Views: 63
Introduction to Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) is a cybersecurity solution designed to detect, investigate, and respond to threats at the endpoint level. Endpoints include devices like laptops, desktops, servers, and mobile devices that connect to an organization’s network. These are often the primary targets for attackers, making them a critical focus for security teams.
EDR solutions offer real-time monitoring and collection of endpoint data to identify suspicious activity and mitigate threats before they can cause significant harm. Unlike traditional antivirus software, which focuses on preventing known threats, EDR emphasizes proactive threat detection, detailed investigation, and rapid response to advanced and evolving cyberattacks.
The main functions of an EDR are:
- Monitor and collect activity data from endpoints that could indicate a threat.
- Analyse this data to identify threat patterns.
- Automatically respond to identified threats, remove or contain them, and notify security personnel.
- Forensics and analysis tools to research identified threats and search for suspicious activities.
Components of EDR solutions
EDR vendors would classify their capabilities differently. However, the following are the common classifications:
- Detection: Fundamentally, EDR solutions are tasked with threat detection. For example, with file analysis, EDRs can flag suspicious files at the sight of any malicious behaviour. The detection process is also based on how good the threat intelligence sources are.
- Response/ Containment: EDRs provide response features that help investigate, detect, remediate and contain threats. The actions here include host segmentation, file deletion/cleanup and conducting investigations through sandboxing conditions. Advanced EDR solutions have the capability to trigger an automated response based on a set of preconfigured rules.
- Integration: EDRs extend endpoint visibility through the collection and aggregation of data. Therefore, in addressing endpoint security, EDR solutions need to work smoothly with existing security solutions in an organisation.
- Insights: Real-time analysis of events is becoming very common, providing a rapid evaluation and correlation of threat data. Through complex machine learning and artificial intelligence algorithms, EDR solutions can automate threat identification and perform behavioural analysis, mapping them to frameworks such as the MITRE ATT&CK.
- Forensics: In-depth investigation of past threats provides valuable information on the inner workings of exploits and how a breach was successful. With this, EDR solutions can outline threat timelines and identify lurking threats that go undetected.
Modern EDR platforms are increasingly integrating advanced technologies such as machine learning and artificial intelligence to enhance detection accuracy and response times.
In your exploration of EDR solutions, LimaCharlie stands out as a powerful, flexible platform designed to cater to evolving cybersecurity needs. It offers endpoint visibility and control while embracing a “Security Infrastructure as a Service” model, enabling security teams to build custom solutions tailored to their organization’s unique challenges.
This post dives deeper into LimaCharlie’s features, benefits, and how it empowers security teams to implement robust endpoint protection.
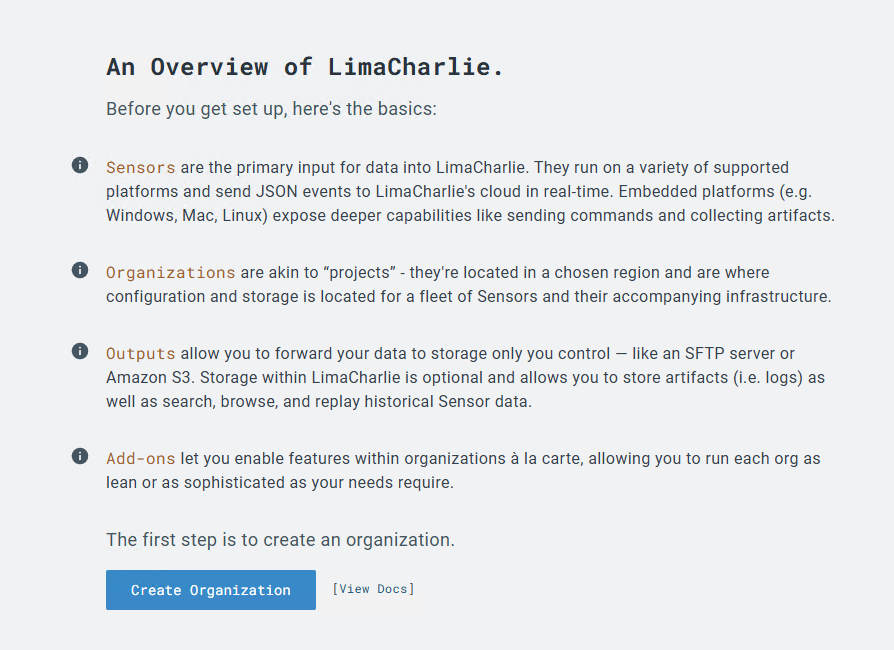
Setup Lima Charlie
Create a free account in the Lima Charlie App portal, https://app.limacharlie.io/login
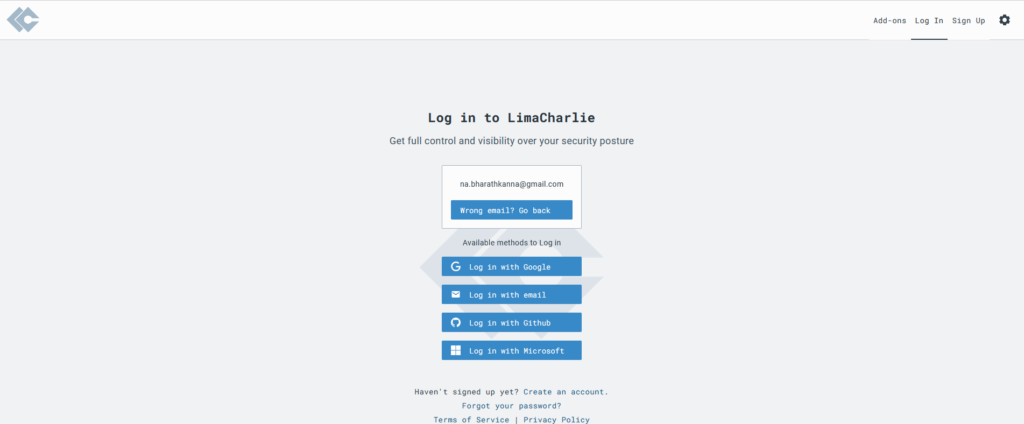
Alternatively, you can also use Google, Microsoft and Github accounts to setup your Lima Charlie account.
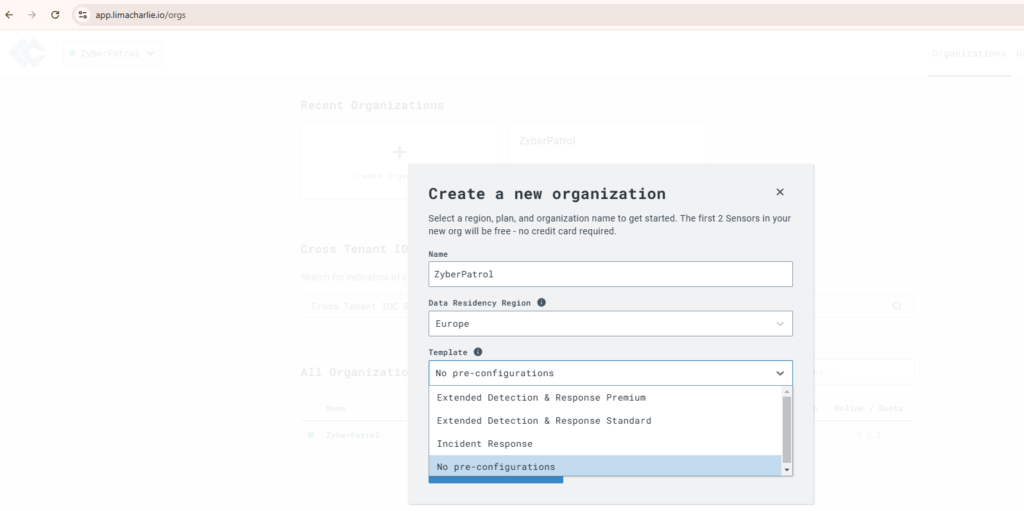
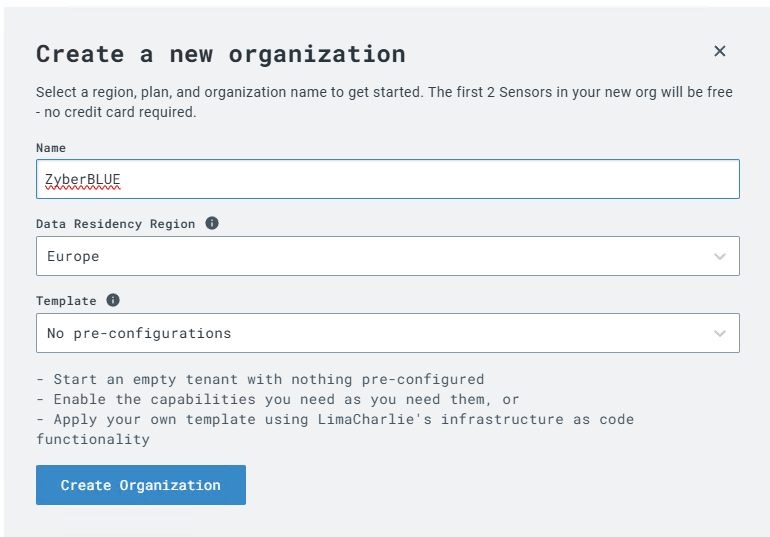
Create your organization.
Note: You can select any of the templates while setting up the organization. This can be changed later.
Create Sensors,
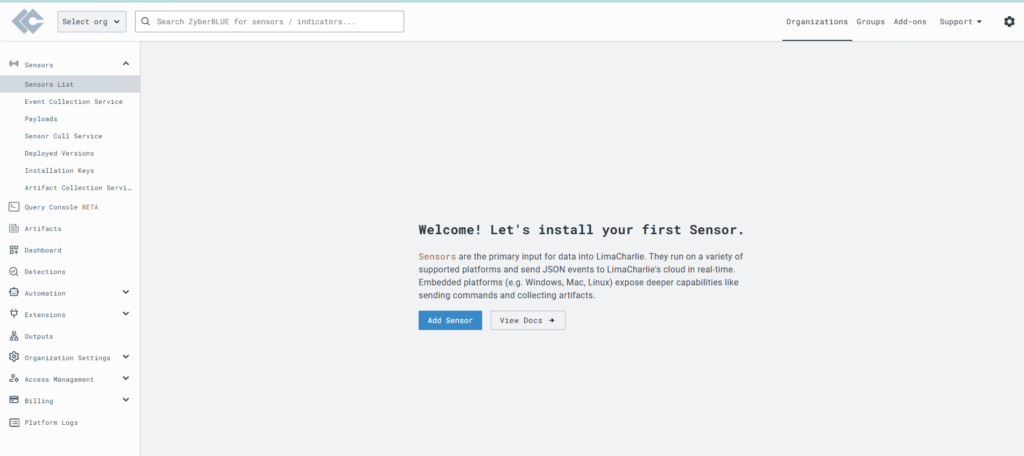
Choose a Sensor Type:
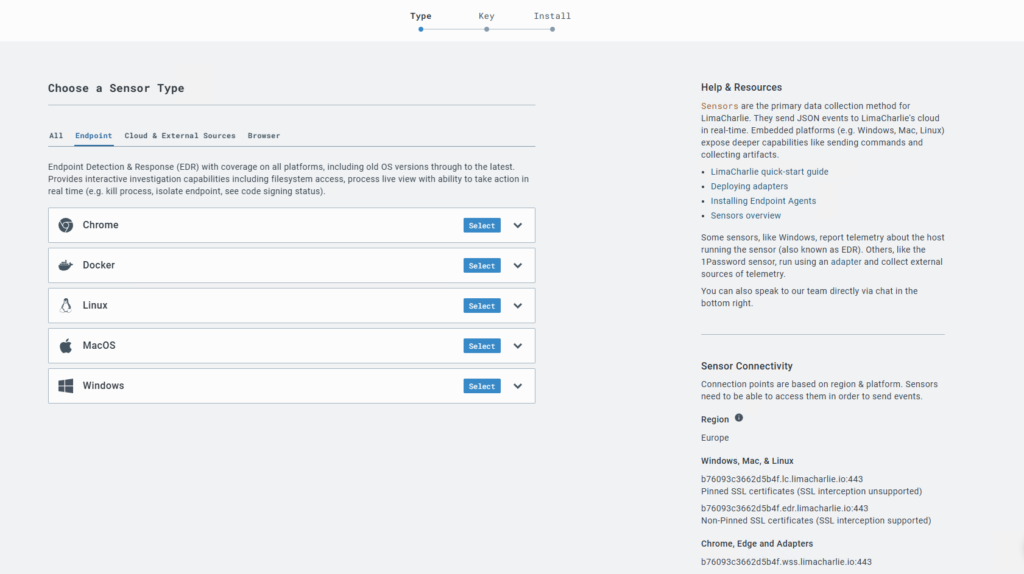
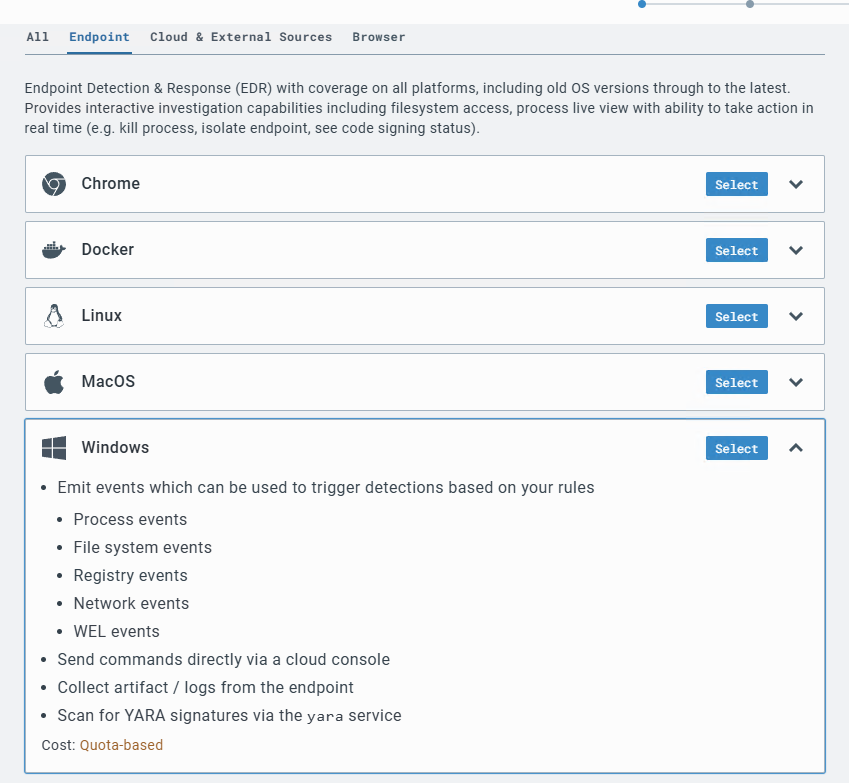
I have chosen “Windows” Sensor under Endpoint category.
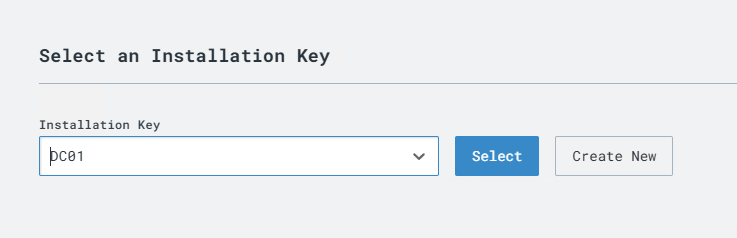
Create an Installation Key. I am using the “Create New” option.
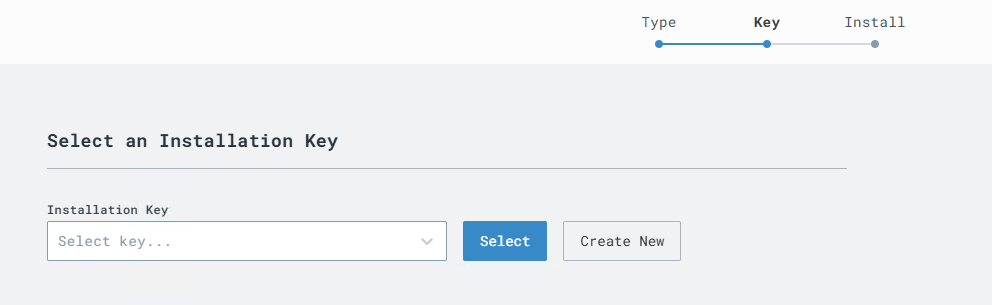
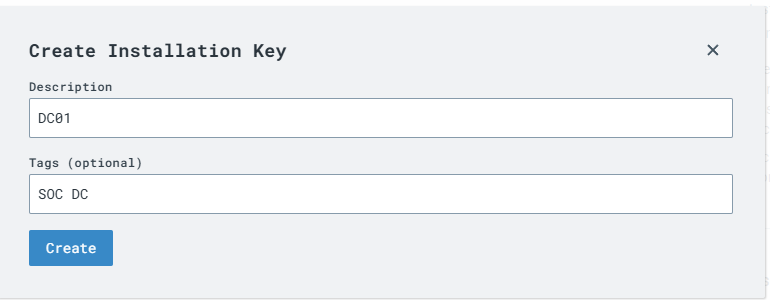
Key has been created, now select the key qnd press SELECT.
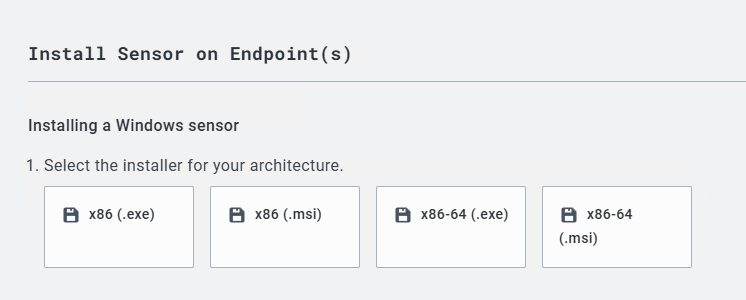
Install Sensor on Endpoints. Now select the appropriate installer type. In my case it’s x86-64.exe.
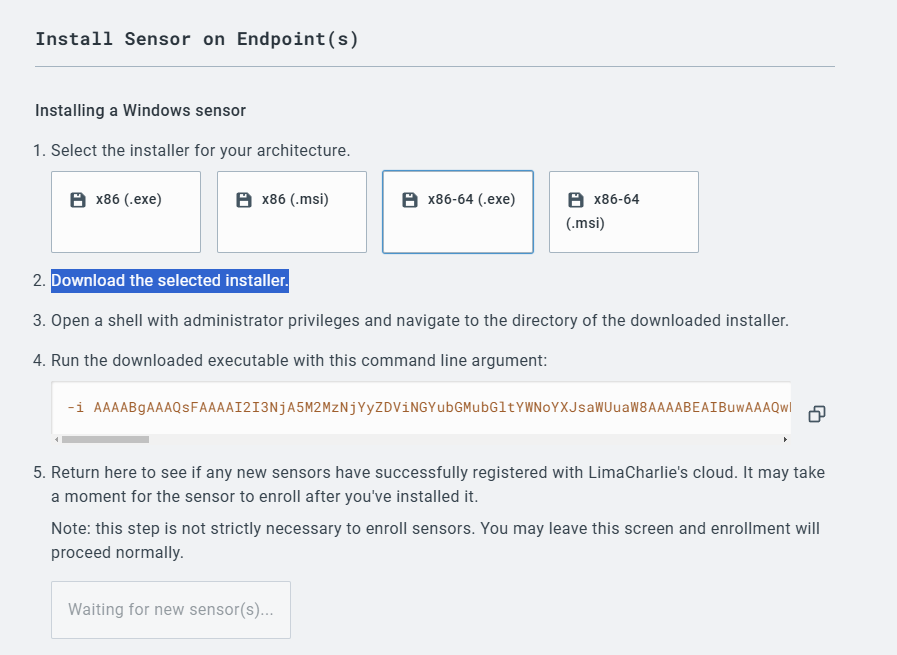
Download the appropriate installer from the link. Also, copy the installation key.
Install the downloaded agent on the endpointwith the installation key (with option -i).
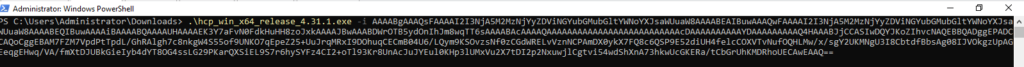
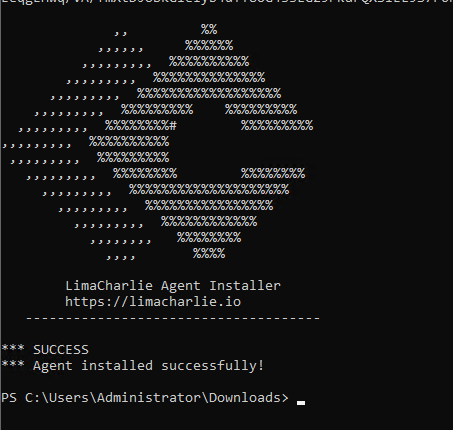
Agent installed and Endpoint is now reporting to the Lima Charlie portal.
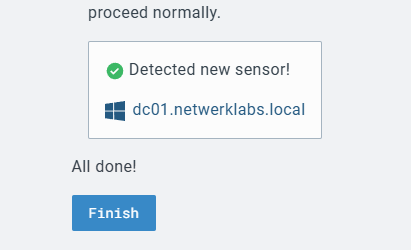
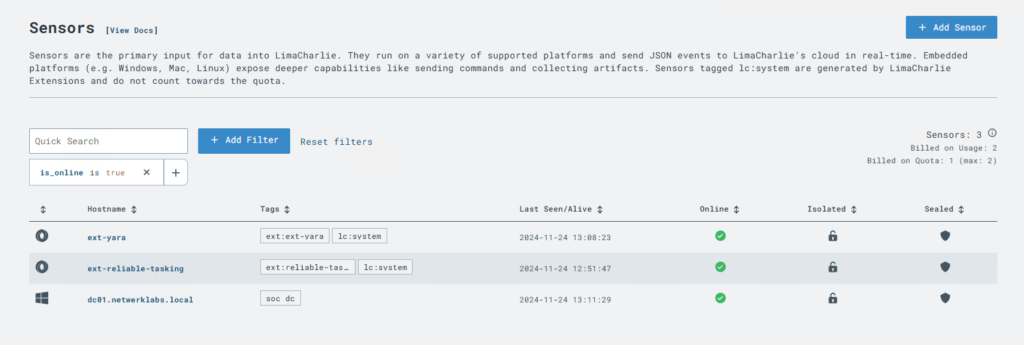
Endpoint details as seen in the console.
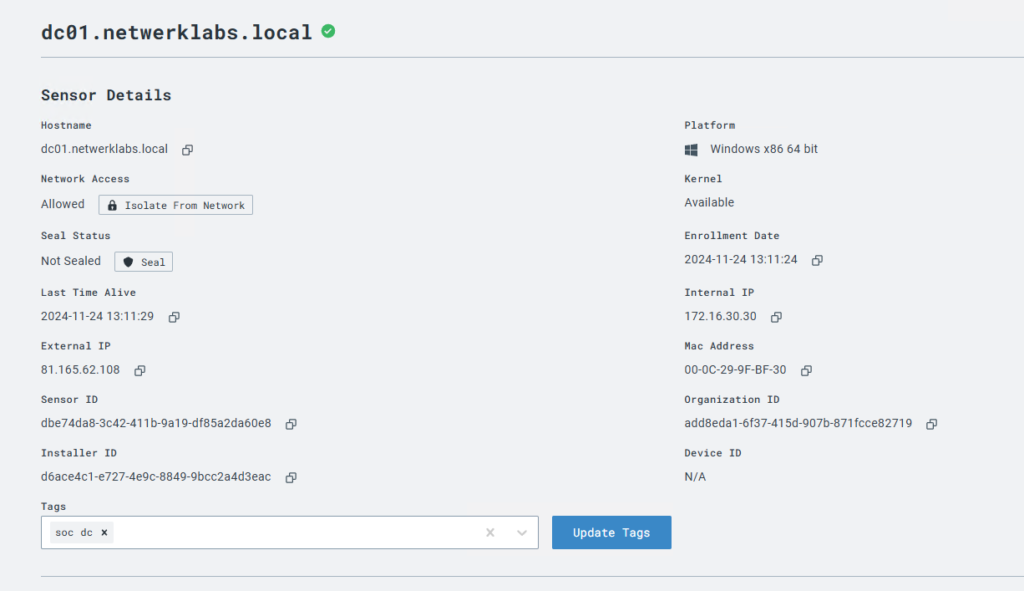
Interesting Telemetry from the Endpoint:
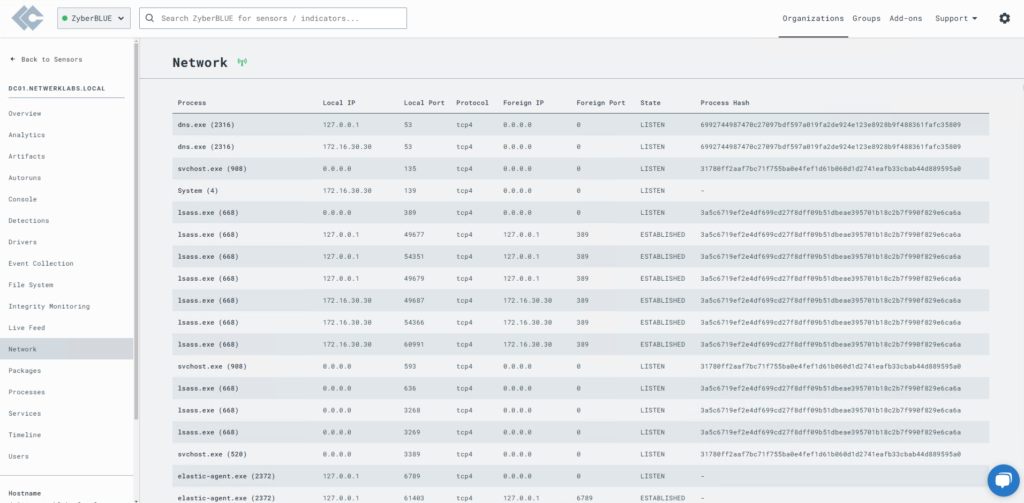
Network
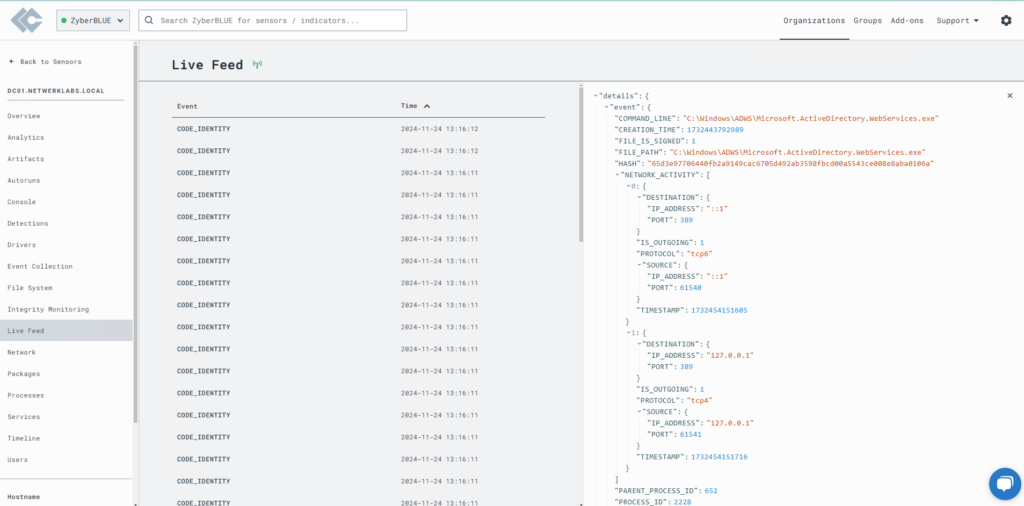
Live Feed
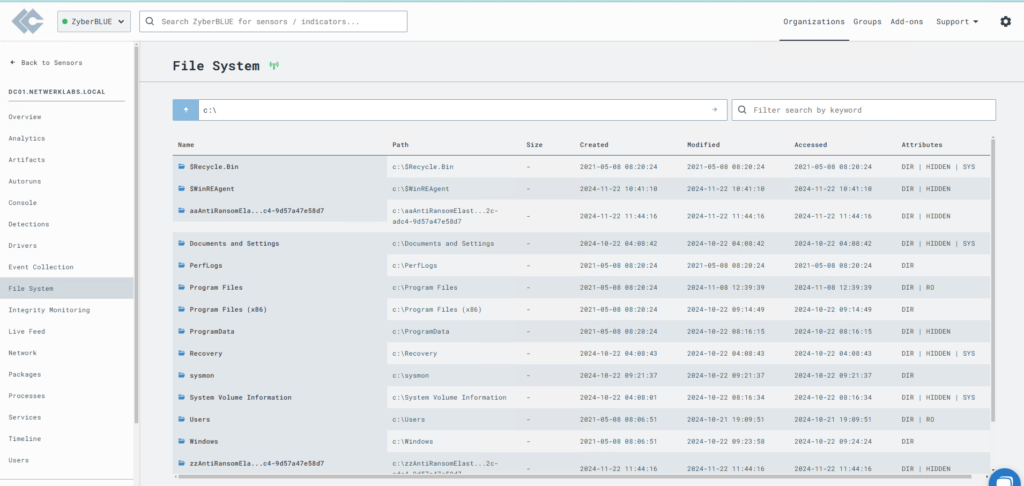
FileSystem Inventory
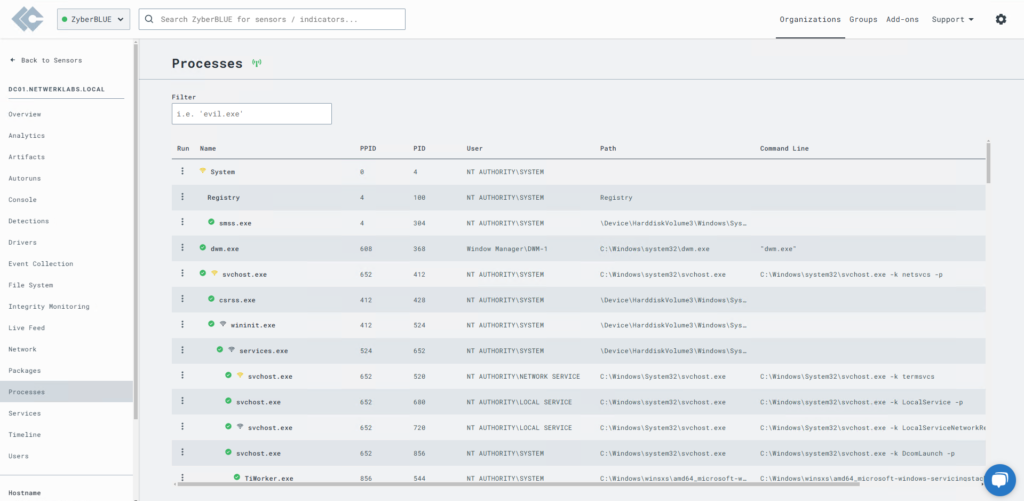
Processes
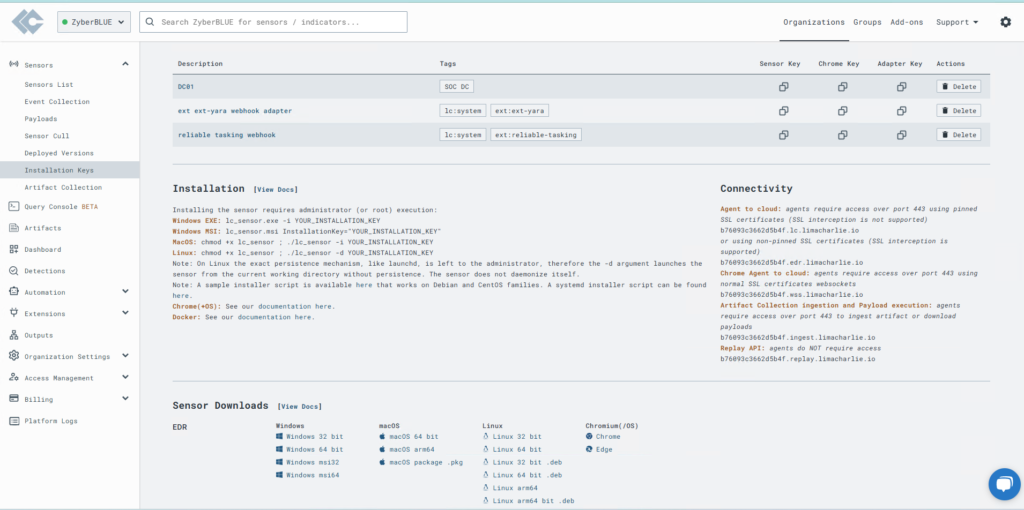
Find your Installation Keys