Views: 461
Wazuh Integration with VirusTotal
Overview
Wazuh integrates with VirusTotal to detect malicious files via the File Integrity Monitoring (FIM) module. This allows inspection of monitored files for potential threats.
About VirusTotal
- Service Features:
- Analyzes files and URLs to detect malware.
- Stores analysis results for file hash lookups.
- Provides an API for programmatic access.
- API Options:
- Public API:
- Free with limitations: 500 requests/day, 4 requests/min.
- Restricted from use in commercial or automated workflows.
- Multiple accounts to bypass limitations are prohibited.
Create an account in VirusTotal website and obtain a public key to use in this lab.
- Private API:
- Premium access with higher request limits and priority.
How Wazuh Integration Works
- FIM Monitoring:
- Detects file additions, changes, or deletions.
- Stores file hashes and triggers alerts for modifications.
- VirusTotal Query:
- Sends file hashes to VirusTotal API when an alert is triggered.
- Receives a JSON response, generating specific alerts:
- Error Alerts:
- Invalid credentials.
- API rate limit reached.
- Informational Alerts:
- No database records or positives found.
- Number of antivirus detections.
- Logs:
- Logs alerts in
/var/ossec/logs/integrations.logand/var/ossec/logs/alerts/alerts.log.
Configuration Steps
1. Enable Integration
- Edit
/var/ossec/etc/ossec.confto include:
<integration>
<name>virustotal</name>
<api_key>API_KEY</api_key> <!-- Replace with your VirusTotal API key -->
<group>syscheck</group>
<alert_format>json</alert_format>
</integration>2. Ubuntu Endpoint Configuration for Directory Monitoring
- Edit the Wazuh agent
/var/ossec/etc/ossec.confconfiguration file. Add the directories for monitoring within the<syscheck>block. - Add to the
<syscheck>section to monitor /tmp folder
. You can also configure this capability remotely using the centralized configuration options provided by the agent.conf file.
<syscheck><br> <directories check_all="yes" realtime="yes">/tmp</directories><br> </syscheck>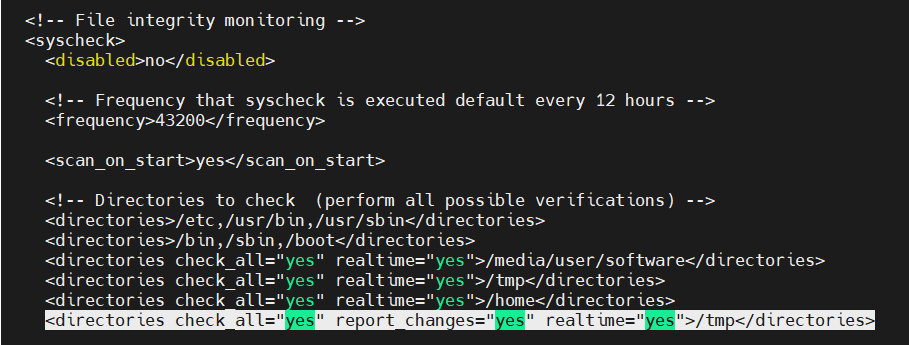
3. Restart the Wazuh Agent
- Systemd:
systemctl restart wazuh-agentNote: Replace placeholders with actual configurations like the VirusTotal API key. For detailed FIM options, refer to the syscheck documentation.
Use Case: Scanning a File
- Wazuh agent with VirusTotal integration identifies malicious content when a file is modified or downloaded in the monitored directory and reports the event to the Wazuh Manager
Let us test this integration by downloading a malicious file on the Ubuntu endpoint in the monitored folder (in this case /tmp folder).
WARNING!!! Download the Eicar file here for testing purposes only. We recommend testing in a sandbox, not in a production environment.
The EICAR Anti-Virus Test File[1] or EICAR test file is a computer file that was developed by the European Institute for Computer Antivirus Research (EICAR) and Computer Antivirus Research Organization (CARO) to test the response of computer antivirus (AV) programs.[2] Instead of using real malware, which could cause real damage, this test file allows people to test anti-virus software without having to use a real computer virus.[3]
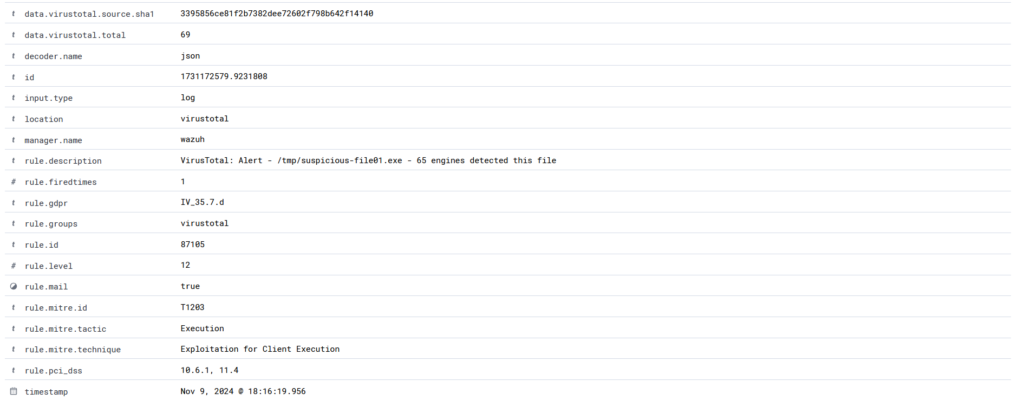
sudo curl -Lo /media/user/software/suspicious-file01.exe https://secure.eicar.org/eicar.comWazuh agent immediately reports the incident to the Wazuh Manager.
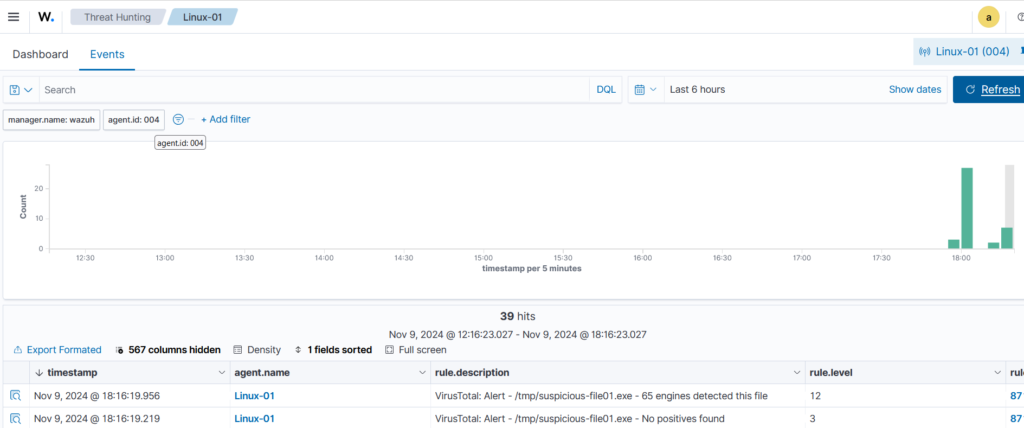
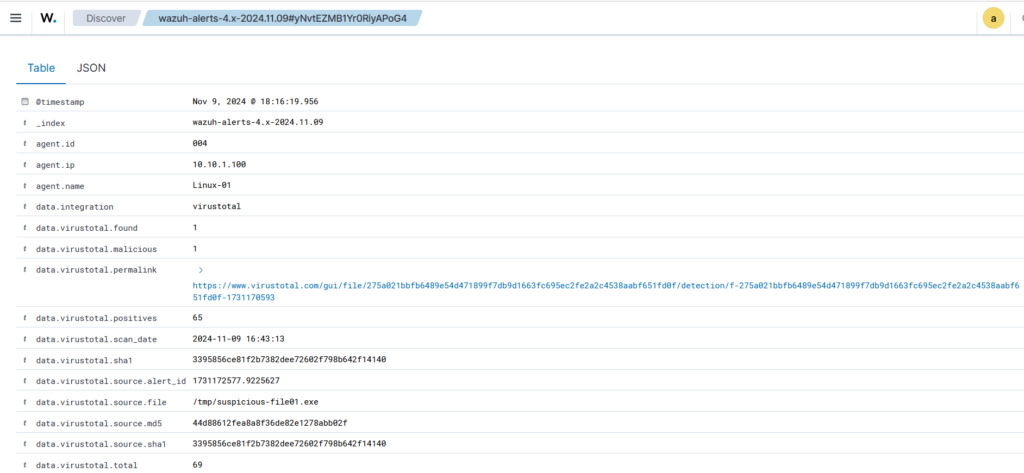
Alert Details
Integrating Wazuh with VirusTotal is a valuable addition to any SOC, enhancing threat intelligence and speeding up incident response. This integration allows cybersecurity analysts to leverage comprehensive data, helping them make informed decisions and act swiftly when threats arise.



