Views: 62
“The pattern matching swiss knife for malware researchers (and everyone else)”
Useful Yara Resources
Various Github repositories provide a wealth of examples of YARA,
https://github.com/Yara-Rules/rules/tree/master/malware
https://github.com/mikesxrs/Open-Source-YARA-rules/tree/masterUseful Yara Rules Repositories
The DFIR Report” shares YARA rules derived from their investigations,
https://github.com/The-DFIR-Report/Yara-RulesYara DFIR Report
YARA in a nutshell
YARA is a tool aimed at (but not limited to) helping malware researchers to identify and classify malware samples. With YARA we can create descriptions of malware families (or whatever you want to describe) based on textual or binary patterns. Each description, a.k.a rule, consists of a set of strings and a boolean expression which determine its logic. Let’s see an example:
rule silent_banker : banker
{
meta:
description = "This is just an example"
threat_level = 3
in_the_wild = true
strings:
$a = {6A 40 68 00 30 00 00 6A 14 8D 91}
$b = {8D 4D B0 2B C1 83 C0 27 99 6A 4E 59 F7 F9}
$c = "UVODFRYSIHLNWPEJXQZAKCBGMT"
condition:
$a or $b or $c
}Rules are used to label these patterns. For example, Yara rules are frequently written to determine if a file is malicious or not, based upon the features – or patterns – it presents.
Strings are a fundamental component of programming languages. Applications use strings to store data such as text.
Why does Malware use Strings?
Malware, just like our “Hello World” application, uses strings to store textual data. Here are a few examples of the data that various malware types store within strings:
| Type | Data | Description |
| Ransomware | 12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw | Bitcoin Wallet for ransom payments |
| Botnet | 12.34.56.7 | The IP address of the Command and Control (C&C) server |
Introduction to Yara Rules
Yara rule(s) is only as effective as our understanding of the patterns we want to search for.
Using a Yara rule is simple. Every yara command requires two arguments to be valid, these are:
1) The rule file we create
2) Name of file, directory, or process ID to use the rule for.
Every rule must have a name and condition.
# Create a Yara rule name "myrule.yara" on directory "yararules"
yara myrule.yar yararulesVarious Github repositories provide a wealth of examples of YARA rules,
https://github.com/Yara-Rules/rules/tree/master/malware
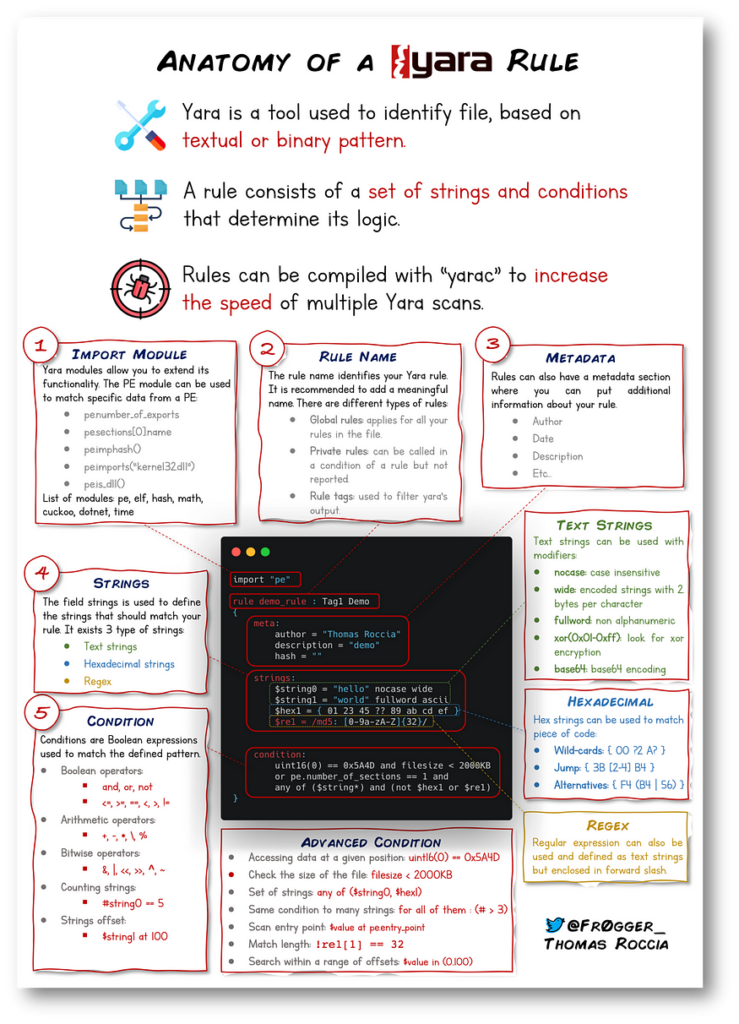
https://github.com/mikesxrs/Open-Source-YARA-rules/tree/masterAnatomy of Yara Rule
Malware Detection and Classification:
YARA rules are particularly useful for SOC analysts in pinpointing and classifying malware. Leveraging YARA rules, analysts can create specific patterns or signatures that correspond to known malware traits or behaviors. This aids in the prompt detection and mitigation of malware threats, bolstering the organization’s overall security posture.
Indicator of Compromise (IOC) Identification:
YARA rules empower SOC analysts to locate and identify IOCs, which are distinct artifacts or behaviors linked to security incidents or breaches. By embedding IOCs into their rules, analysts can swiftly detect and counter potential threats, thus mitigating the consequences of security incidents and curtailing the duration of attackers’ presence within the network.
Collaboration and Standardization:
YARA offers standardized formats and rule structures, fostering collaboration among SOC analysts and tapping into the collective expertise of the broader cybersecurity community.
https://github.com/The-DFIR-Report/Yara-Rules
# https://thedfirreport.com/Integration with Security Tools:
YARA rules can be integrated seamlessly with a plethora of security tools, including SIEM platforms, log analysis systems, and incident response platforms.
Uncoder.io facilitates the conversion of Sigma rules into tailor-made, performance-optimized queries ready for deployment in the chosen SIEM and XDR systems.



