Views: 82
LAB Setup
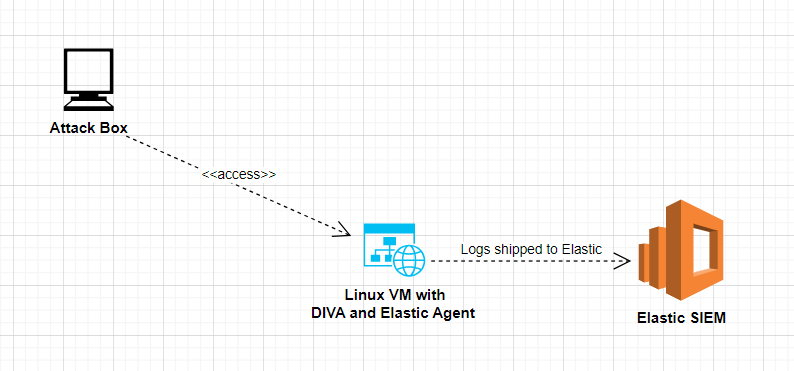
Let’s use the DIWA ( Deliberately Insecure Web Application) vulnerable created by Tim Steufmehl , to setup the victim machine.
Prepare a Linux machiine with Docker installed. Follow the these instructions to install Docker on Ubuntu.
# Create a folder/directory for the App
mkdir directory_name
cd directory_name
#Clone the DIWA app files from Github repository
git clone https://github.com/snsttr/diwa.git
#Create a Docker compose file (named docker-compose.yaml) with the below contents. This file should be placed one folder above the DIWA folder. Use any port for the webapp as per your choice
version: "3.8"
services:
webapp:
build:
context: ./diwa
ports:
- 80:80
volumes:
- /var/log/apache2:/var/log/apache2
#Folder contents after completing the above steps
zyber@diwa:~/apps/diwa$ ls
diwa docker-compose.yaml
#(Optional) Install Docker Compose if it's not already installed
sudo apt install docker-compose
#Start the DIWA app using the following command
docker compose up -d
#The above command will install and run the DIWA app. Final output of the cmd will be similar to the below (note, this is not the full output)
.
.
.
.
.
.
=> => writing image sha256:b3bbfaa48a275fbc4e7b75d278e797d0615ef60df40bde53699cd026e91bdea7 0.0s
=> => naming to docker.io/library/diwa-webapp 0.0s
[+] Running 1/2
⠇ Network diwa_default Created 0.8s
✔ Container diwa-webapp-1 Started With the above steps, the DIWA app should be UP and running on the Linux VM. Let’s test it by accessing the homepage http://<ip-of-the-vm> from the Attack Box.
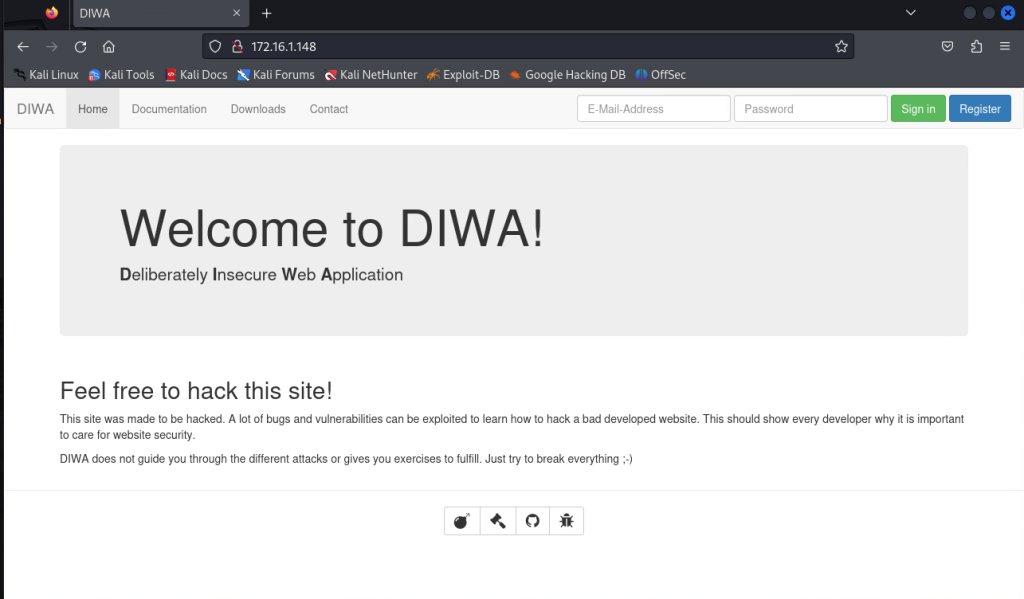
DIWA is a Deliberately Insecure Web Application, which was built for educational purpose. It has lot of security vulnerabilities including “Sensitive Data Exposure”. We are going to use this Sensitive Data Exposure case for our detection.
The DIWA app has a secret/sensitive page, secret-xu2d7a.php. We are going to develop detections for any users gaining access to the sensitive file secret-xu2d7a.php.
Elastic SIEM Agent Policy Creation: To collect Apache webserver logs and Network Traffic
DIWA is using a Apache webserver. Apache webserver is typically configured to log requests to /var/log/apache2/access.log location and it uses the Common Log Format (CLF).
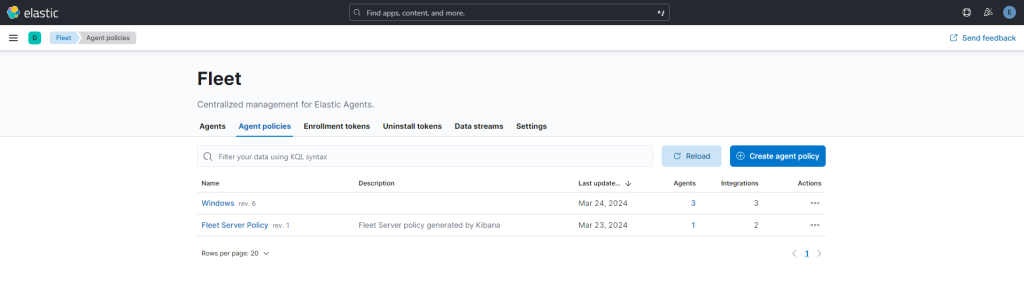
Create a Agent Policy using the defaults options.
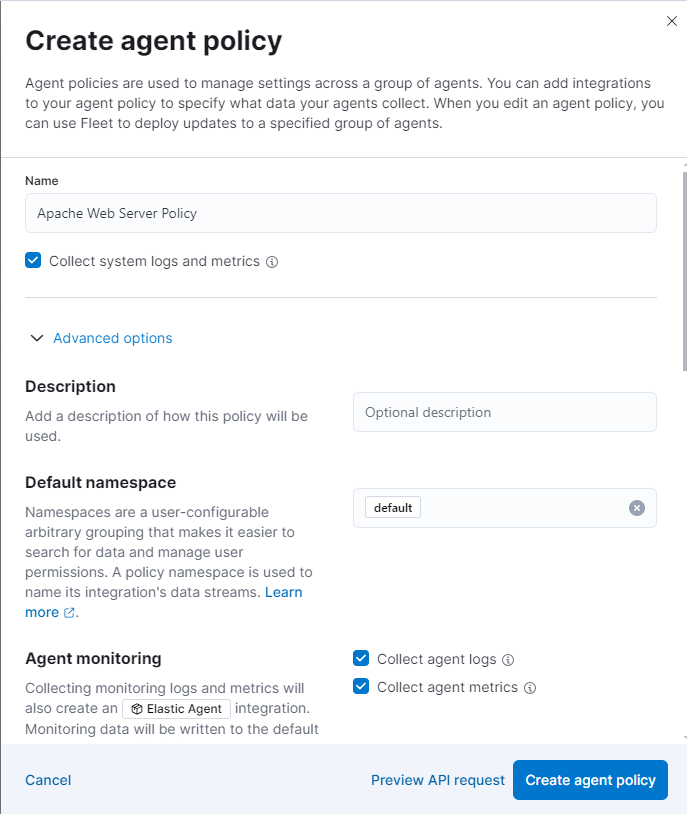
A new policy is created now.
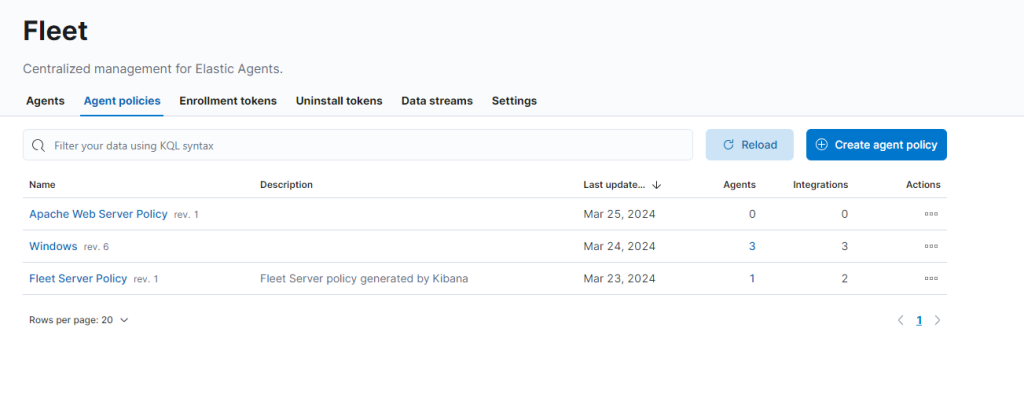
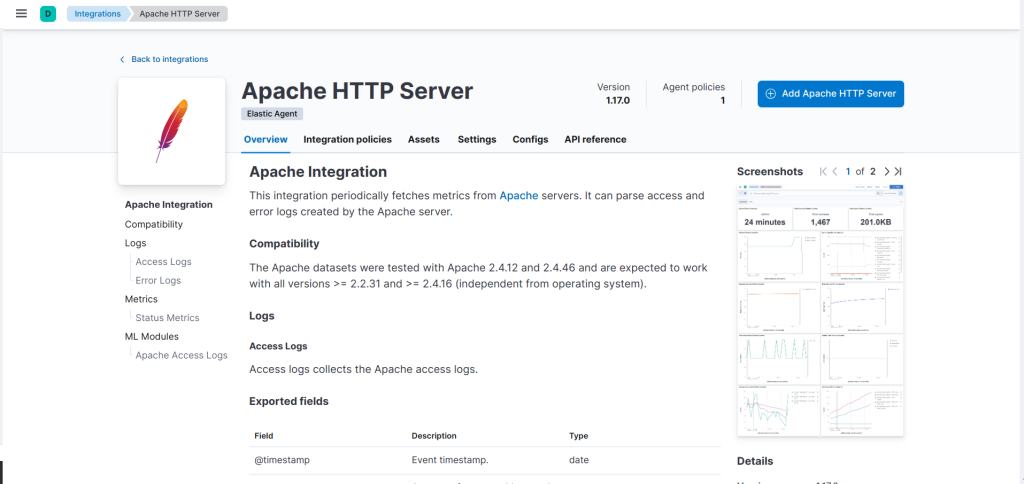
This policy is created with the default integration (system) which is not enough to capture the Apache logs. Let’s add additinal integrations. First let’s start with the Apache HTTP server integration.
Then, also include the Network Packet Capture intergration to the agant policy.
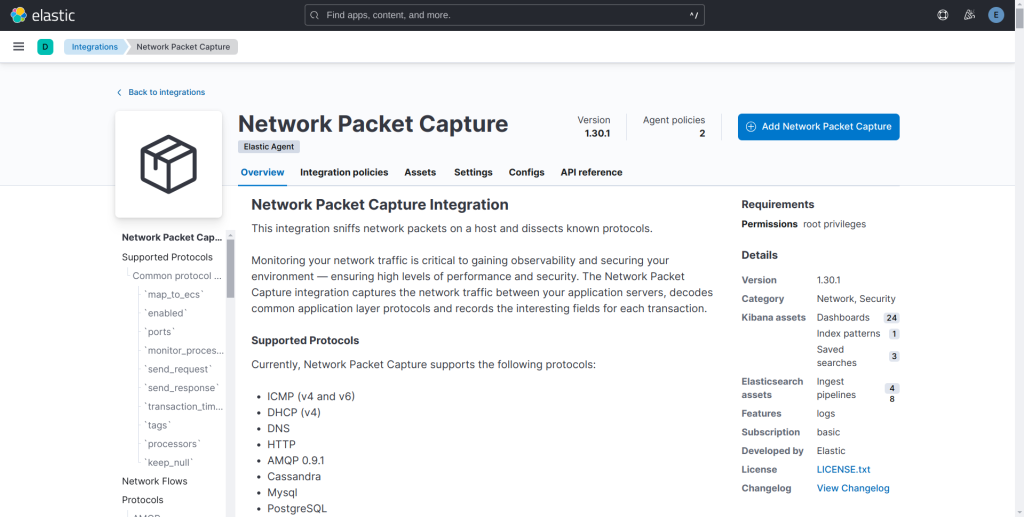
Deploy the Elastic Agent on the Linux VM that is hosting the vulnerable app DIWA. Use the –insecure switch while deploying the agaent (to avoid cert errors in LAB environments).
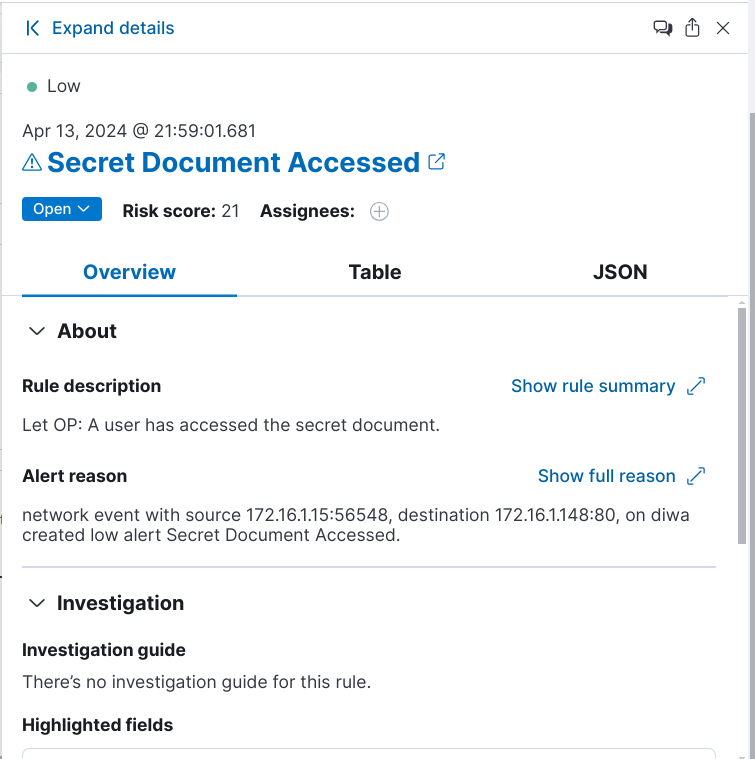
The DIWA app has a hidden vulnerable file/page named “secret-xu2d7a.php” which can be accessed using the link http://172.16.1.148/download.php?file=../content/secret-xu2d7a.php. Let’s create a detection rule to create an alert whenever someone access and download this hidden/secret page.
Threat Detection Rule
From Security –> Alerts, click Manage Ruels and then click on Create new rule. Follow the below steps to create a new custom rule.
Step:1
* Rule type: Custom Query
* Source: (leave unmodified)
* Custom query: url.query:*secret-xu2d7a* or url.full.text:*secret-xu2d7a*Step 2:
* Name: Secret Document Accessed
* Description: A user has accessed the secret documentStep 3:
* Runs every: 5m
* Additional look-back time: 1mFinally, the newly created rule looks like below after saving it.
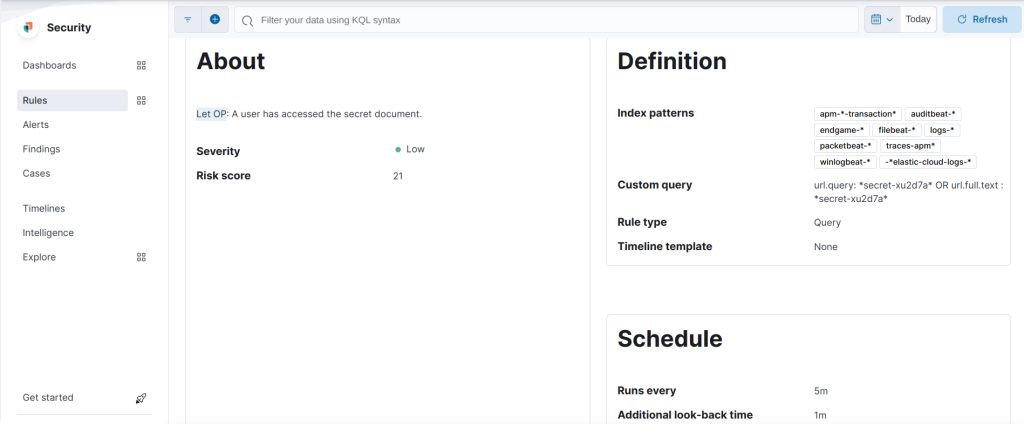
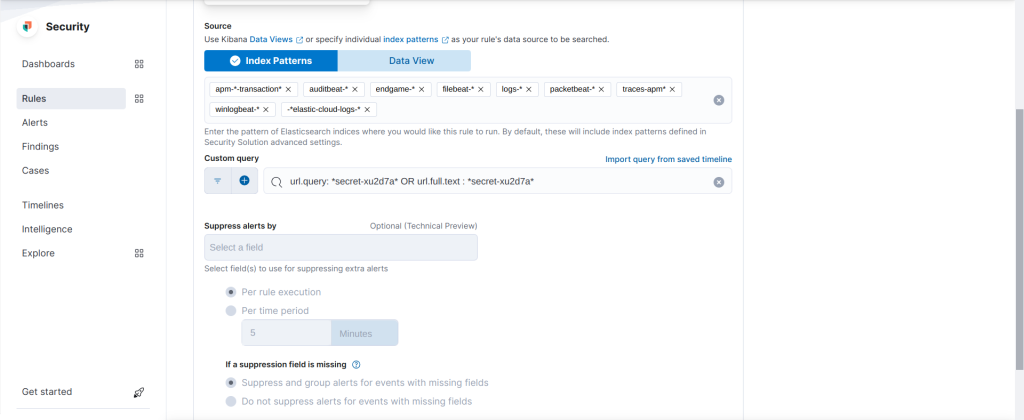
Now, let us try to access the secret file/page using the URL mentioned earler.

Now, we can see the following alerts generated by the rule while we attempted to access the secret document.
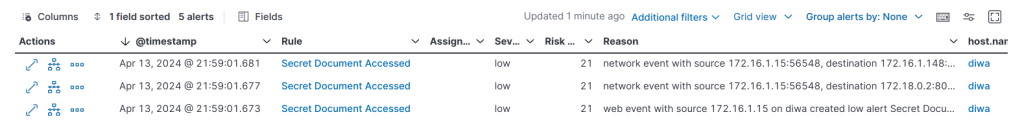
Note: There are three alerts generated for the event. The Web event alert is generated by the “Apache HTTP Capture” integration and two others are created by the “Network Packet Capture” integration. Since, the DIWA app is deployed using docker, two network alerts are generated one for the VM IP and another one for the docker IP of the app.
Description of the Alert: