Views: 32
NIST – Security Incident Handling
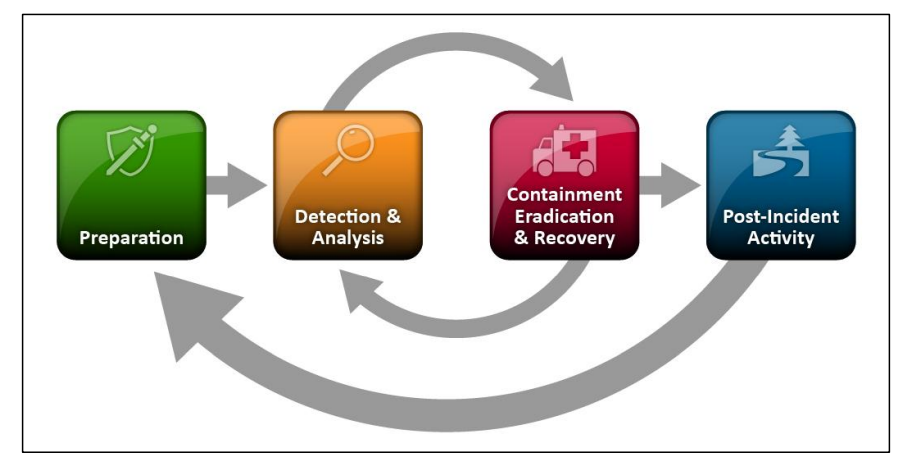
1. Preparation
The preparation phase covers the readiness of an organization against an attack. That means documenting the requirements, defining the policies, incorporating the security controls to monitor like EDR / SIEM / IDS / IPS, etc. It also includes hiring/training the staff.
2. Detection and Analysis
The detection phase covers everything related to detecting an incident and the analysis process of the incident. This phase covers getting alerts from the security controls like SIEM/EDR investigating the alert to find the root cause. This phase also covers hunting for the unknown threat within the organization.
3. Containment, Eradication, and Recovery
This phase covers the actions needed to prevent the incident from spreading and securing the network. It involves steps taken to avoid an attack from spreading into the network, isolating the infected host, clearing the network from the infection traces, and gaining control back from the attack.
4. Post-Incident Activity / Lessons Learnt
This phase includes identifying the loopholes in the organization’s security posture, which led to an intrusion, and improving so that the attack does not happen next time. The steps involve identifying weaknesses that led to the attack, adding detection rules so that similar breach does not happen again, and most importantly, training the staff if required.
Cyber Kill Chain
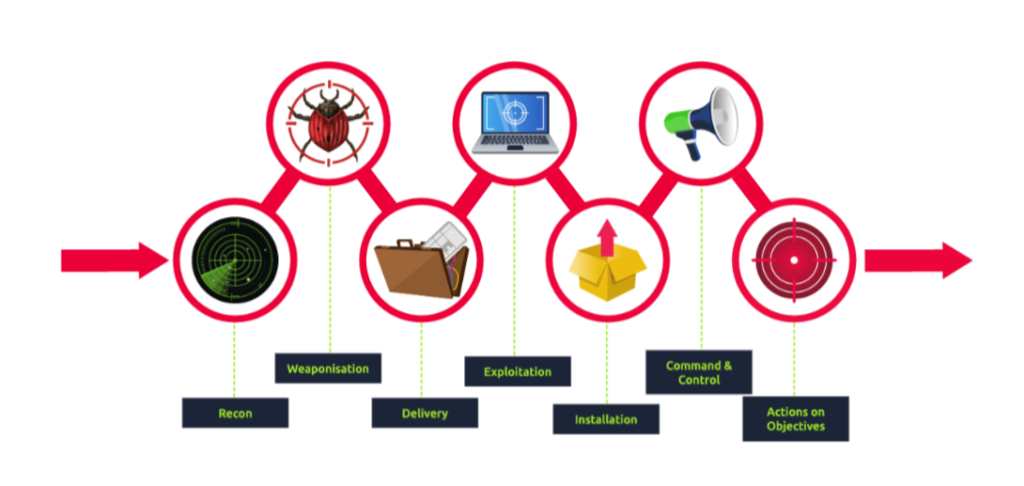
We can follow the Cyber kill Chain Model and map the attacker’s activity in each phase during this Investigation. When required, we will also utilize Open Source Intelligence (OSINT) and other findings to fill the gaps in the kill chain. It is not necessary to follow this sequence of the phases while investigating.
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command & Control
- Actions on Objectives
Interesting log sources
Some of the interesting log sources that will help us in our Investigation are:
| Log Sources | Details |
| wineventlog | It contains Windows Event logs |
| winRegistry | It contains the logs related to registry creation / modification / deletion etc. |
| XmlWinEventLog | It contains the sysmon event logs. It is a very important log source from an investigation point of view. |
| fortigate_utm | It contains Fortinet Firewall logs |
| iis | It contains IIS web server logs |
| Nessus:scan | It contains the results from the Nessus vulnerability scanner. |
| Suricata | It contains the details of the alerts from the Suricata IDS. This log source shows which alert was triggered and what caused the alert to get triggered— a very important log source for the Investigation. |
| stream:http | It contains the network flow related to http traffic. |
| stream: DNS | It contains the network flow related to DNS traffic. |
| stream:icmp | It contains the network flow related to icmp traffic. |
