Views: 36
Wireshark: Traffic Analysis
Investigating Nmap scans
Nmap is an industry-standard tool for mapping networks, identifying live hosts and discovering the services. As it is one of the most used network scanner tools, a security analyst should identify the network patterns created with it.
Common Nmap scan types,
- TCP connect scans
- SYN scans
- UDP scans
It is essential to know how Nmap scans work to spot scan activity on the network.
TCP Flags
| Notes | Wireshark Filters |
| Global search. | tcpudp |
| Only SYN flag. SYN flag is set. The rest of the bits are not important. | tcp.flags == 2tcp.flags.syn == 1 |
| Only ACK flag. ACK flag is set. The rest of the bits are not important. | tcp.flags == 16tcp.flags.ack == 1 |
| Only SYN, ACK flags. SYN and ACK are set. The rest of the bits are not important. | tcp.flags == 18(tcp.flags.syn == 1) and (tcp.flags.ack == 1) |
| Only RST flag. RST flag is set. The rest of the bits are not important. | tcp.flags == 4tcp.flags.reset == 1 |
| Only RST, ACK flags. RST and ACK are set.The rest of the bits are not important. | tcp.flags == 20(tcp.flags.reset == 1) and (tcp.flags.ack == 1) |
| Only FIN flag FIN flag is set. The rest of the bits are not important. | tcp.flags == 1tcp.flags.fin == 1 |
TCP Connect Scans
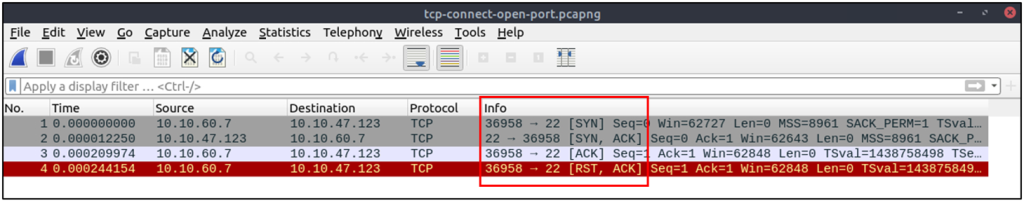
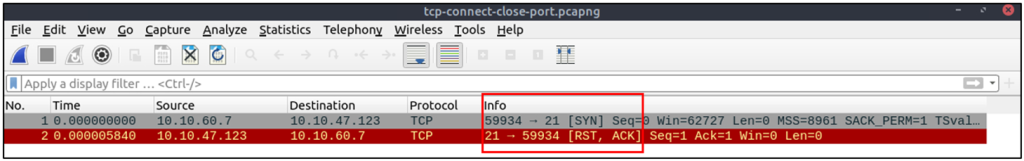
- Relies on the three-way handshake (needs to finish the handshake process).
- Usually conducted with
nmap-sTcommand. - Used by non-privileged users (only option for a non-root user).
- Usually has a windows size larger than 1024 bytes as the request expects some data due to the nature of the protocol.
Open TCP port (Connect):
Closed TCP port (Connect):
#Filter to detect TCP scans in large capture (PCAP) files
tcp.flags.syn==1 and tcp.flags.ack==0 and tcp.window_size > 1024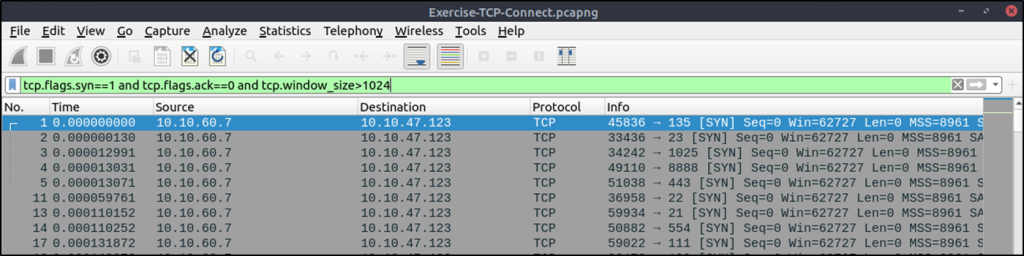
SYN Scans
- Doesn’t rely on the three-way handshake (no need to finish the handshake process).
- Usually conducted with
nmap -sScommand. - Used by privileged users.
- Usually have a size less than or equal to 1024 bytes as the request is not finished and it doesn’t expect to receive data.
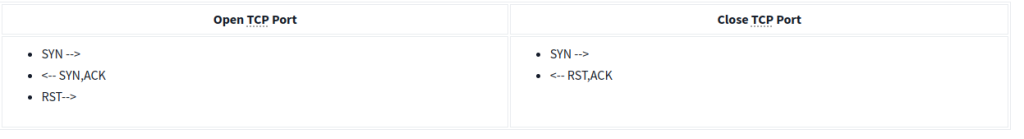
Open TCP port (SYN):
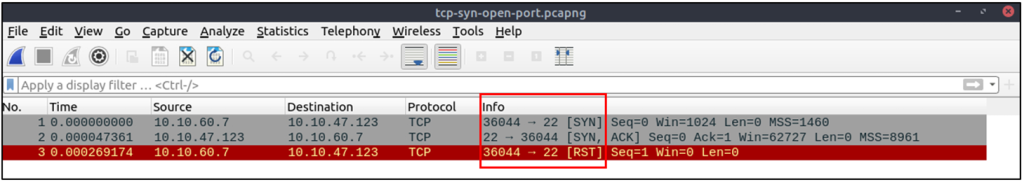
Closed TCP port (SYN):
#Filter to show packets from a cpatured file
tcp.flags.syn==1 and tcp.flags.ack==0 and tcp.window_size <= 1024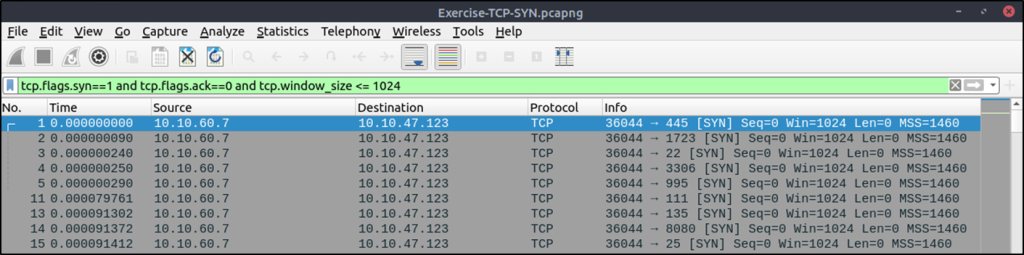
UDP scans
- Doesn’t require a handshake process
- No prompt for open ports
- ICMP error message for close ports
- Usually conducted with
nmap -sUcommand.
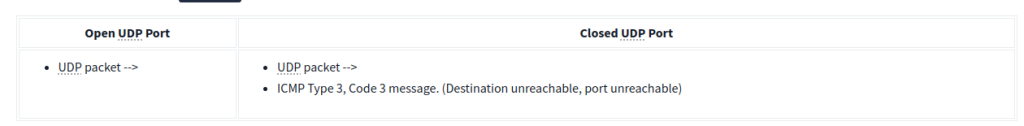
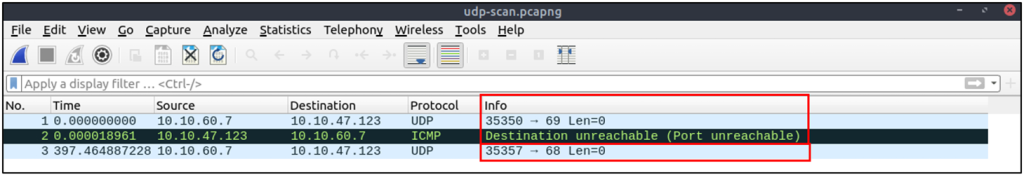
Closed (port no 69) and open (port no 68) UDP ports:
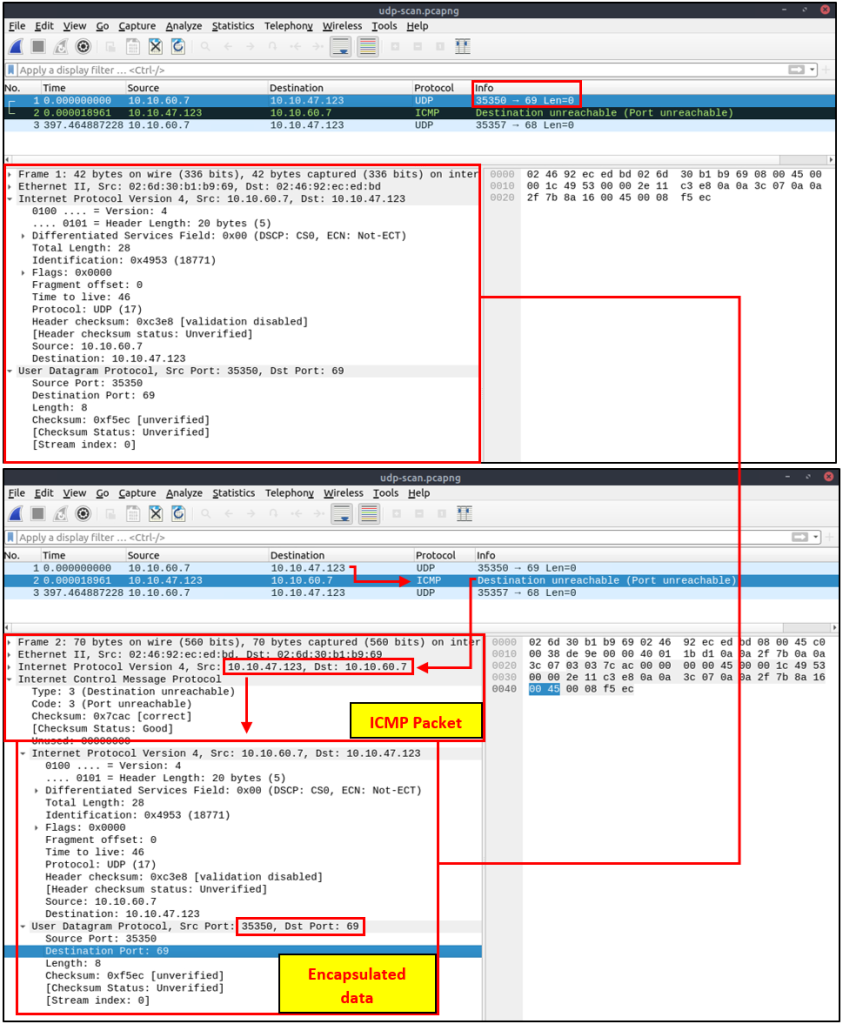
The above image shows that the closed port returns an ICMP error packet. No further information is provided about the error at first glance, so how can an analyst decide where this error message belongs? The ICMP error message uses the original request as encapsulated data to show the source/reason of the packet. Once you expand the ICMP section in the packet details pane, you will see the encapsulated data and the original request, as shown in the below image.
#The given filter shows the UDP scan patterns in a capture file.
icmp.type==3 and icmp.code==3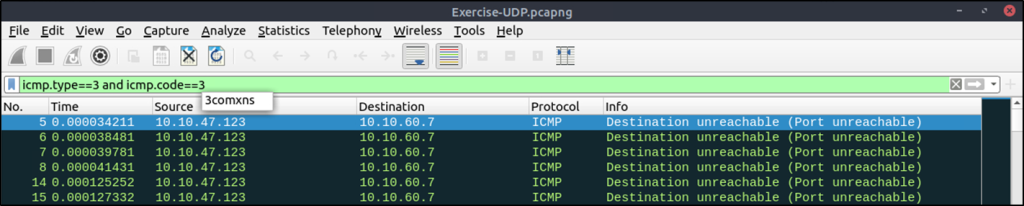
udp.port in {60..70}Investigating ARP Poisoning/Spoofing
- Works on the local network
- Enables the communication between MAC addresses
- Not a secure protocol
- Not a routable protocol
- It doesn’t have an authentication function
- Common patterns are request & response, announcement and gratuitous packets.
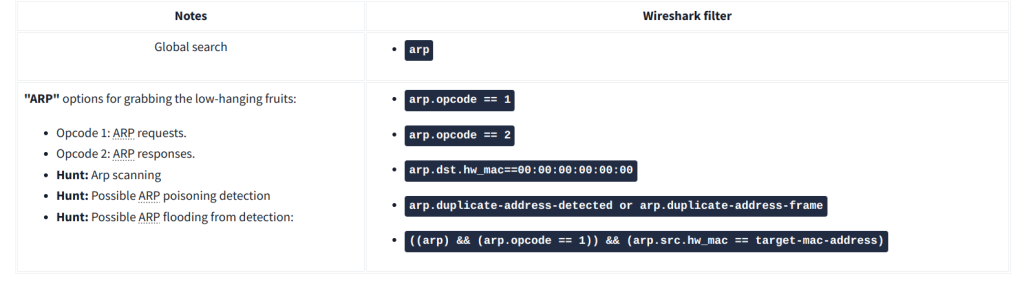
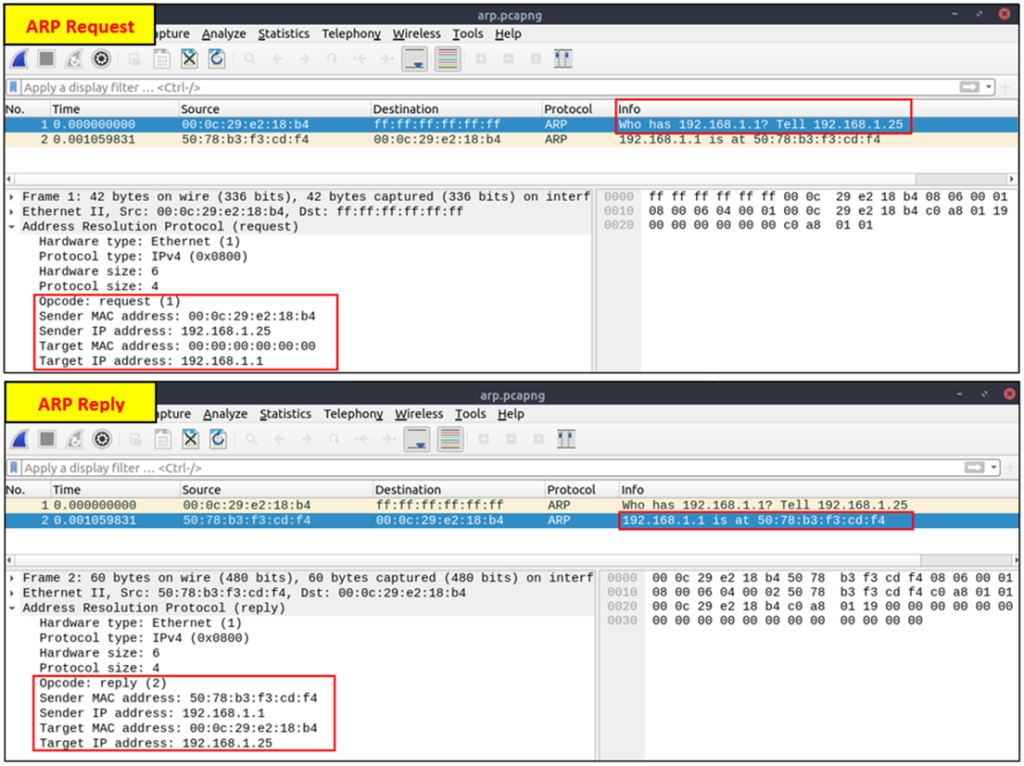
A suspicious situation means having two different ARP responses (conflict) for a particular IP address. In that case, Wireshark’s expert info tab warns the analyst. However, it only shows the second occurrence of the duplicate value to highlight the conflict. Therefore, identifying the malicious packet from the legitimate one is the analyst’s challenge. A possible IP spoofing case is shown in the picture below.
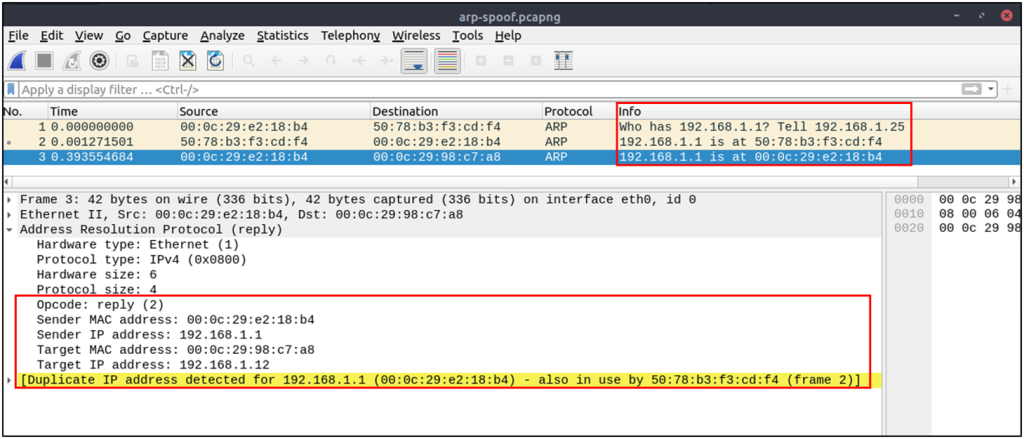
#Detect ARP spoofing
(arp.dst.hw_mac == 00:00:00:00:00:00) && (arp.src.hw_mac == 00:0c:29:e2:18:b4)
#Using eth.addr filter
http && (eth.addr==00:0c:29:e2:18:b4)
#Detect password/credentials
urlencoded-form.key == pass
#HTTP POST method
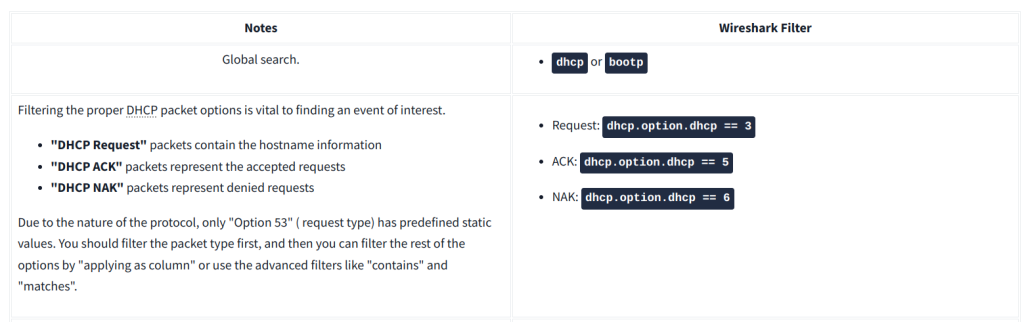
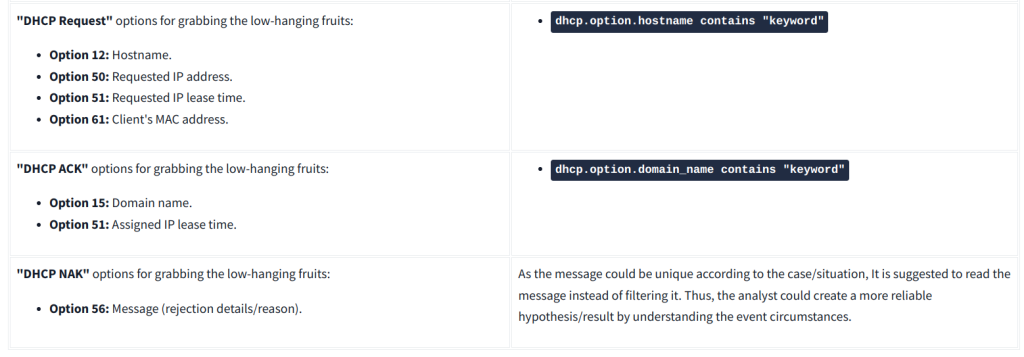
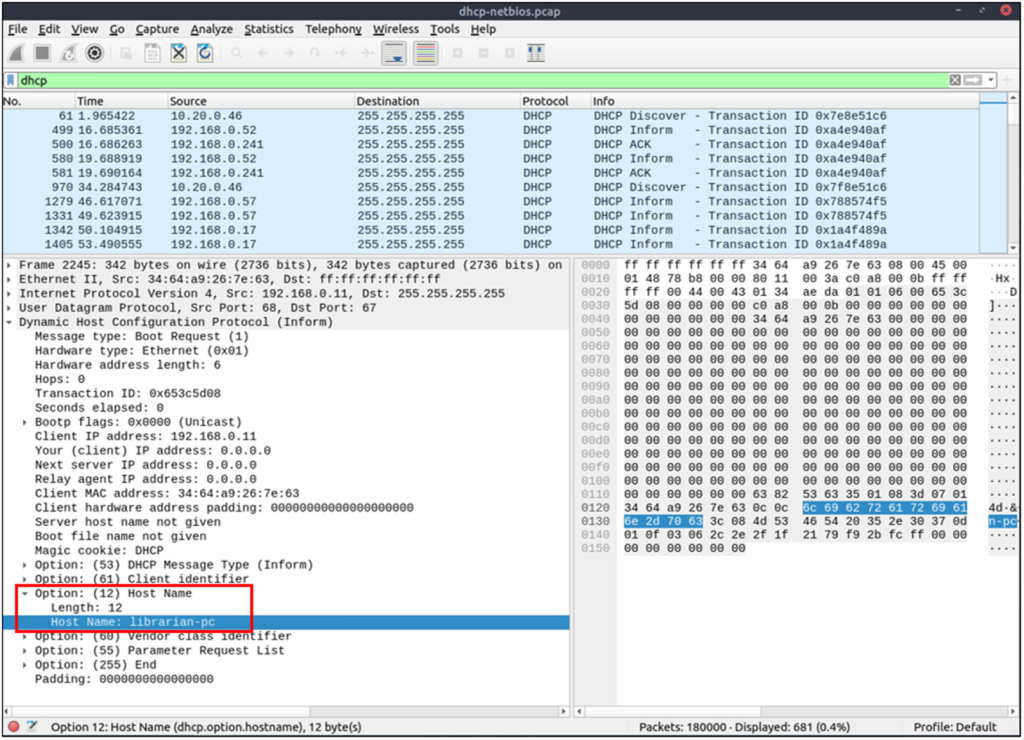
http.request.method == "POST"DHCP Analysis
Click here to go to PART 2 of this series



