Views: 472
In web application penetration testing, entry points are areas of an application where a user can input data or interact with the system, which an attacker could potentially exploit. Identifying these points is crucial because they represent potential paths for unauthorized access, data manipulation, or other malicious actions. Common entry points include form fields, URL parameters, HTTP headers, cookies, and hidden fields in web pages.
Practical Example: Fuzzing for Entry Points in a Web Login Form
Let’s walk through a practical example of identifying and testing an entry point—specifically, a login form.
Scenario
Suppose we have a login form on a web application at https://example.com/login with two fields:
• username
• password
This form submits data to the server for authentication. To a pen tester, this form represents a critical entry point because it accepts user-supplied data (credentials) and communicates with the server.
Step-by-Step Fuzzing for Entry Points
1. Initial Reconnaissance: Use tools like Burp Suite or OWASP ZAP to intercept the request sent when submitting the form. This helps you see the exact parameters being passed and where they go. For instance:
POST /login HTTP/1.1
Host: example.com
Content-Type: application/x-www-form-urlencoded
Content-Length: 30
username=admin&password=pass1232. Identify Parameters: The username and password fields are entry points because they are fields where user input could be manipulated.
3. Fuzzing the Fields: Use a fuzzing tool like Burp Intruder to inject various payloads into these parameters. For example, you might:
• Try common SQL injection payloads like admin’ OR ‘1’=’1 in the username field.
• Try excessively long strings or unusual characters to see if the application handles them properly.
• Submit various types of payloads in both username and password to test how the application responds.
4. Observe Responses: As the fuzzer tests each payload, observe the responses. If the application behaves unexpectedly (e.g., returns an error or displays debug information), this could indicate a vulnerability at the entry point.
5. Analyze and Report Findings: Document any abnormalities or errors that suggest a vulnerability, like SQL injection or error-based information disclosure.
Why Entry Points Matter
These entry points are critical because any vulnerability within them could allow attackers to bypass authentication, execute code, or extract sensitive information. In our example, if the login form were vulnerable to SQL injection, an attacker might be able to log in as an admin without knowing the password, potentially compromising the entire application.
Identifying and testing these entry points is a core part of web application pentesting, as it helps in finding weak spots before an attacker does.
Fuzz Faster U Fool – v1.3.1
TryHackMe has an excellent room to learn and practice this tool. Highly recommended for beginners.
ffuf -h
┌──(zyberpatrol㉿kali-zyberpatrol)-[~]
└─$ ffuf -h
Fuzz Faster U Fool - v2.0.0-dev
HTTP OPTIONS:
-H Header `"Name: Value"`, separated by colon. Multiple -H flags are accepted.
-X HTTP method to use
-b Cookie data `"NAME1=VALUE1; NAME2=VALUE2"` for copy as curl functionality.
-d POST data
-http2 Use HTTP2 protocol (default: false)
-ignore-body Do not fetch the response content. (default: false)
-r Follow redirects (default: false)
-recursion Scan recursively. Only FUZZ keyword is supported, and URL (-u) has to end in it. (default: false)
-recursion-depth Maximum recursion depth. (default: 0)
-recursion-strategy Recursion strategy: "default" for a redirect based, and "greedy" to recurse on all matches (default: default)
-replay-proxy Replay matched requests using this proxy.
-sni Target TLS SNI, does not support FUZZ keyword
-timeout HTTP request timeout in seconds. (default: 10)
-u Target URL
-x Proxy URL (SOCKS5 or HTTP). For example: http://127.0.0.1:8080 or socks5://127.0.0.1:8080
GENERAL OPTIONS:
-V Show version information. (default: false)
-ac Automatically calibrate filtering options (default: false)
-acc Custom auto-calibration string. Can be used multiple times. Implies -ac
-ach Per host autocalibration (default: false)
-ack Autocalibration keyword (default: FUZZ)
-acs Autocalibration strategy: "basic" or "advanced" (default: basic)
-c Colorize output. (default: false)
-config Load configuration from a file
-json JSON output, printing newline-delimited JSON records (default: false)
-maxtime Maximum running time in seconds for entire process. (default: 0)
-maxtime-job Maximum running time in seconds per job. (default: 0)
-noninteractive Disable the interactive console functionality (default: false)
-p Seconds of `delay` between requests, or a range of random delay. For example "0.1" or "0.1-2.0"
-rate Rate of requests per second (default: 0)
-s Do not print additional information (silent mode) (default: false)
-sa Stop on all error cases. Implies -sf and -se. (default: false)
-scraperfile Custom scraper file path
-scrapers Active scraper groups (default: all)
-se Stop on spurious errors (default: false)
-search Search for a FFUFHASH payload from ffuf history
-sf Stop when > 95% of responses return 403 Forbidden (default: false)
-t Number of concurrent threads. (default: 40)
-v Verbose output, printing full URL and redirect location (if any) with the results. (default: false)
MATCHER OPTIONS:
-mc Match HTTP status codes, or "all" for everything. (default: 200,204,301,302,307,401,403,405,500)
-ml Match amount of lines in response
-mmode Matcher set operator. Either of: and, or (default: or)
-mr Match regexp
-ms Match HTTP response size
-mt Match how many milliseconds to the first response byte, either greater or less than. EG: >100 or <100
-mw Match amount of words in response
FILTER OPTIONS:
-fc Filter HTTP status codes from response. Comma separated list of codes and ranges
-fl Filter by amount of lines in response. Comma separated list of line counts and ranges
-fmode Filter set operator. Either of: and, or (default: or)
-fr Filter regexp
-fs Filter HTTP response size. Comma separated list of sizes and ranges
-ft Filter by number of milliseconds to the first response byte, either greater or less than. EG: >100 or <100
-fw Filter by amount of words in response. Comma separated list of word counts and ranges
INPUT OPTIONS:
-D DirSearch wordlist compatibility mode. Used in conjunction with -e flag. (default: false)
-e Comma separated list of extensions. Extends FUZZ keyword.
-ic Ignore wordlist comments (default: false)
-input-cmd Command producing the input. --input-num is required when using this input method. Overrides -w.
-input-num Number of inputs to test. Used in conjunction with --input-cmd. (default: 100)
-input-shell Shell to be used for running command
-mode Multi-wordlist operation mode. Available modes: clusterbomb, pitchfork, sniper (default: clusterbomb)
-request File containing the raw http request
-request-proto Protocol to use along with raw request (default: https)
-w Wordlist file path and (optional) keyword separated by colon. eg. '/path/to/wordlist:KEYWORD'
OUTPUT OPTIONS:
-debug-log Write all of the internal logging to the specified file.
-o Write output to file
-od Directory path to store matched results to.
-of Output file format. Available formats: json, ejson, html, md, csv, ecsv (or, 'all' for all formats) (default: json)
-or Don't create the output file if we don't have results (default: false)
EXAMPLE USAGE:
Fuzz file paths from wordlist.txt, match all responses but filter out those with content-size 42.
Colored, verbose output.
ffuf -w wordlist.txt -u https://example.org/FUZZ -mc all -fs 42 -c -v
Fuzz Host-header, match HTTP 200 responses.
ffuf -w hosts.txt -u https://example.org/ -H "Host: FUZZ" -mc 200
Fuzz POST JSON data. Match all responses not containing text "error".
ffuf -w entries.txt -u https://example.org/ -X POST -H "Content-Type: application/json" \
-d '{"name": "FUZZ", "anotherkey": "anothervalue"}' -fr "error"
Fuzz multiple locations. Match only responses reflecting the value of "VAL" keyword. Colored.
ffuf -w params.txt:PARAM -w values.txt:VAL -u https://example.org/?PARAM=VAL -mr "VAL" -c
More information and examples: https://github.com/ffuf/ffuf
┌──(zyberpatrol㉿kali-zyberpatrol)-[~]
At a minimum we’re required to supply two options: -u to specify an URL and -w to specify a wordlist. The default keyword FUZZ is used to tell ffuf where the wordlist entries will be injected.
ffuf -u http://ip/FUZZ -w /opt/SecLists/Discovery/Web-Content/big.txt
ffuf -u http://ip/FUZZ -w /opt/SecLists/Discovery/Web-Content/big.txt:FUZZ
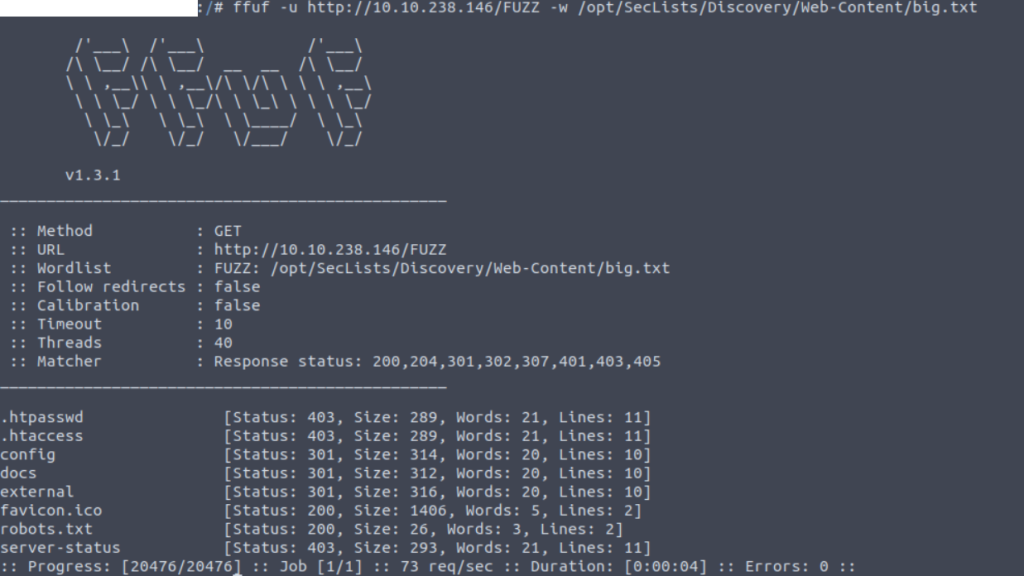
Finding pages and directories
ffuf -u http://172.16.1.120/FUZZ -w /opt/SecLists/Discovery/Web-Content/dict.txt
Recursive Scanning
When we scan recursively, it automatically starts another scan under any newly identified directories that may have on their pages until it has fuzzed the main website and all of its subdirectories.
ffuf -u http://172.16.1.120/dvwa/FUZZ -w /opt/SecLists/Discovery/Web-Content/dict.txt:FUZZ -recursion -recursion-depth 2 -e .php,.css -v -mc 200
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0-dev
________________________________________________
:: Method : GET
:: URL : http://172.16.1.120/dvwa/FUZZ
:: Wordlist : FUZZ: /opt/SecLists/Discovery/Web-Content/dict.txt
:: Extensions : .php .css
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200
________________________________________________
[INFO] Adding a new job to the queue: http://172.16.1.120/dvwa/css/FUZZ
[INFO] Adding a new job to the queue: http://172.16.1.120/dvwa/images/FUZZ
[INFO] Adding a new job to the queue: http://172.16.1.120/dvwa/includes/FUZZ
[Status: 200, Size: 1380, Words: 89, Lines: 19, Duration: 2ms]
| URL | http://172.16.1.120/dvwa/includes/
* FUZZ: includes/
[INFO] Adding a new job to the queue: http://172.16.1.120/dvwa/js/FUZZ
[INFO] Starting queued job on target: http://172.16.1.120/dvwa/css/FUZZ
[Status: 200, Size: 304, Words: 17, Lines: 26, Duration: 12ms]
| URL | http://172.16.1.120/dvwa/css/help.css
* FUZZ: help.css
[Status: 200, Size: 842, Words: 51, Lines: 60, Duration: 9ms]
| URL | http://172.16.1.120/dvwa/css/login.css
* FUZZ: login.css
[Status: 200, Size: 4026, Words: 267, Lines: 267, Duration: 13ms]
| URL | http://172.16.1.120/dvwa/css/main.css
* FUZZ: main.css
[INFO] Starting queued job on target: http://172.16.1.120/dvwa/images/FUZZ
[INFO] Starting queued job on target: http://172.16.1.120/dvwa/includes/FUZZ
[Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 3ms]
| URL | http://172.16.1.120/dvwa/includes/dvwaPhpIds.inc.php
* FUZZ: dvwaPhpIds.inc.php
[Status: 200, Size: 45, Words: 5, Lines: 1, Duration: 19ms]
| URL | http://172.16.1.120/dvwa/includes/dvwaPage.inc.php
* FUZZ: dvwaPage.inc.php
[INFO] Starting queued job on target: http://172.16.1.120/dvwa/js/FUZZ
:: Progress: [15453/15453] :: Job [5/5] :: 6451 req/sec :: Duration: [0:00:01] :: Errors: 5865 ::
Using Filters
-fc (filter code)
Below example filters out pages with 403 error. Pay attention while using -fc (-fc 403) as it may hide some important files.
┌──(zyberpatrol㉿kali-zyberpatrol)-[/opt]
└─$ ffuf -u http://172.16.1.120/dvwa/FUZZ -w /opt/SecLists/Discovery/Web-Content/dict.txt:FUZZ -fc 403
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0-dev
________________________________________________
:: Method : GET
:: URL : http://172.16.1.120/dvwa/FUZZ
:: Wordlist : FUZZ: /opt/SecLists/Discovery/Web-Content/dict.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response status: 403
________________________________________________
[Status: 301, Size: 315, Words: 20, Lines: 10, Duration: 3ms]
* FUZZ: css
[Status: 301, Size: 318, Words: 20, Lines: 10, Duration: 0ms]
* FUZZ: images
[Status: 301, Size: 320, Words: 20, Lines: 10, Duration: 1ms]
* FUZZ: includes
[Status: 200, Size: 1380, Words: 89, Lines: 19, Duration: 6ms]
* FUZZ: includes/
[Status: 301, Size: 314, Words: 20, Lines: 10, Duration: 0ms]
* FUZZ: js
:: Progress: [5151/5151] :: Job [1/1] :: 55 req/sec :: Duration: [0:00:04] :: Errors: 391 ::
┌──(zyberpatrol㉿kali-zyberpatrol)-[/opt]
└─$
-mc(match code)
Sometimes you might want to filter out multiple status codes such as 500, 302, 301, 401, etc. For instance, if you know you want to see 200 status code responses, you could use -mc 200 (match code) instead of having a long list of filtered codes.
┌──(zyberpatrol㉿kali-zyberpatrol)-[/opt]
└─$ ffuf -u http://172.16.1.120/dvwa/FUZZ -w /opt/SecLists/Discovery/Web-Content/dict.txt:FUZZ -recursion -recursion-depth 2 -e .php,.css -v -mc 200
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0-dev
________________________________________________
:: Method : GET
:: URL : http://172.16.1.120/dvwa/FUZZ
:: Wordlist : FUZZ: /opt/SecLists/Discovery/Web-Content/dict.txt
:: Extensions : .php .css
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200
________________________________________________
[INFO] Adding a new job to the queue: http://172.16.1.120/dvwa/css/FUZZ
[INFO] Adding a new job to the queue: http://172.16.1.120/dvwa/images/FUZZ
[INFO] Adding a new job to the queue: http://172.16.1.120/dvwa/includes/FUZZ
[Status: 200, Size: 1380, Words: 89, Lines: 19, Duration: 2ms]
| URL | http://172.16.1.120/dvwa/includes/
* FUZZ: includes/
[INFO] Adding a new job to the queue: http://172.16.1.120/dvwa/js/FUZZ
[INFO] Starting queued job on target: http://172.16.1.120/dvwa/css/FUZZ
[Status: 200, Size: 304, Words: 17, Lines: 26, Duration: 4ms]
| URL | http://172.16.1.120/dvwa/css/help.css
* FUZZ: help.css
[Status: 200, Size: 842, Words: 51, Lines: 60, Duration: 2ms]
| URL | http://172.16.1.120/dvwa/css/login.css
* FUZZ: login.css
[Status: 200, Size: 4026, Words: 267, Lines: 267, Duration: 4ms]
| URL | http://172.16.1.120/dvwa/css/main.css
* FUZZ: main.css
[INFO] Starting queued job on target: http://172.16.1.120/dvwa/images/FUZZ
[INFO] Starting queued job on target: http://172.16.1.120/dvwa/includes/FUZZ
[Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 4ms]
| URL | http://172.16.1.120/dvwa/includes/dvwaPhpIds.inc.php
* FUZZ: dvwaPhpIds.inc.php
[Status: 200, Size: 45, Words: 5, Lines: 1, Duration: 5ms]
| URL | http://172.16.1.120/dvwa/includes/dvwaPage.inc.php
* FUZZ: dvwaPage.inc.php
[INFO] Starting queued job on target: http://172.16.1.120/dvwa/js/FUZZ
:: Progress: [15453/15453] :: Job [5/5] :: 11764 req/sec :: Duration: [0:00:01] :: Errors: 5865 ::
┌──(zyberpatrol㉿kali-zyberpatrol)-[/opt]
└─$
Filtering files with zero (0) size with -fs 0
Unless we have a LFI (local file inclusion) this kind of files aren’t interesting, so we can use -fs 0 (filter size).
Vhost Fuzzing
The key difference between VHosts and sub-domains is that a VHost is basically a ‘sub-domain’ served on the same server and has the same IP, such that a single IP could be serving two or more different websites.
VHosts may or may not have public DNS records.
To scan for VHosts, without manually adding the entire wordlist to our /etc/hosts, we will be fuzzing HTTP headers, specifically the Host: header. To do that, we can use the -H flag to specify a header and will use the FUZZ keyword within it, as follows:
ffuf -w /opt/useful/SecLists/Discovery/DNS/subdomains-top1million-5000.txt:FUZZ -u http://nlabs.local:PORT/ -H 'Host: FUZZ.nlabs.local'
Subdomain Fuzzing
┌──(zyberpatrol㉿kali-zyberpatrol)-[/opt]
└─$ ffuf -u https://FUZZ.tekgenx.com -w /opt/SecLists/Discovery/DNS/subdomains-top1million-5000.txt
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0-dev
________________________________________________
:: Method : GET
:: URL : https://FUZZ.tekgenx.com
:: Wordlist : FUZZ: /opt/SecLists/Discovery/DNS/subdomains-top1million-5000.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
[Status: 200, Size: 37378, Words: 5626, Lines: 297, Duration: 228ms]
* FUZZ: webmail
[Status: 403, Size: 699, Words: 60, Lines: 14, Duration: 107ms]
* FUZZ: blog
Subdomain vs vhosts Enumeration commands
# Subdomain Enumeration
ffuf -u http://FUZZ.mydomain.com -c -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -fs 0
# vhosts Enumeration
ffuf -u http://mydomain.com -c -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -H 'Host: FUZZ.mydomain.com' -fs 0It is possible that we can’t find a sub-domain with direct subdomain enumeration (1st command) but that we can find it with vhost enumeration (2nd command).
Fuzzing Parameters
┌──(zyberpatrol㉿kali-zyberpatrol)-[~]
└─$ ffuf -u 'http://10.10.196.129/sqli-labs/Less-1/?FUZZ=1' -c -w /opt/SecLists/Discovery/Web-Content/burp-parameter-names.txt -fw 39
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.196.129/sqli-labs/Less-1/?FUZZ=1
:: Wordlist : FUZZ: /opt/SecLists/Discovery/Web-Content/burp-parameter-names.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response words: 39
________________________________________________
[Status: 200, Size: 721, Words: 37, Lines: 29, Duration: 33ms]
* FUZZ: id
:: Progress: [6453/6453] :: Job [1/1] :: 75 req/sec :: Duration: [0:00:11] :: Errors: 0 ::
┌──(zyberpatrol㉿kali-zyberpatrol)-[~]
└─$
Value Fuzzing
Now that we found a parameter accepting integer values we’ll start fuzzing values.
At this point, we could generate a wordlist and save a file containing integers. To cut out a step we can use -w - which tells ffuf to read a wordlist from stdout. This will allow us to generate a list of integers with a command of our choice then pipe the output to ffuf. Below is a list of 5 different ways to generate numbers 0 – 255.
$ ruby -e '(0..255).each{|i| puts i}' | ffuf -u 'http://10.10.196.129/sqli-labs/Less-1/?id=FUZZ' -c -w - -fw 33
$ ruby -e 'puts (0..255).to_a' | ffuf -u 'http://10.10.196.129/sqli-labs/Less-1/?id=FUZZ' -c -w - -fw 33
$ for i in {0..255}; do echo $i; done | ffuf -u 'http://10.10.196.129/sqli-labs/Less-1/?id=FUZZ' -c -w - -fw 33
$ seq 0 255 | ffuf -u 'http://10.10.196.129/sqli-labs/Less-1/?id=FUZZ' -c -w - -fw 33
$ cook '[0-255]' | ffuf -u 'http://10.10.196.129/sqli-labs/Less-1/?id=FUZZ' -c -w - -fw 33# save to ids.txt
for i in $(seq 1 1000); do echo $i >> ids.txt; doneExample Below:
┌──(zyberpatrol㉿kali-zyberpatrol)-[~]
└─$ ruby -e '(0..255).each{|i| puts i}' | ffuf -u 'http://10.10.196.129/sqli-labs/Less-1/?id=FUZZ' -c -w - -fw 33
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.196.129/sqli-labs/Less-1/?id=FUZZ
:: Wordlist : FUZZ: -
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response words: 33
________________________________________________
[Status: 200, Size: 721, Words: 37, Lines: 29, Duration: 38ms]
* FUZZ: 1
[Status: 200, Size: 726, Words: 37, Lines: 29, Duration: 38ms]
* FUZZ: 3
[Status: 200, Size: 725, Words: 37, Lines: 29, Duration: 40ms]
* FUZZ: 4
[Status: 200, Size: 731, Words: 37, Lines: 29, Duration: 41ms]
* FUZZ: 2
[Status: 200, Size: 723, Words: 37, Lines: 29, Duration: 41ms]
* FUZZ: 8
[Status: 200, Size: 725, Words: 37, Lines: 29, Duration: 42ms]
* FUZZ: 10
[Status: 200, Size: 725, Words: 37, Lines: 29, Duration: 1023ms]
* FUZZ: 9
[Status: 200, Size: 728, Words: 37, Lines: 29, Duration: 2047ms]
* FUZZ: 5
[Status: 200, Size: 725, Words: 37, Lines: 29, Duration: 3072ms]
* FUZZ: 11
[Status: 200, Size: 728, Words: 37, Lines: 29, Duration: 3072ms]
* FUZZ: 6
[Status: 200, Size: 725, Words: 37, Lines: 29, Duration: 3072ms]
* FUZZ: 12
[Status: 200, Size: 725, Words: 37, Lines: 29, Duration: 3994ms]
* FUZZ: 7
[Status: 200, Size: 725, Words: 37, Lines: 29, Duration: 3994ms]
* FUZZ: 14
:: Progress: [256/256] :: Job [1/1] :: 41 req/sec :: Duration: [0:00:05] :: Errors: 0 ::
Wordlist-based brute-force attacks
ffuf -u http://10.10.196.129/sqli-labs/Less-11/ -c -w /usr/share/seclists/Passwords/Leaked-Databases/hak5.txt -X POST -d 'uname=Dummy&passwd=FUZZ&submit=Submit' -fs 1435 -H 'Content-Type: application/x-www-form-urlencoded'
Example Usage:
Here we have to use the POST method (specified with -X) and to give the POST data (with -d) where we include the FUZZ keyword in place of the password.
We also have to specify a custom header -H 'Content-Type: application/x-www-form-urlencoded' because ffuf doesn’t set this content-type header automatically as curl does.
┌──(zyberpatrol㉿kali-zyberpatrol)-[~]
└─$ ffuf -u http://10.10.196.129/sqli-labs/Less-11/ -c -w /opt/SecLists/Passwords/Leaked-Databases/hak5.txt -X POST -d 'uname=Dummy&passwd=FUZZ&submit=Submit' -fs 1435 -H 'Content-Type: application/x-www-form-urlencoded'
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0-dev
________________________________________________
:: Method : POST
:: URL : http://10.10.196.129/sqli-labs/Less-11/
:: Wordlist : FUZZ: /opt/SecLists/Passwords/Leaked-Databases/hak5.txt
:: Header : Content-Type: application/x-www-form-urlencoded
:: Data : uname=Dummy&passwd=FUZZ&submit=Submit
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response size: 1435
________________________________________________
[Status: 200, Size: 1526, Words: 100, Lines: 50, Duration: 32ms]
* FUZZ: p@ssword
:: Progress: [2351/2351] :: Job [1/1] :: 342 req/sec :: Duration: [0:00:05] :: Errors: 0 ::
Proxifying ffuf traffic
# -x --> Proxy URL
ffuf -u http://10.10.19.168/ -c -w /usr/share/seclists/Discovery/Web-Content/common.txt -x http://127.0.0.1:8080
# Replay matched requests using this proxy
ffuf -u http://10.10.19.168/ -c -w /usr/share/seclists/Discovery/Web-Content/common.txt -replay-proxy http://127.0.0.1:8080

