Views: 18
Understanding the Digital Operational Resilience Act (DORA): A Comprehensive Overview
In an era where digitalization permeates every aspect of our lives, the importance of cybersecurity and operational resilience has never been more critical. The European Union’s Digital Operational Resilience Act (DORA) stands as a landmark regulatory framework aimed at enhancing the digital operational resilience of the financial sector. As a cybersecurity consultant, understanding the intricacies of DORA is essential for advising clients and ensuring compliance. This article delves into the key aspects of DORA, its implications, and the steps organizations need to take to align with its requirements.
What is DORA?
The Digital Operational Resilience Act (DORA) is a legislative proposal by the European Commission aimed at ensuring that all participants in the financial system have the necessary safeguards in place to withstand, respond to, and recover from ICT-related incidents. DORA is part of the broader Digital Finance Package, which seeks to modernize the financial sector in the EU and bolster its resilience against digital threats.
Key Objectives of DORA
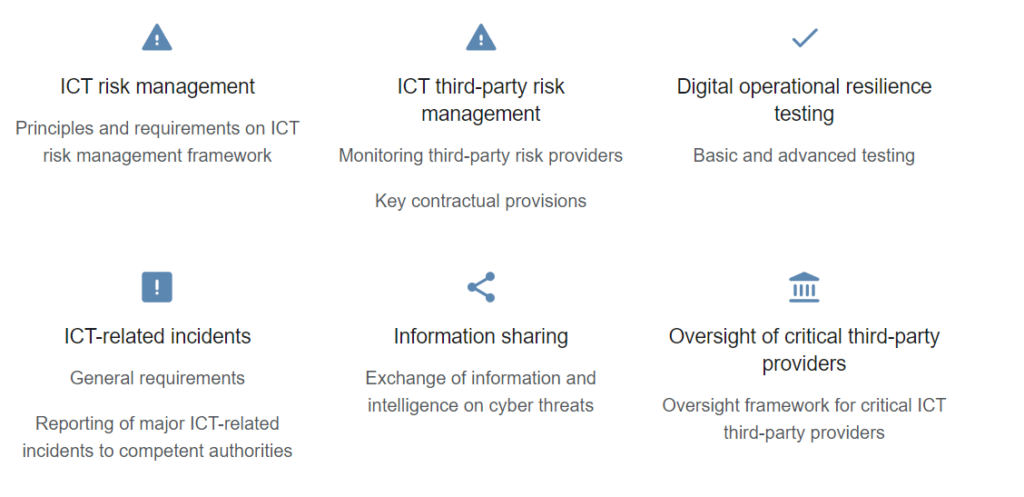
- Enhancing ICT Risk Management: DORA mandates that financial entities develop robust ICT risk management frameworks. These frameworks should encompass risk identification, protection, detection, response, and recovery measures. The goal is to ensure continuous business operations and the security of information assets.
- Incident Reporting: The act introduces stringent requirements for reporting ICT-related incidents. Financial institutions must report significant incidents to competent authorities within a stipulated timeframe. This aims to facilitate swift responses and mitigate the impact of cyber incidents.
- Third-Party Risk Management: DORA places a strong emphasis on the oversight of third-party ICT service providers. Financial entities must ensure that their service providers adhere to stringent security standards and that there are clear protocols for managing third-party risks.
- Information Sharing: To foster a collaborative approach to cybersecurity, DORA encourages information sharing among financial entities, regulators, and other stakeholders. This collective intelligence is vital for anticipating threats and enhancing the overall resilience of the financial sector.
- Operational Resilience Testing: Regular testing of ICT systems, including threat-led penetration testing (TLPT), is a cornerstone of DORA. These tests are designed to identify vulnerabilities and assess the effectiveness of existing security measures.
What does it cover?
Implications for Financial Entities
DORA’s implementation will have far-reaching implications for financial entities operating within the EU. Here are some of the key impacts:
- Compliance Costs: Financial institutions will need to invest significantly in upgrading their ICT infrastructure, training staff, and enhancing their cybersecurity measures to comply with DORA. While these investments are substantial, they are crucial for building a resilient digital framework.
- Enhanced Security Posture: By adhering to DORA’s stringent requirements, financial entities can significantly bolster their security posture. This not only protects them from cyber threats but also enhances their reputation and trustworthiness among clients and stakeholders.
- Regulatory Scrutiny: With increased regulatory oversight, financial institutions will be subject to regular audits and assessments. Non-compliance with DORA can result in severe penalties, including fines and reputational damage.
- Vendor Management: The emphasis on third-party risk management will necessitate a more rigorous approach to vetting and managing ICT service providers. Financial entities will need to ensure that their vendors comply with DORA’s standards and that there are clear contingency plans in place for managing third-party failures.
Steps to Achieve Compliance
Achieving compliance with DORA requires a structured and proactive approach. Here are some steps that financial entities can take:
- Conduct a Gap Analysis: Assess current ICT risk management practices and identify gaps in relation to DORA’s requirements. This will provide a clear roadmap for the necessary enhancements.
- Develop a Comprehensive ICT Risk Management Framework: Establish a robust framework that covers all aspects of risk management, including risk assessment, mitigation, and response. Ensure that this framework is integrated into the organization’s overall risk management strategy.
- Enhance Incident Reporting Mechanisms: Implement efficient incident reporting systems that allow for timely detection and reporting of ICT-related incidents. Train staff on the importance of prompt reporting and the procedures to follow.
- Strengthen Third-Party Risk Management: Develop stringent protocols for assessing and monitoring third-party ICT service providers. Ensure that contracts include provisions for compliance with DORA and that regular audits are conducted.
- Implement Regular Testing: Conduct regular operational resilience tests, including TLPT, to identify and address vulnerabilities. Use the findings from these tests to continuously improve security measures.
- Foster a Culture of Resilience: Promote a culture of resilience within the organization by providing ongoing training and awareness programs. Ensure that all employees understand their role in maintaining digital operational resilience.
Implementation Timeline
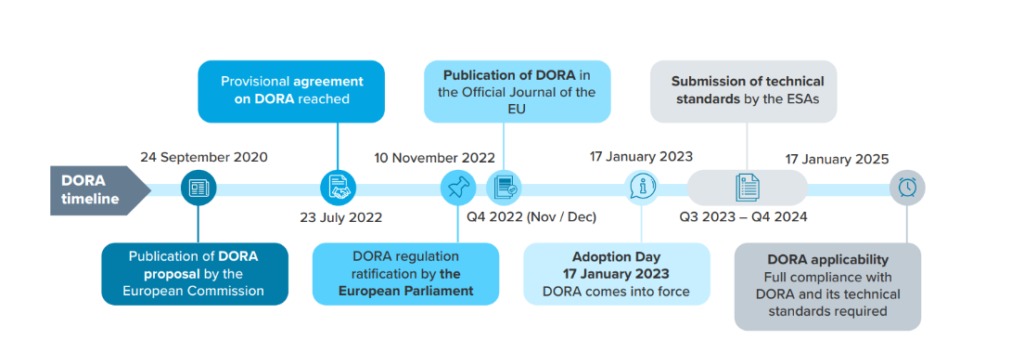
The Digital Operational Resilience Act represents a significant step towards safeguarding the financial sector in the EU from the growing threat of cyber incidents. By understanding and implementing the requirements of DORA, financial entities can enhance their digital operational resilience, protect their clients, and contribute to the stability of the financial system. As a cybersecurity consultant, staying abreast of such regulatory developments and guiding clients through compliance is crucial for ensuring a secure and resilient digital future.
In conclusion, DORA is not just a regulatory requirement but an opportunity for financial institutions to fortify their digital defenses and build a resilient operational framework. By taking proactive steps towards compliance, financial entities can navigate the complexities of the digital landscape with confidence and agility.
4o


