Views: 31
Wireshark: Packet Operations
Statistics | Summary
This menu provides multiple statistics options ready to investigate to help users see the big picture in terms of the scope of the traffic, available protocols, endpoints and conversations, and some protocol-specific details like DHCP, DNS and HTTP/2. For a security analyst, it is crucial to know how to utilise the statical information.
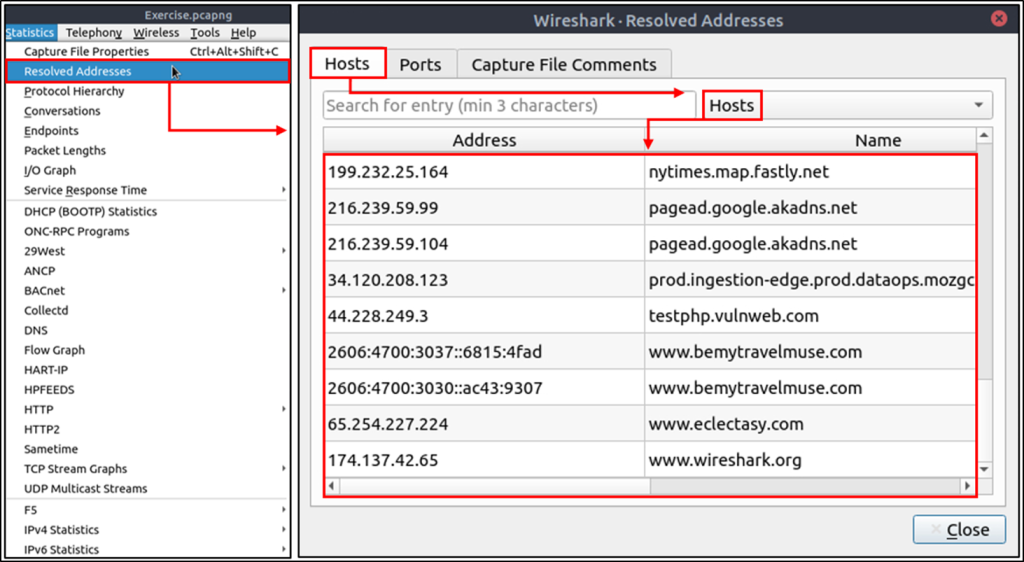
Resolved Addresses
This option helps analysts identify IP addresses and DNS names available in the capture file by providing the list of the resolved addresses and their hostnames. Note that the hostname information is taken from DNS answers in the capture file.
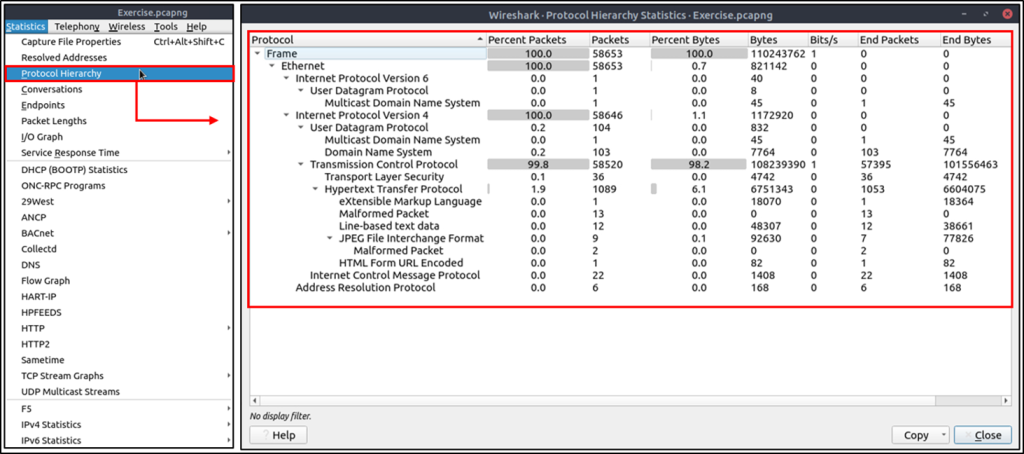
Protocol Hierarchy
This option breaks down all available protocols from the capture file and helps analysts view the protocols in a tree view based on packet counters and percentages. Thus analysts can view the overall usage of the ports and services and focus on the event of interest.
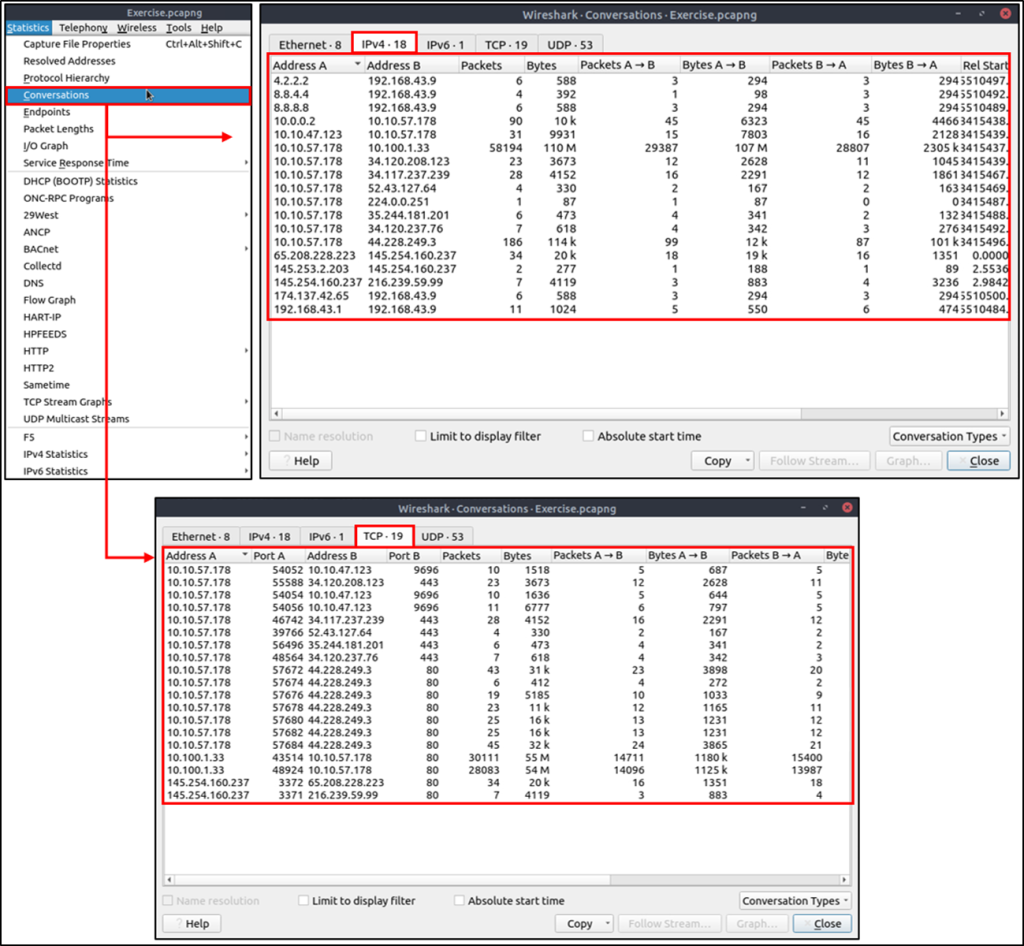
Conversations
Conversation represents traffic between two specific endpoints. This option provides the list of the conversations in five base formats; ethernet, IPv4, IPv6, TCP and UDP. Thus analysts can identify all conversations and contact endpoints for the event of interest.
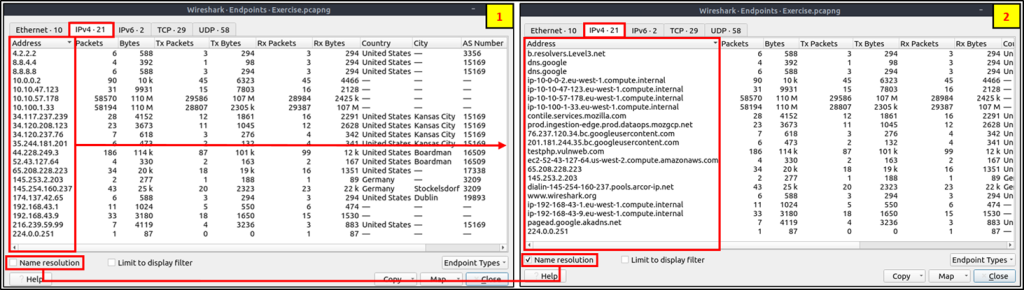
Endpoints
The endpoints option is similar to the conversations option. The only difference is that this option provides unique information for a single information field (Ethernet, IPv4, IPv6, TCP and UDP ).
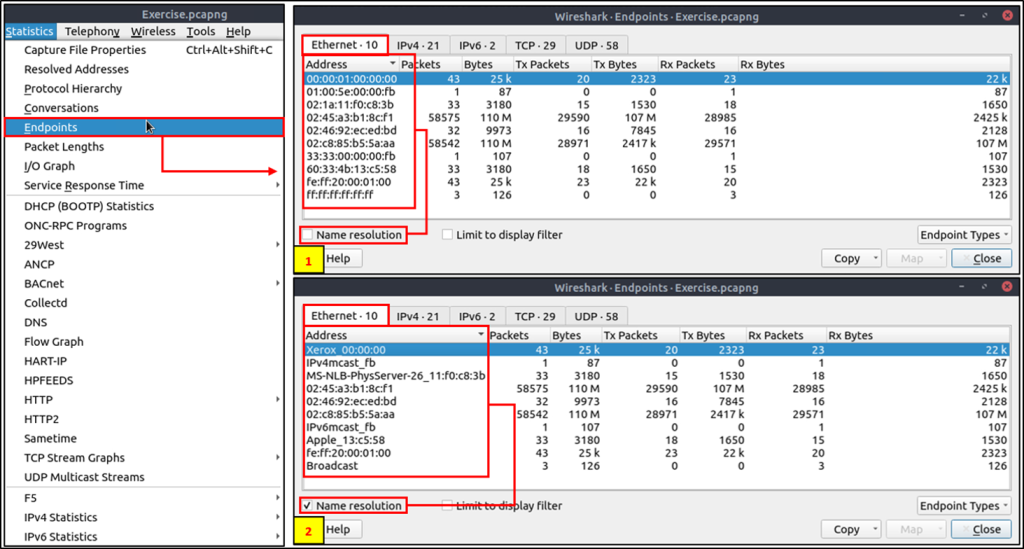
Name resolution is not limited only to MAC addresses. Wireshark provides IP and port name resolution options as well. However, these options are not enabled by default. If you want to use these functionalities, you need to activate them through the “Edit –> Preferences –> Name Resolution” menu.
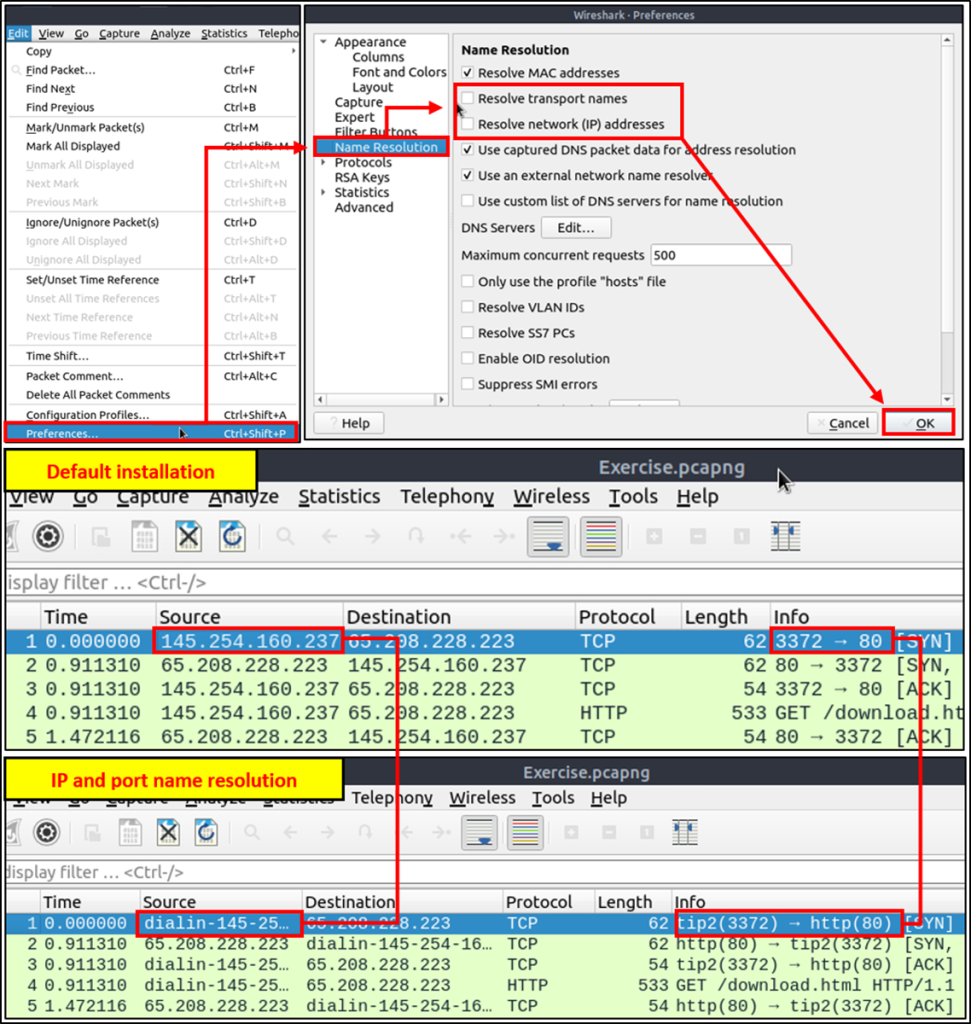
Endpoint menu view with name resolution:
Besides name resolution, Wireshark also provides an IP geolocation mapping that helps analysts identify the map’s source and destination addresses. But this feature is not activated by default and needs supplementary data like the GeoIP database. Currently, Wireshark supports MaxMind databases, and the latest versions of the Wireshark come configured MaxMind DB resolver.
Endpoints and GeoIP view.
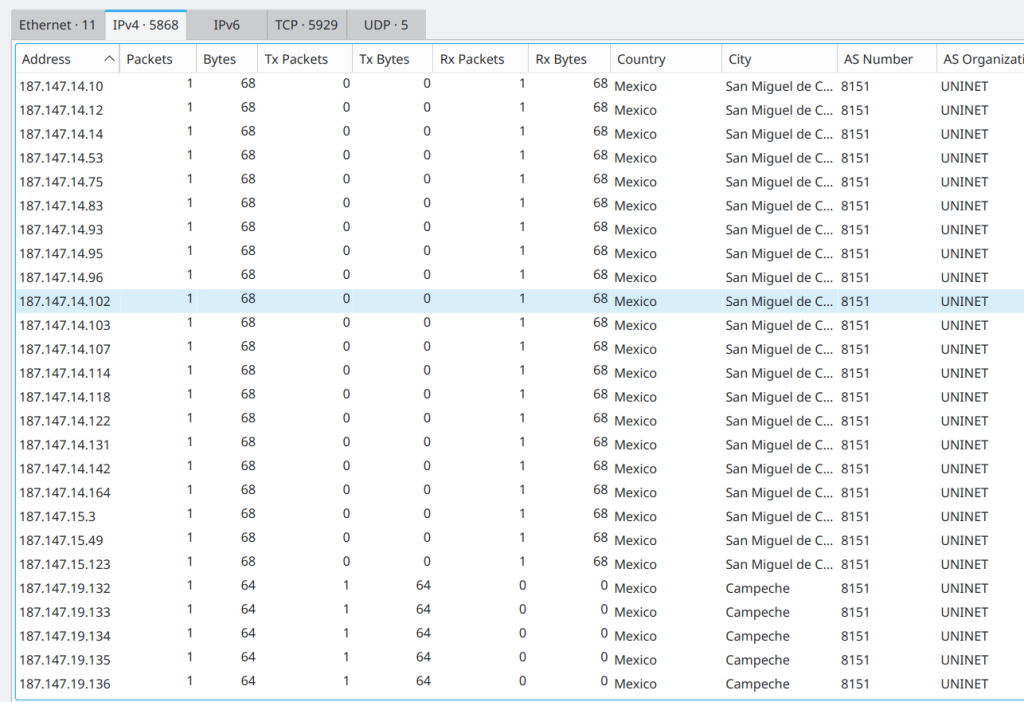
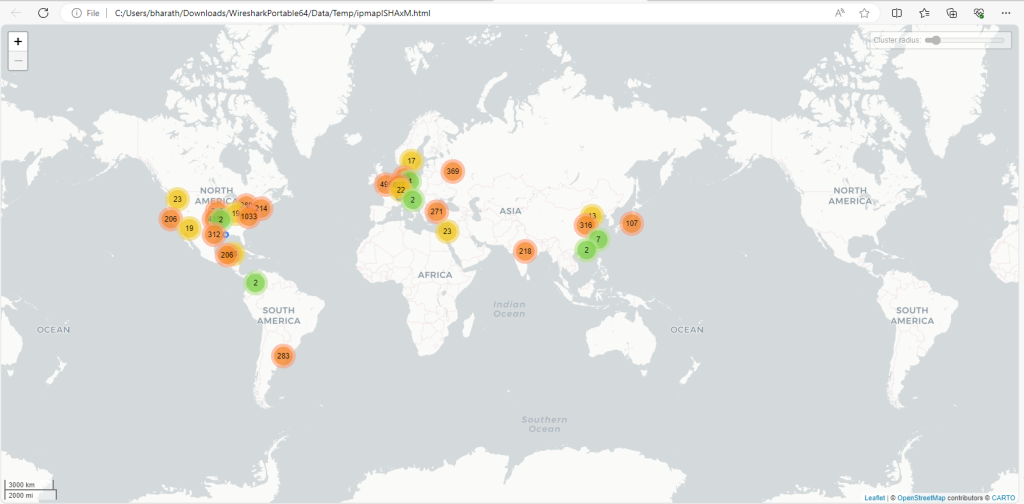
You can create filters based on these fields. Some filter examples are shown below.
- Destination City [IPv4]: ip.geoip.dst_city == “Dublin”
- Source or Destination City [IPv4]: ip.geoip.city == “Dublin”
- Destination Country: ip.geoip.dst_country == “Ireland”
- Destination Country based on Country Code: ip.geoip.dst_country_iso == “IE”
- All Destination Countries Except United States: !ip.geoip.country == “United States”
Statistics | Protocol Details
IPv4 and IPv6
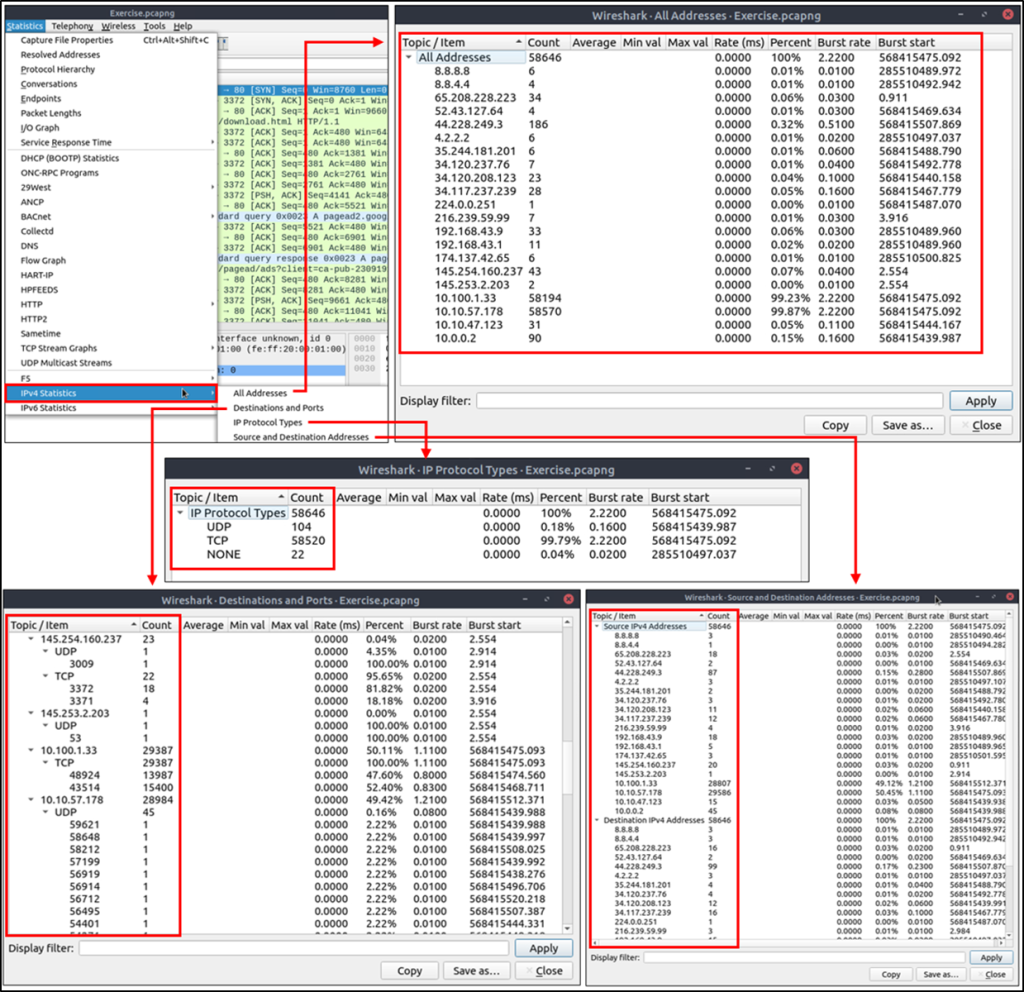
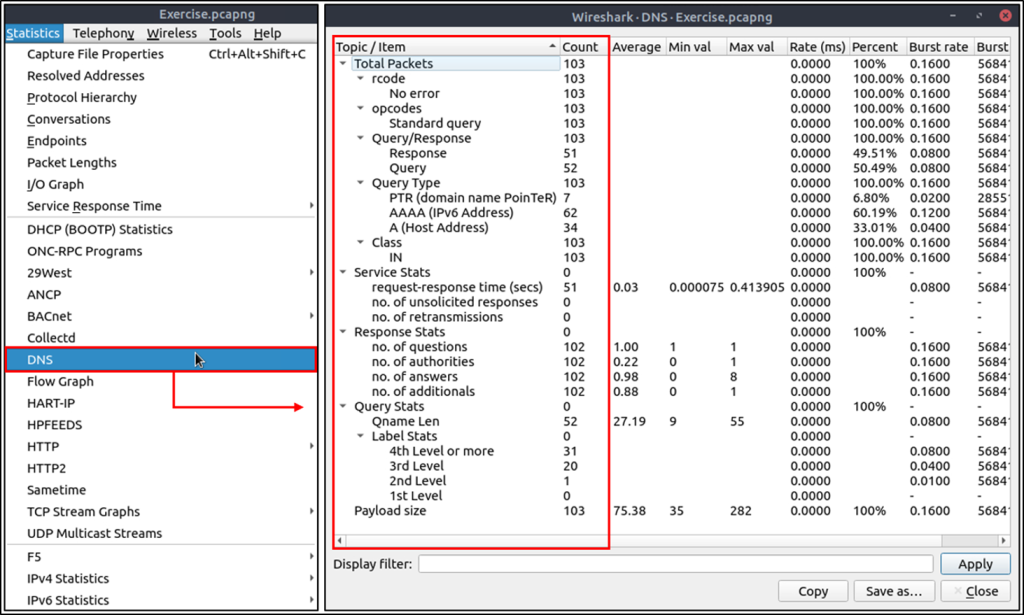
DNS
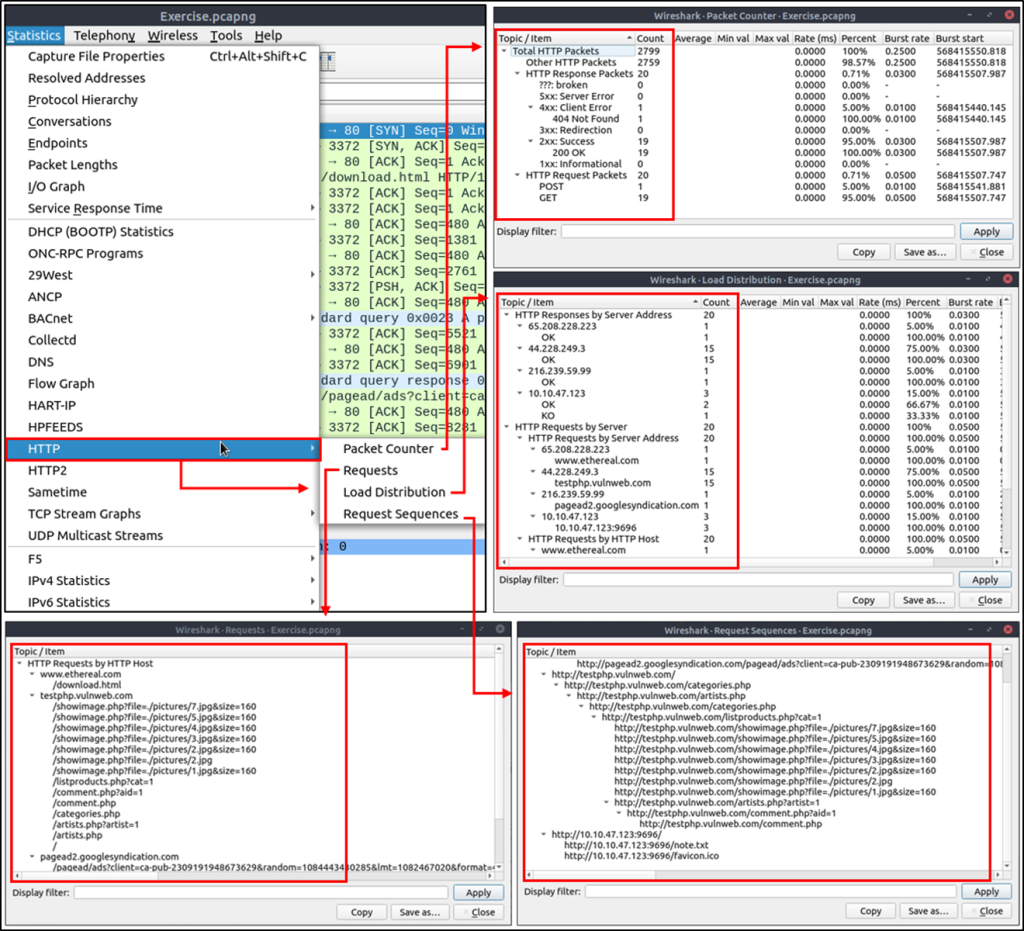
HTTP
Packet Filtering
- Packet filters are defined in lowercase.
- Packet filters have an autocomplete feature to break down protocol details, and each detail is represented by a “dot”.
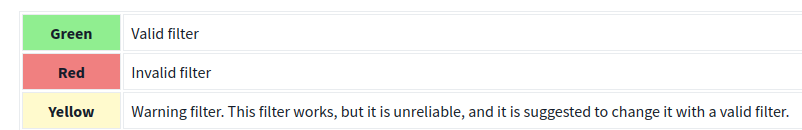
- Packet filters have a three-colour representation explained below.
Capture Filter Syntax
This type of filter is used to save only a specific part of the traffic. It is set before capturing traffic and not changeable during the capture.
Sample filter to capture port 80 traffic: tcp port 80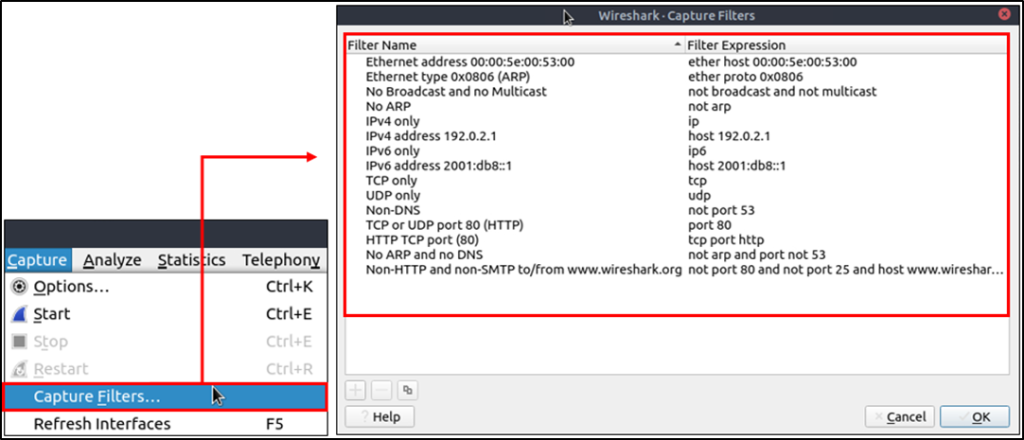
Display Filter Syntax
This type of filter is used to investigate packets by reducing the number of visible packets, and it is changeable during the capture.
It supports 3000 protocols and allows conducting packet-level searches under the protocol breakdown. The official “Display Filter Reference” provides all supported protocols breakdown for filtering.
Sample filter to capture port 80 traffic: tcp.port == 80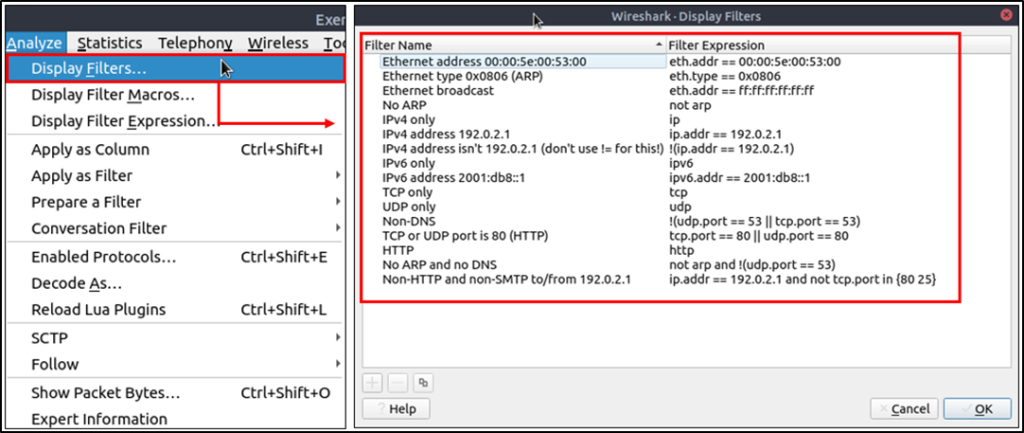
Comparison Operators
| English | C-Like | Description | Example |
| eq | == | Equal | ip.src == 10.10.10.100 |
| ne | != | Not equal | ip.src != 10.10.10.100 |
| gt | > | Greater than | ip.ttl > 250 |
| lt | < | Less Than | ip.ttl < 10 |
| ge | >= | Greater than or equal to | ip.ttl >= 0xFA |
| le | <= | Less than or equal to | ip.ttl <= 0xA |
Note: Wireshark supports decimal and hexadecimal values in filtering.
Logical Expressions
Wireshark supports boolean syntax.
| English | C-Like | Description | Example |
| and | && | Logical AND | (ip.src == 10.10.10.100) AND (ip.src == 10.10.10.111) |
| or | || | Logical OR | (ip.src == 10.10.10.100) OR (ip.src == 10.10.10.111) |
| not | ! | Logical NOT | !(ip.src == 10.10.10.222)Note: Usage of !=value is deprecated; using it could provide inconsistent results. Using the !(value) style is suggested for more consistent results. |
Packet Filtering | Protocol Filters
IP Filters
IP filters help analysts filter the traffic according to the IP level information from the packets (Network layer of the OSI model). This is one of the most commonly used filters in Wireshark. These filters filter network-level information like IP addresses, version, time to live, type of service, flags, and checksum values.
| Filter | Description |
ip | Show all IP packets. |
ip.addr == 10.10.10.111 | Show all packets containing IP address 10.10.10.111. |
ip.addr == 10.10.10.0/24 | Show all packets containing IP addresses from 10.10.10.0/24 subnet. |
ip.src == 10.10.10.111 | Show all packets originated from 10.10.10.111 |
ip.dst == 10.10.10.111 | Show all packets sent to 10.10.10.111 |
TCP and UDP Filters
TCP filters help analysts filter the traffic according to protocol-level information from the packets (Transport layer of the OSI model). These filters filter transport protocol level information like source and destination ports, sequence number, acknowledgement number, windows size, timestamps, flags, length and protocol errors.
| Filter | Description | Filter | Expression |
tcp.port == 80 | Show all TCP packets with port 80 | udp.port == 53 | Show all UDP packets with port 53 |
tcp.srcport == 1234 | Show all TCP packets originating from port 1234 | udp.srcport == 1234 | Show all UDP packets originating from port 1234 |
tcp.dstport == 80 | Show all TCP packets sent to port 80 | udp.dstport == 5353 | Show all UDP packets sent to port 5353 |
Application Level Protocol Filters | HTTP and DNS
Application-level protocol filters help analysts filter the traffic according to application protocol level information from the packets (Application layer of the OSI model ). These filters filter application-specific information, like payload and linked data, depending on the protocol type.
| Filter | Description | Filter | Description |
http | Show all HTTP packets | dns | Show all DNS packets |
http.response.code == 200 | Show all packets with HTTP response code “200” | dns.flags.response == 0 | Show all DNS requests |
http.request.method == "GET" | Show all HTTP GET requests | dns.flags.response == 1 | Show all DNS responses |
http.request.method == "POST" | Show all HTTP POST requests | dns.qry.type == 1 | Show all DNS “A” records |
Display Filter Expressions
Wireshark has a built-in option (Display Filter Expression) that stores all supported protocol structures to help analysts create display filters. When an analyst can’t recall the required filter for a specific protocol or is unsure about the assignable values for a filter, the Display Filter Expressions menu provides an easy-to-use display filter builder guide. It is available under the “Analyse –> Display Filter Expression” menu.
It is impossible to memorise all details of the display filters for each protocol. Each protocol can have different fields and can accept various types of values. The Display Filter Expressions menu shows all protocol fields, accepted value types (integer or string) and predefined values (if any).
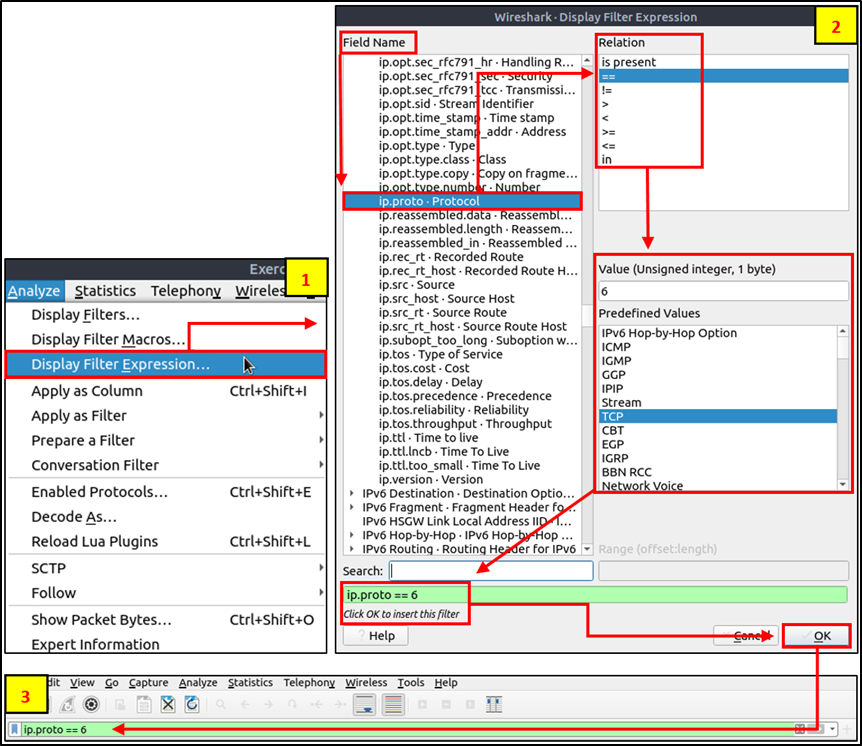
Advanced Filtering
Wireshark has advanced operators and functions. These advanced filtering options help the analyst conduct an in-depth analysis of an event of interest.
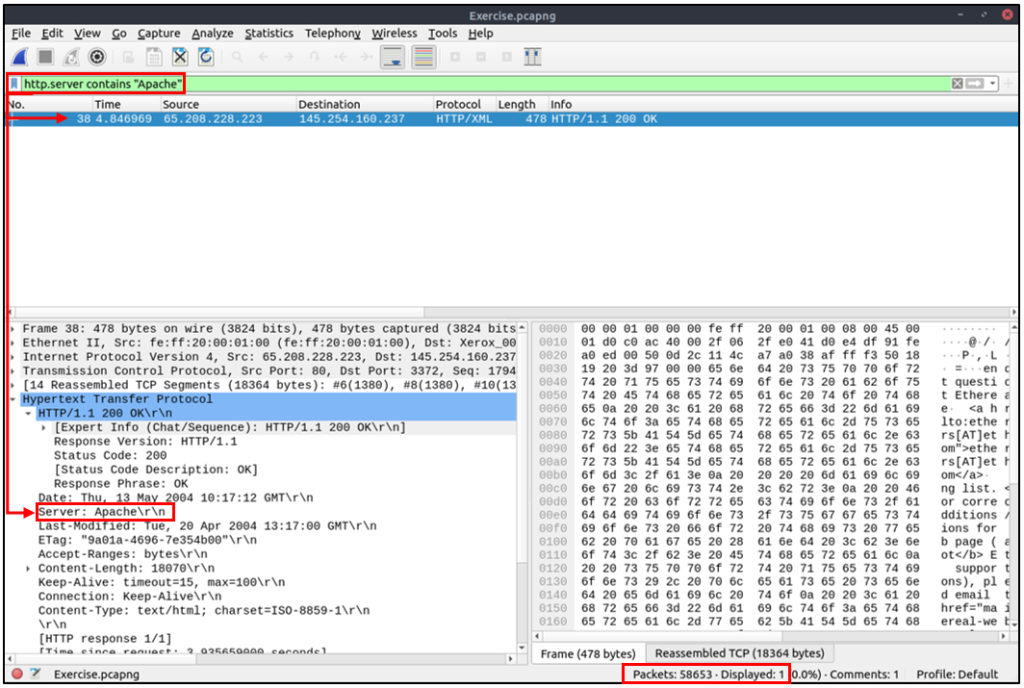
Filter: “contains”
| Filter | contains |
| Type | Comparison Operator |
| Description | Search a value inside packets. It is case-sensitive and provides similar functionality to the “Find” option by focusing on a specific field. |
| Example | Find all “Apache” servers. |
| Workflow | List all HTTP packets where packets’ “server” field contains the “Apache” keyword. |
| Usage | http.server contains "Apache" |
Filter: “matches”
| Filter | matches |
| Type | Comparison Operator |
| Description | Search a pattern of a regular expression. It is case insensitive, and complex queries have a margin of error. |
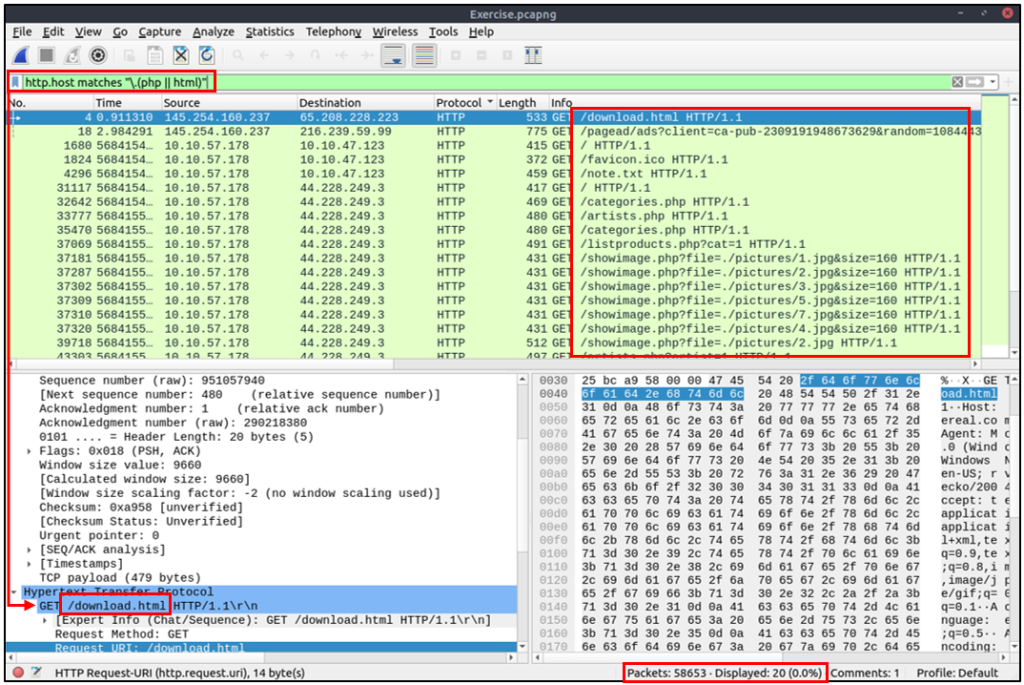
| Example | Find all .php and .html pages. |
| Workflow | List all HTTP packets where packets’ “host” fields match keywords “.php” or “.html”. |
| Usage | http.host matches "\.(php|html)" |
Filter: “in”
| Filter | in |
| Type | Set Membership |
| Description | Search a value or field inside of a specific scope/range. |
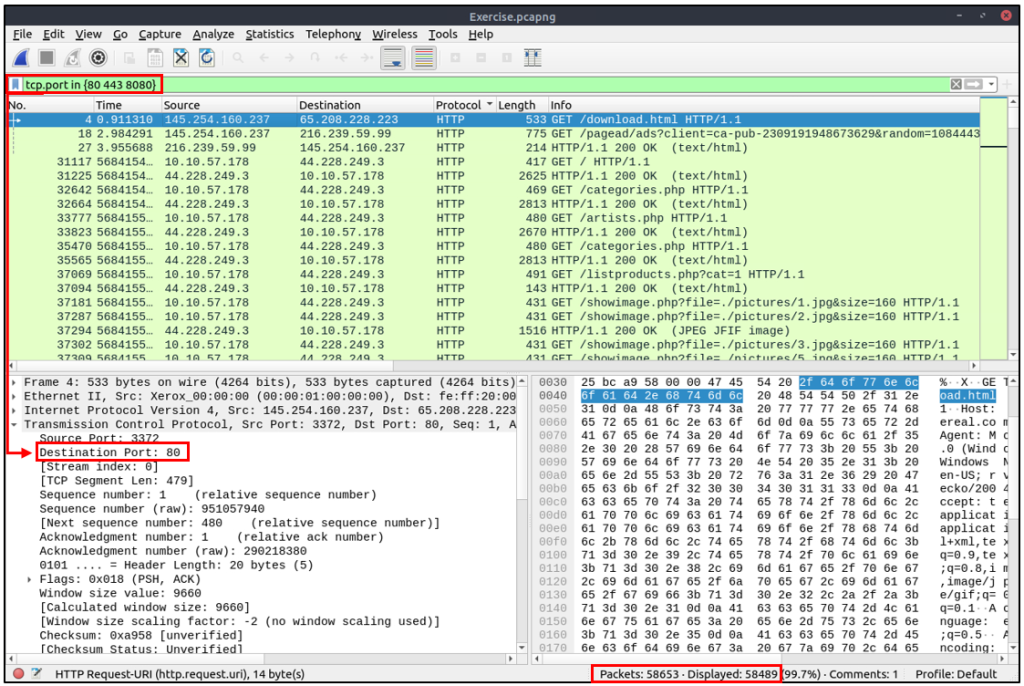
| Example | Find all packets that use ports 80, 443 or 8080. |
| Workflow | List all TCP packets where packets’ “port” fields have values 80, 443 or 8080. |
| Usage | tcp.port in {80 443 8080} |
Filter: “upper”
| Filter | upper |
| Type | Function |
| Description | Convert a string value to uppercase. |
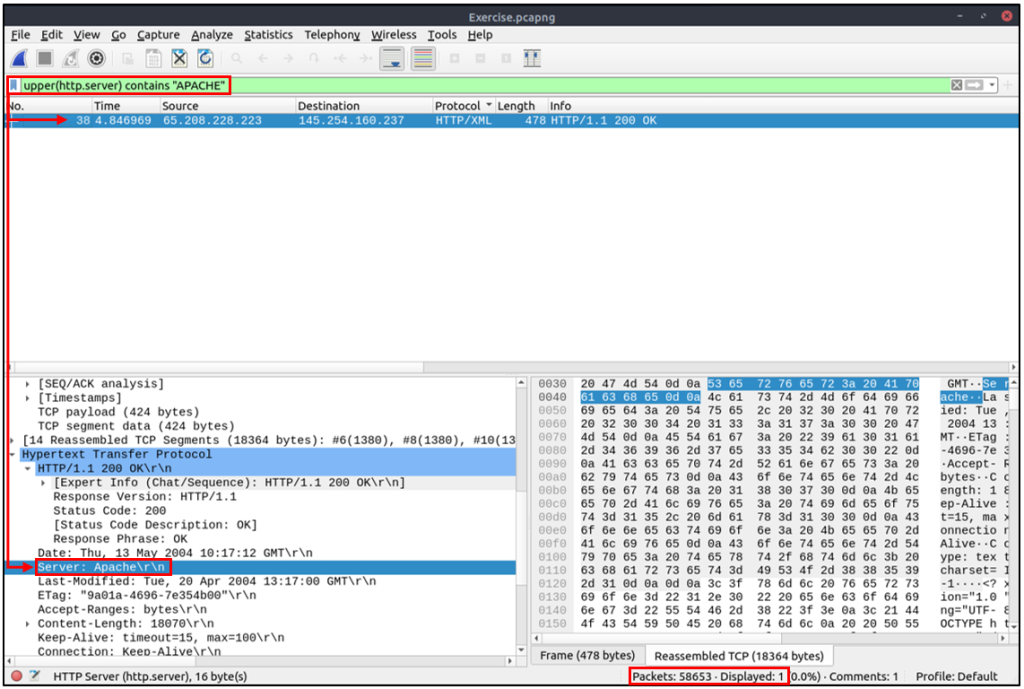
| Example | Find all “APACHE” servers. |
| Workflow | Convert all HTTP packets’ “server” fields to uppercase and list packets that contain the “APACHE” keyword. |
| Usage | upper(http.server) contains "APACHE" |
Filter: “lower”
| Filter | lower |
| Type | Function |
| Description | Convert a string value to lowercase. |
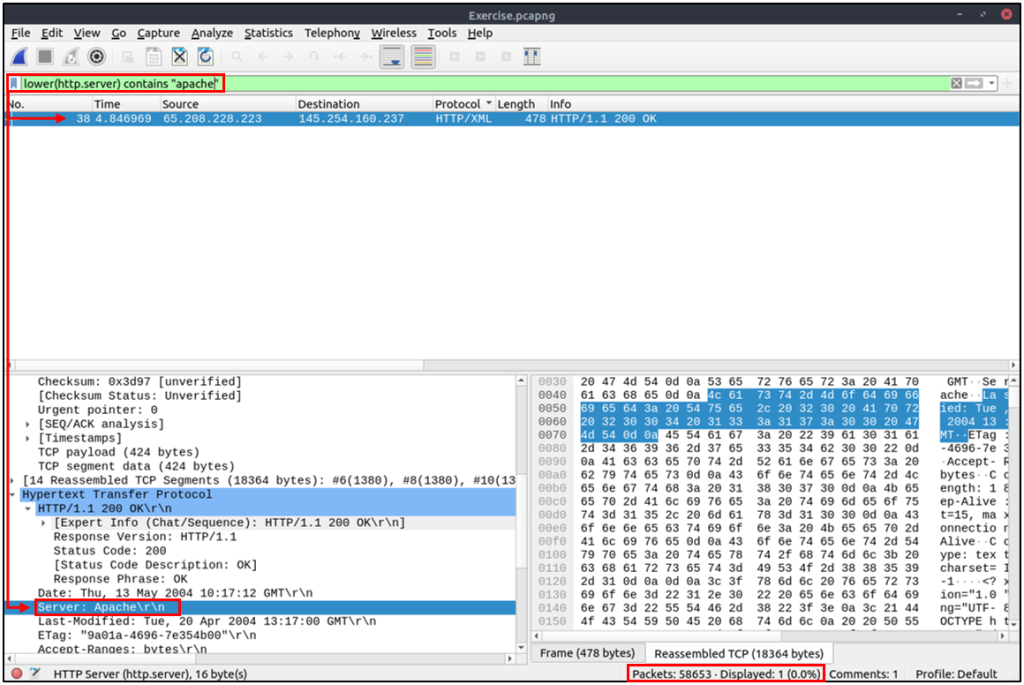
| Example | Find all “apache” servers. |
| Workflow | Convert all HTTP packets’ “server” fields info to lowercase and list packets that contain the “apache” keyword. |
| Usage | lower(http.server) contains "apache" |
Filter: “string”
| Filter | string |
| Type | Function |
| Description | Convert a non-string value to a string. |
| Example | Find all frames with odd numbers. |
| Workflow | Convert all “frame number” fields to string values, and list frames end with odd values. |
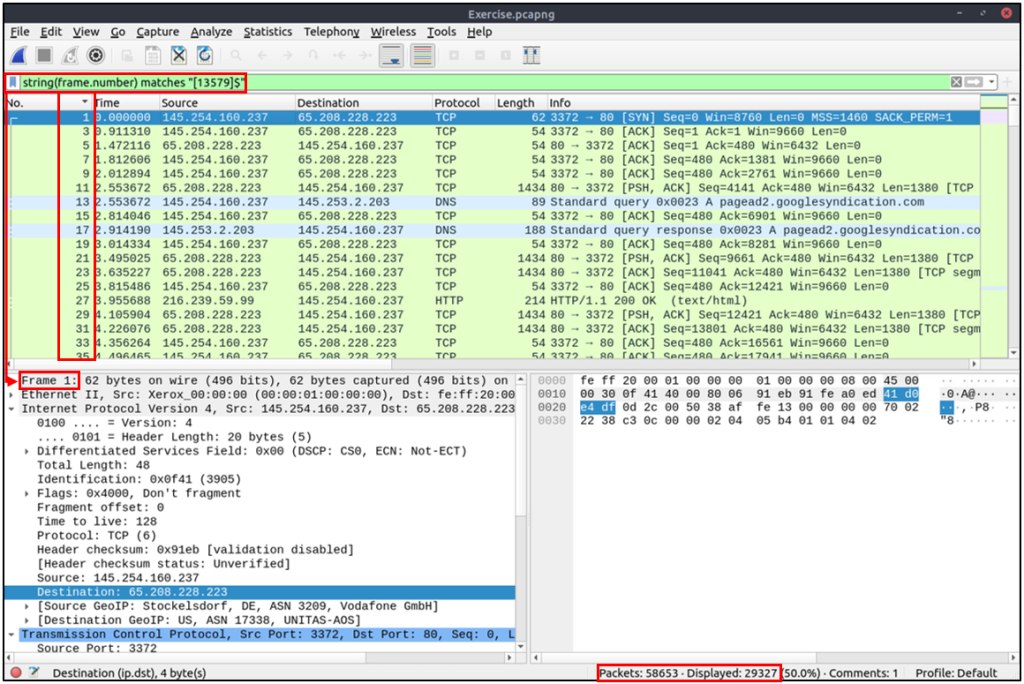
| Usage | string(frame.number) matches "[13579]$" |
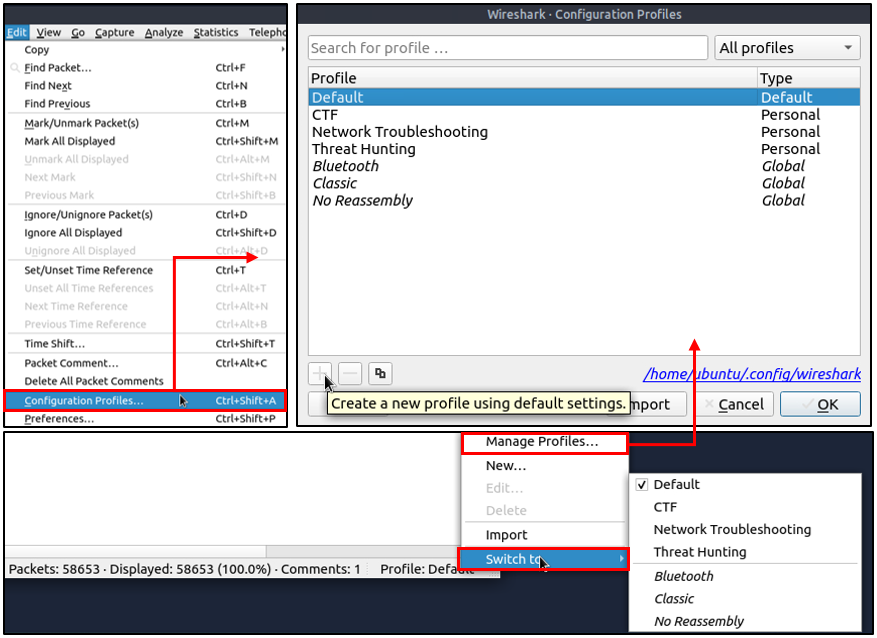
Profiles
Wireshark is a multifunctional tool that helps analysts to accomplish in-depth packet analysis. As we covered during the room, multiple preferences need to be configured to analyse a specific event of interest. It is cumbersome to re-change the configuration for each investigation case, which requires a different set of colouring rules and filtering buttons. This is where Wireshark profiles come into play. You can create multiple profiles for different investigation cases and use them accordingly. You can use the “Edit –> Configuration Profiles” menu or the “lower right bottom of the status bar –> Profile” section to create, modify and change the profile configuration.
Example Usage
#IIS servers running a non-standard HTTP port (other than 80)
http.server contains "IIS" && !tcp.srcport == 80
#IIS servers with version 7.5
http.server matches "IIS/7.5"
#Total number of packets that use ports 3333, 4444 or 9999
tcp.port in {3333 4444 9999}


