Views: 18
RMM software used in phishing attacks
Remote Monitoring & Management (RMM) software, including popular tools like AnyDesk, Atera, and Splashtop, are invaluable for IT administrators today, streamlining tasks and ensuring network integrity from afar. However, these same tools have caught the eye of cybercriminals, who exploit them to infiltrate company networks and pilfer sensitive data.
The modus operandi of these threat actors involves deceiving employees through sophisticated scams and deceptive online advertisements. Unsuspecting employees, misled by these tactics, may inadvertently invite these criminals into their systems. By convincing employees to download and run these seemingly benign RMM applications under the guise of fixing non-existent issues, these fraudsters gain unfettered access to the company’s network.
Indicators of Compromise
Phishing domains
uk-barclaysliveteam[.]com
barclaysbusinesslivechat[.]com
boi-bb-onlineservice[.]com
santanderbusiness-helpcentre[.]comUsers are directed to newly registered websites that mimic their financial institution. In order to get support, they need to download remote desktop software disguised as a ‘live chat application’.
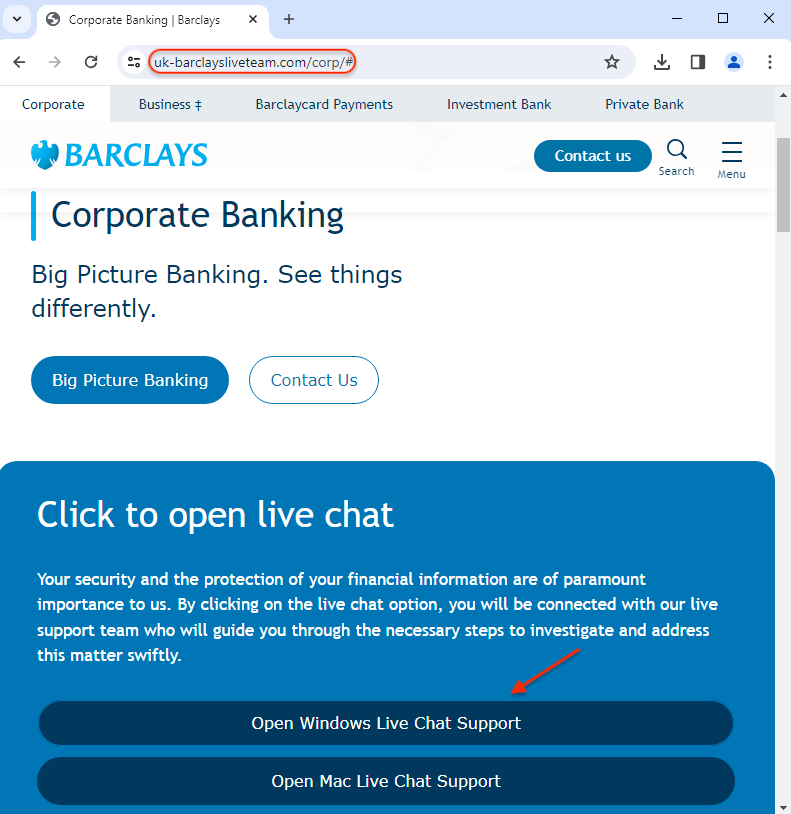
Mitigation
Adopt a robust defense stance by blocking all unnecessary applications using EDR products. Particularly, configuring the EDR to immediately block these RMM tools network-wide.



