Views: 42
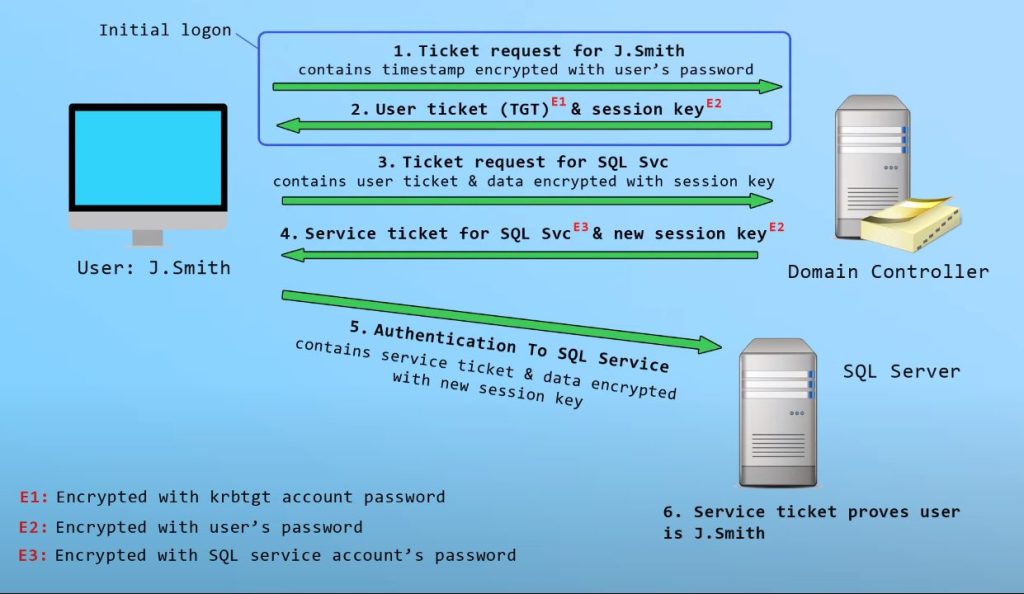
Kerberos Authentication
References
https://www.youtube.com/watch?v=snGeZlDQL2Q
https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-kile/b4af186e-b2ff-43f9-b18e-eedb366abf13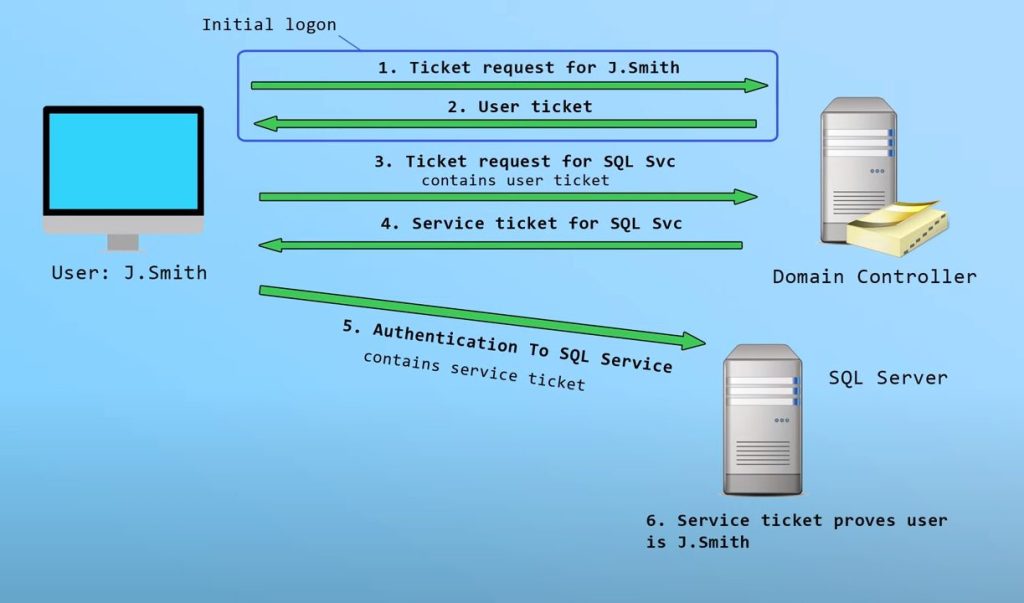
krbtgt account -→ KDC Service Account
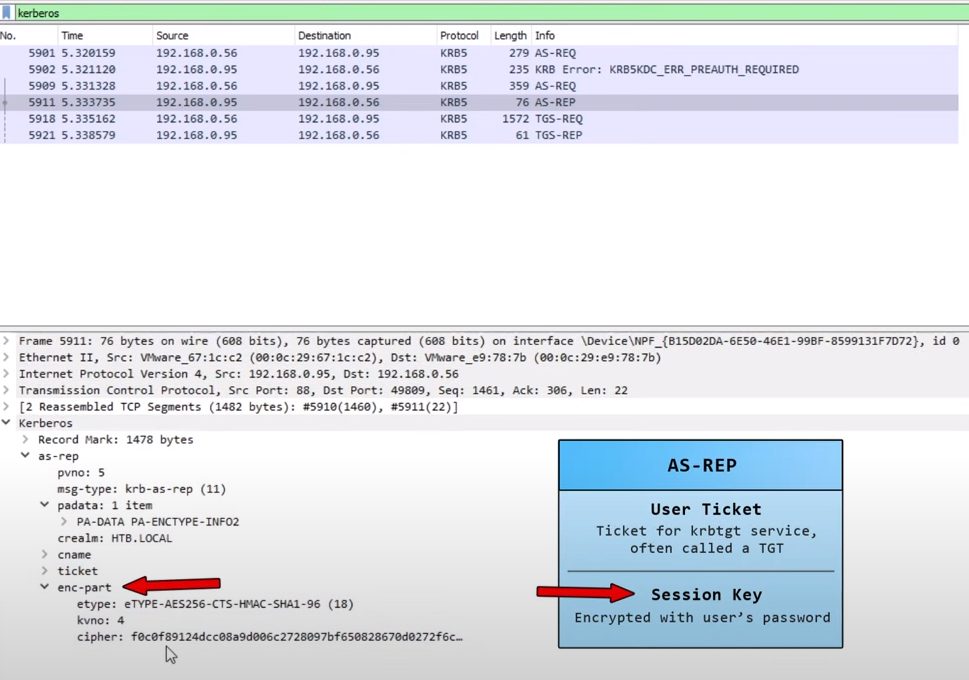
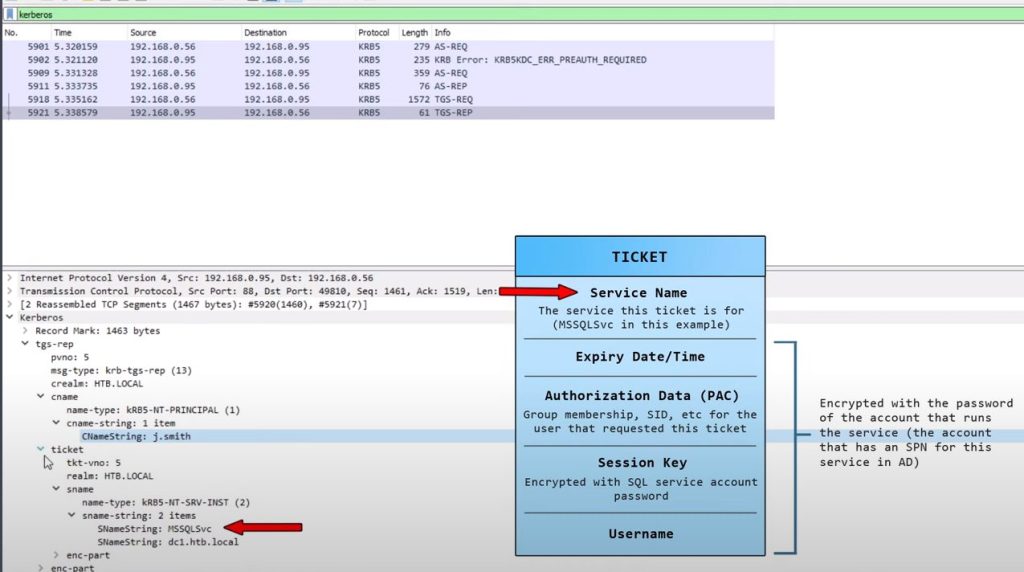
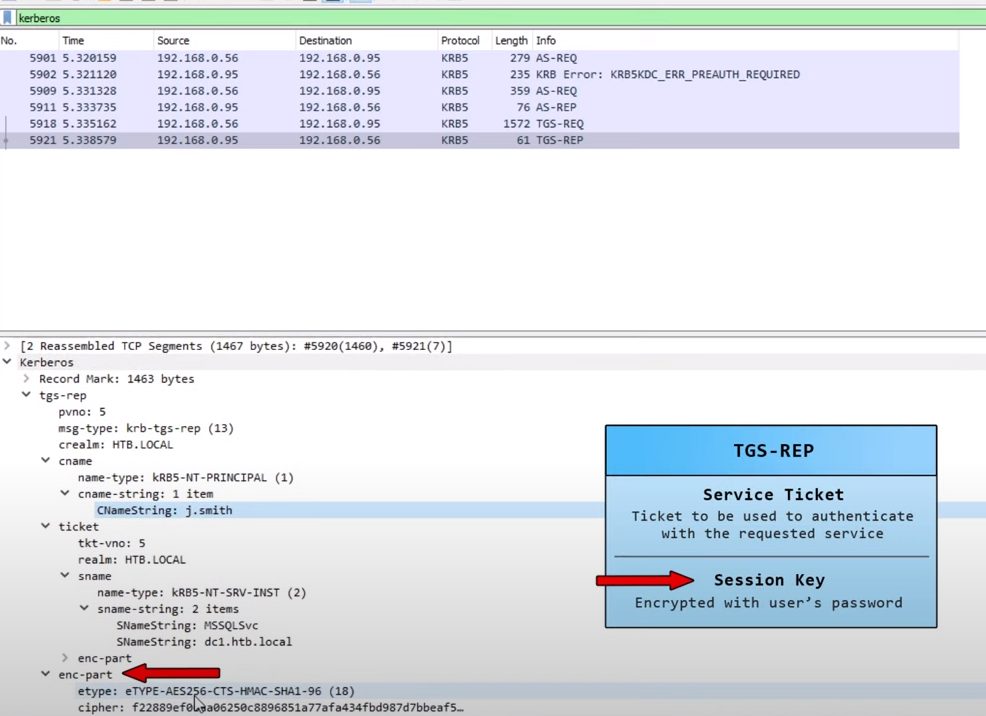
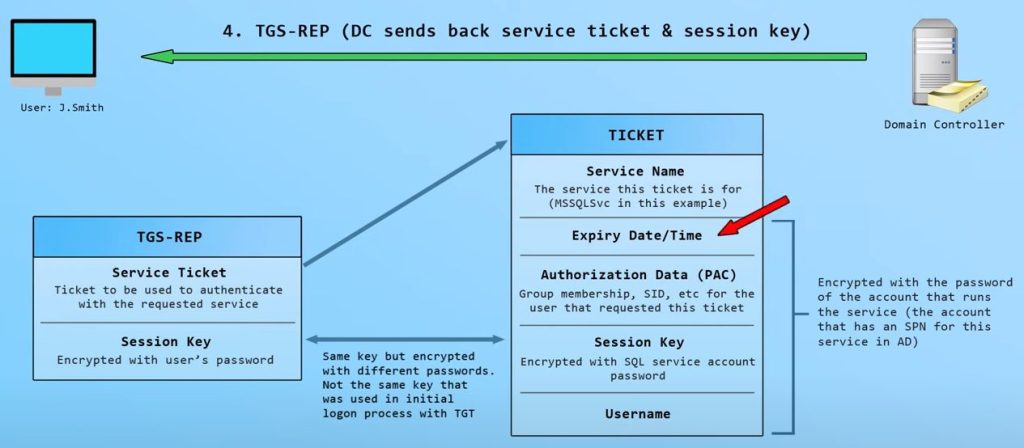
Ticket Details
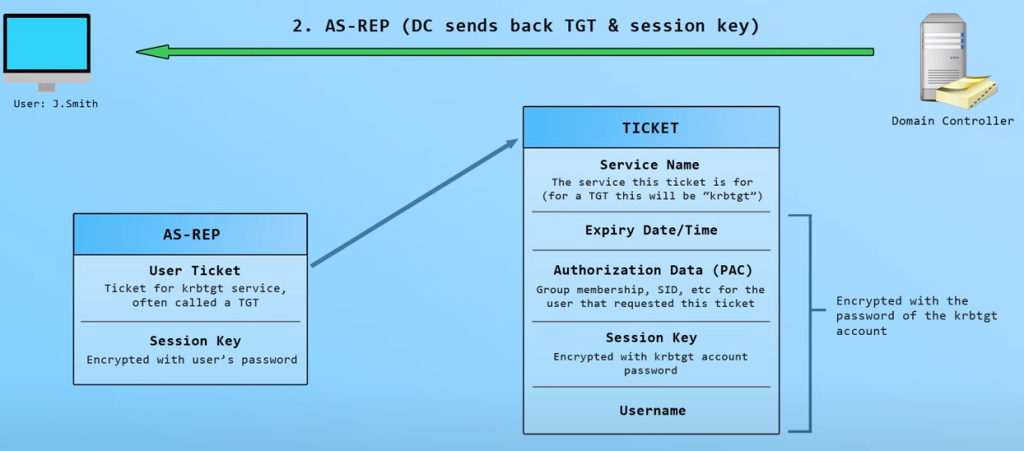
Authorization Data is Microsoft addition to Kerberos; can be manipulated to modify Group membership..etc and launch attacks.
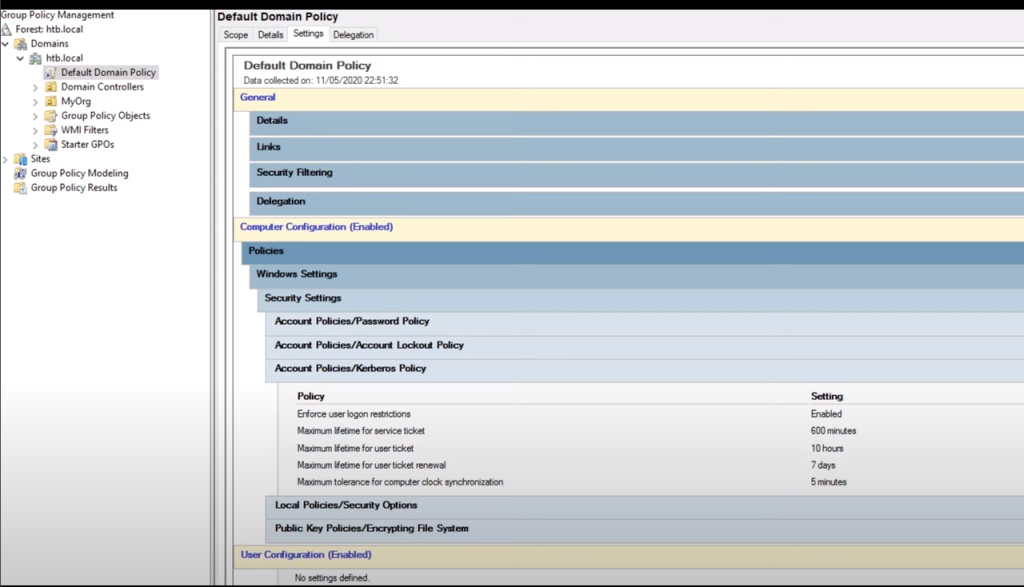
Domian Policy about Kerberos settings (default):
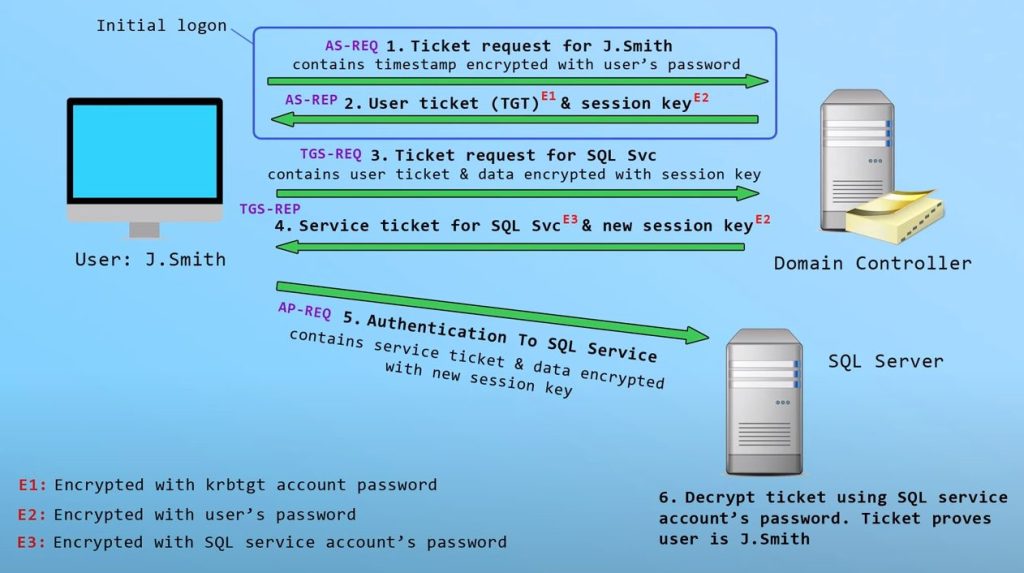
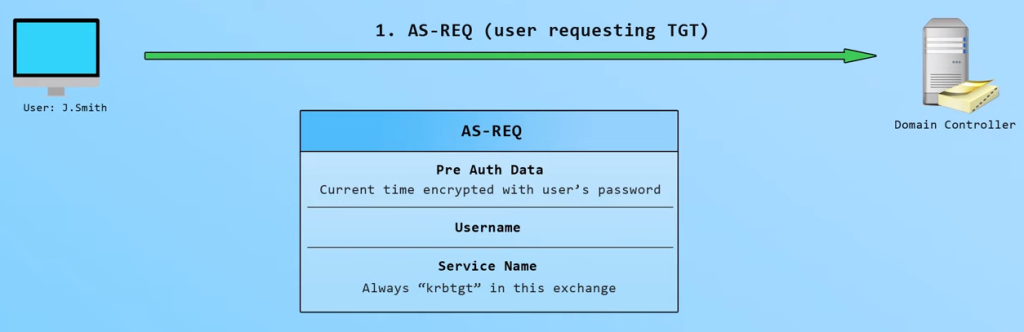
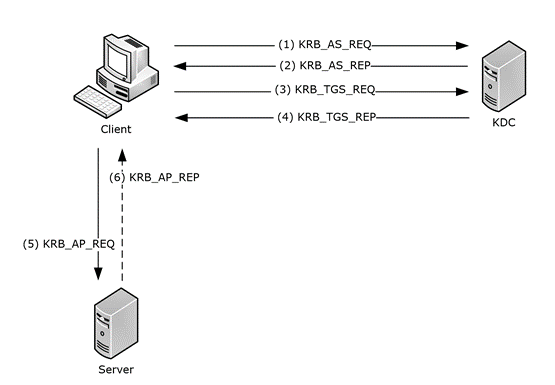
The Authentication Service (AS) exchange ([RFC4120] section 3.1):<1>
- Kerberos authentication service request message (KRB_AS_REQ) ([RFC4120] section 5.4.1): The client sends a request to the KDC for a ticket-granting ticket (TGT) ([RFC4120] section 5.3). The client presents its principal name and can present pre-authentication information.
- Kerberos authentication service response message (KRB_AS_REP) ([RFC4120] section 5.4.2): The KDC returns a TGT and a session key the client can use to encrypt and authenticate communication with the KDC for ticket-granting service (TGS) requests, without reusing the persistent key.
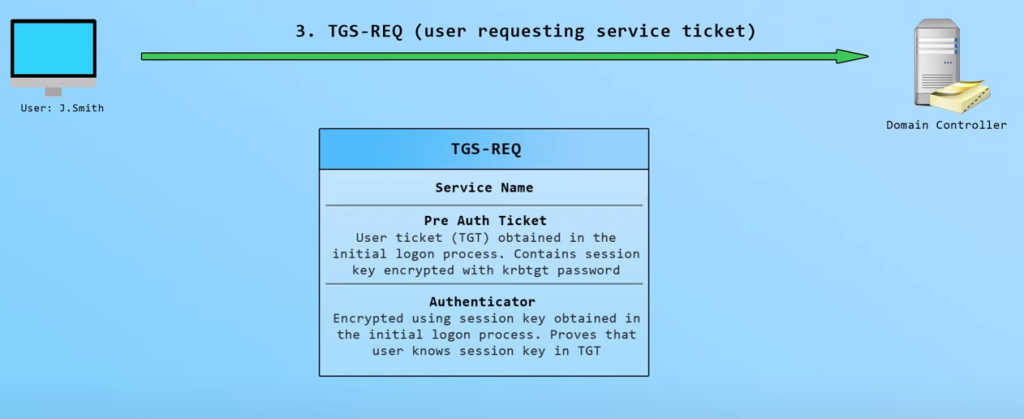
The Ticket-Granting Service (TGS) exchange ([RFC4120] section 3.3):
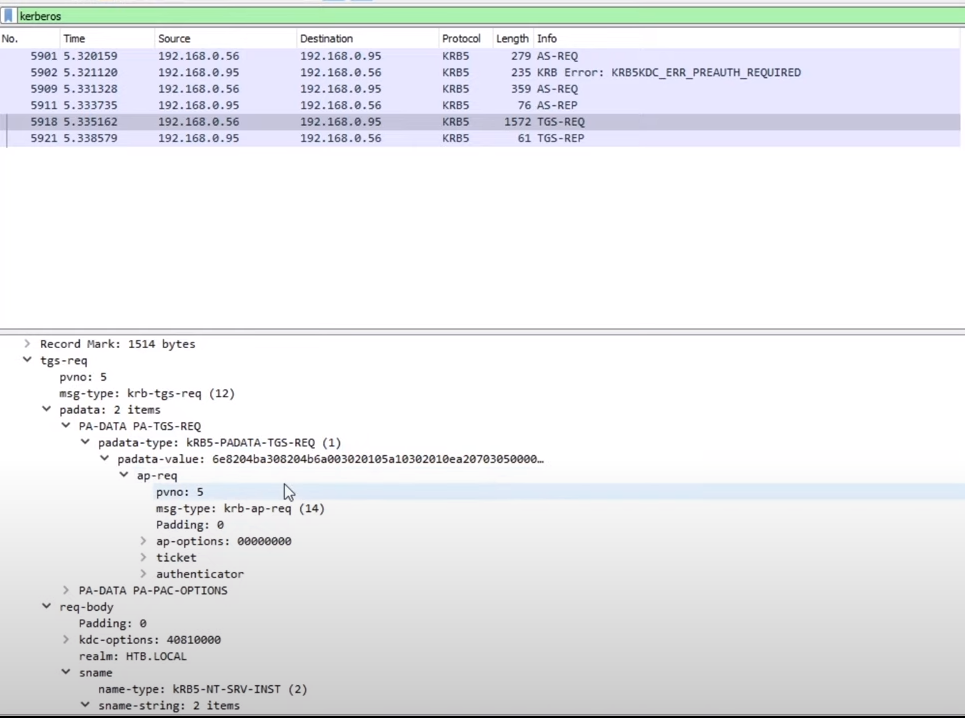
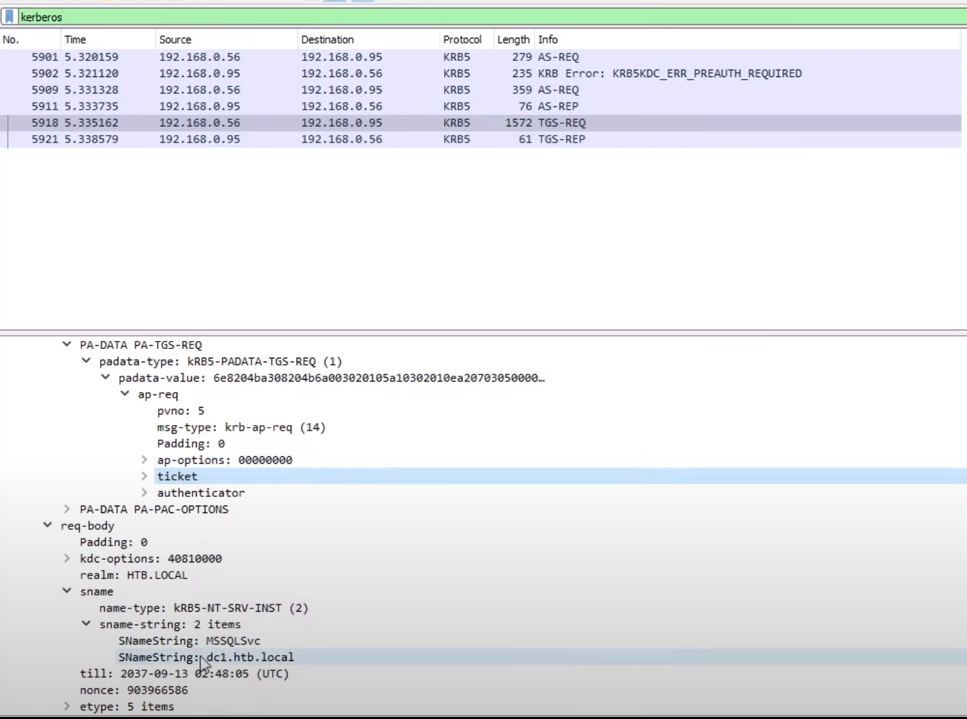
- Kerberos ticket-granting service (TGS) request message (KRB_TGS_REQ) ([RFC4120] section 5.4.1): The client sends a request to the KDC for a ticket ([RFC4120] section 5.3) for the server. The client presents the TGT ([RFC4120] section 5.3), a Kerberos authenticator ([RFC4120] section 5.5.1), and the service principal name (SPN).
- Kerberos ticket-granting service (TGS) response message (KRB_TGS_REP) ([RFC4120] section 5.4.2): The KDC validates the TGT ([RFC4120] section 5.3) and the authenticator ([RFC4120] section 5.5.1). If these are valid, the KDC returns a service ticket ([RFC4120] section 5.3) and session key the client can use to encrypt communication with the server.
The Client/Server Authentication Protocol (AP) exchange ([RFC4120] section 3.2):
- Kerberos application server request message (KRB_AP_REQ) ([RFC4120] section 5.5.1): The client requests access to the server. The client presents the ticket ([RFC4120] section 5.3) and a new authenticator ([RFC4120] section 5.5.1). The server will decrypt the ticket, validate the authenticator, and can use any authorization data ([RFC4120] section 5.2.6) contained in the ticket for access control.
- Kerberos application server response message (KRB_AP_REP) ([RFC4120] section 5.5.2): Optionally, the client might request that the server verify its own identity. If mutual authentication is requested, the server returns the client’s timestamp from the authenticator encrypted with the session key.
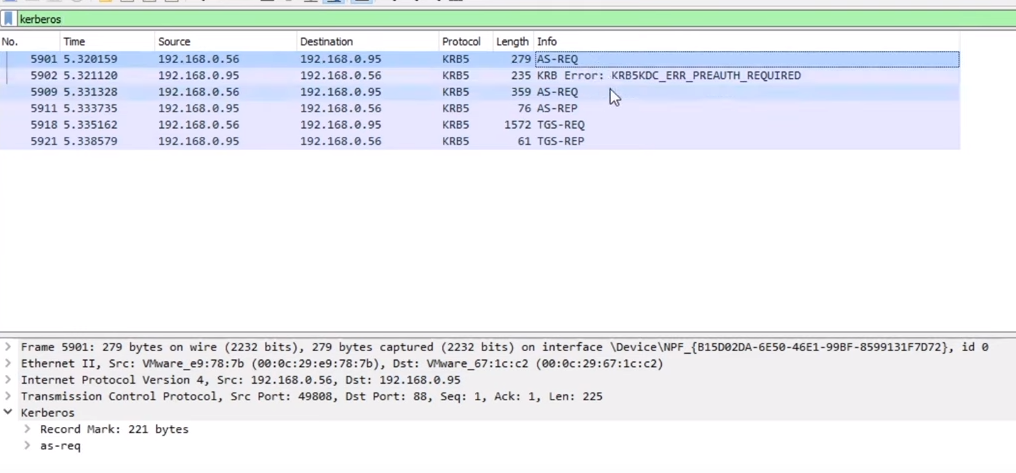
Packet Capture
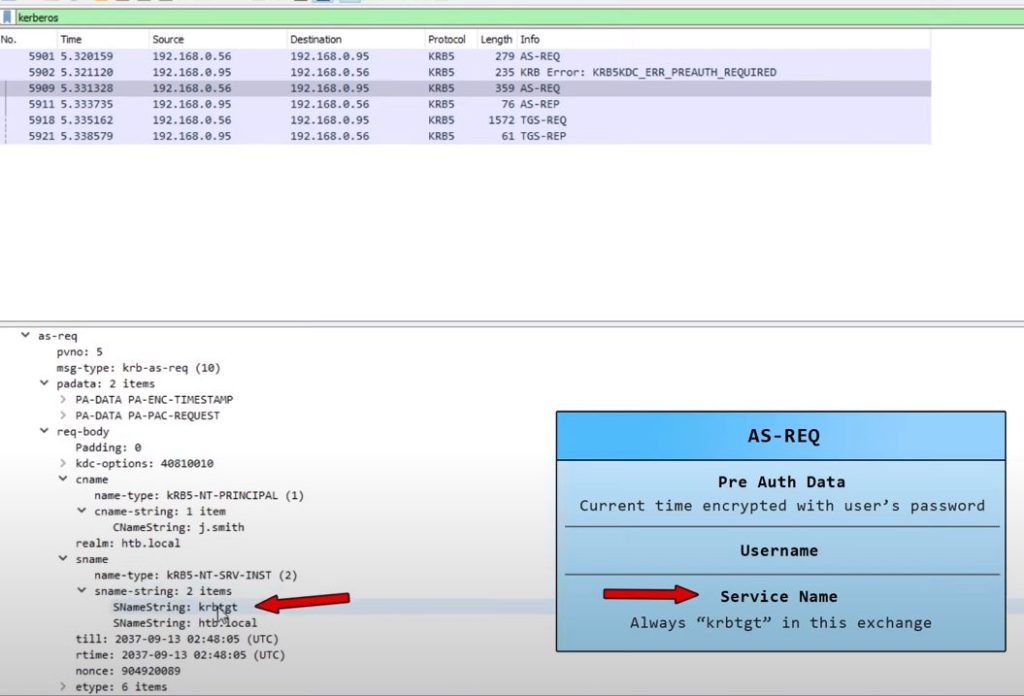
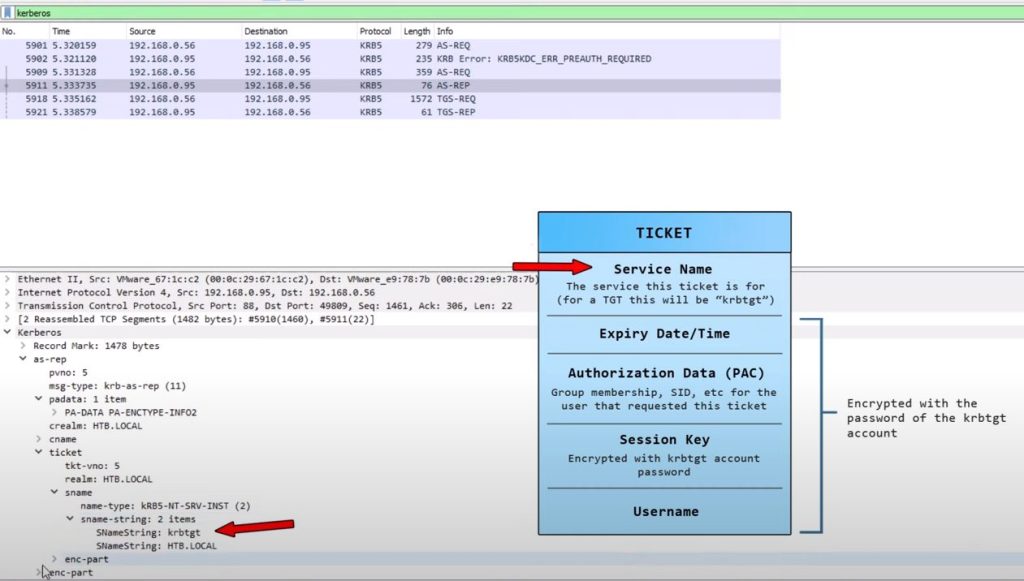
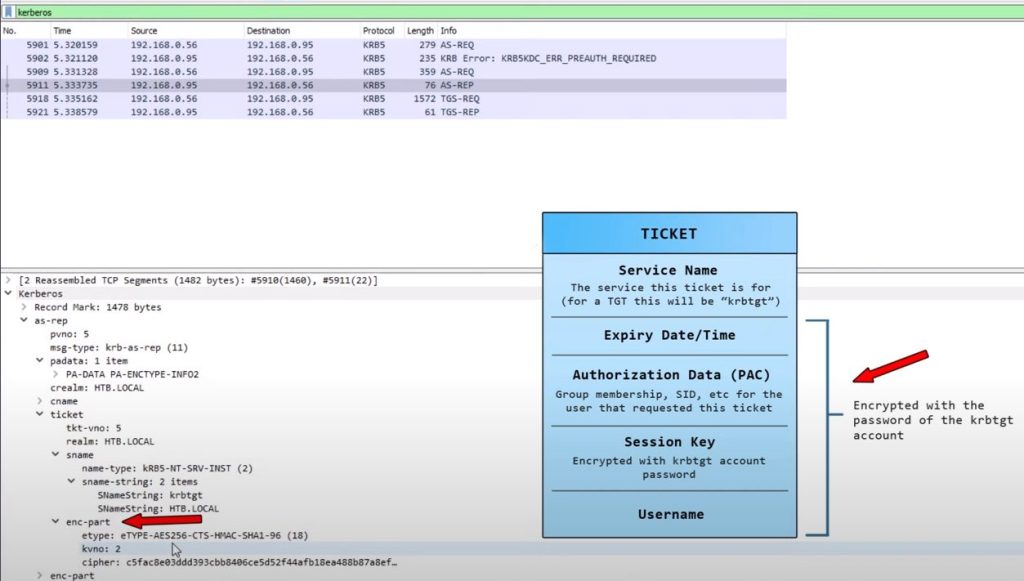
Seperate Session Key (encrypted):