Views: 77
Identifying Hosts
When investigating a compromise or malware infection activity, a security analyst should know how to identify the hosts on the network apart from IP to MAC address match. One of the best methods is identifying the hosts and users on the network to decide the investigation’s starting point and list the hosts and users associated with the malicious traffic/activity.
Usually, enterprise networks use a predefined pattern to name users and hosts. While this makes knowing and following the inventory easier, it has good and bad sides. The good side is that it will be easy to identify a user or host by looking at the name. The bad side is that it will be easy to clone that pattern and live in the enterprise network for adversaries. There are multiple solutions to avoid these kinds of activities, but for a security analyst, it is still essential to have host and user identification skills.
Protocols that can be used in Host and User identification:
- Dynamic Host Configuration Protocol (DHCP) traffic
- NetBIOS (NBNS) traffic
- Kerberos traffic
DHCP Analysis
DHCP investigation in a nutshell:
| Description | Wireshark Filter |
|---|---|
| Global search. | dhcp or bootp |
| Filtering the proper DHCP packet options is vital to finding an event of interest. “DHCP Request” packets contain the hostname information “DHCP ACK” packets represent the accepted requests “DHCP NAK” packets represent denied requests Due to the nature of the protocol, only “Option 53” ( request type) has predefined static values. You should filter the packet type first, and then you can filter the rest of the options by “applying as column” or use the advanced filters like “contains” and “matches”. | Request: dhcp.option.dhcp == 3ACK: dhcp.option.dhcp == 5NAK: dhcp.option.dhcp == 6 |
| “DHCP Request” options for grabbing the low-hanging fruits: Option 12: Hostname. Option 50: Requested IP address. Option 51: Requested IP lease time. Option 61: Client’s MAC address. | dhcp.option.hostname contains "keyword" |
| “DHCP ACK” options for grabbing the low-hanging fruits: Option 15: Domain name. Option 51: Assigned IP lease time. | dhcp.option.domain_name contains "keyword" |
| “DHCP NAK” options for grabbing the low-hanging fruits: Option 56: Message (rejection details/reason). | As the message could be unique according to the case/situation, It is suggested to read the message instead of filtering it. Thus, the analyst could create a more reliable hypothesis/result by understanding the event circumstances. |
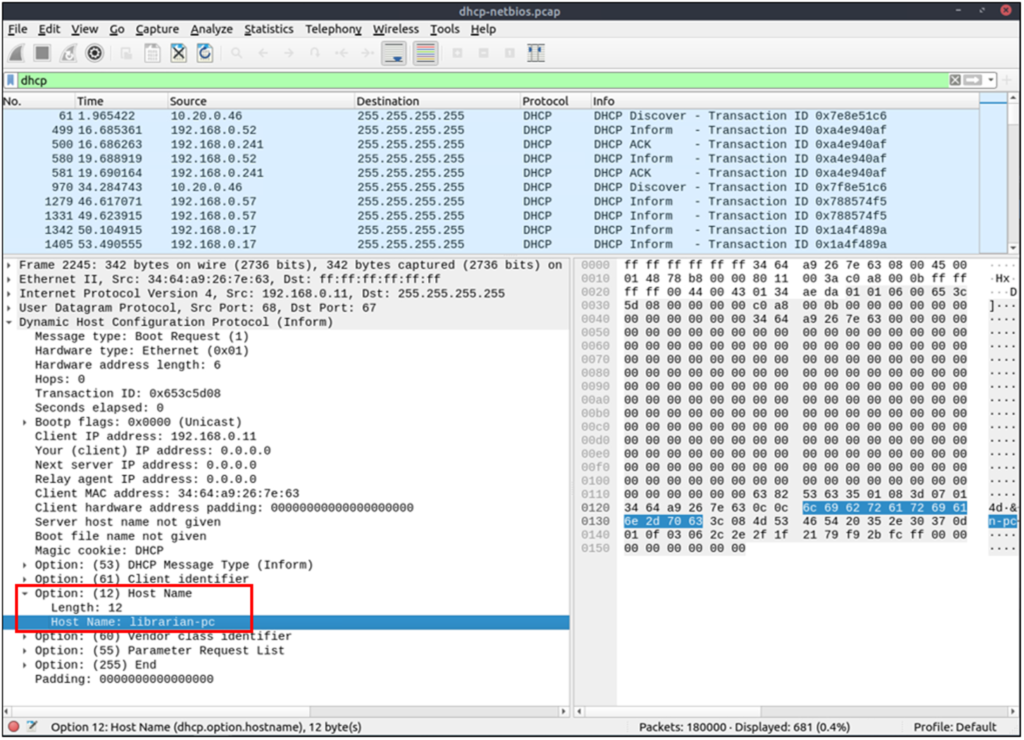
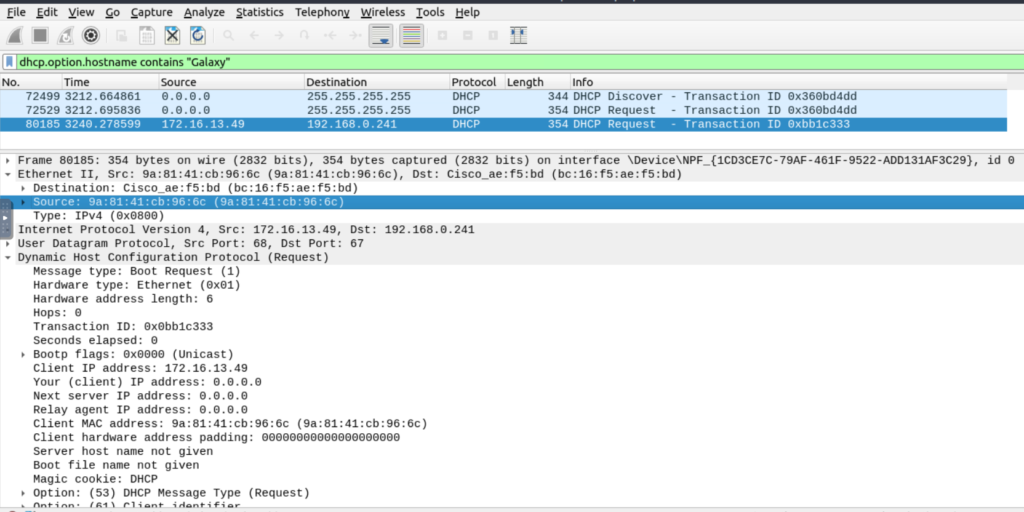
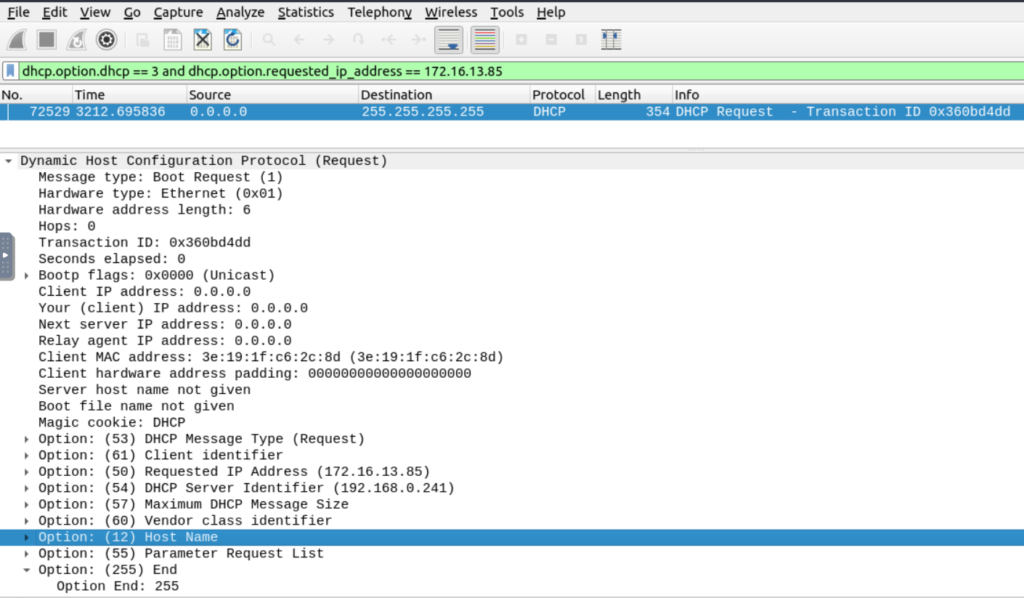
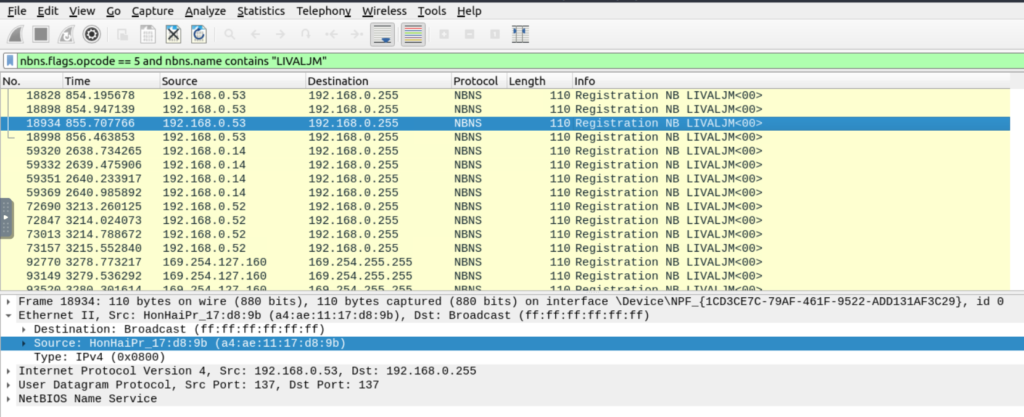
NetBIOS (NBNS) Analysis
NetBIOS or Network Basic Input/Output System is the technology responsible for allowing applications on different hosts to communicate with each other.
| Description | Wireshark Filter |
|---|---|
| Global search. | nbns |
| “NBNS” options for grabbing the low-hanging fruits: Queries: Query details. Query details could contain “name, Time to live (TTL) and IP address details” | nbns.name contains "keyword" |
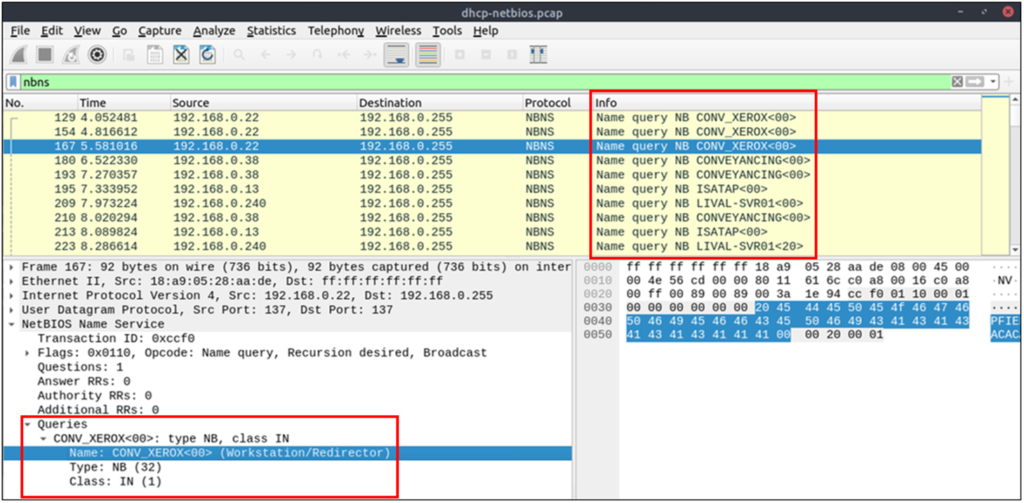
Kerberos Analysis
Kerberos is the default authentication service for Microsoft Windows domains. It is responsible for authenticating service requests between two or more computers over the untrusted network. The ultimate aim is to prove identity securely.
| Description | Wireshark Filter |
|---|---|
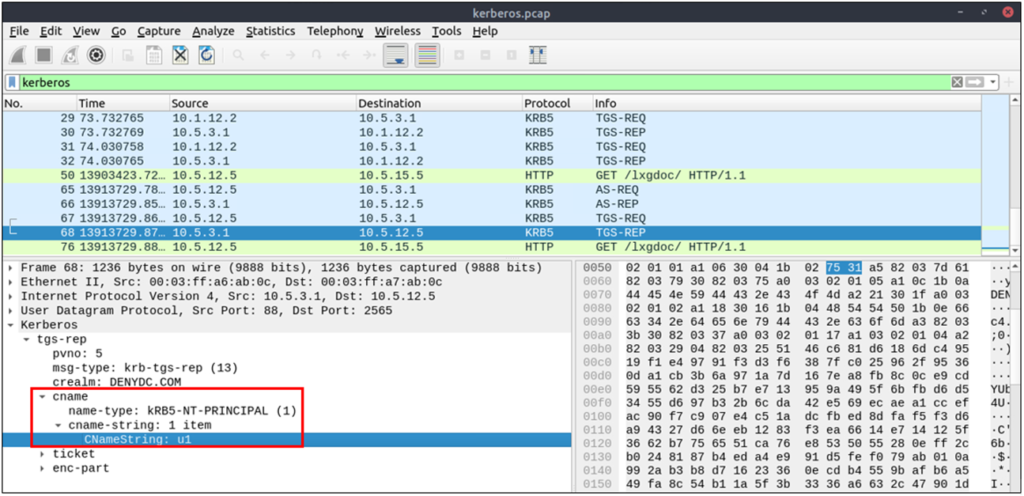
| Global search. | kerberos |
| User account search: CNameString: The username. Note: Some packets could provide hostname information in this field. To avoid this confusion, filter the “$” value. The values end with “$” are hostnames, and the ones without it are user names. | kerberos.CNameString contains "keyword"kerberos.CNameString and !(kerberos.CNameString contains "$" ) |
| “Kerberos” options for grabbing the low-hanging fruits: pvno: Protocol version. realm: Domain name for the generated ticket. sname: Service and domain name for the generated ticket. addresses: Client IP address and NetBIOS name. Note: the “addresses” information is only available in request packets. | kerberos.pvno == 5kerberos.realm contains ".org"kerberos.SNameString == "krbtg" |
Click here to go to PART 1 of this series



