Views: 35
Cyber Kill Chain Official Page: https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html
Cyber Kill Chain is a framework created by Lockheed Martin in 2011 and used to model the attacks of attackers. Within this framework, attacker behaviors and the whole cyber attack process consists of 7 steps that follow one another.
Cyber Kill Chain is important for the SOC analyst to have a better understanding of the stages of a cyber attack and to determine which action(s) the cyber attack starts with and which action(s) follows. The SOC analyst can use Cyber Kill Chain to analyze where in the cyber attack the acts of the attacker noticed on the systems occur. The Cyber Kill Chain enables the organization to determine where and how severe the security flaws are. Blueteams can identify areas where security measures are lacking based on these flaws and take the appropriate actions
Cyber Kill chain Stages
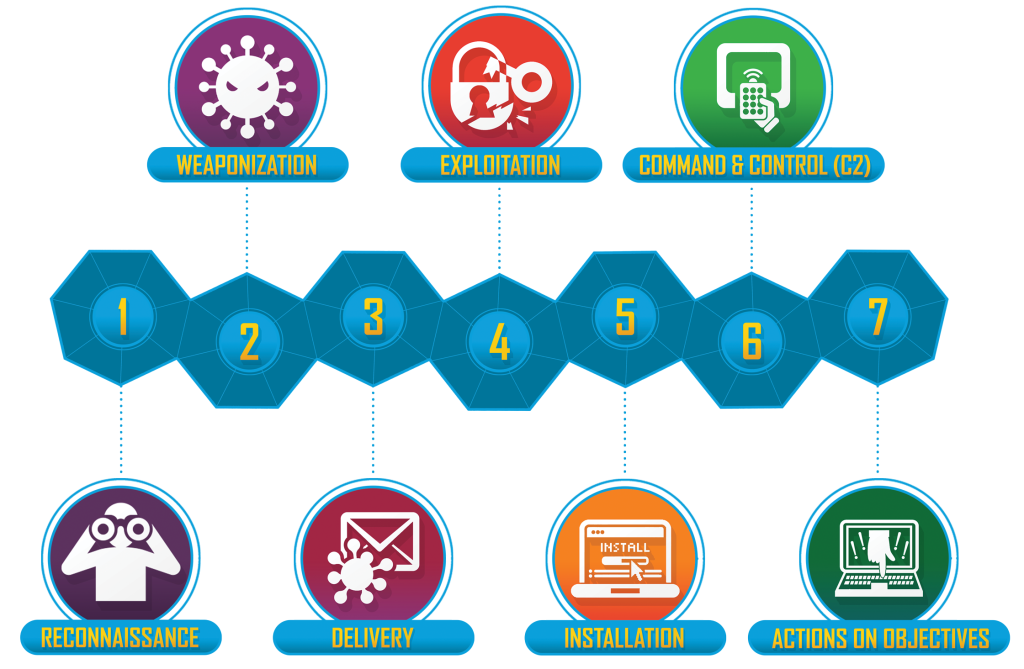
Reconnaissance
The attacker attempts to obtain information about the target system at this step. The more knowledge an attacker has about the target system, the more the attack surface seems to him. Attack vectors for the target are disclosed in this way. The techniques employed at this stage may be divided into two subcategories:
- Passive Reconnaissance
- Active Reconnaissance
The term “Passive Reconnaissance” refers to the collecting of information from sources about the target system without physically engaging with the target system. As an instance of this, Web archive websites can be used to obtain information that is no longer available on the target system’s website.
“Active Reconnaissance” refers to the method of acquiring information about a target system by engaging with it directly. By submitting a request to a web server, for instance, version information about the web server may be acquired from the response.
Weaponization
The “Weaponization” is the second step in the Cyber Kill Chain. At this stage, the attacker uses the information obtained in the previous stage to access the tools needed for the attack or develops the tool/script directly.

