Views: 229
OpenCTI is an open source platform allowing organizations to manage their cyber threat intelligence knowledge and observables. OpenCTI is designed to provide organizations with the means to manage CTI through the storage, analysis, visualization and presentation of threat campaigns, malware and IOCs.
Developed by the collaboration of the French National cybersecurity agency (ANSSI), the platform’s main objective is to create a comprehensive tool that allows users to capitalise on technical and non-technical information while developing relationships between each piece of information and its primary source. The platform can use the MITRE ATT&CK framework to structure the data. Additionally, it can be integrated with other threat intel tools such as MISP and TheHive.
OpenCTI Data Model
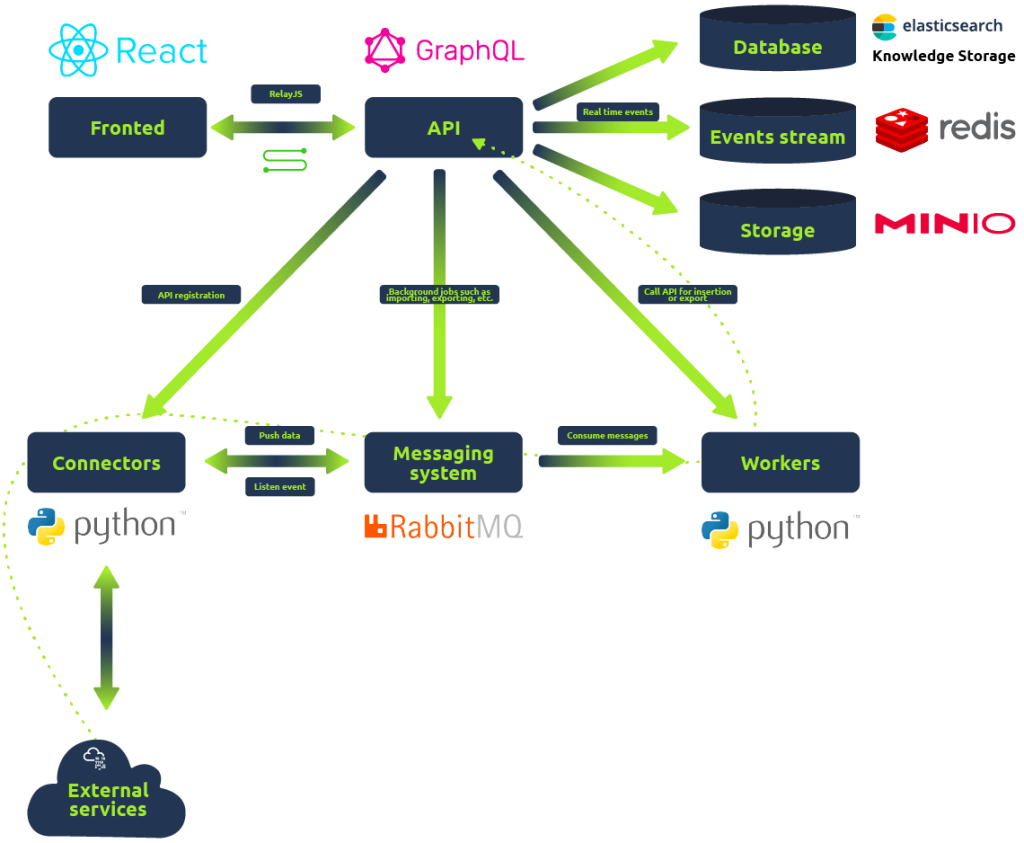
- GraphQL API: The API connects clients to the database and the messaging system.
- Write workers: Python processes utilised to write queries asynchronously from the RabbitMQ messaging system.
- Connectors: Another set of Python processes used to ingest, enrich or export data on the platform. These connectors provide the application with a robust network of integrated systems and frameworks to create threat intelligence relations and allow users to improve their defence tactics.
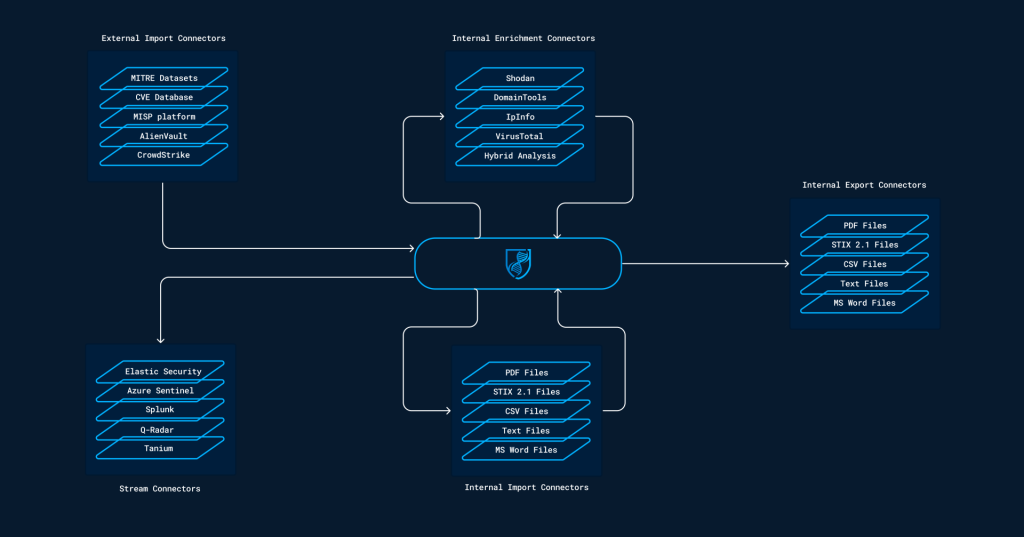
OpenCTI Connectors
| Class | Description | Examples |
|---|---|---|
| External Input Connector | Ingests information from external sources | CVE, MISP, TheHive, MITRE |
| Stream Connector | Consumes platform data stream | History, Tanium |
| Internal Enrichment Connector | Takes in new OpenCTI entities from user requests | Observables enrichment |
| Internal Import File Connector | Extracts information from uploaded reports | PDFs, STIX2 Import |
| Internal Export File Connector | Exports information from OpenCTI into different file formats | CSV, STIX2 export, PDF |
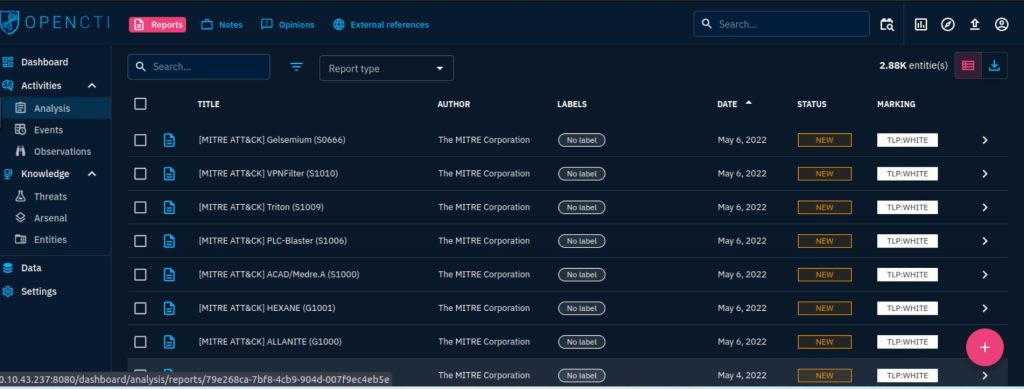
OpenCTI Dashboard
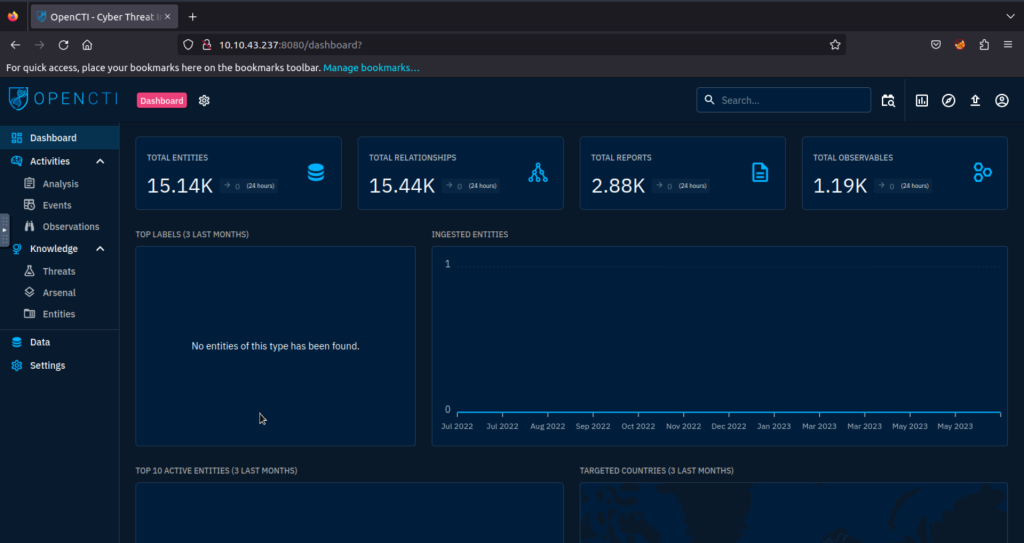
Activities
The activities section covers security incidents ingested onto the platform in the form of reports. It makes it easy for analysts to investigate these incidents.
Analysis