max Command Line Length: 512
Max Specific Command Line Length:
ATRN:255 AUTH:246 BDAT:255 DATA:246 DEBUG:255
EHLO:500 EMAL:255 ESAM:255 ESND:255 ESOM:255
ETRN:246 EVFY:255 EXPN:255 HELO:500 HELP:500
IDENT:255 MAIL:260 NOOP:255 ONEX:246 QUEU:246
QUIT:246 RCPT:300 RSET:246 SAML:246 SEND:246
SIZE:255 STARTTLS:246 SOML:246 TICK:246 TIME:246
TURN:246 TURNME:246 VERB:246 VRFY:255 X-EXPS:246
XADR:246 XAUTH:246 XCIR:246 XEXCH50:246 XGEN:246
XLICENSE:246 X-LINK2STATE:246 XQUE:246 XSTA:246 XTRN:246
XUSR:246
Max Header Line Length: 1000
Max Response Line Length: 512
X-Link2State Alert: Yes
Drop on X-Link2State Alert: No
Alert on commands: None
Alert on unknown commands: No
SMTP Memcap: 838860
MIME Max Mem: 838860
Base64 Decoding: Enabled
Base64 Decoding Depth: Unlimited
Quoted-Printable Decoding: Enabled
Quoted-Printable Decoding Depth: Unlimited
Unix-to-Unix Decoding: Enabled
Unix-to-Unix Decoding Depth: Unlimited
Non-Encoded MIME attachment Extraction: Enabled
Non-Encoded MIME attachment Extraction Depth: Unlimited
Log Attachment filename: Enabled
Log MAIL FROM Address: Enabled
Log RCPT TO Addresses: Enabled
Log Email Headers: Enabled
Email Hdrs Log Depth: 1464
SSH config:
Autodetection: ENABLED
Challenge-Response Overflow Alert: ENABLED
SSH1 CRC32 Alert: ENABLED
Server Version String Overflow Alert: ENABLED
Protocol Mismatch Alert: ENABLED
Bad Message Direction Alert: DISABLED
Bad Payload Size Alert: DISABLED
Unrecognized Version Alert: DISABLED
Max Encrypted Packets: 20
Max Server Version String Length: 100
MaxClientBytes: 19600 (Default)
Ports:
22
DCE/RPC 2 Preprocessor Configuration
Global Configuration
DCE/RPC Defragmentation: Enabled
Memcap: 102400 KB
Events: co
SMB Fingerprint policy: Disabled
Server Default Configuration
Policy: WinXP
Detect ports (PAF)
SMB: 139 445
TCP: 135
UDP: 135
RPC over HTTP server: 593
RPC over HTTP proxy: None
Autodetect ports (PAF)
SMB: None
TCP: 1025-65535
UDP: 1025-65535
RPC over HTTP server: 1025-65535
RPC over HTTP proxy: None
Invalid SMB shares: C$ D$ ADMIN$
Maximum SMB command chaining: 3 commands
SMB file inspection: Disabled
DNS config:
DNS Client rdata txt Overflow Alert: ACTIVE
Obsolete DNS RR Types Alert: INACTIVE
Experimental DNS RR Types Alert: INACTIVE
Ports: 53
SSLPP config:
Encrypted packets: not inspected
Ports:
443 465 563 636 989
992 993 994 995 7801
7802 7900 7901 7902 7903
7904 7905 7906 7907 7908
7909 7910 7911 7912 7913
7914 7915 7916 7917 7918
7919 7920
Server side data is trusted
Maximum SSL Heartbeat length: 0
Sensitive Data preprocessor config:
Global Alert Threshold: 25
Masked Output: DISABLED
SIP config:
Max number of sessions: 40000
Max number of dialogs in a session: 4 (Default)
Status: ENABLED
Ignore media channel: DISABLED
Max URI length: 512
Max Call ID length: 80
Max Request name length: 20 (Default)
Max From length: 256 (Default)
Max To length: 256 (Default)
Max Via length: 1024 (Default)
Max Contact length: 512
Max Content length: 2048
Ports:
5060 5061 5600
Methods:
invite cancel ack bye register options refer subscribe update join info message notify benotify do qauth sprack publish service unsubscribe prack
IMAP Config:
Ports: 143
IMAP Memcap: 838860
MIME Max Mem: 838860
Base64 Decoding: Enabled
Base64 Decoding Depth: Unlimited
Quoted-Printable Decoding: Enabled
Quoted-Printable Decoding Depth: Unlimited
Unix-to-Unix Decoding: Enabled
Unix-to-Unix Decoding Depth: Unlimited
Non-Encoded MIME attachment Extraction: Enabled
Non-Encoded MIME attachment Extraction Depth: Unlimited
POP Config:
Ports: 110
POP Memcap: 838860
MIME Max Mem: 838860
Base64 Decoding: Enabled
Base64 Decoding Depth: Unlimited
Quoted-Printable Decoding: Enabled
Quoted-Printable Decoding Depth: Unlimited
Unix-to-Unix Decoding: Enabled
Unix-to-Unix Decoding Depth: Unlimited
Non-Encoded MIME attachment Extraction: Enabled
Non-Encoded MIME attachment Extraction Depth: Unlimited
Modbus config:
Ports:
502
DNP3 config:
Memcap: 262144
Check Link-Layer CRCs: ENABLED
Ports:
20000
+++++++++++++++++++++++++++++++++++++++++++++++++++
Initializing rule chains...
WARNING: /etc/snort/rules/chat.rules(33) threshold (in rule) is deprecated; use detection_filter instead.
WARNING: /etc/snort/rules/community-sql-injection.rules(6) GID 1 SID 100000106 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-sql-injection.rules(7) GID 1 SID 100000107 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-sql-injection.rules(8) GID 1 SID 100000108 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-sql-injection.rules(9) GID 1 SID 100000109 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-sql-injection.rules(11) GID 1 SID 100000192 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-sql-injection.rules(12) GID 1 SID 100000193 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-sql-injection.rules(13) GID 1 SID 100000194 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-sql-injection.rules(14) GID 1 SID 100000690 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-sql-injection.rules(15) GID 1 SID 100000691 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-client.rules(6) GID 1 SID 100000118 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-client.rules(7) GID 1 SID 100000119 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-client.rules(9) GID 1 SID 100000228 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-client.rules(14) GID 1 SID 100000284 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-client.rules(16) GID 1 SID 100000447 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-client.rules(18) GID 1 SID 100000692 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-client.rules(20) GID 1 SID 100000693 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-client.rules(23) GID 1 SID 100000864 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-iis.rules(7) GID 1 SID 100000138 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-iis.rules(8) GID 1 SID 100000139 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-iis.rules(9) GID 1 SID 100000173 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-iis.rules(10) GID 1 SID 100000174 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(6) GID 1 SID 100000121 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(7) GID 1 SID 100000122 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(8) GID 1 SID 100000129 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(9) GID 1 SID 100000130 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(10) GID 1 SID 100000131 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(12) GID 1 SID 100000132 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(13) GID 1 SID 100000133 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(14) GID 1 SID 100000140 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(15) GID 1 SID 100000141 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(16) GID 1 SID 100000142 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(17) GID 1 SID 100000143 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(18) GID 1 SID 100000144 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(19) GID 1 SID 100000145 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(20) GID 1 SID 100000146 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(22) GID 1 SID 100000148 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(23) GID 1 SID 100000149 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(24) GID 1 SID 100000150 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(25) GID 1 SID 100000177 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(26) GID 1 SID 100000178 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(27) GID 1 SID 100000179 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(28) GID 1 SID 100000184 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(29) GID 1 SID 100000185 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(30) GID 1 SID 100000200 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(31) GID 1 SID 100000209 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(33) GID 1 SID 100000216 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(34) GID 1 SID 100000217 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(35) GID 1 SID 100000225 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(38) GID 1 SID 100000237 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(39) GID 1 SID 100000302 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(40) GID 1 SID 100000303 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(42) GID 1 SID 100000313 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(43) GID 1 SID 100000314 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(49) GID 1 SID 100000317 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(50) GID 1 SID 100000318 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(51) GID 1 SID 100000319 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(52) GID 1 SID 100000320 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(53) GID 1 SID 100000321 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(54) GID 1 SID 100000322 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(55) GID 1 SID 100000323 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(56) GID 1 SID 100000324 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(57) GID 1 SID 100000325 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(58) GID 1 SID 100000326 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(59) GID 1 SID 100000327 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(60) GID 1 SID 100000328 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(61) GID 1 SID 100000329 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(62) GID 1 SID 100000330 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(63) GID 1 SID 100000331 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(64) GID 1 SID 100000332 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(65) GID 1 SID 100000333 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(66) GID 1 SID 100000334 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(67) GID 1 SID 100000335 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(68) GID 1 SID 100000336 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(69) GID 1 SID 100000337 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(70) GID 1 SID 100000338 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(71) GID 1 SID 100000339 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(72) GID 1 SID 100000340 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(73) GID 1 SID 100000341 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(74) GID 1 SID 100000342 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(75) GID 1 SID 100000343 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(76) GID 1 SID 100000344 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(77) GID 1 SID 100000345 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(78) GID 1 SID 100000346 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(79) GID 1 SID 100000347 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(80) GID 1 SID 100000348 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(81) GID 1 SID 100000349 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(82) GID 1 SID 100000350 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(83) GID 1 SID 100000351 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(84) GID 1 SID 100000352 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(85) GID 1 SID 100000353 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(86) GID 1 SID 100000354 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(87) GID 1 SID 100000355 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(88) GID 1 SID 100000356 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(89) GID 1 SID 100000357 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(90) GID 1 SID 100000358 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(91) GID 1 SID 100000359 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(92) GID 1 SID 100000360 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(93) GID 1 SID 100000361 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(94) GID 1 SID 100000362 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(95) GID 1 SID 100000363 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(96) GID 1 SID 100000364 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(97) GID 1 SID 100000365 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(98) GID 1 SID 100000366 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(99) GID 1 SID 100000367 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(100) GID 1 SID 100000368 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(101) GID 1 SID 100000369 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(102) GID 1 SID 100000370 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(103) GID 1 SID 100000371 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(104) GID 1 SID 100000372 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(105) GID 1 SID 100000373 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(106) GID 1 SID 100000374 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(107) GID 1 SID 100000375 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(108) GID 1 SID 100000376 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(109) GID 1 SID 100000377 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(110) GID 1 SID 100000378 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(111) GID 1 SID 100000379 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(112) GID 1 SID 100000380 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(113) GID 1 SID 100000382 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(114) GID 1 SID 100000383 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(115) GID 1 SID 100000384 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(116) GID 1 SID 100000385 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(117) GID 1 SID 100000386 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(119) GID 1 SID 100000387 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(120) GID 1 SID 100000388 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(121) GID 1 SID 100000389 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(122) GID 1 SID 100000390 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(123) GID 1 SID 100000391 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(124) GID 1 SID 100000392 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(125) GID 1 SID 100000393 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(126) GID 1 SID 100000394 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(127) GID 1 SID 100000395 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(128) GID 1 SID 100000396 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(129) GID 1 SID 100000397 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(130) GID 1 SID 100000398 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(131) GID 1 SID 100000399 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(132) GID 1 SID 100000400 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(133) GID 1 SID 100000401 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(134) GID 1 SID 100000402 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(135) GID 1 SID 100000403 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(136) GID 1 SID 100000404 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(137) GID 1 SID 100000405 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(138) GID 1 SID 100000406 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(139) GID 1 SID 100000407 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(140) GID 1 SID 100000408 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(141) GID 1 SID 100000409 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(142) GID 1 SID 100000410 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(143) GID 1 SID 100000411 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(144) GID 1 SID 100000412 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(145) GID 1 SID 100000413 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(146) GID 1 SID 100000414 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(147) GID 1 SID 100000415 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(148) GID 1 SID 100000416 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(149) GID 1 SID 100000417 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(150) GID 1 SID 100000418 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(151) GID 1 SID 100000419 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(152) GID 1 SID 100000420 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(153) GID 1 SID 100000421 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(154) GID 1 SID 100000422 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(155) GID 1 SID 100000423 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(156) GID 1 SID 100000424 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(157) GID 1 SID 100000425 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(158) GID 1 SID 100000426 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(161) GID 1 SID 100000427 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(162) GID 1 SID 100000428 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(163) GID 1 SID 100000429 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(166) GID 1 SID 100000430 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(167) GID 1 SID 100000431 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(168) GID 1 SID 100000432 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(169) GID 1 SID 100000433 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(170) GID 1 SID 100000434 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(171) GID 1 SID 100000435 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(172) GID 1 SID 100000436 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(173) GID 1 SID 100000437 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(174) GID 1 SID 100000438 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(175) GID 1 SID 100000439 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(176) GID 1 SID 100000440 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(177) GID 1 SID 100000441 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(178) GID 1 SID 100000442 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(179) GID 1 SID 100000443 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(180) GID 1 SID 100000444 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(181) GID 1 SID 100000448 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(182) GID 1 SID 100000449 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(183) GID 1 SID 100000450 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(184) GID 1 SID 100000451 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(185) GID 1 SID 100000452 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(186) GID 1 SID 100000453 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(187) GID 1 SID 100000454 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(188) GID 1 SID 100000455 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(189) GID 1 SID 100000456 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(190) GID 1 SID 100000457 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(191) GID 1 SID 100000458 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(192) GID 1 SID 100000459 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(193) GID 1 SID 100000460 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(194) GID 1 SID 100000461 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(195) GID 1 SID 100000462 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(196) GID 1 SID 100000694 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(197) GID 1 SID 100000695 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(198) GID 1 SID 100000696 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(199) GID 1 SID 100000697 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(200) GID 1 SID 100000698 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(201) GID 1 SID 100000699 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(202) GID 1 SID 100000700 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(203) GID 1 SID 100000701 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(204) GID 1 SID 100000702 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(207) GID 1 SID 100000890 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(208) GID 1 SID 100000891 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(211) GID 1 SID 100000895 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(212) GID 1 SID 100000896 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(213) GID 1 SID 100000897 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(214) GID 1 SID 100000898 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-misc.rules(215) GID 1 SID 100000899 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(6) GID 1 SID 100000151 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(7) GID 1 SID 100000186 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(8) GID 1 SID 100000187 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(9) GID 1 SID 100000188 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(10) GID 1 SID 100000195 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(11) GID 1 SID 100000201 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(12) GID 1 SID 100000202 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(13) GID 1 SID 100000203 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(14) GID 1 SID 100000204 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(15) GID 1 SID 100000205 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(16) GID 1 SID 100000206 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(17) GID 1 SID 100000211 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(18) GID 1 SID 100000212 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(19) GID 1 SID 100000213 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(20) GID 1 SID 100000214 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(21) GID 1 SID 100000218 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(22) GID 1 SID 100000220 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(23) GID 1 SID 100000221 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(24) GID 1 SID 100000285 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(25) GID 1 SID 100000286 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(26) GID 1 SID 100000287 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(27) GID 1 SID 100000288 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(28) GID 1 SID 100000289 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(29) GID 1 SID 100000290 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(30) GID 1 SID 100000291 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(31) GID 1 SID 100000292 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(32) GID 1 SID 100000293 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(33) GID 1 SID 100000294 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(34) GID 1 SID 100000295 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(35) GID 1 SID 100000296 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(36) GID 1 SID 100000297 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(37) GID 1 SID 100000298 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(38) GID 1 SID 100000299 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(39) GID 1 SID 100000300 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(40) GID 1 SID 100000304 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(41) GID 1 SID 100000305 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(42) GID 1 SID 100000306 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(43) GID 1 SID 100000307 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(44) GID 1 SID 100000308 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(45) GID 1 SID 100000309 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(46) GID 1 SID 100000445 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(48) GID 1 SID 100000463 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(49) GID 1 SID 100000464 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(50) GID 1 SID 100000465 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(51) GID 1 SID 100000466 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(52) GID 1 SID 100000467 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(53) GID 1 SID 100000468 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(54) GID 1 SID 100000469 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(55) GID 1 SID 100000470 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(56) GID 1 SID 100000471 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(57) GID 1 SID 100000472 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(58) GID 1 SID 100000473 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(59) GID 1 SID 100000474 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(60) GID 1 SID 100000475 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(61) GID 1 SID 100000476 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(62) GID 1 SID 100000477 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(63) GID 1 SID 100000478 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(64) GID 1 SID 100000479 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(65) GID 1 SID 100000480 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(66) GID 1 SID 100000481 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(67) GID 1 SID 100000482 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(68) GID 1 SID 100000483 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(69) GID 1 SID 100000484 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(70) GID 1 SID 100000485 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(71) GID 1 SID 100000486 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(72) GID 1 SID 100000487 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(73) GID 1 SID 100000488 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(74) GID 1 SID 100000489 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(75) GID 1 SID 100000490 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(76) GID 1 SID 100000491 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(77) GID 1 SID 100000492 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(78) GID 1 SID 100000493 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(79) GID 1 SID 100000494 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(80) GID 1 SID 100000495 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(81) GID 1 SID 100000496 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(82) GID 1 SID 100000497 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(83) GID 1 SID 100000498 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(84) GID 1 SID 100000499 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(85) GID 1 SID 100000500 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(86) GID 1 SID 100000501 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(87) GID 1 SID 100000502 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(88) GID 1 SID 100000503 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(89) GID 1 SID 100000504 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(90) GID 1 SID 100000505 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(91) GID 1 SID 100000506 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(92) GID 1 SID 100000507 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(93) GID 1 SID 100000508 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(94) GID 1 SID 100000509 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(95) GID 1 SID 100000510 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(96) GID 1 SID 100000511 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(97) GID 1 SID 100000512 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(98) GID 1 SID 100000513 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(99) GID 1 SID 100000514 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(100) GID 1 SID 100000515 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(101) GID 1 SID 100000516 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(102) GID 1 SID 100000517 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(103) GID 1 SID 100000518 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(104) GID 1 SID 100000519 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(105) GID 1 SID 100000520 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(106) GID 1 SID 100000521 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(107) GID 1 SID 100000522 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(108) GID 1 SID 100000523 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(109) GID 1 SID 100000524 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(110) GID 1 SID 100000525 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(111) GID 1 SID 100000526 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(112) GID 1 SID 100000527 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(113) GID 1 SID 100000528 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(114) GID 1 SID 100000529 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(115) GID 1 SID 100000530 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(116) GID 1 SID 100000531 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(117) GID 1 SID 100000532 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(118) GID 1 SID 100000533 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(119) GID 1 SID 100000534 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(120) GID 1 SID 100000535 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(121) GID 1 SID 100000536 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(122) GID 1 SID 100000537 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(123) GID 1 SID 100000538 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(124) GID 1 SID 100000539 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(125) GID 1 SID 100000540 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(126) GID 1 SID 100000541 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(127) GID 1 SID 100000542 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(128) GID 1 SID 100000543 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(129) GID 1 SID 100000544 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(130) GID 1 SID 100000545 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(131) GID 1 SID 100000546 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(132) GID 1 SID 100000547 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(133) GID 1 SID 100000548 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(134) GID 1 SID 100000549 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(135) GID 1 SID 100000550 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(136) GID 1 SID 100000551 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(137) GID 1 SID 100000552 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(138) GID 1 SID 100000553 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(139) GID 1 SID 100000554 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(140) GID 1 SID 100000555 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(141) GID 1 SID 100000556 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(142) GID 1 SID 100000557 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(143) GID 1 SID 100000558 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(144) GID 1 SID 100000559 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(145) GID 1 SID 100000560 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(146) GID 1 SID 100000561 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(147) GID 1 SID 100000562 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(148) GID 1 SID 100000563 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(149) GID 1 SID 100000564 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(150) GID 1 SID 100000565 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(151) GID 1 SID 100000566 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(152) GID 1 SID 100000567 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(153) GID 1 SID 100000568 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(154) GID 1 SID 100000569 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(155) GID 1 SID 100000570 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(156) GID 1 SID 100000571 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(157) GID 1 SID 100000572 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(158) GID 1 SID 100000573 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(159) GID 1 SID 100000574 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(160) GID 1 SID 100000575 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(161) GID 1 SID 100000576 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(162) GID 1 SID 100000577 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(163) GID 1 SID 100000578 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(164) GID 1 SID 100000579 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(165) GID 1 SID 100000580 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(166) GID 1 SID 100000581 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(167) GID 1 SID 100000582 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(168) GID 1 SID 100000583 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(169) GID 1 SID 100000584 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(170) GID 1 SID 100000585 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(171) GID 1 SID 100000586 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(172) GID 1 SID 100000587 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(173) GID 1 SID 100000588 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(174) GID 1 SID 100000589 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(175) GID 1 SID 100000590 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(176) GID 1 SID 100000591 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(177) GID 1 SID 100000592 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(178) GID 1 SID 100000593 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(179) GID 1 SID 100000594 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(180) GID 1 SID 100000595 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(181) GID 1 SID 100000596 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(182) GID 1 SID 100000597 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(183) GID 1 SID 100000598 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(184) GID 1 SID 100000599 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(185) GID 1 SID 100000600 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(186) GID 1 SID 100000601 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(187) GID 1 SID 100000602 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(188) GID 1 SID 100000603 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(189) GID 1 SID 100000604 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(190) GID 1 SID 100000605 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(191) GID 1 SID 100000606 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(192) GID 1 SID 100000607 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(193) GID 1 SID 100000608 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(194) GID 1 SID 100000609 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(195) GID 1 SID 100000610 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(196) GID 1 SID 100000611 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(197) GID 1 SID 100000612 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(198) GID 1 SID 100000613 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(199) GID 1 SID 100000614 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(200) GID 1 SID 100000615 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(201) GID 1 SID 100000616 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(202) GID 1 SID 100000617 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(203) GID 1 SID 100000618 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(204) GID 1 SID 100000619 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(205) GID 1 SID 100000620 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(206) GID 1 SID 100000621 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(207) GID 1 SID 100000622 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(208) GID 1 SID 100000623 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(209) GID 1 SID 100000624 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(210) GID 1 SID 100000625 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(211) GID 1 SID 100000626 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(212) GID 1 SID 100000627 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(213) GID 1 SID 100000628 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(214) GID 1 SID 100000629 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(215) GID 1 SID 100000630 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(216) GID 1 SID 100000631 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(217) GID 1 SID 100000632 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(218) GID 1 SID 100000633 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(219) GID 1 SID 100000634 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(220) GID 1 SID 100000635 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(221) GID 1 SID 100000636 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(222) GID 1 SID 100000637 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(223) GID 1 SID 100000638 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(224) GID 1 SID 100000639 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(225) GID 1 SID 100000640 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(226) GID 1 SID 100000641 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(227) GID 1 SID 100000642 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(228) GID 1 SID 100000643 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(229) GID 1 SID 100000644 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(230) GID 1 SID 100000645 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(231) GID 1 SID 100000646 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(232) GID 1 SID 100000647 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(233) GID 1 SID 100000648 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(234) GID 1 SID 100000649 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(235) GID 1 SID 100000650 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(236) GID 1 SID 100000651 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(237) GID 1 SID 100000652 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(238) GID 1 SID 100000653 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(239) GID 1 SID 100000654 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(240) GID 1 SID 100000655 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(241) GID 1 SID 100000656 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(242) GID 1 SID 100000657 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(243) GID 1 SID 100000658 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(244) GID 1 SID 100000659 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(245) GID 1 SID 100000660 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(246) GID 1 SID 100000661 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(247) GID 1 SID 100000662 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(248) GID 1 SID 100000663 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(249) GID 1 SID 100000664 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(250) GID 1 SID 100000665 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(251) GID 1 SID 100000666 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(252) GID 1 SID 100000667 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(253) GID 1 SID 100000668 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(254) GID 1 SID 100000669 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(255) GID 1 SID 100000670 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(256) GID 1 SID 100000671 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(257) GID 1 SID 100000672 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(258) GID 1 SID 100000673 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(259) GID 1 SID 100000674 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(260) GID 1 SID 100000675 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(261) GID 1 SID 100000676 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(262) GID 1 SID 100000677 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(263) GID 1 SID 100000678 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(264) GID 1 SID 100000679 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(265) GID 1 SID 100000680 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(266) GID 1 SID 100000681 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(267) GID 1 SID 100000682 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(268) GID 1 SID 100000683 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(270) GID 1 SID 100000703 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(271) GID 1 SID 100000704 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(272) GID 1 SID 100000705 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(273) GID 1 SID 100000706 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(274) GID 1 SID 100000707 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(275) GID 1 SID 100000708 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(276) GID 1 SID 100000709 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(277) GID 1 SID 100000710 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(278) GID 1 SID 100000711 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(279) GID 1 SID 100000712 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(280) GID 1 SID 100000713 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(281) GID 1 SID 100000714 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(282) GID 1 SID 100000715 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(283) GID 1 SID 100000716 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(284) GID 1 SID 100000717 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(285) GID 1 SID 100000718 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(286) GID 1 SID 100000719 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(287) GID 1 SID 100000720 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(288) GID 1 SID 100000721 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(289) GID 1 SID 100000722 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(290) GID 1 SID 100000723 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(291) GID 1 SID 100000724 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(292) GID 1 SID 100000725 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(293) GID 1 SID 100000726 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(294) GID 1 SID 100000727 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(295) GID 1 SID 100000728 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(296) GID 1 SID 100000729 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(297) GID 1 SID 100000730 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(298) GID 1 SID 100000731 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(299) GID 1 SID 100000732 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(300) GID 1 SID 100000733 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(301) GID 1 SID 100000734 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(302) GID 1 SID 100000735 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(303) GID 1 SID 100000736 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(304) GID 1 SID 100000737 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(305) GID 1 SID 100000738 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(306) GID 1 SID 100000739 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(307) GID 1 SID 100000740 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(308) GID 1 SID 100000741 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(309) GID 1 SID 100000742 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(310) GID 1 SID 100000743 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(311) GID 1 SID 100000744 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(312) GID 1 SID 100000745 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(313) GID 1 SID 100000746 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(314) GID 1 SID 100000747 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(315) GID 1 SID 100000748 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(316) GID 1 SID 100000749 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(317) GID 1 SID 100000750 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(318) GID 1 SID 100000751 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(319) GID 1 SID 100000752 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(320) GID 1 SID 100000753 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(321) GID 1 SID 100000754 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(322) GID 1 SID 100000755 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(323) GID 1 SID 100000756 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(324) GID 1 SID 100000757 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(325) GID 1 SID 100000758 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(326) GID 1 SID 100000759 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(327) GID 1 SID 100000760 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(328) GID 1 SID 100000761 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(329) GID 1 SID 100000762 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(330) GID 1 SID 100000763 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(331) GID 1 SID 100000764 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(332) GID 1 SID 100000765 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(333) GID 1 SID 100000766 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(334) GID 1 SID 100000767 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(335) GID 1 SID 100000768 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(336) GID 1 SID 100000769 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(337) GID 1 SID 100000770 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(338) GID 1 SID 100000771 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(339) GID 1 SID 100000772 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(340) GID 1 SID 100000773 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(341) GID 1 SID 100000774 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(342) GID 1 SID 100000775 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(343) GID 1 SID 100000776 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(344) GID 1 SID 100000777 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(345) GID 1 SID 100000778 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(346) GID 1 SID 100000779 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(347) GID 1 SID 100000780 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(348) GID 1 SID 100000781 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(349) GID 1 SID 100000782 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(350) GID 1 SID 100000783 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(351) GID 1 SID 100000784 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(352) GID 1 SID 100000785 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(353) GID 1 SID 100000786 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(354) GID 1 SID 100000787 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(355) GID 1 SID 100000788 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(356) GID 1 SID 100000789 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(357) GID 1 SID 100000790 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(358) GID 1 SID 100000791 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(359) GID 1 SID 100000792 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(360) GID 1 SID 100000793 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(361) GID 1 SID 100000794 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(362) GID 1 SID 100000795 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(363) GID 1 SID 100000796 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(364) GID 1 SID 100000797 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(365) GID 1 SID 100000798 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(366) GID 1 SID 100000799 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(367) GID 1 SID 100000800 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(368) GID 1 SID 100000801 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(369) GID 1 SID 100000802 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(370) GID 1 SID 100000803 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(371) GID 1 SID 100000804 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(372) GID 1 SID 100000805 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(373) GID 1 SID 100000806 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(374) GID 1 SID 100000807 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(375) GID 1 SID 100000808 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(376) GID 1 SID 100000809 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(377) GID 1 SID 100000810 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(378) GID 1 SID 100000811 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(379) GID 1 SID 100000812 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(380) GID 1 SID 100000813 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(381) GID 1 SID 100000814 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(382) GID 1 SID 100000815 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(383) GID 1 SID 100000816 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(384) GID 1 SID 100000817 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(385) GID 1 SID 100000818 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(386) GID 1 SID 100000820 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(387) GID 1 SID 100000821 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(388) GID 1 SID 100000822 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(389) GID 1 SID 100000823 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(390) GID 1 SID 100000824 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(391) GID 1 SID 100000825 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(392) GID 1 SID 100000826 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(393) GID 1 SID 100000827 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(394) GID 1 SID 100000828 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(395) GID 1 SID 100000829 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(396) GID 1 SID 100000830 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(397) GID 1 SID 100000831 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(398) GID 1 SID 100000832 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(399) GID 1 SID 100000833 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(400) GID 1 SID 100000834 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(401) GID 1 SID 100000835 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(402) GID 1 SID 100000836 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(403) GID 1 SID 100000837 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(404) GID 1 SID 100000838 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(405) GID 1 SID 100000839 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(406) GID 1 SID 100000840 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(407) GID 1 SID 100000841 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(408) GID 1 SID 100000842 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(409) GID 1 SID 100000843 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(410) GID 1 SID 100000844 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(411) GID 1 SID 100000845 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(412) GID 1 SID 100000846 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(413) GID 1 SID 100000847 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(414) GID 1 SID 100000849 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(415) GID 1 SID 100000850 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(416) GID 1 SID 100000851 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(417) GID 1 SID 100000852 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(418) GID 1 SID 100000853 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(419) GID 1 SID 100000854 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(420) GID 1 SID 100000855 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(421) GID 1 SID 100000856 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(422) GID 1 SID 100000857 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(423) GID 1 SID 100000858 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(424) GID 1 SID 100000859 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(425) GID 1 SID 100000860 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(426) GID 1 SID 100000861 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(427) GID 1 SID 100000862 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(428) GID 1 SID 100000863 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(431) GID 1 SID 100000865 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(432) GID 1 SID 100000866 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(433) GID 1 SID 100000867 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(434) GID 1 SID 100000868 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(435) GID 1 SID 100000869 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(436) GID 1 SID 100000870 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(437) GID 1 SID 100000871 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(438) GID 1 SID 100000872 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(439) GID 1 SID 100000873 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(441) GID 1 SID 100000882 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(443) GID 1 SID 100000883 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(444) GID 1 SID 100000884 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(445) GID 1 SID 100000885 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(446) GID 1 SID 100000886 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(447) GID 1 SID 100000887 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(448) GID 1 SID 100000888 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(449) GID 1 SID 100000889 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(450) GID 1 SID 100000906 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(451) GID 1 SID 100000907 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(452) GID 1 SID 100000908 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(453) GID 1 SID 100000909 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(454) GID 1 SID 100000910 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(455) GID 1 SID 100000911 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(456) GID 1 SID 100000912 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(457) GID 1 SID 100000913 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(458) GID 1 SID 100000914 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(459) GID 1 SID 100000915 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(460) GID 1 SID 100000916 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(461) GID 1 SID 100000917 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(462) GID 1 SID 100000918 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(463) GID 1 SID 100000919 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(464) GID 1 SID 100000920 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(465) GID 1 SID 100000921 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(466) GID 1 SID 100000922 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(467) GID 1 SID 100000925 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(468) GID 1 SID 100000926 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(469) GID 1 SID 100000929 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(470) GID 1 SID 100000930 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(471) GID 1 SID 100000931 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(472) GID 1 SID 100000932 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(473) GID 1 SID 100000933 in rule duplicates previous rule. Ignoring old rule.
WARNING: /etc/snort/rules/community-web-php.rules(474) GID 1 SID 100000934 in rule duplicates previous rule. Ignoring old rule.
4151 Snort rules read
3477 detection rules
0 decoder rules
0 preprocessor rules
3477 Option Chains linked into 271 Chain Headers
0 Dynamic rules
+++++++++++++++++++++++++++++++++++++++++++++++++++
+-------------------[Rule Port Counts]---------------------------------------
| tcp udp icmp ip
| src 151 18 0 0
| dst 3306 126 0 0
| any 383 48 146 22
| nc 27 8 95 20
| s+d 12 5 0 0
+----------------------------------------------------------------------------
+-----------------------[detection-filter-config]------------------------------
| memory-cap : 1048576 bytes
+-----------------------[detection-filter-rules]-------------------------------
| none
-------------------------------------------------------------------------------
+-----------------------[rate-filter-config]-----------------------------------
| memory-cap : 1048576 bytes
+-----------------------[rate-filter-rules]------------------------------------
| none
-------------------------------------------------------------------------------
+-----------------------[event-filter-config]----------------------------------
| memory-cap : 1048576 bytes
+-----------------------[event-filter-global]----------------------------------
| none
+-----------------------[event-filter-local]-----------------------------------
| gen-id=1 sig-id=2923 type=Threshold tracking=dst count=10 seconds=60
| gen-id=1 sig-id=2523 type=Both tracking=dst count=10 seconds=10
| gen-id=1 sig-id=1991 type=Limit tracking=src count=1 seconds=60
| gen-id=1 sig-id=2275 type=Threshold tracking=dst count=5 seconds=60
| gen-id=1 sig-id=3273 type=Threshold tracking=src count=5 seconds=2
| gen-id=1 sig-id=2495 type=Both tracking=dst count=20 seconds=60
| gen-id=1 sig-id=2924 type=Threshold tracking=dst count=10 seconds=60
| gen-id=1 sig-id=2494 type=Both tracking=dst count=20 seconds=60
| gen-id=1 sig-id=3152 type=Threshold tracking=src count=5 seconds=2
| gen-id=1 sig-id=2496 type=Both tracking=dst count=20 seconds=60
+-----------------------[suppression]------------------------------------------
| none
-------------------------------------------------------------------------------
Rule application order: activation->dynamic->pass->drop->sdrop->reject->alert->log
Verifying Preprocessor Configurations!
WARNING: flowbits key 'smb.tree.create.llsrpc' is set but not ever checked.
WARNING: flowbits key 'ms_sql_seen_dns' is checked but not ever set.
33 out of 1024 flowbits in use.
[ Port Based Pattern Matching Memory ]
+- [ Aho-Corasick Summary ] -------------------------------------
| Storage Format : Full-Q
| Finite Automaton : DFA
| Alphabet Size : 256 Chars
| Sizeof State : Variable (1,2,4 bytes)
| Instances : 215
| 1 byte states : 204
| 2 byte states : 11
| 4 byte states : 0
| Characters : 64982
| States : 32135
| Transitions : 872051
| State Density : 10.6%
| Patterns : 5055
| Match States : 3855
| Memory (MB) : 17.00
| Patterns : 0.51
| Match Lists : 1.02
| DFA
| 1 byte states : 1.02
| 2 byte states : 14.05
| 4 byte states : 0.00
+----------------------------------------------------------------
[ Number of patterns truncated to 20 bytes: 1039 ]
--== Initialization Complete ==--
,,_ -*> Snort! <*-
o" )~ Version 2.9.7.0 GRE (Build 149)
'''' By Martin Roesch & The Snort Team: http://www.snort.org/contact#team
Copyright (C) 2014 Cisco and/or its affiliates. All rights reserved.
Copyright (C) 1998-2013 Sourcefire, Inc., et al.
Using libpcap version 1.9.1 (with TPACKET_V3)
Using PCRE version: 8.39 2016-06-14
Using ZLIB version: 1.2.11
Rules Engine: SF_SNORT_DETECTION_ENGINE Version 2.4 <Build 1>
Preprocessor Object: SF_POP Version 1.0 <Build 1>
Preprocessor Object: SF_SSH Version 1.1 <Build 3>
Preprocessor Object: SF_DNP3 Version 1.1 <Build 1>
Preprocessor Object: SF_DNS Version 1.1 <Build 4>
Preprocessor Object: SF_GTP Version 1.1 <Build 1>
Preprocessor Object: SF_MODBUS Version 1.1 <Build 1>
Preprocessor Object: SF_SDF Version 1.1 <Build 1>
Preprocessor Object: SF_DCERPC2 Version 1.0 <Build 3>
Preprocessor Object: SF_FTPTELNET Version 1.2 <Build 13>
Preprocessor Object: SF_REPUTATION Version 1.1 <Build 1>
Preprocessor Object: SF_SMTP Version 1.1 <Build 9>
Preprocessor Object: SF_IMAP Version 1.0 <Build 1>
Preprocessor Object: SF_SIP Version 1.1 <Build 1>
Preprocessor Object: SF_SSLPP Version 1.1 <Build 4>
Snort successfully validated the configuration!
Snort exitingIDS/IPS mode with parameter “-N”
Start the Snort instance and disable logging by running the following command:
sudo snort -c /etc/snort/snort.conf -NThis command will disable logging mode. The rest of the other functions will still be available (if activated).
The command-line output will provide the information requested with the parameters. So, if you activate verbosity (-v) or full packet dump (-X) you will still have the output in the console, but there will be no logs in the log folder.
IDS/IPS mode with parameter “-D”
Start the Snort instance in background mode with the following command:
sudo snort -c /etc/snort/snort.conf -DThe command-line output will provide the information requested with the parameters. So, if you activate verbosity (-v) or full packet dump (-X) with packet logger mode (-l) you will still have the logs in the logs folder, but there will be no output in the console.
Use “ps” command to check the running process.
ps -ef | grep snortUse the “kill” command to stop the process.
sudo kill -9 2898Note that daemon mode is mainly used to automate the Snort. This parameter is mainly used in scripts to start the Snort service in the background. It is not recommended to use this mode unless you have a working knowledge of Snort and stable configuration.
Link to the PART II of the series.



