Views: 152
In the realm of cybersecurity, especially within red teaming and penetration testing, Command and Control (C2) frameworks are pivotal. They facilitate the management of compromised systems, enabling operators to execute commands, maintain persistence, and exfiltrate data. Among the various C2 frameworks available, Covenant C2 stands out due to its unique features and capabilities.
🔍 Understanding Command & Control (C2) Frameworks
At its core, a C2 framework is akin to a Netcat listener but designed to handle multiple reverse shells concurrently. Unlike basic tools, C2 frameworks often include specialized payload generators and support for common network protocols like HTTP, HTTPS, and DNS. They also offer advanced session management and post-exploitation features.
Key Components of a C2 Framework:
- C2 Server: Acts as the central hub where agents connect to receive commands.
- Agents/Payloads: Programs generated by the C2 framework that establish a connection back to the server.
- Listeners: Applications running on the C2 server, waiting for incoming connections over specific protocols.
- Beacons: The process of an agent connecting back to the listener.
🛡️ Introduction to Covenant C2
Covenant is a .NET-based C2 framework designed to highlight the attack surface of .NET applications and facilitate offensive .NET tradecraft. It serves as a collaborative platform for red teamers, offering several distinguishing features:
Intuitive Web Interface: Provides a user-friendly dashboard for managing operations.
- Multi-User Collaboration: Allows multiple users to interact with the same server, either independently or collaboratively.
- Listener Profiles: Enables customization of network communication between agents and listeners.
- Encrypted Key Exchange: Implements secure communication channels between agents and listeners.
- Dynamic Compilation: Utilizes the Roslyn API for real-time C# code compilation and obfuscation.
- Tracking Indicators: Monitors and summarizes actions during operations for deconfliction and educational purposes.
🧰 Built-in Tools and Capabilities
Covenant C2 comes equipped with several pre-installed tools to aid in post-exploitation activities:
- Mimikatz: For credential extraction.
- PowerSploit: A collection of PowerShell scripts for exploitation.
- Nishang: PowerShell scripts for offensive security.
- SharpUp: Tools for privilege escalation.
These tools can be executed directly from the agent’s shell, eliminating the need to manually upload binaries.
🧠 Advanced Features
Listener Profiles
Covenant allows the creation of listener profiles, enabling customization of how agents communicate with listeners. This feature helps in evading detection by mimicking legitimate traffic patterns.
Encrypted Key Exchange
The framework employs an encrypted key exchange mechanism, ensuring secure communication between agents and listeners. This approach enhances the confidentiality and integrity of the data transmitted.
Dynamic Compilation
Covenant utilizes the Roslyn API for dynamic C# code compilation. This method compiles and obfuscates code in real-time, reducing the risk of detection by signature-based security solutions.
Tracking Indicators
The framework tracks various indicators throughout an operation, providing a comprehensive overview of actions taken. This feature is valuable for debriefing and improving future operations.
🕵️♂️ Covenant C2 LAB Setup

🛠️ Installating Covenant C2 on Kali Linux using Docker
Covenant C2 can be installed using two primary methods:
1. Docker Installation on Kali Linux
Execute the following commands to setup Docker on Kali Linux machine.
docker-ce can be installed from Docker repository. One thing to bear in mind, Kali Linux is based on Debian, so we need to use Debian’s current stable version (even though Kali Linux is a rolling distribution). At the time of writing (Dec. 2023), its “bookworm”:
echo "deb [arch=amd64 signed-by=/etc/apt/keyrings/docker.gpg] https://download.docker.com/linux/debian bookworm stable" | \
sudo tee /etc/apt/sources.list.d/docker.list Import the gpg key:
curl -fsSL https://download.docker.com/linux/debian/gpg |
sudo gpg --dearmor -o /etc/apt/keyrings/docker.gpgInstall the latest version of docker-ce:
sudo apt update
sudo apt install -y docker-ce docker-ce-cli containerd.ioVerify the status of Docker:
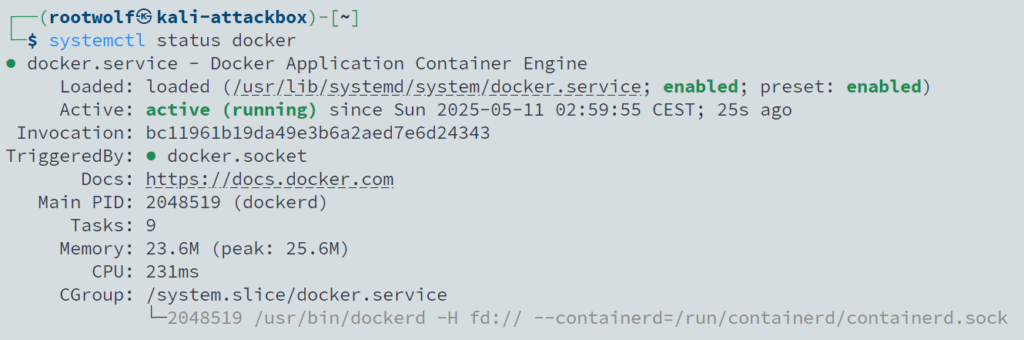
2. Covenant Installation
Using Docker simplifies the setup process and avoids dependency issues.
First, build the docker image using the following commands:
git clone --recurse-submodules https://github.com/cobbr/Covenant
cd Covenant/Covenant
docker build -t covenant .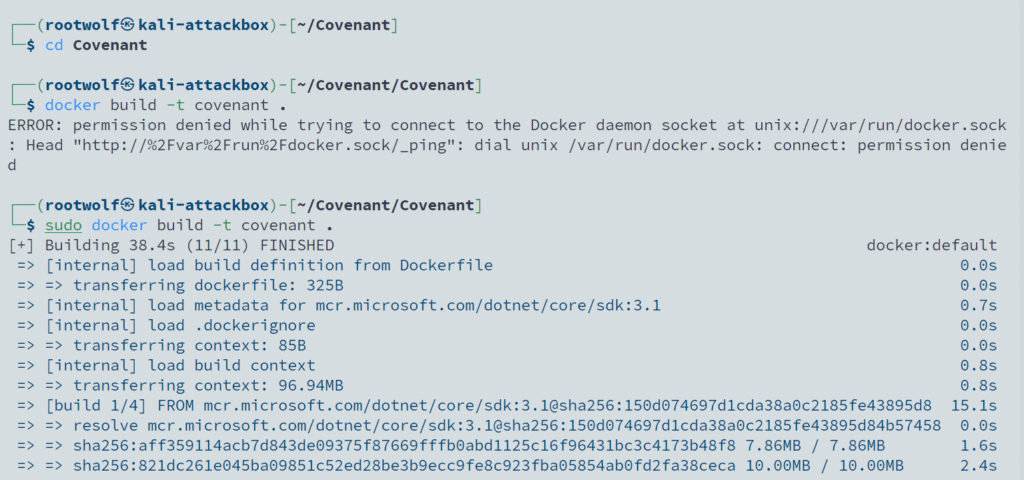
Now, run Covenant within the Docker container (be sure to replace the “</absolute/path/to/Covenant/Covenant/Data>” with your absolute path!)”:
docker run -it -p 7443:7443 -p 80:80 -p 443:443 — name covenant -v </absolute/path/to/Covenant/Covenant/Data>:/app/Data covenantMake sure you provide the absolute path to the directory, not a relative one.
In my case, the relevant path is /home/rootwolf/Covenant/Covenant/Data ; so the final command is,
docker run -it -p 7443:7443 -p 80:80 -p 443:443 --name covenant -v /home/rootwolf/Covenant/Covenant/Data:/app/Data covenantReplace </absolute/path/to/Covenant/Covenant/Data> with the actual path to your data directory. After running these commands, Covenant will be accessible via https://127.0.0.1:7443.
🧰 Accessing Covenant C2
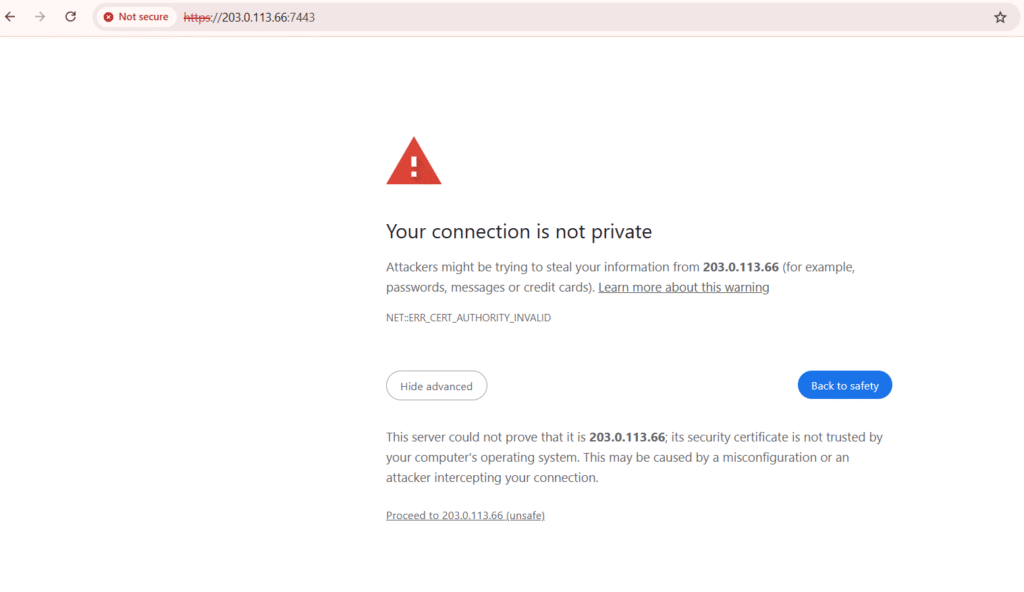
Ignore the security warning and proceed forward to the Covenant Home screen.

After starting Covenant, you must register an initial user through the web interface. The Home page will allow you to register the initial user.

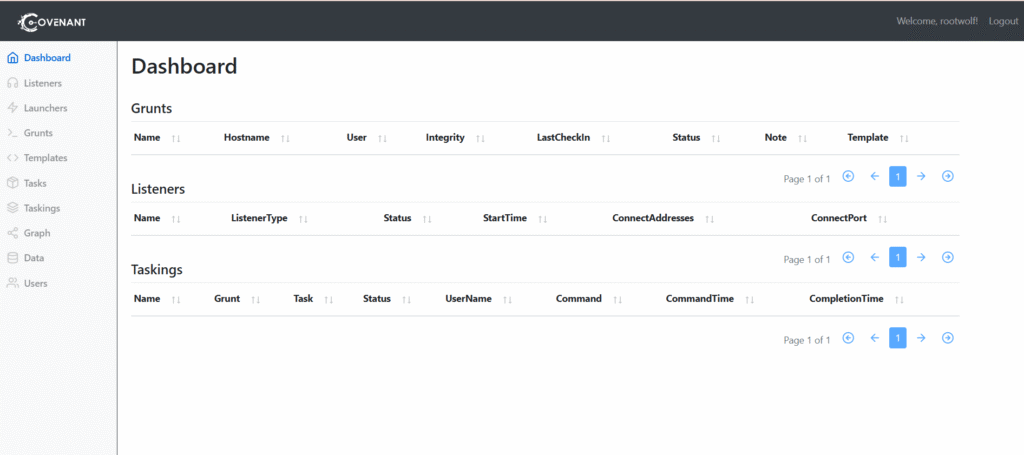
If everything goes well you’ll see this dashboard & Welkom to Covenant C2!
User Management
Covenant Users should be created for each operator to enable collaboration and so that actions can be tracked by operators.
Click on the “Users” navigation page in the sidebar to view a list of current users:
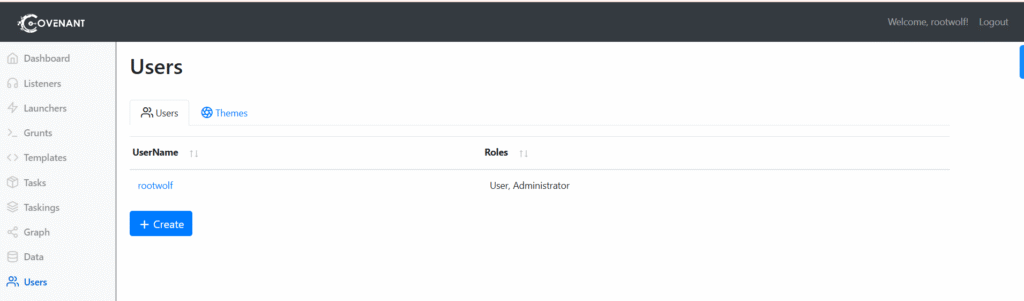
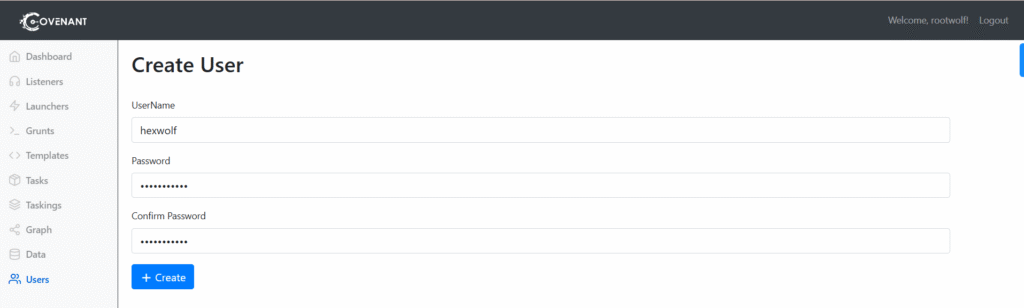

Yoc can manage the Themes and User roles by clicking on the user account
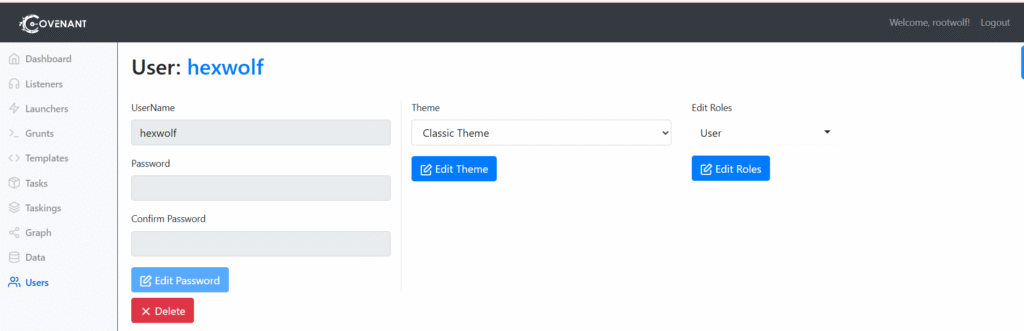
The following roles can be applied to a user:
Administrator — An Administrator has the privileges to conduct user management such as creating and editing Covenant Users.
User — A User can conduct operations on active Grunts.
Listener — The Listener role is only used for Listeners, who must have an account to use Covenant’s API, but is not needed for operators.
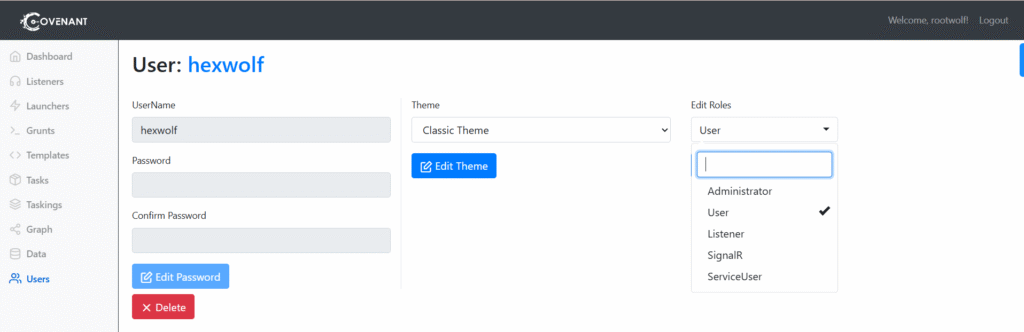
(Note: We see two more roles listed in the drop-down, however there are no references about these roles in Covenant C2 documentation).
End of PART-I.


